Functional security, part 7 of 7. Methods of ensuring information and functional security
A source
At the end of a series of publications on functional safety , in today's article we will look at what organizational and technical methods are used to ensure functional safety.
Most of the methods can be applied, among other things, to ensure information security within the framework of the concept of integral safety (safety & security) of modern control systems.
')
The set of analyzed methods is based on the requirements of IEC 61508 "Functional safety of electrical, electronic, programmable electronic safety-related systems " (IEC 61508 Functional safety of electrical / electronic / programmable electronic safety-related systems). In terms of the specifics of ensuring information security of the automated process control system, NIST SP 800-82 Guide to Industrial Control Systems (ICS) Security , considered in a previous article, was taken as the basis.
IEC 61508: Methods and means of ensuring functional safety
When performing certification for compliance with IEC 61508 requirements for a particular SIL (Safety Integrity Level) level, it is important to demonstrate that, first, the product has a necessary and sufficient functional safety mechanism (FB), and, second, that The necessary and sufficient set of methods to ensure the FB was used in the development process. Proceeding from this, we conditionally divide the methods of providing security into technical and organizational ones.
The FB assurance methods are aimed at protecting against accidental hardware failures caused by the physical aging of elements, as well as against systematic failures caused by imperfect design processes. Since in the modern world FB is unthinkable to be considered in isolation from information security (IB), the methods of providing FB also, for the most part, provide protection against cyber attacks.
At the same time, most of the methods are complex, that is, the same method in one way or another aims to protect against accidental and systematic failures.
A description of the methods for securing the FB is contained in IEC 61508-7 “Methods and means” . However, to understand the requirements for the application of a method, part 7 alone is not enough.
