DNA Security - Security built into the network infrastructure
Introduction:
Considering security embedded in the network infrastructure and speaking of such concepts as DNA, we mean something very deeply integrated and embedded in the essence itself, in the case under consideration in the essence of the network. But we begin in principle with the very concept of DNA and how Cisco sees it for the network as a whole and what role information security plays here.
DNA concept:
')
DNA is a new Cisco approach to infrastructure, which brings with it the capabilities to provide technologies and approaches that can give modern business the advantages and drivers that a modern enterprise needs to effectively conduct business in the Digitalization Era.
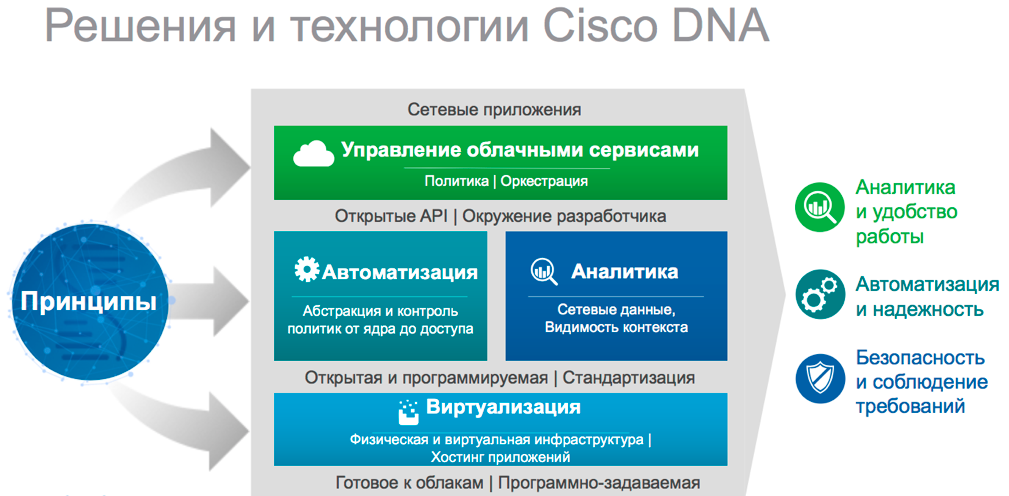
Figure 1
The integral components of this approach are the programmability of the infrastructure, the possibilities for flexible automation of operations, the rapid introduction of services, abstraction, and the reduction of operating costs for both supporting current infrastructure and introducing innovations and services. The network must be flexible, and in this we can use the capabilities of the SDN architecture, APIs that give flexibility in the integration of systems, quick adaptation to their system infrastructure needs.
Virtualization, supplemented by software interfaces, provides flexible possibilities for the deployment of ready-made infrastructures and their rapid replication, modification and adaptation to changing business needs.
Analytics , a smart modern network should be not only a tool for deploying services and ensuring business operations, but also a source of important information and analytics that can provide real leverage for decision making and adjustments to business processes.
Deep integration of cloud services, applications and infrastructure with services deployed at the customer’s site blurs the line and provides transparent and convenient mechanisms for the development and implementation of hybrid infrastructures, which is one of the key requirements of modern digital business.
Due to the risks currently experienced from growing cyber threats that pose real risks to businesses, especially in an era when we are increasingly dependent on telecommunications, the Internet of things and online operations, greater attention is required to be paid to information security and this DNA concept includes information security tools and mechanisms. as a fundamental component of the entire infrastructure. Whatever we implement, which service is not launched - it must be deployed, operated and maintained safely and this information security process must be as automated as possible, thereby not reducing, but only increasing the efficiency of the business and its processes. The main pillars of this concept are shown in Figure 1.
Network as a security tool:
At the current time, the classic approach to segmentation and network access creates many gaps in the infrastructure, lack of deep control and visibility within the infrastructure. We cannot fully see what is happening inside our network infrastructure, in fact we are blind to the activities that occur in the protected segments of our network infrastructures, because the only way to get detailed information on network activities is to pass these connections through specialized filtering or analytics as firewalls (ITUs), intrusion prevention systems (IPS), and other devices leading deep packet analysis and protocol inspection. Thus, if we take the vast majority of networks where such solutions are located in their minimum, namely, on the perimeter of access to external networks and access to the data center - we have no picture of what is happening inside our campus network and inside the data center. Inside the network, active scanning, compromise, denial of service attacks, attempts to output distributed data with their prior collection, etc., can occur, but we will be blind to this. Installing an ITU or IPS on each floor switch is an extremely difficult task for the financial component, and the performance required for deep packet analysis required for the access / distribution / core level is very, very expensive. As a result, we detect an attack only when the network traffic reaches the control point, for example, the network perimeter, unfortunately all the underlying infrastructure at that time may already be compromised. Our visibility in classical segmentation will be limited and the difference in real connections and visible ones will somehow remind us of the illustration from Figure 2.
