Get to know WannaCry
The ransomware attack caused damage to many companies and organizations around the world, including the Spanish telecommunications company Telefonica, hospitals in the UK and the US delivery company FedEx. A malicious program belonging to the class of cryptographers has become known as “WannaCry”.
The malware can TCP port 445 (Server Message Block / SMB) and spread like a worm, attacking hosts and encrypting the files on them. After that, he needs to list a certain number of bitcoins for decryption.
In connection with this attack, it was recommended to all organizations to make sure that the latest updates were installed on their computers running on Windows. Also on them should be closed ports 139 and 445 for external access. Ports are used by the SMB protocol.
It should also be noted that the threat is still being actively investigated, so that the situation may change depending on the reaction of the attackers to the actions of computer security specialists.
')
CAMPAIGN DETAILS
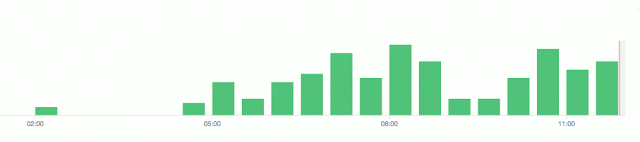
We saw a spike in scanning our “Internet Lures”, which began almost at 5 am EST (9 am UTC).
INFRASTRUCTURE ANALYSIS
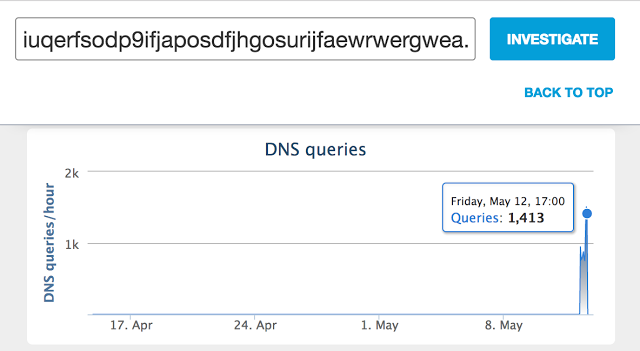
Researchers at Cisco Umbrella first noticed requests to the domain switch (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea [.] Com), which began at 07:24 UTC, and after only 10 hours, the number of requests already exceeded 1400 per hour ( approx. Transl .: Apparently, it’s about requests for their service).
The domain name looks like it was composed by humans, since most of the characters are on adjacent rows of the keyboard.
This domain can be called a switch, based on its role in the execution of the malware:
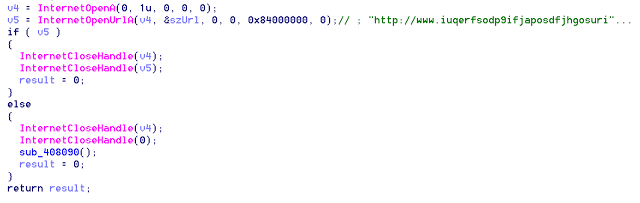
The code above attempts to get a GET request to the domain and, in case of failure, continues to propagate. If the request is successful, the program ends. Now the domain is registered to a known DNS funnel , which causes it to interrupt a malicious action.
From the translator: The C & C domain was specifically registered, according to MalwareTech's tweeter, to stop or suspend the distribution of Malvari .
ANALYSIS OF THE HARVEST
The original mssecsvc.exe file runs another file called tasksche.exe. Then the domain switch is checked, after which the service mssecsvc2.0 is created. This service executes the mssecsvc.exe file with a different entry point than during the first launch. The second launch receives the IP address of the infected machine and tries to connect to the 445 TCP port of each IP address within the subnet. When the malware successfully connects to a remote machine, a connection is established and data is transferred. Apparently, somewhere in the process of this transfer, a known vulnerability is used, which was closed by updating MS 17-010. At the moment there is no complete understanding of SMB traffic, and under what conditions the malware can spread, using a security hole.
The taskche.exe file checks all drives, as well as folders and connected devices that are linked to letters, like 'C: /', 'D: /', etc. Malware then looks for files with the extensions that are listed in the program (and are listed below) and encrypts them using 2048-bit RSA encryption. While the files are encrypted, the Tor / folder is created where the tor.exe file is placed and the 9 dll files it uses. Additionally, taskdl.exe and taskse.exe are created. The first one deletes the temporary files, and the second launches @ wanadecryptor @ .exe, which shows the user a window asking him to pay. The @ wanadecryptor @ .exe file is responsible only for displaying the message. File encryption occurs in the background using tasksche.exe.
The tor.exe file is launched using @ wanadecryptor @ .exe. This new process starts connecting to Tor nodes. Thus, WannaCry maintains anonymity by passing all of its traffic through the Tor network.
As is typical for ransomware programs, the program also deletes any shadow copies on the victim's computer to make recovery even more difficult. This is done using WMIC.exe, vssadmin.exe and cmd.exe

