Cisco ACR 2017 Threat Research: Changes on the Other Side of the Barricade
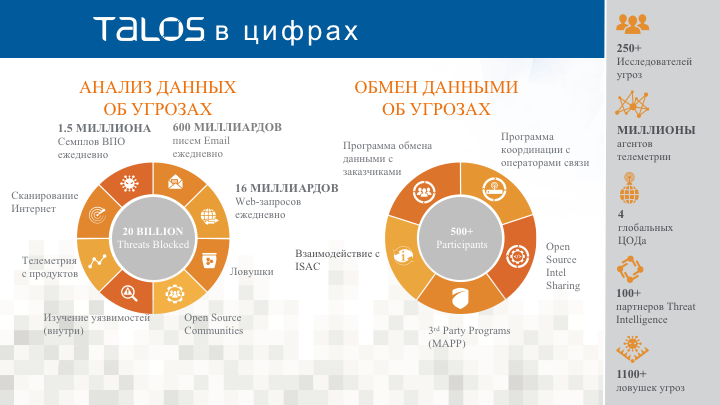
Cisco has a division of Talos , which deals with a wide range of research in the field of information security threats (the latest WannaCry research is also their work). Talos is based on a wealth of data collected around the world and analyzed around the clock:

In total, about 7 trillion threats fall in the field of view of Cisco Talos, which is 6 times the number of Google search queries for the same period of time. This amount of information is distributed across five divisions of Cisco Talos, which are engaged in:
')
Here we will talk about the activities of the last Cisco Talos department today. Over the past 10 years, Cisco has published its annual report, which highlights key trends on the other side of the barricades over the past year. The last 2016 was no exception - in February we presented our Cisco Annual Cybersecurity Report (Cisco ACR 2017) to the world, which, some time later, was translated into Russian. I will not retell in detail all 110 pages of this report, I’ll dwell on some interesting trends and conclusions that can be drawn from them.
For obvious reasons, any cyber attack requires prior intelligence. At this stage, hackers are looking for a vulnerable Internet infrastructure or weaknesses in the network, through which you can get access to users' computers and eventually penetrate the network of an organization. Third place in our ranking is fraud on Facebook, including falsified offers, polls and media content. Facebook's high positions of fraud in the annual and semi-annual ratings of the most common types of malware indicate the crucial role of social engineering in the implementation of a significant proportion of cyber attacks. There are 1.8 billion active Facebook accounts in the world, which quite naturally turns this social network into fertile ground for the activity of cybercriminals and other hackers seeking to deceive users.
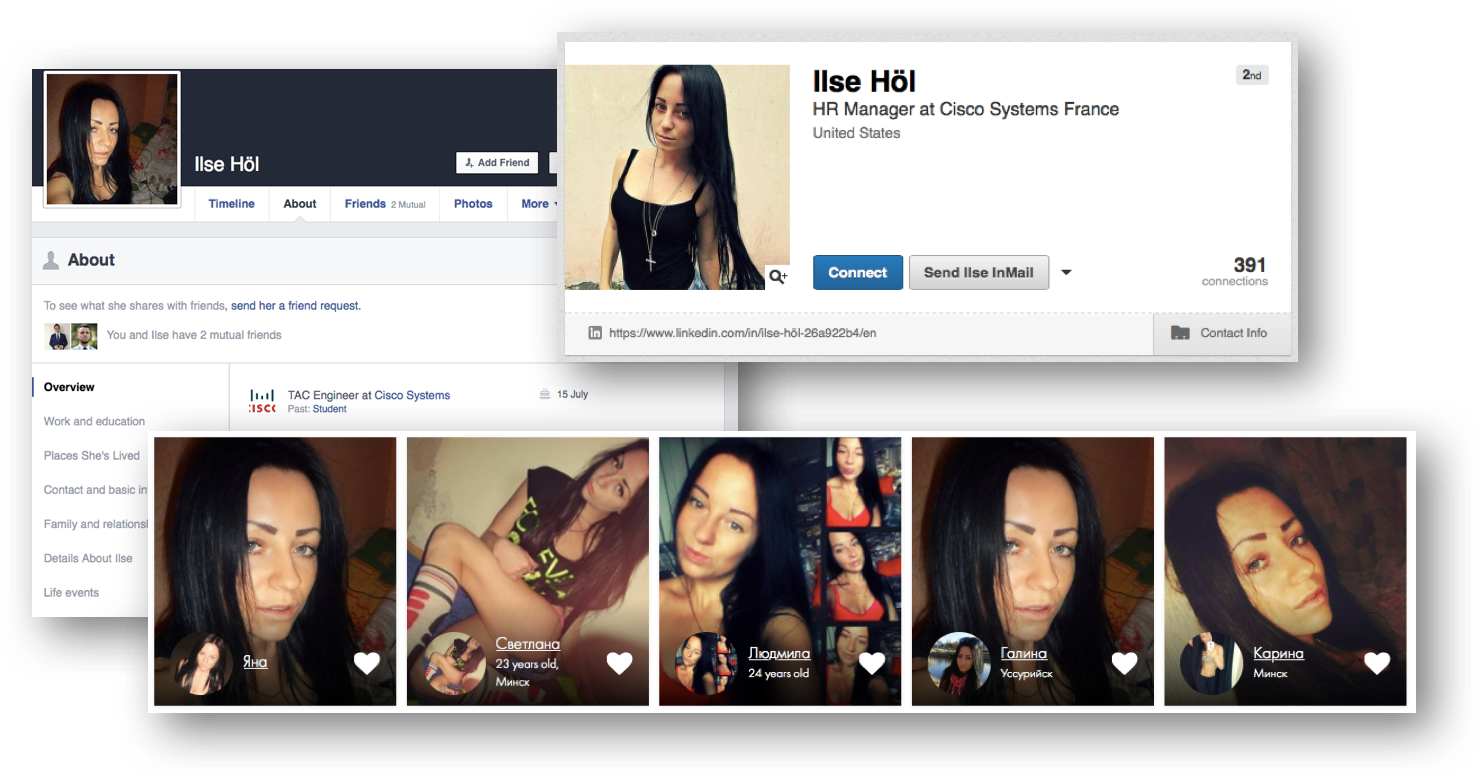
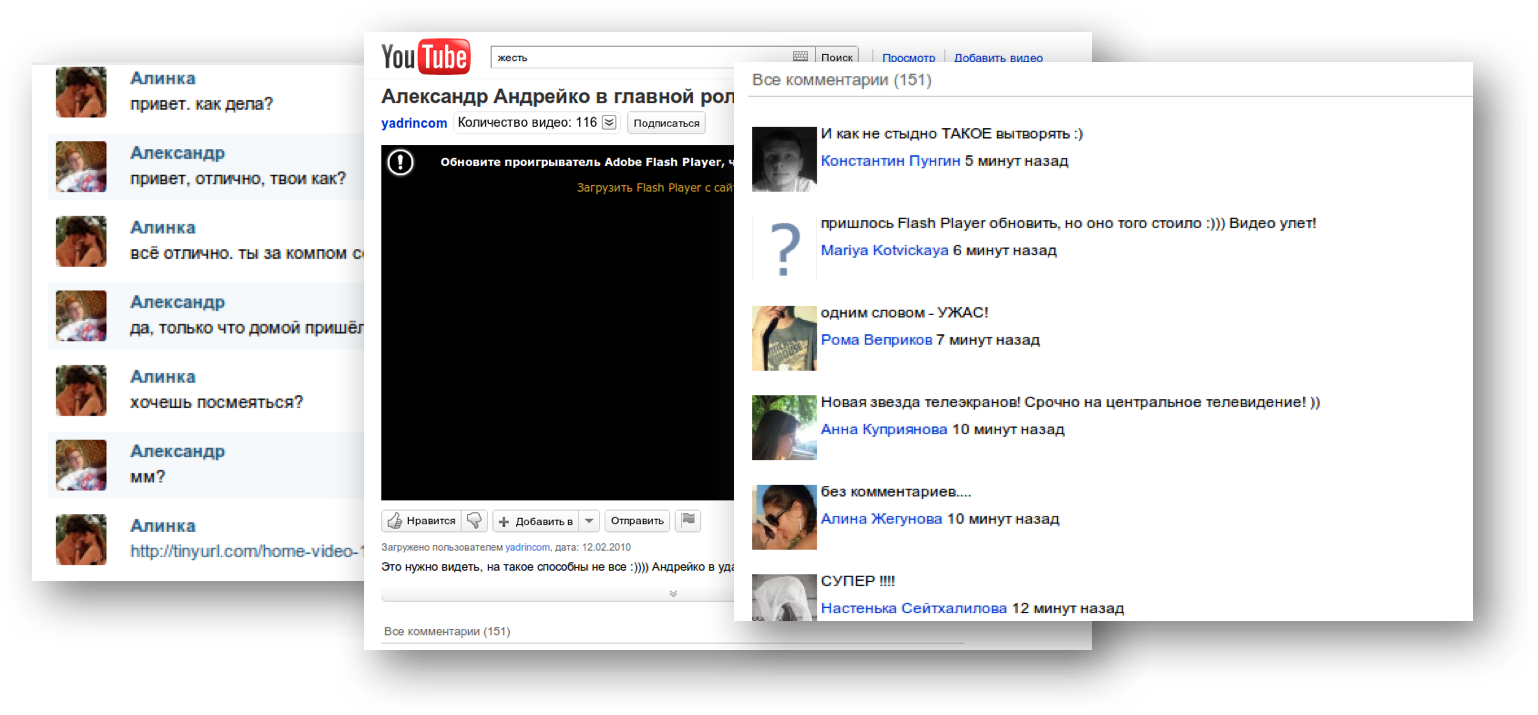
In order not to go far I will give an example of an attack personally on me. I once had a girlfriend on Facebook called Ilze Hall. The profile says that she works as a Cisco TAC technical support worker in Amsterdam. Quite a normal situation for Cisco - we have a lot of female engineers. But something embarrassed me on Ilze’s page and I decided to check it out through other social networks. In LinkedIn (even before the ban on this social network in Russia), it was also found. And also a Cisco employee. But only this time she worked in our personnel office in Paris. But this is impossible even in our liberal company.
Around the same time, the FindFace service became popular, allowing you to find a person’s page on the VKontakte social network using a photo. I uploaded a picture of Ilze there and got a lot of coincidences. Ilze from Amsterdam and Paris simultaneously turned out to be Karina from Minsk, Galina from Ussuriysk, and also Lyudmila, Svetlana and Yana (now she, by the way, on Facebook is called Amelina Tatiana).