In part 2 of IEC 61508 , which is devoted to providing FB systems and hardware, and in part 3 , which contains software requirements, there are three essential applications that define methods and means of protection against accidental and systematic failures. The structure of IEC 61508 is such that the methods and tools are described in detail in Part 7. Thus, the requirements for protection against failures from Parts 2 and 3 of IEC 61508 are traced to descriptions of the methods and tools for securing the FB in Part 7. This relationship is shown in Figure 1.
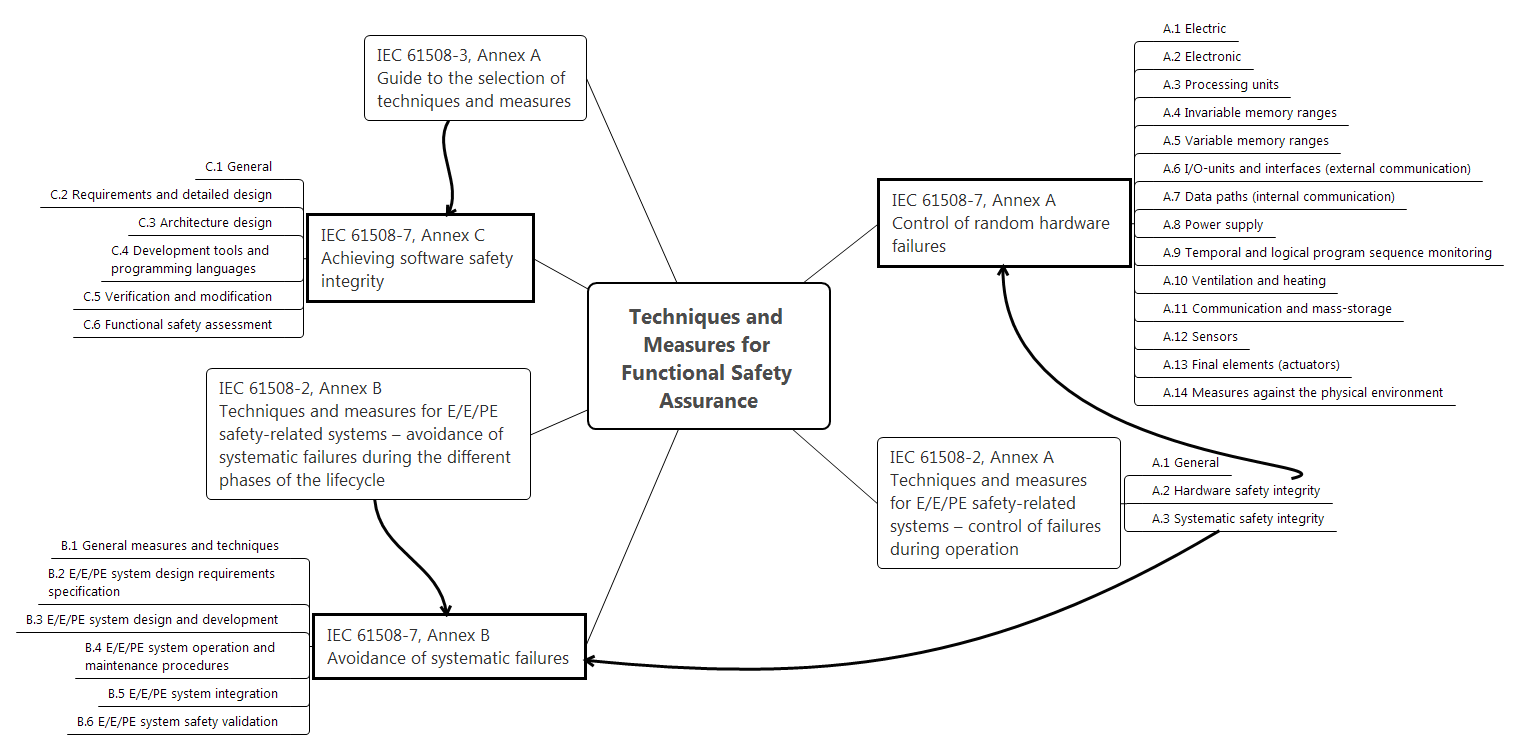
Figure 1. Structure of safety methods according to IEC 61508
Annex A of part 2 of IEC 61508 considers the control of hardware failures during operation, and it is understood that these can be both random and systematic failures. A detailed description of protection methods against accidental failures is contained in Annex A of Part 7 of IEC 61508. Methods of protection against accidental failures are divided into categories, depending on the type of hardware considered, for example, electrical components, electronic components, processor modules, memory, etc.
The Appendix In part 2 of IEC 61508 discusses methods for protecting against systematic hardware failures over a life cycle. It should be noted that IEC 61508 considers engineering errors, operational errors and external extreme influences (climatic, mechanical, radiation and others) as sources of systematic hardware failures. A detailed description of the relevant methods is contained in the Appendix. In part 7 of IEC 61508. The structure of the presentation of methods for protecting against systematic hardware failures has its own characteristics, for example, B.1 General measures and techniques include such different methods as Project Management, Documentation, Separation, Diversity. Next, the methods are distributed in stages of the life cycle.
Appendix A of part 3 of IEC 61508 provides guidance on the choice of software development and testing methods to achieve safety integrity. A detailed description of the relevant methods is contained in Annex C of Part 7 of IEC 61508. Here, in category C.1 General, no methods are described at all. Further, the methods are divided into categories: requirements and detailed design, architectural design, tools and programming languages, verification and modification, evaluation of the FB.
To illustrate the above in IEC 61508, consider the simplest table that defines the methods used to ensure the functional safety of software at the stage of the development of a specification of requirements (see Figure 2).
