PHDays HackQuest 2017: RanSomWare - a small cryptor on GO
Good day to all, just came to the end of a two-week HackQuest from PHDays . Despite the predominance of tasks related to WEB, the organizers did not ignore the tasks associated with the reverse. The decision of one of these tasks ( erawmosnar ), I would like to consider today. Besides, I think after WannaCry this topic will become even more relevant.
There was only 1 hint to the task:
Download the file and open it in IDA, andsuffer go google for us over1000 unnamed functions, and apparently this is Golang :

A quick search on Google showed a solution to this problem. Download the script, run it in IDA and enjoy.
')

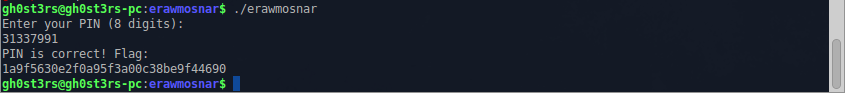
Starting all the same binary, we see an invitation to enter the 8-digit PIN, and a message about its incorrectness in case of failure.

Using this as a starting point is not difficult to find a function that handles all this. After processing the code by the script, this function is called main_main .
It all starts with the fact that a hash is written to the buffer:

Then we are asked to enter a pin:
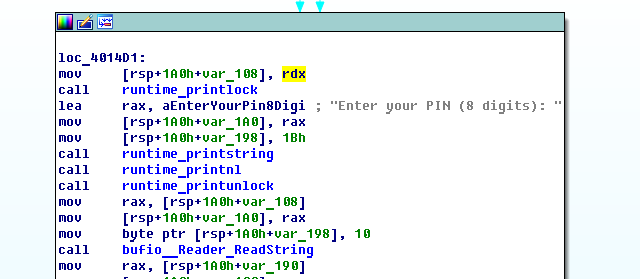
Then the SHA1 hash is calculated from it, and it is checked against the standard, well, then everything is simple, either we see the flag, or the contents of the current directory are encrypted:
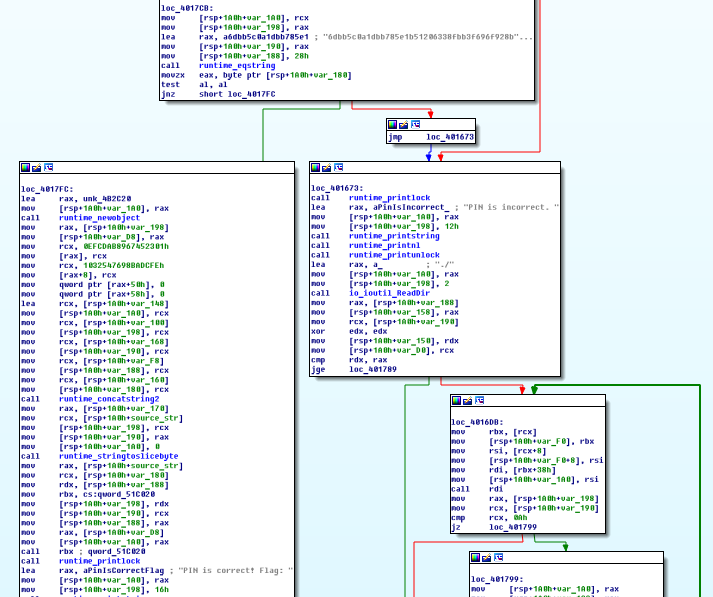
Set several breakpoints for clarity:
The first breakpoint is triggered before the runtime_concatstring2 function call , some hash is sent to the stack, and our pin, along with the "\ n" symbol:
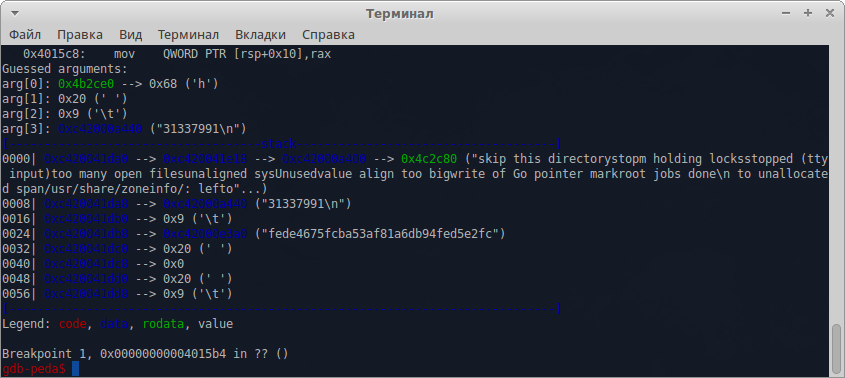
We press to continue, we get to the next breakpoint, where the result of the concatenation of the PIN code we entered with the salt is clearly visible:

On the third breakpoint, the hashes are simply checked. Now having all the necessary information, it remains only to clear the hash. Create a dictionary for enumeration:
And run the brute force:
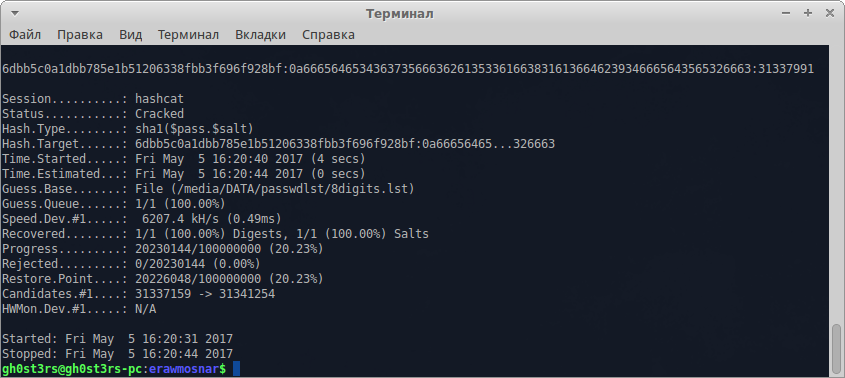
Pin successfully picked up, it remains to pick up the flag:
There was only 1 hint to the task:
Warn: erawmosnar == ransomware, do not run it, if you don’t know what you doing.
Let's start
Download the file and open it in IDA, and
A quick search on Google showed a solution to this problem. Download the script, run it in IDA and enjoy.
')
Starting all the same binary, we see an invitation to enter the 8-digit PIN, and a message about its incorrectness in case of failure.

Using this as a starting point is not difficult to find a function that handles all this. After processing the code by the script, this function is called main_main .
It all starts with the fact that a hash is written to the buffer:
Then we are asked to enter a pin:
Then the SHA1 hash is calculated from it, and it is checked against the standard, well, then everything is simple, either we see the flag, or the contents of the current directory are encrypted:
Set several breakpoints for clarity:
gdb-peda$ break *0x4015B4 Breakpoint 1 at 0x4015b4 gdb-peda$ break *0x4015D5 Breakpoint 2 at 0x4015d5 gdb-peda$ break *0x401669 Breakpoint 3 at 0x401669 gdb-peda$ The first breakpoint is triggered before the runtime_concatstring2 function call , some hash is sent to the stack, and our pin, along with the "\ n" symbol:

We press to continue, we get to the next breakpoint, where the result of the concatenation of the PIN code we entered with the salt is clearly visible:

On the third breakpoint, the hashes are simply checked. Now having all the necessary information, it remains only to clear the hash. Create a dictionary for enumeration:
gh0st3rs@gh0st3rs-pc:erawmosnar$ crunch 8 8 1234567890 -o /media/DATA/passwdlst/8digits.lst And run the brute force:
gh0st3rs@gh0st3rs-pc:erawmosnar$ sudo hashcat -m 110 --hex-salt hash /media/DATA/passwdlst/8digits.lst 
Pin successfully picked up, it remains to pick up the flag:

Source: https://habr.com/ru/post/328114/
All Articles