About six months later, Alena Golubeva knocked on my door, the chat with which reminded me of the famous dialogue Hottabych from the Russian film of the same name, in which the main character tried to get acquainted with the bot named “Kisa”. On Alena Golubeva’s phrase “it’s so interesting with you,” I laughed and banned her, after having “broken through” through FindFace. It turned out that Alyona from Moscow also had “twin sisters” - Vasilina from Mogilev and Tatiana from Krasnodar. However, if I can still understand the use of identical clothes for twins, then the use of identical photographs defies logical explanation :)
If I inadvertently entered into this “friendly” relationship, I can assume that after some time I would get a link to the “cool” video, or even to the movie with me in the lead role with the postscript “and how ashamed SUCH get up :) ”. Curiosity could overcome suspicion (and what suspicions against “friends”) and I would click on the link sent. The key task of the attackers is to make the “friend” on the social network do something. The consequences are predictable - infecting a computer and establishing control over it, with all the ensuing consequences.
Addressing this threat requires an integrated approach — from training and regular user awareness to the use of Internet access control tools (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), the next generation ITU (for example, Cisco Firepower NGFW ), endpoint protection (for example, Cisco AMP for Endpoints ).
Our research has shown another clear shift: the set of methods used at the intelligence stage during the implementation of web attacks has changed. Software Adobe Flash for many years remained an attractive vector of web attacks, with which hackers repeatedly hacked and compromised systems. However, the amount of Flash content that is present on the Internet is still declining, and awareness of Flash vulnerabilities is increasing, and in the current environment large-scale hacks are hardly possible. Indeed, Adobe itself is gradually refusing to develop and support this platform and urges developers to move to new standards, such as HTML5. In many ways, this is why in 2016 the three leading exploit whales, namely Angler, Nuclear and Neutrino (and they used Flash as the main attack vector), suddenly disappeared from the scene, giving way to smaller players and novices.
At the same time, the number of threats directly targeting vulnerable browsers and plug-ins (plugin) is growing. This shift reflects a new trend: cybercriminals are increasingly using malicious advertising, since in modern conditions it is quite difficult to compromise a large number of users with the help of traditional vectors of web attacks. Cisco threat analysis specialists report large-scale distribution of malicious adware, including ad substitutes, various utilities and downloaders, as well as programs that change browser settings. We detected adware infection in 75% of companies surveyed recently as part of our project to study the problem of adware.