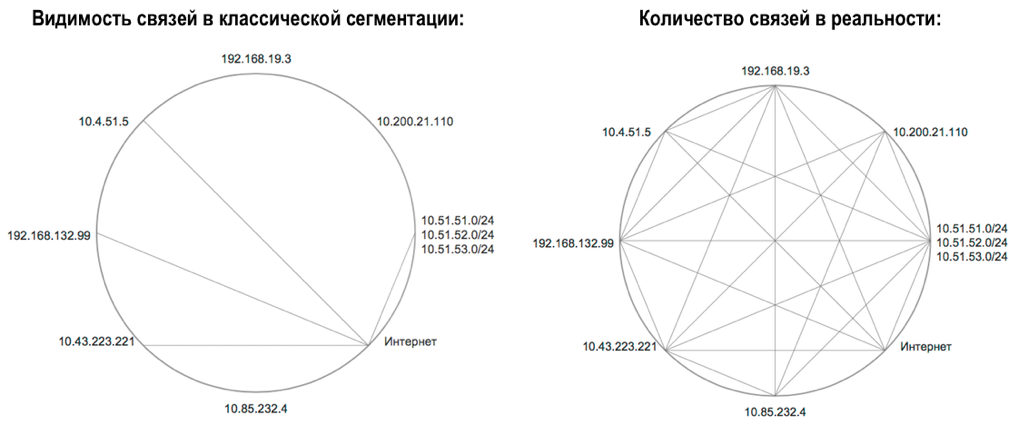
Figure 2
Imagine that you can see and constantly monitor all transactions within the network and have their full history, but what will this give us in our base?
These and other questions are answered by DNA Security's integrated network security concept.
A modern intellectual network of Cisco digital enterprise can be an effective means of information security and flexibly integrate into existing enterprise information security systems by exchanging with it the whole wealth of existing knowledge about the connected infrastructure and activities in it. After all, the Cisco intelligent network has a large set of knowledge, such as:
Thus, the network is transformed not only into a full-fledged sensor, but also into an effective means of monitoring information security.
The key components to achieve the most from our network infrastructure and turn it into an effective information security tool are the Cisco Identity Services Engine with the Cisco Trustsec security architecture and the Cisco StealthWatch, see Figure # 3.
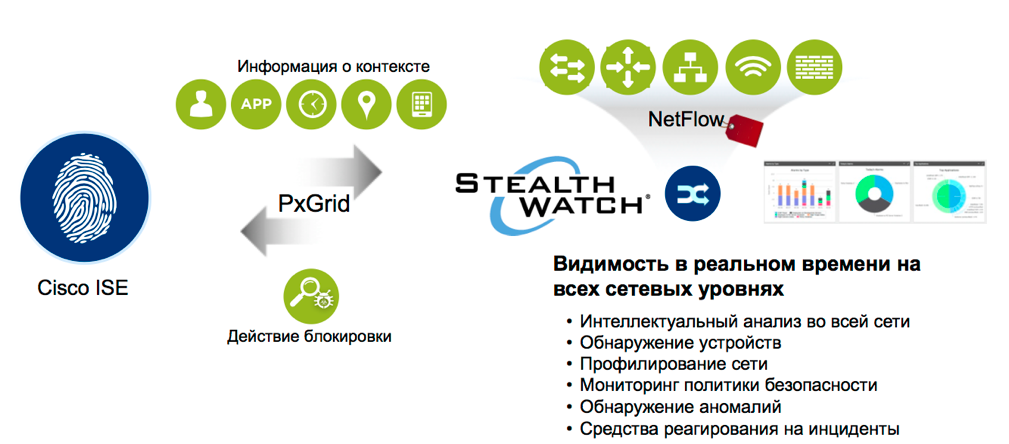
Figure 3
Network as a means of control:
The core of the architecture is the network access control and accounting system - the Cisco Identity Services Engine (ISE) whose tasks include:

Figure 4
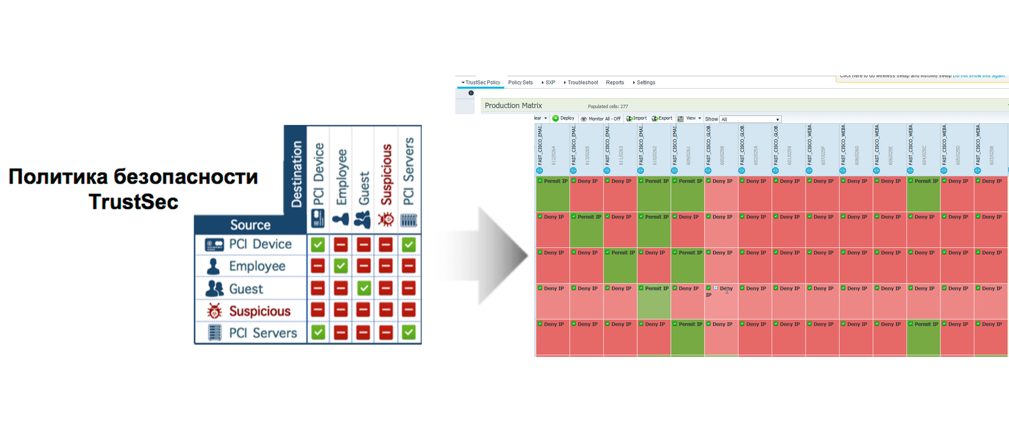
Figure 5
Applying the segmentation of the software-defined segmentation of Trustsec to our devices / users on the network is assigned an SGT tag, depending on their functional role in the network defined by us (the business). Having an access matrix in ISE, we clearly indicate which roles (SGT tags) can have access to which roles (SGT tags) and how this access should be in a simple and clear interface of the matrix view. As soon as the device, connecting to the network, receives this label, all associated access policies from the specified matrix are automatically applied to all transactions directed from the source label to the assignment labels of other functional roles in the enterprise network.