WannaCry uses various ways to help its accomplishment. So it is used attrib.exe, to change the flag + h (hide), as well as icacls.exe, to give full rights to all users: “icacls. / grant Everyone: F / T / C / Q ".
It is noteworthy that the program has a modular architecture. It is likely that all executable files in it are written by different people. Potentially, this may mean that the structure of the program may allow different malicious scripts to be run.
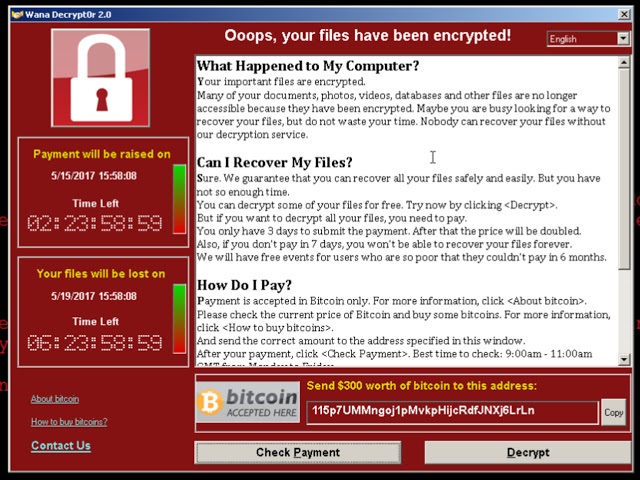
After the encryption is complete, the malware displays a window requesting a ransom for the files. An interesting point is that the window is an executable file, not a picture, an HTA file, or a text file.
Victims should understand that there is no obligation for criminals to actually provide the keys for decryption after paying the ransom.
HOW TO FIGHT
To combat this malware there are two recommendations:
Lesion indicators
File Names:
IP used:
File Encryption Extensions:
→ Source
The malware can TCP port 445 (Server Message Block / SMB) and spread like a worm, attacking hosts and encrypting the files on them. After that, he needs to list a certain number of bitcoins for decryption.
In connection with this attack, it was recommended to all organizations to make sure that the latest updates were installed on their computers running on Windows. Also on them should be closed ports 139 and 445 for external access. Ports are used by the SMB protocol.
It should also be noted that the threat is still being actively investigated, so that the situation may change depending on the reaction of the attackers to the actions of computer security specialists.
')
CAMPAIGN DETAILS
We saw a spike in scanning our “Internet Lures”, which began almost at 5 am EST (9 am UTC).

INFRASTRUCTURE ANALYSIS
Researchers at Cisco Umbrella first noticed requests to the domain switch (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea [.] Com), which began at 07:24 UTC, and after only 10 hours, the number of requests already exceeded 1400 per hour ( approx. Transl .: Apparently, it’s about requests for their service).