Exploit kits are distributed among victims in two main ways: through hacked sites and malicious advertising. Hackers place a link to the launch page of the exploit kit in a malicious advertisement, on a hacked website, or use an intermediate link (broker). Such links linking hacked websites and exploit kits servers are called gateways. The broker serves as an intermediary between the source referral link and the actual set of exploits that delivers the malicious code to users' devices. This tactic is becoming more popular as hackers tend to act faster to save space for their actions and avoid detection. Thanks to brokers, hackers move quickly between various malicious servers without changing the initial parameters of redirection. Since criminals do not need to constantly modify websites or malicious advertisements to launch an infection chain, operators of exploit kits have more time to invade.
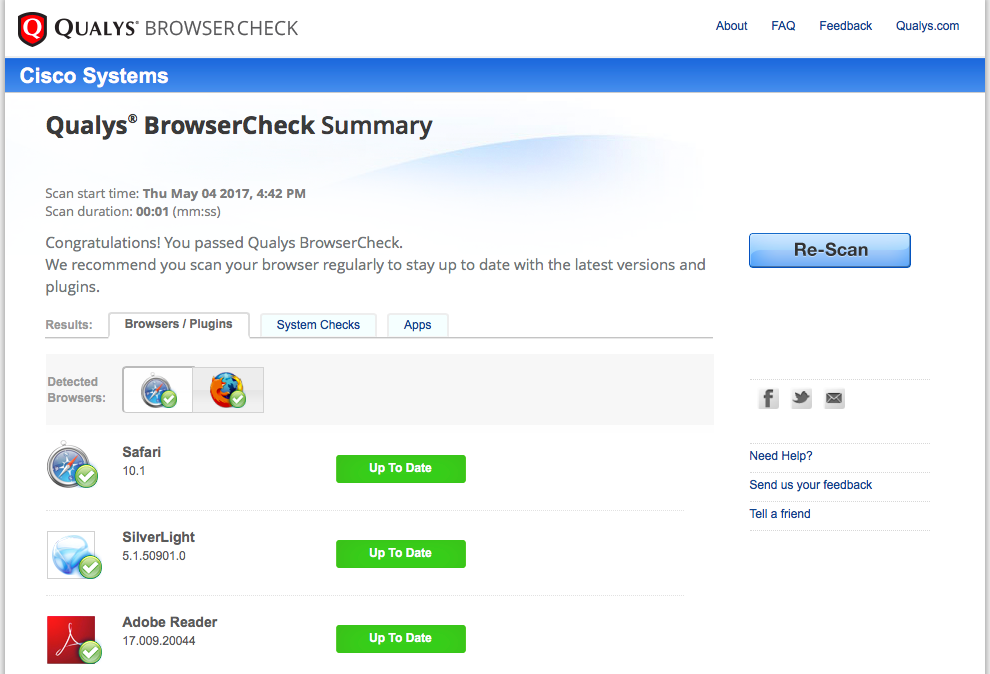
To combat this problem, not only endpoint protection tools are suitable, but also simpler and less expensive recommendations - disabling unused and regular updating of used plugins. With the help of various additional tools, you can control the presence of vulnerable or non-updated plug-ins, for example, with the help of Qualys Browser Check. The simplest measures mentioned above will significantly increase protection against common web threats and will deprive hackers of working space for the next stage in the attack chain - the stage of creating cyber-weapons.
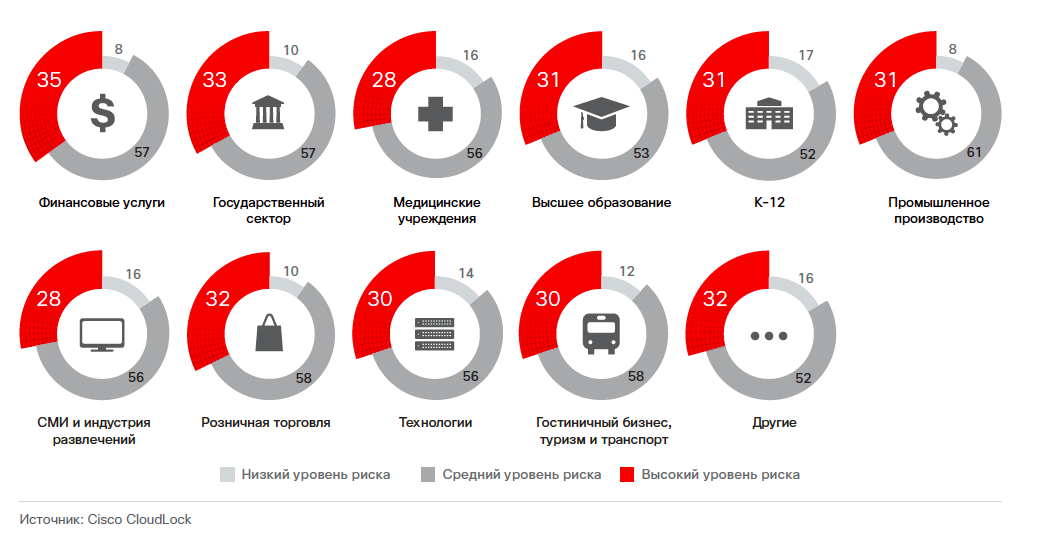
Another important trend that we noted in our report is the growing number of threats from third-party cloud applications. When they are implemented, the perimeter of the organization’s security expands and covers the alien infrastructure of the company. At the same time, the border is blurred rather quickly, as employees introduce a wide variety of cloud applications into the work environment. Such applications help to increase productivity and stay connected during the working day. However, these same applications form a shadow IT layer that represents a threat to the security of the organization. The shadow layer is in direct contact with the corporate infrastructure and allows you to freely exchange data with the corporate cloud and SaaS platforms, for which it is enough to obtain permission from the user to access via the OAuth protocol. Specialists of CloudLock , which provides cloud security services (currently part of Cisco), track the growth in the number of third-party cloud applications in a group of 900 organizations from various industries.
At the beginning of 2016, about 129,000 unique applications were discovered. By the end of October, this figure had increased to 222,000. In total, since 2014, the number of applications has increased approximately 11 times. CloudLock has developed a CARI (Cloud Application Risk Index) classification system that helps security professionals assess the level of threat from a cloud application used in a corporate environment. According to the classification results, 27% of these applications were classified as high hazard.
To control access to cloud environments, you need not only to use next-generation firewalls (for example, Cisco Firepower NGFW ) and Internet access control tools (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), but also specialized solutions of the Cloud Access Security Broker ( CASB), which can connect to external SaaS platforms and control access to them even from outside the corporate network, from home, from personal mobile devices. In the same case, when it comes to using cloud IaaS and PaaS platforms, you can use appropriate virtualized security solutions to control them (for example, Cisco vNGIPS , Cisco StealthWatch Cloud License, and others).
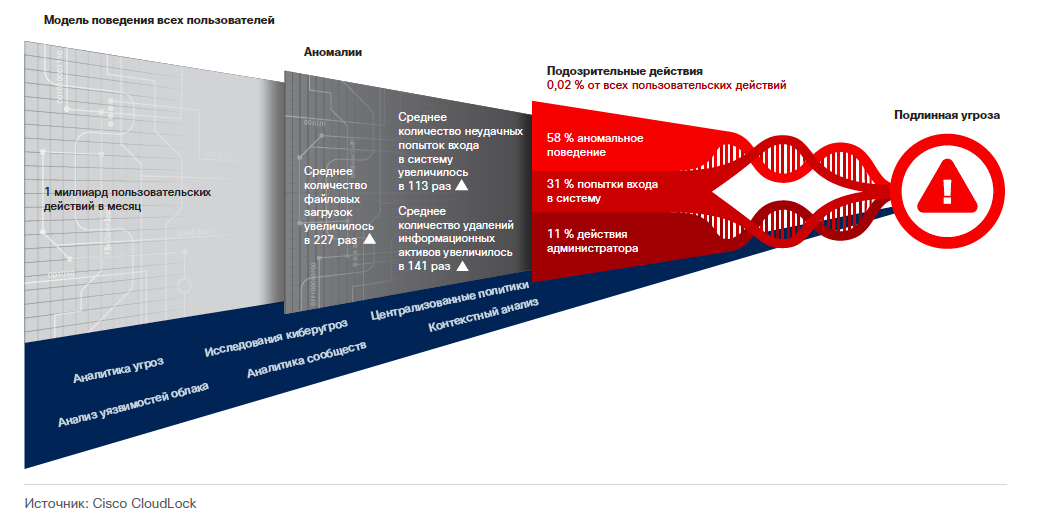
To identify suspicious behavior of users and objects (including third-party cloud applications) within the framework of corporate SaaS platforms, security specialists should analyze the billions of natural, legitimate operations carried out in the organization's information environment in order to determine normal behavior patterns. These models are used as a background for searching for behavioral anomalies. Having found suspicious activity, it is necessary to mutually compare the corresponding operations in order to determine from where the real threat can emanate that requires further analysis. According to Cisco, only 1 out of 5000 (0.02%) actions performed by users in cloud applications are suspicious. And the task of security experts, of course, is to discover this one action. It is necessary to break through the noise of countless alerts about potential security problems and focus on combating real threats. This problem can be solved only in one way - through automation. To solve this problem several years ago we bought the European company Cognitive Security, whose solution, Cognitive Threat Analytics (CTA), is used to automate the search for suspicious activity in web logs.