As a result of ISE integration into the infrastructure, we understand exactly who, what (see Figure 6) and with what rights to connect to our network, we performed automatic role-segmentation of our network and now the issue of attribution of gray IP addresses in the past becomes resolved - we received an exact picture of who / where / when / how to connect to the network and with what rights. Next, consider how we get a deeper look at what is happening in our protected segments and see what was hidden for us in the past.
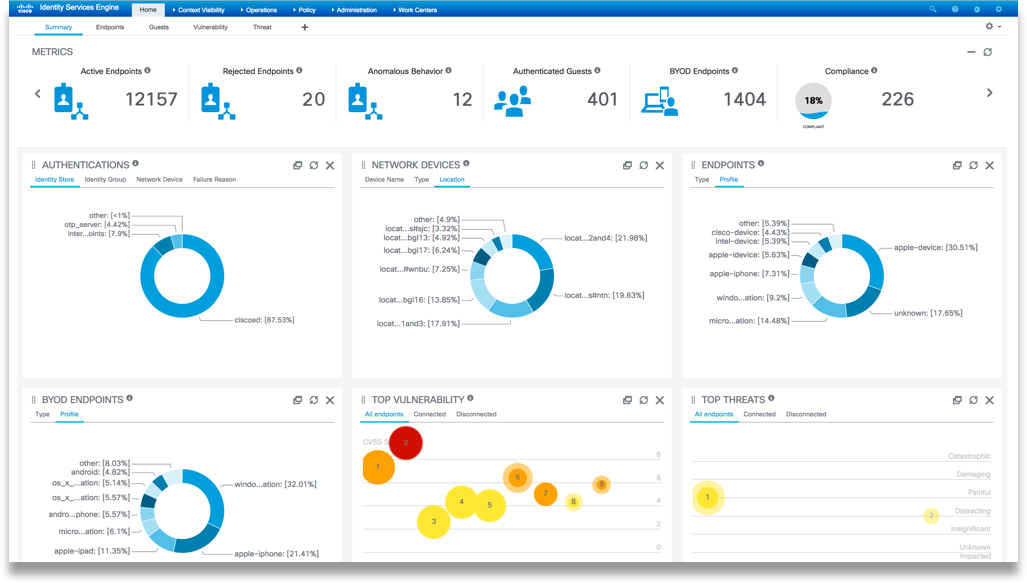
Figure 6
Network as a security sensor:
Cisco has pioneered the implementation of Netflow features on campus infrastructure equipment. Classically, the Netflow protocol was used to evaluate network performance and troubleshoot / debug, however, having the ability to receive full (non-sampled) Netflow directly from access level devices allows us to get visibility of all connections up to transactions between access ports in one switch. The convenience of NetFlow is that we collect only the descriptive part of the network connections, which provides the following benefits:
Analyzing the collected NetFlow data, behavioral analysis, tracking anomalous behavior and monitoring the implementation of security policies for organization traffic performs the Cisco StealthWatch solution, having more than 90+ algorithms and mathematical models for determining the malicious behavior of various categories onboard, see Figure 7.
