Burp Suite: Swiss Army Knife for Testing Web Applications

Burp Suite is a platform for auditing web application security . Contains tools for mapping a web application, searching for files and folders, modifying queries, fuzzing, selecting passwords and much more. There is also a BApp store add-ons store that contains additional extensions that increase the functionality of the application. It is worth noting the appearance in the latest release of mobile assistant for the study of the security of mobile applications - MobileAssistant for the iOS platform.
Burp Suite is an integrated platform designed for auditing a web application, both in manual and automatic modes. Contains an intuitive interface with specially designed tabs that allow you to improve and speed up the attack process. The tool itself is a proxy mechanism that intercepts and processes all requests coming from the browser. It is possible to install a burp certificate for analyzing https connections.
If you look at the statistics and reports of bug-bounty programs, you can see the use of this tool almost everywhere in the screenshots. Along with OWASP, ZAP is the most popular set of utilities for testing web applications.
')
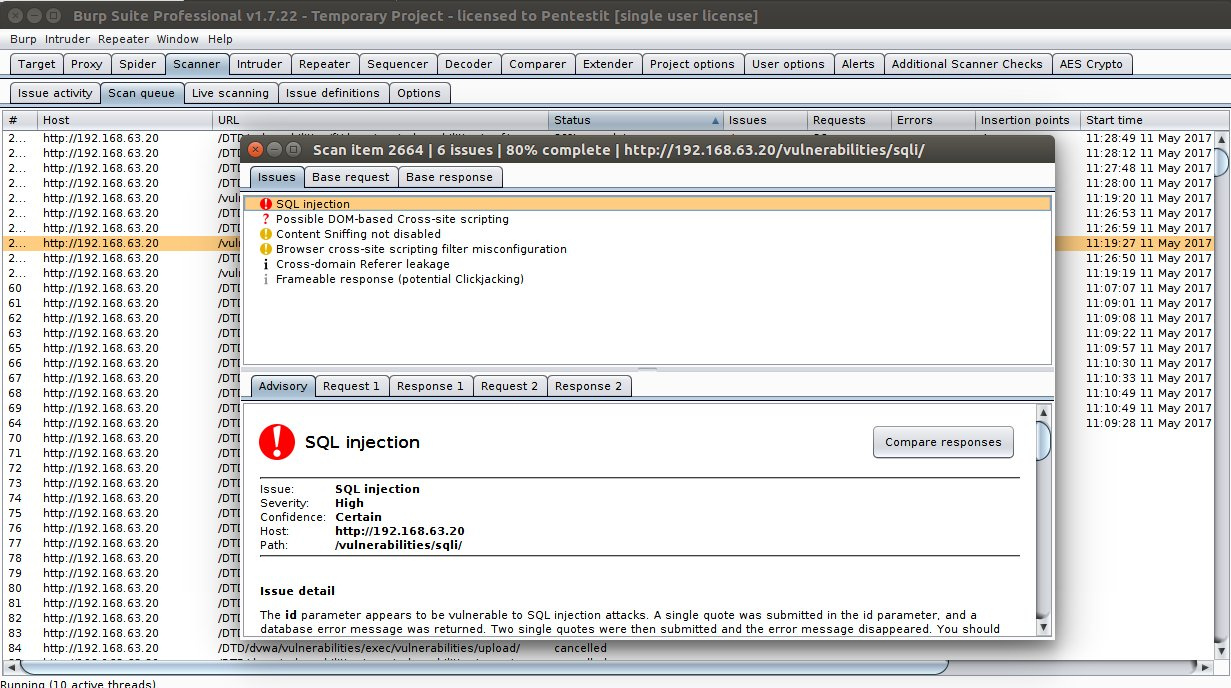
In the image, use Burp Scanner to analyze the Damn Vulnerable Web Application (DVWA).
There are two versions of Burp Suite: Professional and Free.
Although the differences in functionality are quite substantial - the Free version is a complete testing tool. One of the main differences is the lack of a scanner in the free version and the limitation of the number of requests per unit of time. Also, in the free version there are no built-in payloads for an intruder, but it is quite possible to use external ones, for example: github.com/1N3/IntruderPayloads . There are restrictions on the use of add-ons from the BApp store. A significant disadvantage is the absence of the Burp Collaborator in the free version (using an external service to identify vulnerabilities).
Composition
The main functionality is based on the following modules:
- Proxy is a HTTP (S) intercept proxy server in man-in-the-middle mode. Being between the browser and the web application, it will allow you to intercept, examine and modify traffic going in both directions.
- Spider - a spider or crawler that allows you to automatically collect information about the architecture of a web application.
- Scanner - automatic vulnerability scanner (OWASP TOP 10, etc.) Available in the Professional version, in the free version only a description of the features.
- Intruder is a utility that allows you to automatically perform various types of attacks, such as password guessing, enumeration of identifiers, fuzzing, and so on.
- Repeater is a utility for modifying and re-sending individual HTTP requests and analyzing application responses.
- Sequencer is a utility for analyzing the generation of random application data, identifying the generation algorithm, data predictability.
- Decoder is a utility for manual or automatic conversion of web application data.
- Comparer is a utility for detecting data differences.
- Extender - extensions in BurpSuite. You can add as ready from the BApp store, and its own design.
Using a set of tools allows you to most deeply and productively explore a web application.