Good old spam continues to be one of the problems for any user. The results of our research indicate an increase in the global volume of spam at the expense of large and profitable botnets that send such letters. About two thirds of email traffic (65%) is spam. At the same time, spam is harmful not only because it distracts from the main activity. According to data collected by Cisco threat analysis experts, malicious emails accounted for 8 to 10% of global spam in 2016. In addition, the percentage of spam with malicious attachments is increasing, with hackers apparently experimenting with various file formats in search of the most effective means for implementing attacks.
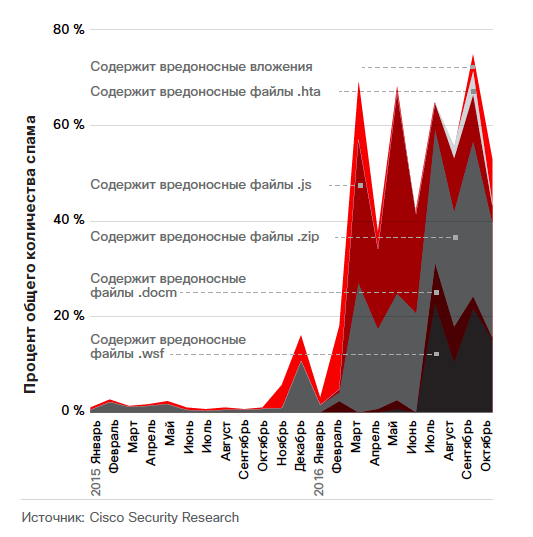
Analysis of CBL data (a blacklist based on DNS containing suspicious addresses from which spam is sent) for 10 years showed that the volume of spam in 2016 is close to the record high in 2010.
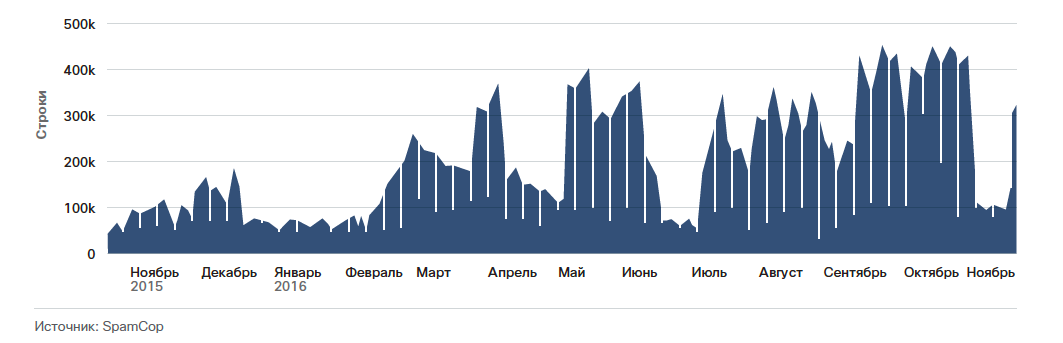
In the past few years, the volume of spam has remained relatively small, which can be explained by the emergence of new technologies for protection against spam and the resonant shutdown of spam botnets. According to our experts, the recent increase in spam has been linked to the activity of the Necurs botnet. Necurs is the main distribution vector of the ransomware of the Locky family. Through this same botnet spreads the banking Trojan Dridex and other similar programs. Many IP addresses from which spam was sent by the Necurs command were infected more than 2 years ago. Necurs hides its real scale, using only certain subsets of infected hosts to send spam. As a rule, a botnet exploits an infected host for 2–3 days, followed by a break of 2-3 weeks. This pattern of behavior complicates the fight against spam attacks. Security specialists find and disinfect one of the infected hosts, believing that they have solved the problem, but the owners of the Necurs botnet are just waiting for the right moment to launch another attack.
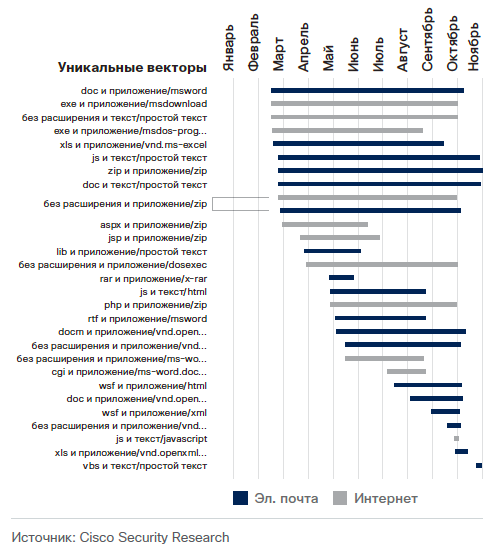
The infrastructure of one of the most popular malware of the past year, Locky, is as follows. For visualization, we used the Cisco OpenDNS Investigate service and the OpenGraphitti visualization library . Red nodes are known blacklisted malicious domains; gray nodes are good domains; greens are popular and good domains, orange ones are IP addresses, and blue nodes are file hashes. Pulsation displays the movement of DNS traffic between nodes.
In this case, the attackers are trying in every way to increase the likelihood of successful penetration and infection, and for this they use several vectors at once to attack, constantly combining and expanding them. For example, with the malicious code Locky, the visualization of the infrastructure of which is shown above, this distribution of attack vectors is as follows:
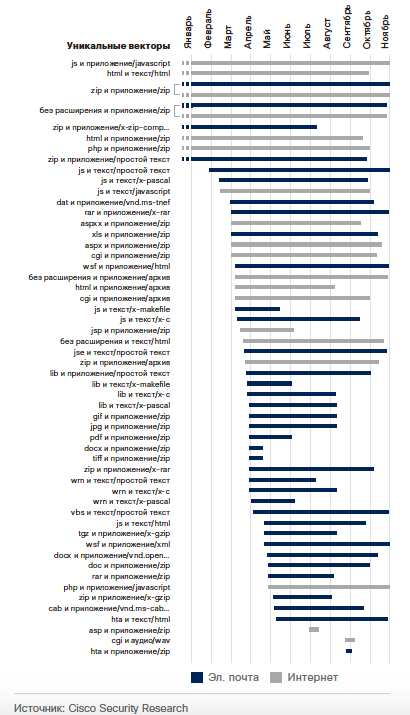
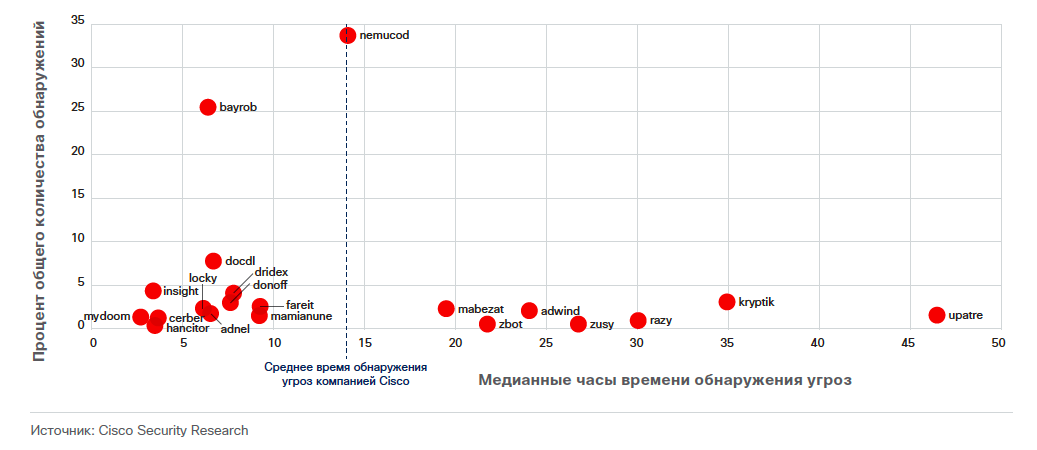
And Nemucod has even more unique vectors:
All this leads to the fact that the average time of detection of malicious programs varies from several hours (for well-known campaigns) to several days.
Combating such a tactic by an attacker requires not only the use of effective e-mail protection tools (for example, Cisco E-mail Security Appliance ), but also Threat Intelligence technologies (for example, Cisco OpenDNS , Cisco AMP Threat Grid, and others) that allow you to quickly receive information about dynamically changing threat landscape — use their IP addresses, domains, autonomous systems, and block them using traditional network security tools — firewalls (for example, Cisco ASA or Cisco Firepower NGFW ), intrusion prevention systems (for example, Cisco NGIPS ), Internet access control systems (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), endpoint protection systems (for example, Cisco AMP for Endpoints ), etc.
Probably, these are all key points that I would like to highlight in the brief section on threats to our annual report on cybersecurity, Cisco Annual Cybersecurity Report 2017, which can be freely downloaded from our website in Russian. But our report is not limited to analyzing only the behavior of the attackers. We are actively exploring the behavior of the defender and in the next article (if again there is no sudden epidemic that we will have to write about, as we did for WannaCry ), we will look at interesting aspects related to cybersecurity. In this case, we will operate only with Russian statistics. Yes, yes, we have not only world statistics, but also local statistics, which show differences in the behavior of advocates throughout the world and in our country. But about this in the next article.
- 90 billion DNS queries daily
- 18.5 billion files daily, of which 1.5 million are malicious (by the way, Kaspersky Lab 2 million malware detects weekly )
- 16 billion Web requests (URLs) daily
- 600 billion emails daily.

