Ransomware day: Wana Decrypt0r mass infection
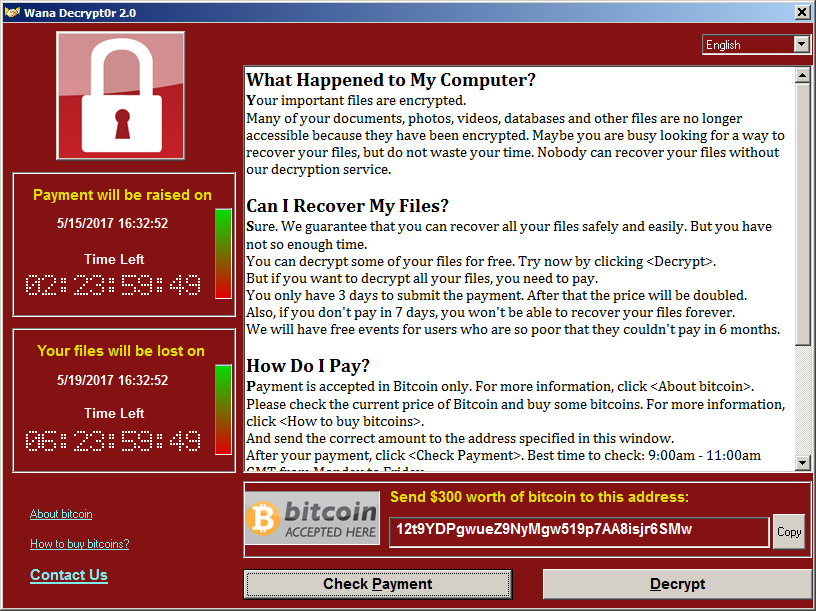
Over 60,000 computers have been attacked and infected by the extortion virus Wana Decrypt0r. The authors of Wana Decrypt0r use the ETERNALBLUE exploit created by NSA experts for the SMBv1 vulnerability (MS17-010) to deliver malicious code on Windows systems. The virus encrypts all files on the computer and requires a ransom - $ 300 in bitcoins. The payment is given for three days, then the amount is doubled.
MalwareHunterTeam, a cybersecurity expert team, claims that servers in Russia and Taiwan suffered the most as a result of the attack. Other countries were also hit: Great Britain, Spain, Italy, Germany, Portugal, Turkey, Ukraine, Kazakhstan, Indonesia, Vietnam, Japan and the Philippines.
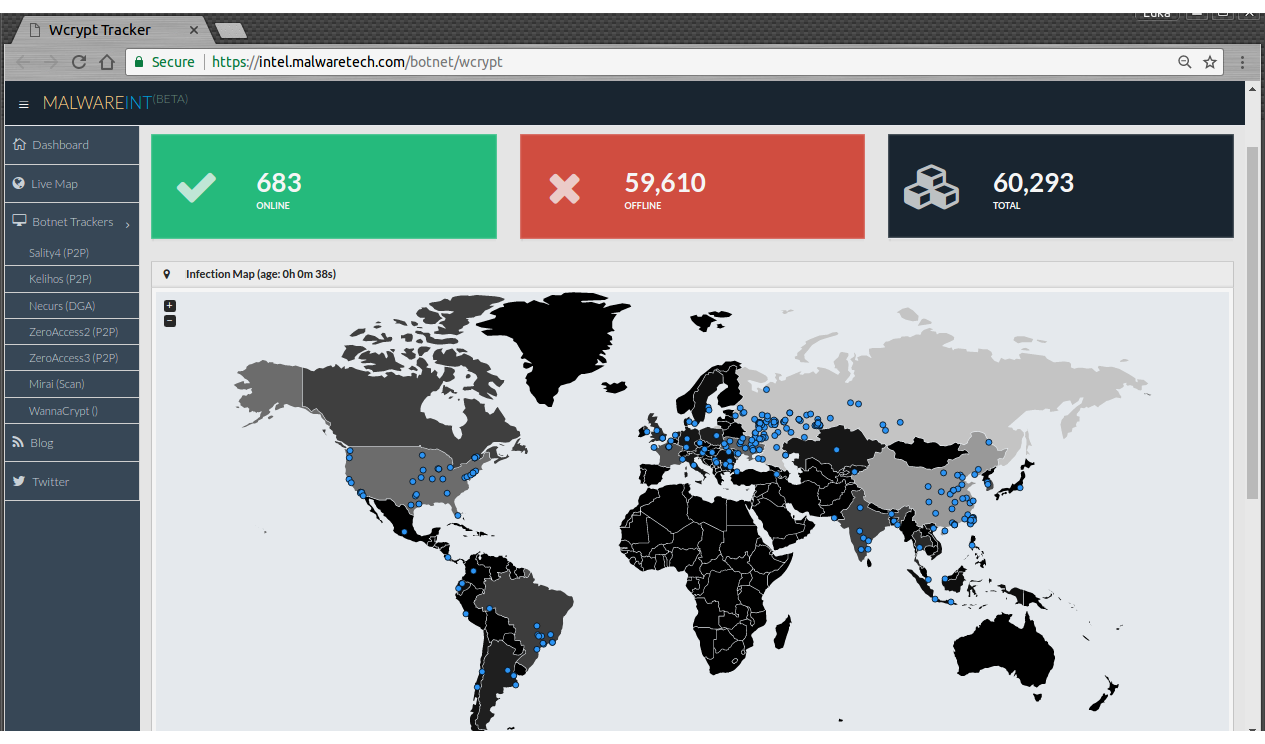
Microsoft closed the vulnerability in March. But, apparently, not everyone managed to update their systems. A real-time map of infections can be seen here: https://intel.malwaretech.com/botnet/wcrypt
Protective measures
As a means of protection, it is recommended to urgently update Windows systems (if you have not done this for some reason), use a means of detecting and blocking attacks — a firewall, etc.
For example, this can be done using the following commands:
netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=135 name="Block_TCP-135" netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=445 name="Block_TCP-445" ')
Source: https://habr.com/ru/post/328538/
All Articles