Intruder
One of the main testing tools is Burp Intruder. The principle of its operation is as follows: it processes each HTTP request (called the “basic request”), changing parameters in various ways, issuing each modified version of the request and analyzing the application's responses to identify interesting functions or behavior of the web application.
For each attack, it is possible to specify a set of payloads (payloads) and their position in the basic request. Numerous methods for creating payloads are available (including simple lists of strings, numbers, dates, brute force, bitflipping, and many others). Various tools are available for analyzing the results and identifying interesting questions for further study.

On the image use Burp Intruder - setting payload values for password selection.
Burp Intruder has a very flexible system of settings, so it can be used to automate many types of attacks. You can use it to perform other tasks, such as the selection of user identifiers, the collection of important information or fuzzing.
The types of possible attacks depend on the particular application and may include: checking for the presence of SQL injections, XSS, buffer overflow, directory traversal; bruteforce-attacks on various authentication schemes, enumeration of values, manipulations with the contents of parameters; search for hidden content and functionality, the calculation of session identifiers and their interception, data collection, the implementation of DoS-attacks associated with the features of the web application.

In the image, using Burp Intruder to identify sql injections is a choice of payloads.
Burp Intruder contains (in the Pro version) a set of pre-selected payloads (strings to detect the presence of vulnerabilities). In addition, it contains a large number of utilities for the dynamic generation of attack vectors suitable for a specific application. Also, additional payloads (for example, user names or passwords) or specific fuzzing requests can be loaded into it.
The basis of each attack is the sending of modified HTTP requests. Their contents are generated based on the initial request and the established payload positions. The result of the work will be a table with various data (status, response length, etc.)
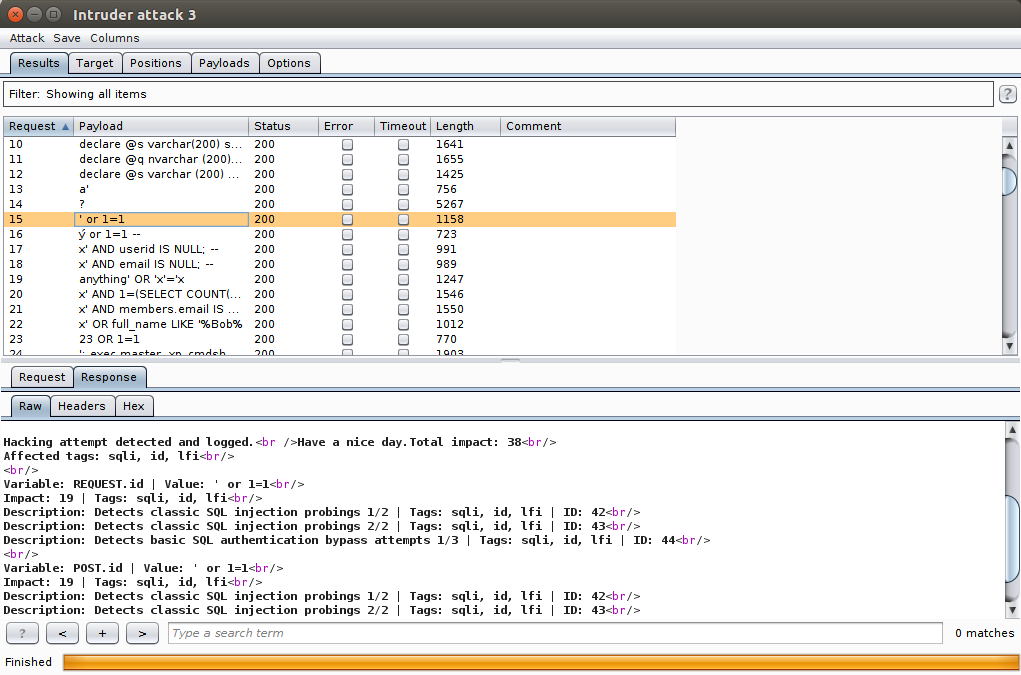
In the image, using Burp Intruder to detect sql injections is an attack.
Burp Intruder supports the following types of attacks:
- Sniper - a separate data set is used - one field (area marked with markers) - one payload. This type of attack is useful when individually testing fields for common vulnerabilities (such as XSS).
- Battering ram - with this type of attack, the principle is used - all fields - one payload. This can be useful when for the implementation of an attack it is necessary to place the same data in multiple positions at once.