In total, about 7 trillion threats fall in the field of view of Cisco Talos, which is 6 times the number of Google search queries for the same period of time. This amount of information is distributed across five divisions of Cisco Talos, which are engaged in:
')
- analysis of threats (threat intelligence) and creation of indicators of compromise in various formats (attack signatures, black lists of malicious domains, categories and URL reputation levels, malicious file hashes, etc.)
- research into the detection of these threats
- development of “engines” that solve various tasks in the field of threat detection (this unit, in particular, is developing and supporting Snort)
- search and research vulnerabilities
- publication of the results of their research.

Here we will talk about the activities of the last Cisco Talos department today. Over the past 10 years, Cisco has published its annual report, which highlights key trends on the other side of the barricades over the past year. The last 2016 was no exception - in February we presented our Cisco Annual Cybersecurity Report (Cisco ACR 2017) to the world, which, some time later, was translated into Russian. I will not retell in detail all 110 pages of this report, I’ll dwell on some interesting trends and conclusions that can be drawn from them.
For obvious reasons, any cyber attack requires prior intelligence. At this stage, hackers are looking for a vulnerable Internet infrastructure or weaknesses in the network, through which you can get access to users' computers and eventually penetrate the network of an organization. Third place in our ranking is fraud on Facebook, including falsified offers, polls and media content. Facebook's high positions of fraud in the annual and semi-annual ratings of the most common types of malware indicate the crucial role of social engineering in the implementation of a significant proportion of cyber attacks. There are 1.8 billion active Facebook accounts in the world, which quite naturally turns this social network into fertile ground for the activity of cybercriminals and other hackers seeking to deceive users.
In order not to go far I will give an example of an attack personally on me. I once had a girlfriend on Facebook called Ilze Hall. The profile says that she works as a Cisco TAC technical support worker in Amsterdam. Quite a normal situation for Cisco - we have a lot of female engineers. But something embarrassed me on Ilze’s page and I decided to check it out through other social networks. In LinkedIn (even before the ban on this social network in Russia), it was also found. And also a Cisco employee. But only this time she worked in our personnel office in Paris. But this is impossible even in our liberal company.