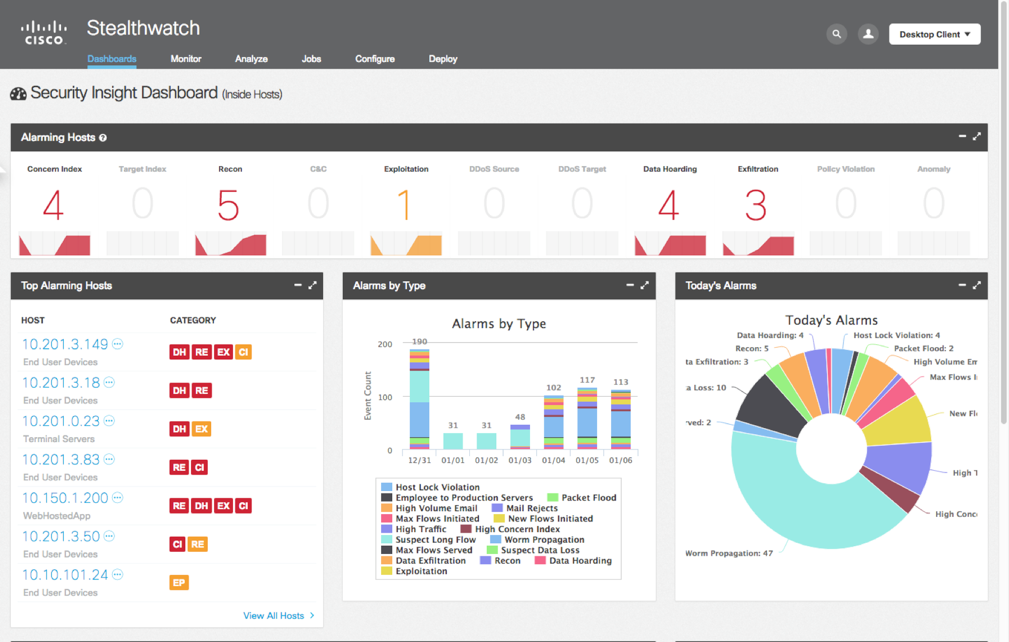
Figure number 7
But only if Netflow can be useful for us, the network and its individual components can give us a large amount of telemetry, which, being aggregated, gives an even deeper context to the occurring activities and allows them to be more clearly identified. Having a complete picture of network activities, we can real-time link data from such subsystems as (see Figure No. 8):
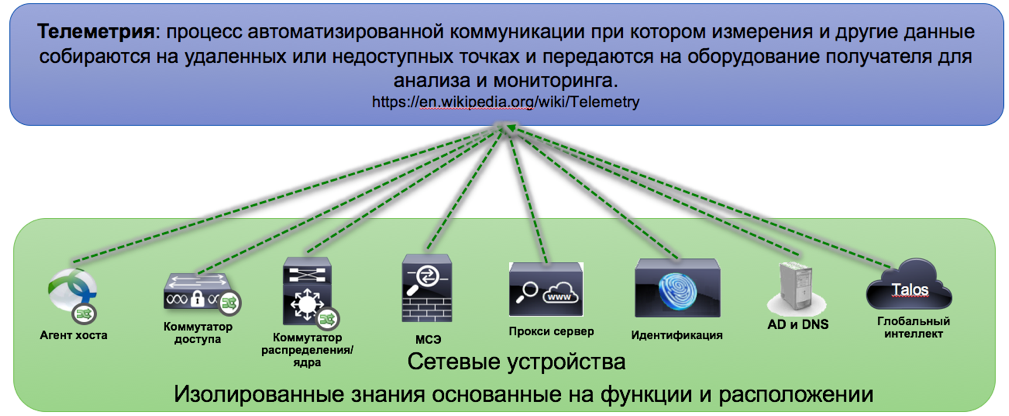
Figure 8
Let us consider several examples of how telemetry can be useful to us in attributing data streams. We will search for data streams according to criteria that interest us, or simply respond to the threat by viewing the associated transactions (see Figures 9, 10, 11).
In Figure 9, we clearly see an example of data flow attribution:
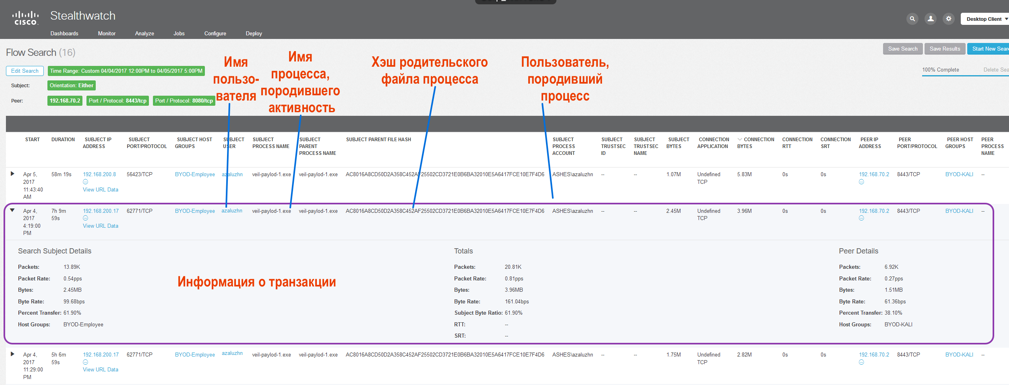
Figure number 9