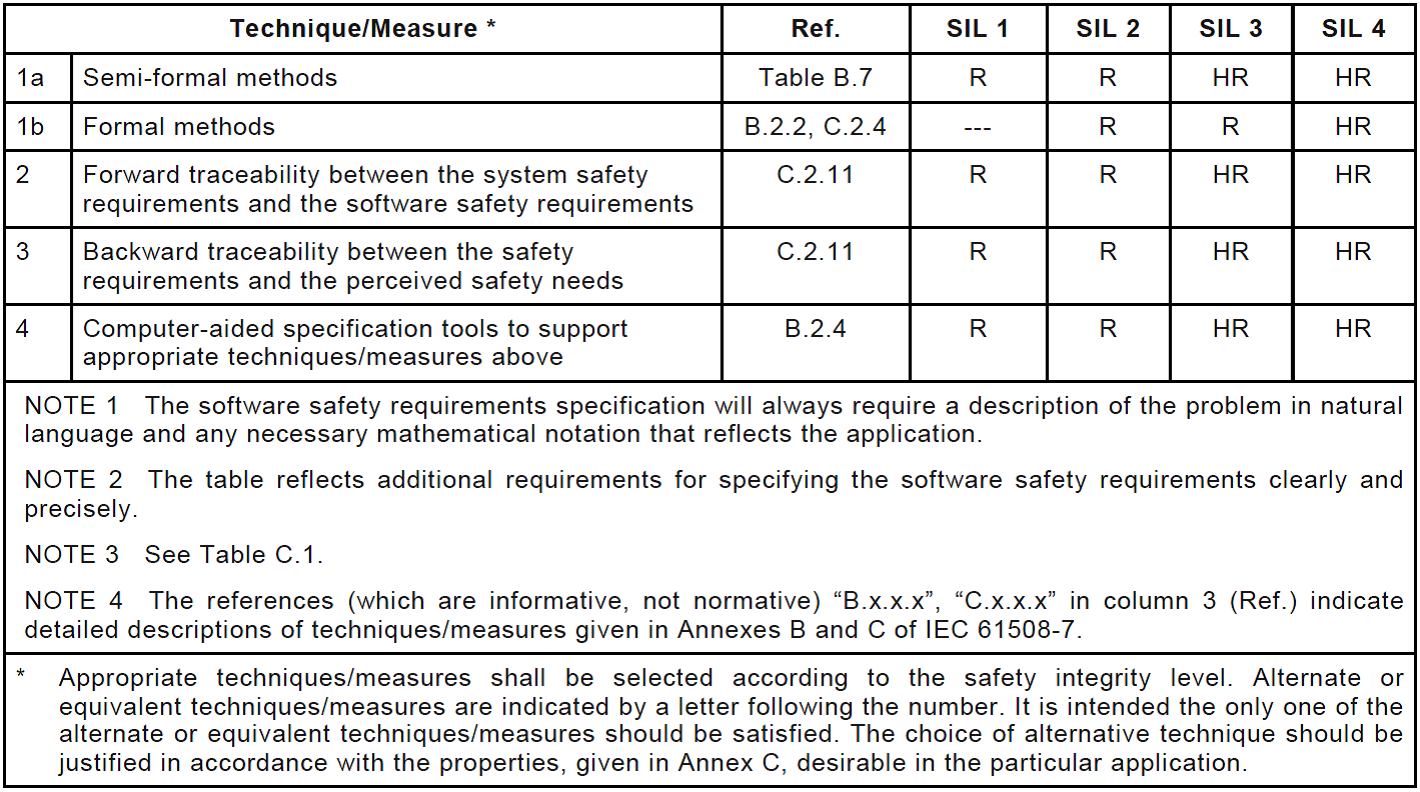
Figure 2. IEC 61508-7, Table A.1 - Software safety requirements specification
Suppose we are interested in the SIL3 safety integrity level. Those methods which in the column "SIL3" are designated as HR (Highly Recommended) should be applied without fail. In any case, it will be almost impossible for the certifying authority to explain why this or that necessarily recommended method has not been used. The methods designated as R (Recommended) can be applied, however, they can also be reasonably abandoned. With Table A1 (SIL3) everything is quite simple here. The use of formal methods is recommended, however, the priority of using semi-formal methods is higher (Highly Recommended). Therefore, if semi-formal methods are used, then formal methods can be waived. The use of direct and reverse tracing is also mandatory (the trace of requirements has already been mentioned in previous publications ). The use of software to support tracing and specification development is obvious.