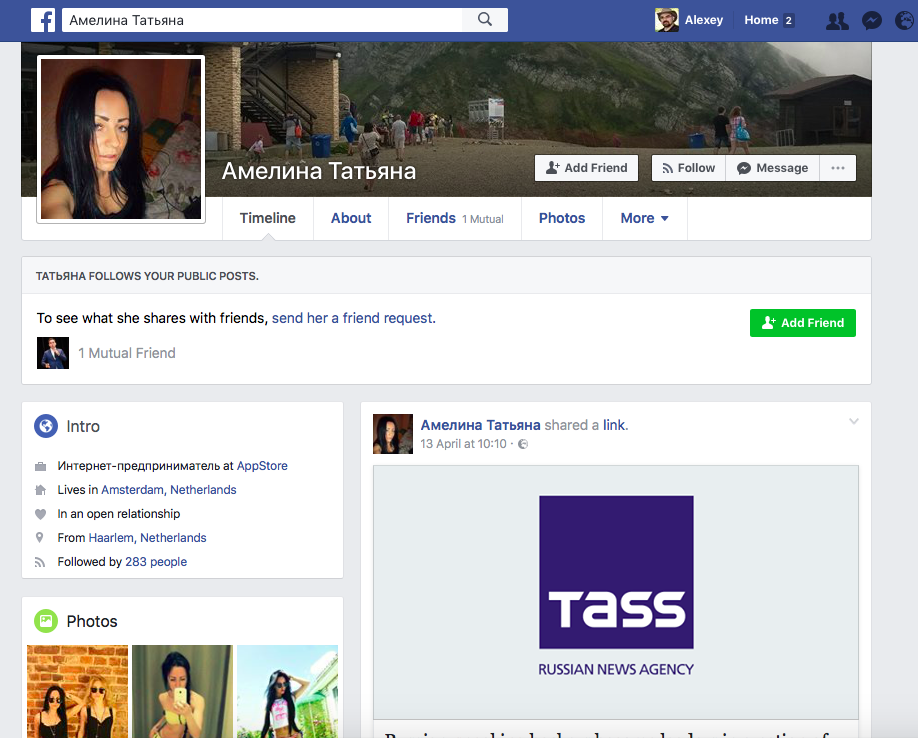
Around the same time, the FindFace service became popular, allowing you to find a person’s page on the VKontakte social network using a photo. I uploaded a picture of Ilze there and got a lot of coincidences. Ilze from Amsterdam and Paris simultaneously turned out to be Karina from Minsk, Galina from Ussuriysk, and also Lyudmila, Svetlana and Yana (now she, by the way, on Facebook is called Amelina Tatiana).