In Figure 10 we see the device profile, it also indicates:
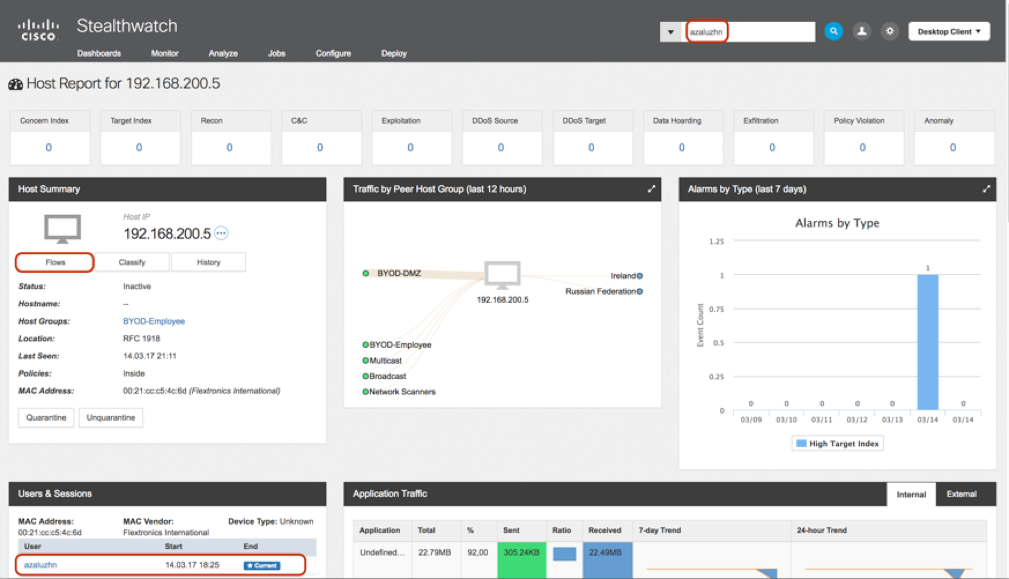
Figure 10
In Figure 11, we see the result of integration with the corporate WEB-Proxy and receiving telemetry from it. This telemetry provides detailed information on WEB requests associated with HTTP / HTTPS transaction traffic, with additional attribution provided by WEB-Proxy, such as:
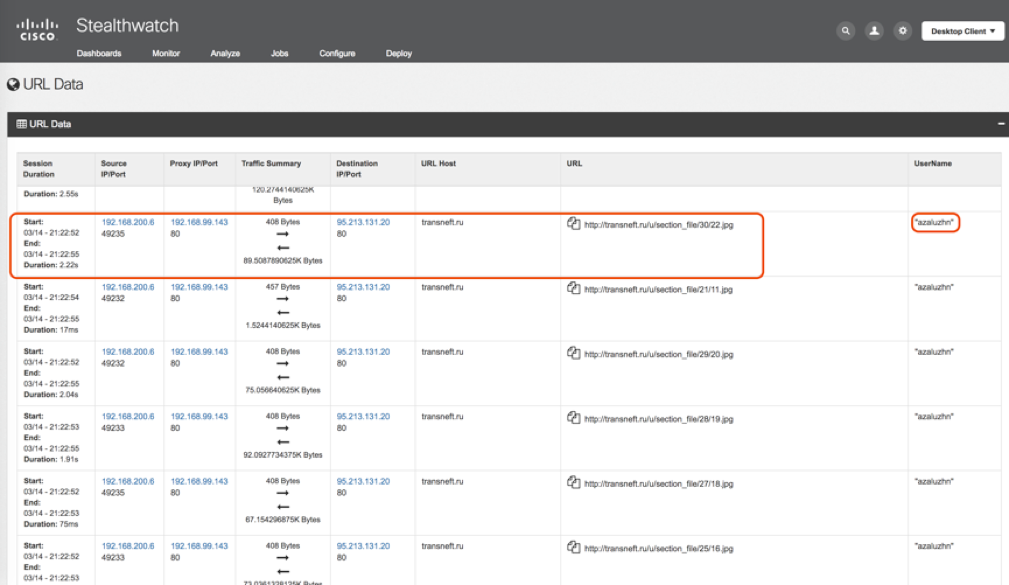
Figure number 11
Network factory and integration:
As we see, having collected a rich telemetry from our network, we received a very high level of visibility and attribution of all network activities within the network (see Figure 12). Our network has become a real network factory with a clear role-segmentation and transparency of all transactions with the detection of malicious behavior, which allows us to take our enterprise information security system to a new level.