As we have said, it is advisable to divide security methods into organizational and technical. We now consider these two groups.
Organizational methods of ensuring information and functional security
In fact, organizational measures have already been considered in previous publications of this series. These include FB management, project management, life cycle management, development and testing methods. We make a small summary of these methods according to the structure of IEC 61508. All these methods can be equally applied to both functional and information security.
Project management
The use of project management methods allows you to provide the required level of security, that is, to keep in the so-called "quality triangle". The “Project Management Knowledge Body” or PMBOK contains recommendations for implementing processes at all stages of the project life cycle.
Documenting
Documentation and documentation management is an important method for recording all technical and organizational decisions on product development important to safety. Special attention is paid to documenting changes in products and processes. Documentation should be carried out throughout the life cycle.
The life cycle of IB and FB
Implementation of the life cycle of information security and security is a requirement that has already been discussed in detail in previous publications. In IEC 61508, particular emphasis is placed on such aspects as:
- a structured system development process and software ;
- implementation of the verification and validation process, consisting in the phased implementation of reviews, analysis and testing;
- support of the product after release, taking into account feedback on the results of operation.
Using best practices and coding standards
IEC 61508 requires the introduction of the safe use of programming languages, which is the use of languages with strong typing and support for structured programming, it is recommended that a limited number of language constructs be used. For example, for microcontroller security systems, preference is given to language C, rather than C ++. Relevant standards are used to define coding rules and prohibited constructions, such as MISRA .
Coding standards and best practices define a number of conventions (coding conventions) that are used in software development as code requirements. Such agreements include naming and annotation rules, indentation and code design rules, restrictions on complexity, etc.
A common practice is the so-called defensive programming, when, when a critical problem occurs, the software shuts down the work in a predetermined manner, i.e. puts the system into a safe state.
Using Certified Compilers and Libraries
When developing software important to security, it is necessary to ensure that the compiler converts the source code into executable in a predictable and deterministic way. To do this, use certified compilers and code translators, as well as certified libraries of software components. In the past few years, leading manufacturers of microprocessors and FPGAs have released versions of compilers and associated libraries that have been certified and, accordingly, can be used to develop security software. Modern trends in electronics engineering are leading to an increasing integration of software and hardware design of programmable components, therefore, the role and impact on the safety of development tools will increase.
Quality control in hardware production
In the production of hardware, special attention is paid to the quality of printed circuit boards with electronic components installed on them. Quality control is made up of components such as:
- development and verification of hardware design;
- quality management of purchased materials and components;
- Production Management;
- quality inspection at the production site;
- testing of released hardware.
Using formal and semi-formal notations
Another organizational method required by IEC 61508 is the use of formal and semi-formal notations to develop a specification of requirements and system designs, as well as software and hardware components. Currently, the most common semi-formal notations for the design of programmable systems are IDEF and UML .
For programmable logic controllers, typical programming languages are developed and described in IEC 61131-3 , supported by most development environments. The most common is the graphical language FBD (Function Block Diagram) , which is actually a formal notation for software design.
Technical methods to ensure FB
We begin by considering the architecture of the process control system (see Figure 3). The system includes:
- power supply components;
- field equipment (sensors and actuators);
- programmable logic controllers, including input and output modules and control modules;
- network equipment, servers, and human-machine interface components.

Figure 3. Typical architecture of the process control system (source: ISA / IEC 62443)
Reservation
Now we will consider how redundancy can be implemented for the process control system.
Redundancy can be implemented both for individual components or their groups, and for the system as a whole. This is the case that is brought to your attention (see Figure 4).