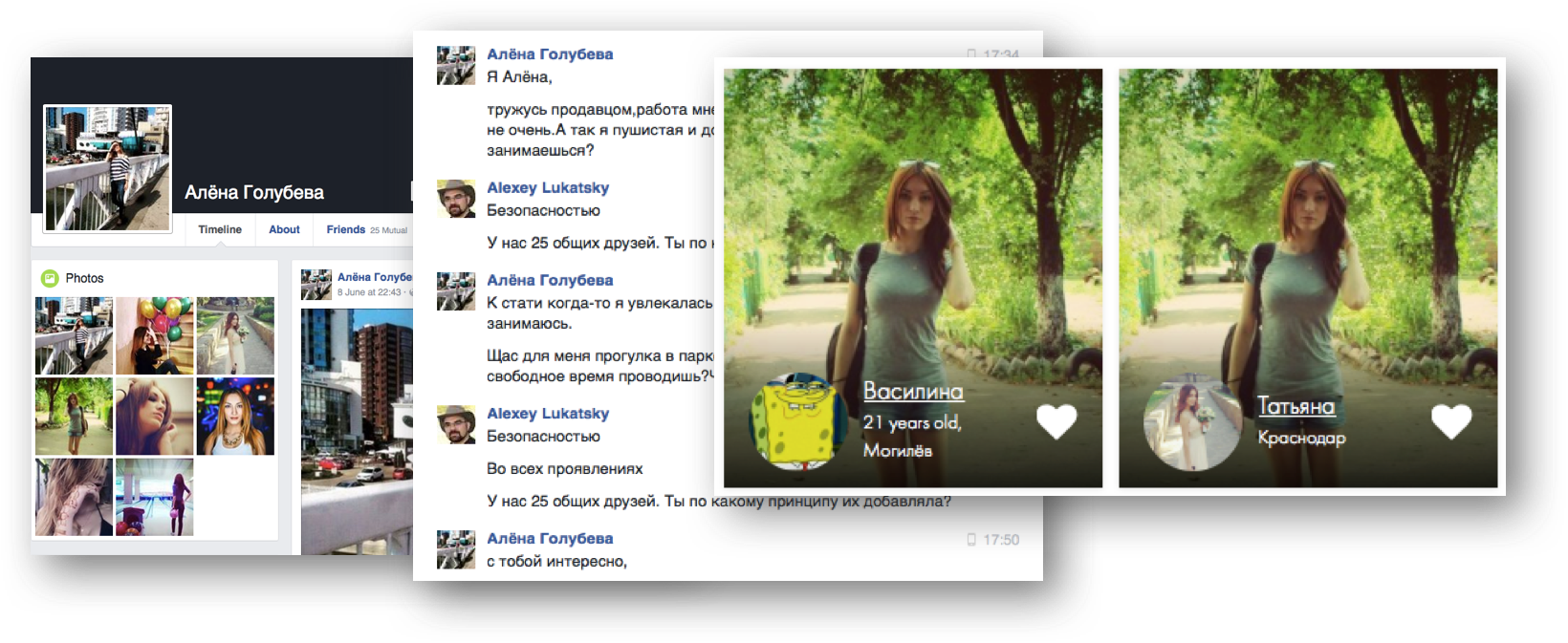
About six months later, Alena Golubeva knocked on my door, the chat with which reminded me of the famous dialogue Hottabych from the Russian film of the same name, in which the main character tried to get acquainted with the bot named “Kisa”. On Alena Golubeva’s phrase “it’s so interesting with you,” I laughed and banned her, after having “broken through” through FindFace. It turned out that Alyona from Moscow also had “twin sisters” - Vasilina from Mogilev and Tatiana from Krasnodar. However, if I can still understand the use of identical clothes for twins, then the use of identical photographs defies logical explanation :)

If I inadvertently entered into this “friendly” relationship, I can assume that after some time I would get a link to the “cool” video, or even to the movie with me in the lead role with the postscript “and how ashamed SUCH get up :) ”. Curiosity could overcome suspicion (and what suspicions against “friends”) and I would click on the link sent. The key task of the attackers is to make the “friend” on the social network do something. The consequences are predictable - infecting a computer and establishing control over it, with all the ensuing consequences.

Addressing this threat requires an integrated approach — from training and regular user awareness to the use of Internet access control tools (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), the next generation ITU (for example, Cisco Firepower NGFW ), endpoint protection (for example, Cisco AMP for Endpoints ).
Our research has shown another clear shift: the set of methods used at the intelligence stage during the implementation of web attacks has changed. Software Adobe Flash for many years remained an attractive vector of web attacks, with which hackers repeatedly hacked and compromised systems. However, the amount of Flash content that is present on the Internet is still declining, and awareness of Flash vulnerabilities is increasing, and in the current environment large-scale hacks are hardly possible. Indeed, Adobe itself is gradually refusing to develop and support this platform and urges developers to move to new standards, such as HTML5. In many ways, this is why in 2016 the three leading exploit whales, namely Angler, Nuclear and Neutrino (and they used Flash as the main attack vector), suddenly disappeared from the scene, giving way to smaller players and novices.
At the same time, the number of threats directly targeting vulnerable browsers and plug-ins (plugin) is growing. This shift reflects a new trend: cybercriminals are increasingly using malicious advertising, since in modern conditions it is quite difficult to compromise a large number of users with the help of traditional vectors of web attacks. Cisco threat analysis specialists report large-scale distribution of malicious adware, including ad substitutes, various utilities and downloaders, as well as programs that change browser settings. We detected adware infection in 75% of companies surveyed recently as part of our project to study the problem of adware.

Exploit kits are distributed among victims in two main ways: through hacked sites and malicious advertising. Hackers place a link to the launch page of the exploit kit in a malicious advertisement, on a hacked website, or use an intermediate link (broker). Such links linking hacked websites and exploit kits servers are called gateways. The broker serves as an intermediary between the source referral link and the actual set of exploits that delivers the malicious code to users' devices. This tactic is becoming more popular as hackers tend to act faster to save space for their actions and avoid detection. Thanks to brokers, hackers move quickly between various malicious servers without changing the initial parameters of redirection. Since criminals do not need to constantly modify websites or malicious advertisements to launch an infection chain, operators of exploit kits have more time to invade.
To combat this problem, not only endpoint protection tools are suitable, but also simpler and less expensive recommendations - disabling unused and regular updating of used plugins. With the help of various additional tools, you can control the presence of vulnerable or non-updated plug-ins, for example, with the help of Qualys Browser Check. The simplest measures mentioned above will significantly increase protection against common web threats and will deprive hackers of working space for the next stage in the attack chain - the stage of creating cyber-weapons.