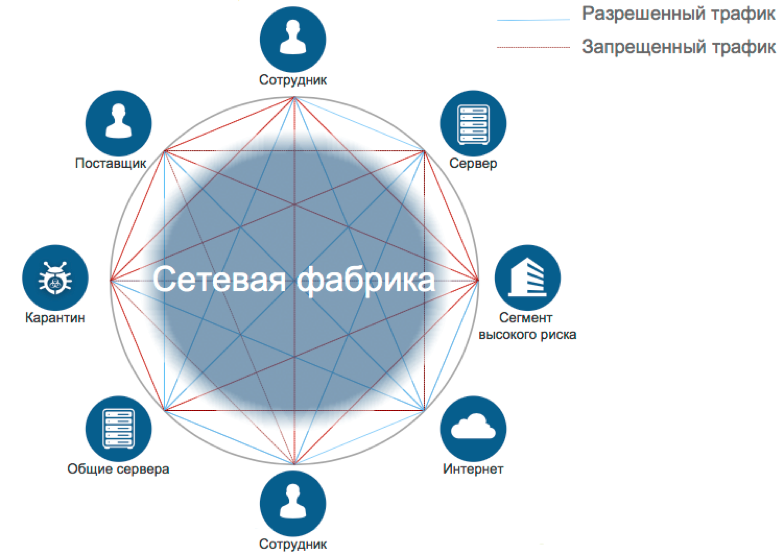
Figure number 12
APIs provide an opportunity to integrate this architecture transparently into the enterprise information security infrastructure and how to exchange context by ISE about the attributes of each terminal device in the network with firewalling, intrusion detection, anti-malware, content filtering systems, SIEM systems for filtering decisions based on the knowledge provided, so be an effective lever of control to block the threat directly at the point of Switching to the network - quarantine a compromised device or an intruder with the help of ISE, either automatically or manually.
Conclusion:
In conclusion, I want to say that the network of a modern digital enterprise should help businesses be more successful, help innovate faster and more efficiently, automate routine manual operations of deploying services and supporting infrastructure, providing automated and deep information security tools in their very essence, in their DNA, giving deep analytics and understanding of the processes taking place for the possibility of operational decision making.
The described architecture brings the capabilities of the network infrastructure to a real reduction in operating costs and the provision of opportunities for:
The Cisco DNA architecture gives you the opportunity to get more from your Cisco intelligent network and use its capabilities to the fullest to move to a modern digital enterprise.
Useful links:
Article - Cisco DNA Architecture
Considering security embedded in the network infrastructure and speaking of such concepts as DNA, we mean something very deeply integrated and embedded in the essence itself, in the case under consideration in the essence of the network. But we begin in principle with the very concept of DNA and how Cisco sees it for the network as a whole and what role information security plays here.
DNA concept:
')
DNA is a new Cisco approach to infrastructure, which brings with it the capabilities to provide technologies and approaches that can give modern business the advantages and drivers that a modern enterprise needs to effectively conduct business in the Digitalization Era.

Figure 1
The integral components of this approach are the programmability of the infrastructure, the possibilities for flexible automation of operations, the rapid introduction of services, abstraction, and the reduction of operating costs for both supporting current infrastructure and introducing innovations and services. The network must be flexible, and in this we can use the capabilities of the SDN architecture, APIs that give flexibility in the integration of systems, quick adaptation to their system infrastructure needs.
Virtualization, supplemented by software interfaces, provides flexible possibilities for the deployment of ready-made infrastructures and their rapid replication, modification and adaptation to changing business needs.
Analytics , a smart modern network should be not only a tool for deploying services and ensuring business operations, but also a source of important information and analytics that can provide real leverage for decision making and adjustments to business processes.
Deep integration of cloud services, applications and infrastructure with services deployed at the customer’s site blurs the line and provides transparent and convenient mechanisms for the development and implementation of hybrid infrastructures, which is one of the key requirements of modern digital business.
Due to the risks currently experienced from growing cyber threats that pose real risks to businesses, especially in an era when we are increasingly dependent on telecommunications, the Internet of things and online operations, greater attention is required to be paid to information security and this DNA concept includes information security tools and mechanisms. as a fundamental component of the entire infrastructure. Whatever we implement, which service is not launched - it must be deployed, operated and maintained safely and this information security process must be as automated as possible, thereby not reducing, but only increasing the efficiency of the business and its processes. The main pillars of this concept are shown in Figure 1.
Network as a security tool:
At the current time, the classic approach to segmentation and network access creates many gaps in the infrastructure, lack of deep control and visibility within the infrastructure. We cannot fully see what is happening inside our network infrastructure, in fact we are blind to the activities that occur in the protected segments of our network infrastructures, because the only way to get detailed information on network activities is to pass these connections through specialized filtering or analytics as firewalls (ITUs), intrusion prevention systems (IPS), and other devices leading deep packet analysis and protocol inspection. Thus, if we take the vast majority of networks where such solutions are located in their minimum, namely, on the perimeter of access to external networks and access to the data center - we have no picture of what is happening inside our campus network and inside the data center. Inside the network, active scanning, compromise, denial of service attacks, attempts to output distributed data with their prior collection, etc., can occur, but we will be blind to this. Installing an ITU or IPS on each floor switch is an extremely difficult task for the financial component, and the performance required for deep packet analysis required for the access / distribution / core level is very, very expensive. As a result, we detect an attack only when the network traffic reaches the control point, for example, the network perimeter, unfortunately all the underlying infrastructure at that time may already be compromised. Our visibility in classical segmentation will be limited and the difference in real connections and visible ones will somehow remind us of the illustration from Figure 2.