- Pitchfork - this type of attack uses several paylodes for several fields. For example, in the first query, the first row from the first test set will be placed in the first place indicated by the markers. And the first line from the second set will fit into the second position. When forming the second request, the second line from the first set will be placed in the first place, and the second line from the second set will be placed on the second line. This type of attack can be useful in situations where the application needs to send all the time different, but somehow interrelated data. For example, if you want to send the username in one field and its ID in another.
- luster bomb - this type of attack uses the search of the main set of payloads and the addition of secondary ones. It is convenient to use, for example, for selecting passwords: on the first request, Intruder will place the first line from the first set of payloads in the first position and the second from the second line into the first position. In the second query, the first row of the first set will remain in the first place, and the second row of the second set will be placed on the second. Then the third, and so on.
The attack results window allows you to control the progress of the attack and save its results.
MobileAssistant
Burp Suite Mobile Assistant is a tool to make it easy to test iOS applications with Burp Suite.
It can change the system-wide proxy settings for iOS devices so that HTTP (S) traffic can be easily redirected to Burp for analysis. He is also able to use SSL pinning - the introduction of his certificate. Mobile assistant can be used on jailbroken iOS devices, ranging from version 8 of iOS to 10 (although it does not guarantee stable operation). For installation, you need Cydia and a full-fledged Burp on the host system.

The appearance of this tool will greatly facilitate the identification of vulnerabilities in OWASP Mobile Top 10.
Conclusion
Burp Suite is deservedly one of the most popular tools for pentesters around the world due to its flexible capabilities, methods of combining manual and automated analysis methods when conducting web application security testing.
Note: Like any security testing software, Burp Suite contains features that can damage a web application. Security testing essentially involves interacting with a web application in non-standard ways that can cause problems for some web applications. Due care must be taken when using Burp Suite, backing up before testing, and not using Burp Suite against any systems for which you have not received permission from the resource owner.
Source: https://habr.com/ru/post/328382/
All Articles