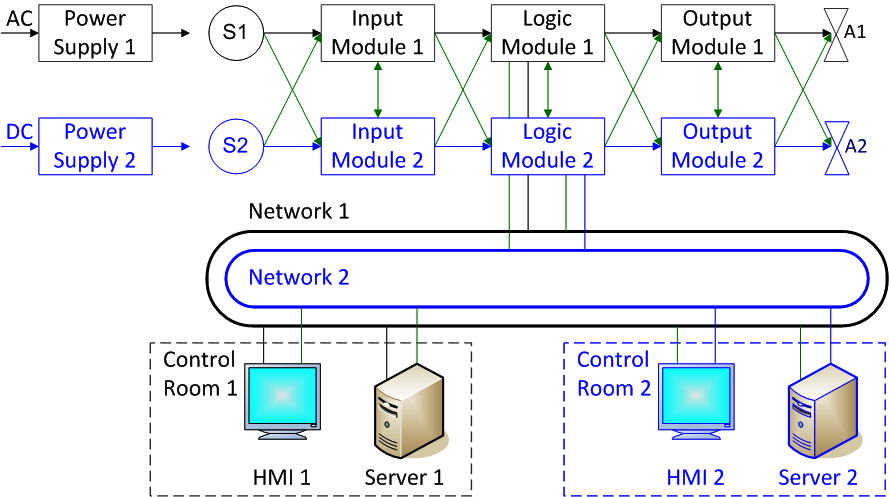
Figure 4. Duplication of process control system components
Let's start with the power supply. Ideally, maximum independence is ensured by supplying independent channels of the system from independent sources. The diagram shows that the first channel is powered by an alternating current source, and the second channel is powered by direct current. Then, in case of problems with power supply in one of the power supply systems, only one of the channels will be de-energized. Ensuring continuity and quality of power supply even in extreme conditions is a vital aspect of ensuring the safety of control systems.
Redundant sensors, controllers and actuators may be used. Protocols of information exchange can be organized between channels (they are indicated in green in the diagram) or maximum independence between channels can be realized, and then there will be no exchange.
In addition, a duplicated network architecture and a duplicate human-machine interface with duplicate computing components and data storages can be implemented.
Diversity (sabotage) when reserving
Diverity (divercity) is called the type of reservation, when in the backup channels the same function is performed in different ways, for example, using different equipment or different software.
Normal redundancy does not protect against systematic failures caused by design errors. Therefore, if the system versions are designed differently, then the number of total systematic channel failures (the so-called common cause failures) will decrease (in any case, theoretically decrease). This is taken into account with the help of the so-called -factor, which shows the ratio of the number of failures (or failure rates) by the common cause to the total number of failures (or failure rates). -factor depends on the strategy of subversiveness used. The greater the difference between the channels, the lower the value factor (see Figure 5).

Figure 5. Reduction in the number of common cause failures when using different (submarine) duplicated channels (source: IEC 61508)
Of course, the use of diversion is an extremely expensive method that increases the cost of the system several times, but in some high-risk industries, for example, in the nuclear power industry, this is justified and required by standards.
Independence and separation of components
Another method that complements redundancy is the principle of independence and separation (independency and separation) of components, aimed at preventing the spread of failures between systems and their components. Separation can be physical when, for example, the system channels are physically located in different rooms or at a considerable distance from each other (see Figure 6). Electrical separation is also used, including, for example, galvanic isolation, as well as functional independence and communication independence, for example, shielding of cables and separation of electrical and signal cables.
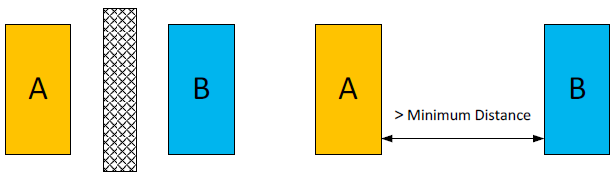
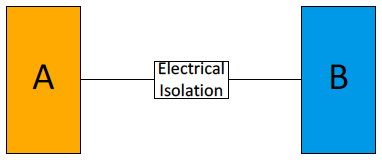
Figure 6. Physical and electrical independence of the channels (source: IEC 60709)
Self test
Self-diagnostics of digital devices can be simplified as follows (see Figure 7).