Figure 2
Imagine that you can see and constantly monitor all transactions within the network and have their full history, but what will this give us in our base?
- The chaos of dynamic IP addresses and impersonal transactions, search in which any significant events brings even more confusion
- IP addresses are constantly changing and binding to the topology of the host and the user at time A and B can be completely different, and what if the incident occurred three months ago?
- How to understand which user and device at each time point was tied to the data flow, what was their role and method of accessing the network, how to determine the harmfulness of the connection behavior or predict the harmfulness of the behavior on a long-term basis?
- What control methods can we use if necessary?
- How to recognize malicious behavior and integrate the network with high-level information security systems of the enterprise?
- How to precisely control all these devices and their activities that could possibly violate security policies?
These and other questions are answered by DNA Security's integrated network security concept.
A modern intellectual network of Cisco digital enterprise can be an effective means of information security and flexibly integrate into existing enterprise information security systems by exchanging with it the whole wealth of existing knowledge about the connected infrastructure and activities in it. After all, the Cisco intelligent network has a large set of knowledge, such as:
- What is connected to it and can determine the type of connected devices.
- What users are behind the terminal devices at specific points in time.
- Can provide an analysis of the state of the device the most convenient and transparent method.
- He sees all the transactions going through it and can give this knowledge through the Flexible Netflow protocol by enriching the data fields with additional knowledge and context.
- Attribute data flows and personalize them.
- Perform automatic role-based segmentation of access according to a centralized security policy, taking into account the context, and apply it transparently across the entire infrastructure.
- It can block the intruder directly at the point of connection to the network, whether it is a wired network, wireless or access via VPN.
- Transparently authorize context-based access without reference to topology and addressing regardless of the point and method of connection.
- Provide integration programming interfaces for third-party systems for the purpose of operational automation, including for information security.
Thus, the network is transformed not only into a full-fledged sensor, but also into an effective means of monitoring information security.
The key components to achieve the most from our network infrastructure and turn it into an effective information security tool are the Cisco Identity Services Engine with the Cisco Trustsec security architecture and the Cisco StealthWatch, see Figure # 3.

Figure 3
Network as a means of control:
The core of the architecture is the network access control and accounting system - the Cisco Identity Services Engine (ISE) whose tasks include:
- Authentication of user and non-user connections to the network via wired / wireless / VPN directions.
- Determining the type of connecting devices using the analysis of the network activities of the terminal devices by a number of protocols, for this purpose, the Device Sensor function is used in the intelligent switches / WLAN controllers of Cisco and the tree of heuristic definitions in the Cisco ISE itself.
- Integration with user directory systems and both active and passive authentication of connections.
- Role-based authorization of each network connection with the assignment of the Security Group Tag (SGT) label, depending on the context to the individual functional roles in the network, see Figure # 4. Transparent automatic access segmentation using the Cisco Trustsec architecture using a single access matrix for SGT tags, see Figure # 5.
- Assessment of the status of connecting devices and their compliance with the company's security policy.
- Exchange of the accumulated context through a software interface with other solutions that make up the Cisco network security architecture, and with third-party information security systems with the ability to quickly change the authorization of the connected device in the event of an information security incident.

Figure 4

Figure 5
Applying the segmentation of the software-defined segmentation of Trustsec to our devices / users on the network is assigned an SGT tag, depending on their functional role in the network defined by us (the business). Having an access matrix in ISE, we clearly indicate which roles (SGT tags) can have access to which roles (SGT tags) and how this access should be in a simple and clear interface of the matrix view. As soon as the device, connecting to the network, receives this label, all associated access policies from the specified matrix are automatically applied to all transactions directed from the source label to the assignment labels of other functional roles in the enterprise network.
As a result of ISE integration into the infrastructure, we understand exactly who, what (see Figure 6) and with what rights to connect to our network, we performed automatic role-segmentation of our network and now the issue of attribution of gray IP addresses in the past becomes resolved - we received an exact picture of who / where / when / how to connect to the network and with what rights. Next, consider how we get a deeper look at what is happening in our protected segments and see what was hidden for us in the past.

Figure 6
Network as a security sensor:
Cisco has pioneered the implementation of Netflow features on campus infrastructure equipment. Classically, the Netflow protocol was used to evaluate network performance and troubleshoot / debug, however, having the ability to receive full (non-sampled) Netflow directly from access level devices allows us to get visibility of all connections up to transactions between access ports in one switch. The convenience of NetFlow is that we collect only the descriptive part of the network connections, which provides the following benefits:
- We do not overload communication channels for transferring large amounts of analytics; Netflow traffic is incomparably small compared to the data it describes, in fact, it is metadata.