Another important trend that we noted in our report is the growing number of threats from third-party cloud applications. When they are implemented, the perimeter of the organization’s security expands and covers the alien infrastructure of the company. At the same time, the border is blurred rather quickly, as employees introduce a wide variety of cloud applications into the work environment. Such applications help to increase productivity and stay connected during the working day. However, these same applications form a shadow IT layer that represents a threat to the security of the organization. The shadow layer is in direct contact with the corporate infrastructure and allows you to freely exchange data with the corporate cloud and SaaS platforms, for which it is enough to obtain permission from the user to access via the OAuth protocol. Specialists of CloudLock , which provides cloud security services (currently part of Cisco), track the growth in the number of third-party cloud applications in a group of 900 organizations from various industries.
At the beginning of 2016, about 129,000 unique applications were discovered. By the end of October, this figure had increased to 222,000. In total, since 2014, the number of applications has increased approximately 11 times. CloudLock has developed a CARI (Cloud Application Risk Index) classification system that helps security professionals assess the level of threat from a cloud application used in a corporate environment. According to the classification results, 27% of these applications were classified as high hazard.

To control access to cloud environments, you need not only to use next-generation firewalls (for example, Cisco Firepower NGFW ) and Internet access control tools (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), but also specialized solutions of the Cloud Access Security Broker ( CASB), which can connect to external SaaS platforms and control access to them even from outside the corporate network, from home, from personal mobile devices. In the same case, when it comes to using cloud IaaS and PaaS platforms, you can use appropriate virtualized security solutions to control them (for example, Cisco vNGIPS , Cisco StealthWatch Cloud License, and others).
To identify suspicious behavior of users and objects (including third-party cloud applications) within the framework of corporate SaaS platforms, security specialists should analyze the billions of natural, legitimate operations carried out in the organization's information environment in order to determine normal behavior patterns. These models are used as a background for searching for behavioral anomalies. Having found suspicious activity, it is necessary to mutually compare the corresponding operations in order to determine from where the real threat can emanate that requires further analysis. According to Cisco, only 1 out of 5000 (0.02%) actions performed by users in cloud applications are suspicious. And the task of security experts, of course, is to discover this one action. It is necessary to break through the noise of countless alerts about potential security problems and focus on combating real threats. This problem can be solved only in one way - through automation. To solve this problem several years ago we bought the European company Cognitive Security, whose solution, Cognitive Threat Analytics (CTA), is used to automate the search for suspicious activity in web logs.

Good old spam continues to be one of the problems for any user. The results of our research indicate an increase in the global volume of spam at the expense of large and profitable botnets that send such letters. About two thirds of email traffic (65%) is spam. At the same time, spam is harmful not only because it distracts from the main activity. According to data collected by Cisco threat analysis experts, malicious emails accounted for 8 to 10% of global spam in 2016. In addition, the percentage of spam with malicious attachments is increasing, with hackers apparently experimenting with various file formats in search of the most effective means for implementing attacks.

Analysis of CBL data (a blacklist based on DNS containing suspicious addresses from which spam is sent) for 10 years showed that the volume of spam in 2016 is close to the record high in 2010.

In the past few years, the volume of spam has remained relatively small, which can be explained by the emergence of new technologies for protection against spam and the resonant shutdown of spam botnets. According to our experts, the recent increase in spam has been linked to the activity of the Necurs botnet. Necurs is the main distribution vector of the ransomware of the Locky family. Through this same botnet spreads the banking Trojan Dridex and other similar programs. Many IP addresses from which spam was sent by the Necurs command were infected more than 2 years ago. Necurs hides its real scale, using only certain subsets of infected hosts to send spam. As a rule, a botnet exploits an infected host for 2–3 days, followed by a break of 2-3 weeks. This pattern of behavior complicates the fight against spam attacks. Security specialists find and disinfect one of the infected hosts, believing that they have solved the problem, but the owners of the Necurs botnet are just waiting for the right moment to launch another attack.
The infrastructure of one of the most popular malware of the past year, Locky, is as follows. For visualization, we used the Cisco OpenDNS Investigate service and the OpenGraphitti visualization library . Red nodes are known blacklisted malicious domains; gray nodes are good domains; greens are popular and good domains, orange ones are IP addresses, and blue nodes are file hashes. Pulsation displays the movement of DNS traffic between nodes.
In this case, the attackers are trying in every way to increase the likelihood of successful penetration and infection, and for this they use several vectors at once to attack, constantly combining and expanding them. For example, with the malicious code Locky, the visualization of the infrastructure of which is shown above, this distribution of attack vectors is as follows:

And Nemucod has even more unique vectors:

All this leads to the fact that the average time of detection of malicious programs varies from several hours (for well-known campaigns) to several days.

Combating such a tactic by an attacker requires not only the use of effective e-mail protection tools (for example, Cisco E-mail Security Appliance ), but also Threat Intelligence technologies (for example, Cisco OpenDNS , Cisco AMP Threat Grid, and others) that allow you to quickly receive information about dynamically changing threat landscape — use their IP addresses, domains, autonomous systems, and block them using traditional network security tools — firewalls (for example, Cisco ASA or Cisco Firepower NGFW ), intrusion prevention systems (for example, Cisco NGIPS ), Internet access control systems (for example, Cisco Web Security Appliance or Cisco OpenDNS Umbrella ), endpoint protection systems (for example, Cisco AMP for Endpoints ), etc.
Probably, these are all key points that I would like to highlight in the brief section on threats to our annual report on cybersecurity, Cisco Annual Cybersecurity Report 2017, which can be freely downloaded from our website in Russian. But our report is not limited to analyzing only the behavior of the attackers. We are actively exploring the behavior of the defender and in the next article (if again there is no sudden epidemic that we will have to write about, as we did for WannaCry ), we will look at interesting aspects related to cybersecurity. In this case, we will operate only with Russian statistics. Yes, yes, we have not only world statistics, but also local statistics, which show differences in the behavior of advocates throughout the world and in our country. But about this in the next article.
Source: https://habr.com/ru/post/328502/
All Articles