The domain name looks like it was composed by humans, since most of the characters are on adjacent rows of the keyboard.
This domain can be called a switch, based on its role in the execution of the malware:

The code above attempts to get a GET request to the domain and, in case of failure, continues to propagate. If the request is successful, the program ends. Now the domain is registered to a known DNS funnel , which causes it to interrupt a malicious action.
From the translator: The C & C domain was specifically registered, according to MalwareTech's tweeter, to stop or suspend the distribution of Malvari .
ANALYSIS OF THE HARVEST
The original mssecsvc.exe file runs another file called tasksche.exe. Then the domain switch is checked, after which the service mssecsvc2.0 is created. This service executes the mssecsvc.exe file with a different entry point than during the first launch. The second launch receives the IP address of the infected machine and tries to connect to the 445 TCP port of each IP address within the subnet. When the malware successfully connects to a remote machine, a connection is established and data is transferred. Apparently, somewhere in the process of this transfer, a known vulnerability is used, which was closed by updating MS 17-010. At the moment there is no complete understanding of SMB traffic, and under what conditions the malware can spread, using a security hole.
The taskche.exe file checks all drives, as well as folders and connected devices that are linked to letters, like 'C: /', 'D: /', etc. Malware then looks for files with the extensions that are listed in the program (and are listed below) and encrypts them using 2048-bit RSA encryption. While the files are encrypted, the Tor / folder is created where the tor.exe file is placed and the 9 dll files it uses. Additionally, taskdl.exe and taskse.exe are created. The first one deletes the temporary files, and the second launches @ wanadecryptor @ .exe, which shows the user a window asking him to pay. The @ wanadecryptor @ .exe file is responsible only for displaying the message. File encryption occurs in the background using tasksche.exe.
The tor.exe file is launched using @ wanadecryptor @ .exe. This new process starts connecting to Tor nodes. Thus, WannaCry maintains anonymity by passing all of its traffic through the Tor network.
As is typical for ransomware programs, the program also deletes any shadow copies on the victim's computer to make recovery even more difficult. This is done using WMIC.exe, vssadmin.exe and cmd.exe

WannaCry uses various ways to help its accomplishment. So it is used attrib.exe, to change the flag + h (hide), as well as icacls.exe, to give full rights to all users: “icacls. / grant Everyone: F / T / C / Q ".
It is noteworthy that the program has a modular architecture. It is likely that all executable files in it are written by different people. Potentially, this may mean that the structure of the program may allow different malicious scripts to be run.
After the encryption is complete, the malware displays a window requesting a ransom for the files. An interesting point is that the window is an executable file, not a picture, an HTA file, or a text file.

Victims should understand that there is no obligation for criminals to actually provide the keys for decryption after paying the ransom.
HOW TO FIGHT
To combat this malware there are two recommendations:
- Ensure that all computers using Windows have the latest update. At a minimum, update MS17-010.
- In accordance with the best practices, any organization in which SMB is publicly available (ports 139, 445) should immediately block incoming traffic.
Lesion indicators
File Names:
- d5e0e8694ddc0548d8e6b87c83d50f4ab85c1debadb106d6a6a794c3e746f4fa b.wnry
- 402751fa49e0cb68fe052cb3db87b05e71c1d950984d339940cf6b29409f2a7c r.wnry
- e18fdd912dfe5b45776e68d578c3af3547886cf1353d7086c8bee037436dff4b s.wnry
- 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79 taskdl.exe
- 2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d taskse.exe
- 97ebce49b14c46bebc9ec2448d00e1e397123b256e2be9eba5140688e7bc0ae6 t.wnry
- b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25 u.wnry
IP used:
- 188 [.] 166 [.] 23 [.] 127: 443
- 193 [.] 23 [.] 244 [.] 244: 443
- 2 [.] 3 [.] 69 [.] 209: 9001
- 146 [.] 0 [.] 32 [.] 144: 9001
- 50 [.] 7 [.] 161 [.] 218: 9001
- 217.79.179 [.] 77
- 128.31.0 [.] 39
- 213.61.66 [.] 116
- 212.47.232 [.] 237
- 81.30.158 [.] 223
- 79.172.193 [.] 32
- 89.45.235 [.] 21
- 38.229.72 [.] 16
- 188.138.33 [.] 220
File Encryption Extensions:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif, .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp, .pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif, .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .ARC, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx, .doc → Source
Source: https://habr.com/ru/post/328548/
All Articles