- There is no need to change the topology, since these statistics, like syslog, we can collect from the entire infrastructure at a single point.
- Using analytics algorithms and behavioral mathematical models of malicious behavior, we can detect signs of malicious behavior.
- By accumulating analytics, you can perform a long-term analysis and track abnormal behavior in the infrastructure.
Analyzing the collected NetFlow data, behavioral analysis, tracking anomalous behavior and monitoring the implementation of security policies for organization traffic performs the Cisco StealthWatch solution, having more than 90+ algorithms and mathematical models for determining the malicious behavior of various categories onboard, see Figure 7.

Figure number 7
But only if Netflow can be useful for us, the network and its individual components can give us a large amount of telemetry, which, being aggregated, gives an even deeper context to the occurring activities and allows them to be more clearly identified. Having a complete picture of network activities, we can real-time link data from such subsystems as (see Figure No. 8):
- Firewalls with translation information (NAT) of addresses and filtering solutions (permit / deny) (NSEL / Netflow)
- Proxy servers with associated web transaction logs (syslog)
- Information from identification systems, access control systems - AD / ISE (API / PXGRID)
- End user hosts for tracing network activities up to the process and privileges of the user who generated them (IPFIX / Netflow)
- Apply Global Threat Intelligence Intelligence to Identify Malicious Node Connections (SLIC)

Figure 8
Let us consider several examples of how telemetry can be useful to us in attributing data streams. We will search for data streams according to criteria that interest us, or simply respond to the threat by viewing the associated transactions (see Figures 9, 10, 11).
In Figure 9, we clearly see an example of data flow attribution:
- Which user was behind the AWS that spawned network activity.
- The parameters of the network activity itself.
- The name of the process on the automated workplace that generated the activity.
- The hash of the file that was the parent for this process.
- User privileges from which this process was launched.
- When using the TrustSec architecture, you can see the SGT tags of the source and destination of the traffic.

Figure number 9
In Figure 10 we see the device profile, it also indicates:
- What alarms on this device worked, when and from what categories.
- You can delve into the threads associated with the alarm message.
- Search for any transactions on this host.
- See the timeline of user activity on this host.
- Analyze traffic patterns for the last 24 hours, broken down by protocols in the outbound and inbound traffic directions.
- Send device to quarantine when integrating with Cisco ISE.

Figure 10
In Figure 11, we see the result of integration with the corporate WEB-Proxy and receiving telemetry from it. This telemetry provides detailed information on WEB requests associated with HTTP / HTTPS transaction traffic, with additional attribution provided by WEB-Proxy, such as:
- The IP address of the specific Proxy from the farm that processed the request.
- The IP address of the machine that made the request and the IP address that DNS resolved at the time of the domain request.
- The requested domain.
- Full requested URL.
- A user as he was associated with a transaction on a proxy server.

Figure number 11
Network factory and integration:
As we see, having collected a rich telemetry from our network, we received a very high level of visibility and attribution of all network activities within the network (see Figure 12). Our network has become a real network factory with a clear role-segmentation and transparency of all transactions with the detection of malicious behavior, which allows us to take our enterprise information security system to a new level.

Figure number 12
APIs provide an opportunity to integrate this architecture transparently into the enterprise information security infrastructure and how to exchange context by ISE about the attributes of each terminal device in the network with firewalling, intrusion detection, anti-malware, content filtering systems, SIEM systems for filtering decisions based on the knowledge provided, so be an effective lever of control to block the threat directly at the point of Switching to the network - quarantine a compromised device or an intruder with the help of ISE, either automatically or manually.
Conclusion:
In conclusion, I want to say that the network of a modern digital enterprise should help businesses be more successful, help innovate faster and more efficiently, automate routine manual operations of deploying services and supporting infrastructure, providing automated and deep information security tools in their very essence, in their DNA, giving deep analytics and understanding of the processes taking place for the possibility of operational decision making.
The described architecture brings the capabilities of the network infrastructure to a real reduction in operating costs and the provision of opportunities for:
- The introduction of new services without changing the topology and associated labor costs.
- Flexibility and mobility of employees and devices in the network with transparent access authorization.
- Automatic maintenance of role-based segmentation and application of security policies in a simple and understandable form from a single interface.
- Monitoring the status of connected devices and correcting it until the process is fully automated.
- Deep visibility and analysis of everything happening on the network, detection and blocking of malicious activity in areas that were previously a blind spot.
- Integration with enterprise information security systems to build a seamless transparent information security system of the enterprise.
- Getting a rich context about the network and its components and historical tracking to enable detailed investigation of incidents.
The Cisco DNA architecture gives you the opportunity to get more from your Cisco intelligent network and use its capabilities to the fullest to move to a modern digital enterprise.
Useful links:
Article - Cisco DNA Architecture
Source: https://habr.com/ru/post/328474/
All Articles