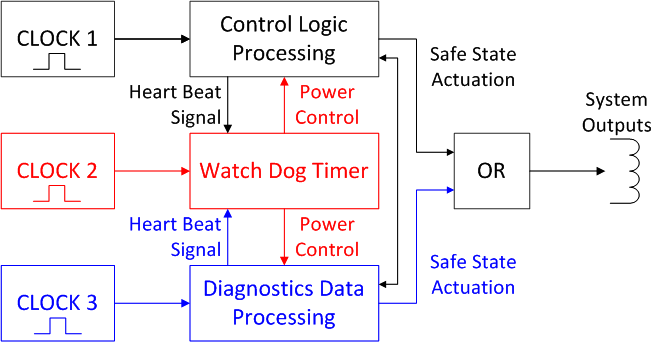
Figure 7. Diagnostics implementation in control systems
Along with the main algorithms of digital control, the diagnostic data processing and watchdog are implemented in parallel in the system. All these three processes are performed independently of each other, independent clock sources, different chips, etc. can be used.
Watchdog monitors the simplest response from the chips that process the data, and when a problem is detected (the response is stopped), it turns off the power and puts the system into a safe state. In addition, the watchdog can monitor the power level and issue a similar shutdown command if there is a dangerous power deviation from the specified level. A safe state for security systems, as a rule, consists in removing power from the output analog and discrete outputs. If necessary, the security system can supply power to the actuators, but then the output requires additional signal converters.
If self-diagnostics detected a critical problem (for example, hardware failure, hardware or software configuration violation, data transmission violation, etc.), a command is issued to put the system into a safe state, which is performed the same way as if the command came from main control logic.
Now we generalize what typical functions the self-diagnostics of digital devices should perform. The functions of the watches and power control have just been considered.
An important diagnostic function is to control the configuration of software and hardware. This property also affects information security. During operation, each hardware module periodically transmits information about its serial number and configuration of the loaded software (for example, check-amount). In the event of a configuration violation, the system performs specified protective actions, up to a transition to a safe state and a power outage.
Another option to perform hangup monitoring is internal or external timers that control the execution time of individual control logic modules. Tasks can be restarted several times, in case of several unsuccessful restarts, a decision can also be made on transition to a safe state.
An important function of control systems is to ensure the accuracy of measurement of input and output analog signals. To diagnose measurement accuracy, redundant ADCs and DACs can be used, in which the processing results are compared and a diagnostic message is issued on the coincidence or discrepancy of the results.
Much attention in the control systems is paid to the transfer of data packets, both through communication channels and in processing distributed between the software and hardware components. Here, methods such as transmission confirmation, timeout control, integrity monitoring and data packet transmission sequence, cyclic codes (CRC) are used for diagnosis. To protect information during data transmission encryption algorithms can be used.
Environmental Protection
Another group of safety techniques is designed to protect against adverse effects. The method of independence and separation has already been considered by us.
To ensure the functioning of control systems, ventilation and air conditioning are used, structures resistant to vibration and other mechanical effects are designed, fire extinguishing systems and non-combustible materials, materials and coatings resistant to chemical and radiation effects are used.
Serious attention is paid to ensuring electromagnetic compatibility. For this, filtering and suppression of electromagnetic interference of various kinds, both external and own, is carried out to limit the impact on other equipment.
Special ATEX standards are applied to the design of explosion-proof systems. IP standards are used to design systems that are protected from dust and moisture.
Protection from personnel errors
Personnel operating control systems can both reduce and increase risks. Many technological accidents were caused by human factors. At the same time, there are many cases when professional actions allowed avoiding catastrophes and death. Therefore, the development of a human-machine interface with ergonomic requirements and protection from operator errors is also an important direction of safety.
Information Security Features
APCS
When considering methods aimed at providing security tools, it is also important to provide information security. IEC 61508 only contains a few general words on this subject. We will focus on several features of automated process control systems that determine the approach to providing information security systems for such facilities. In Figure 8, potential vulnerabilities are considered, from which attack vectors are formed.
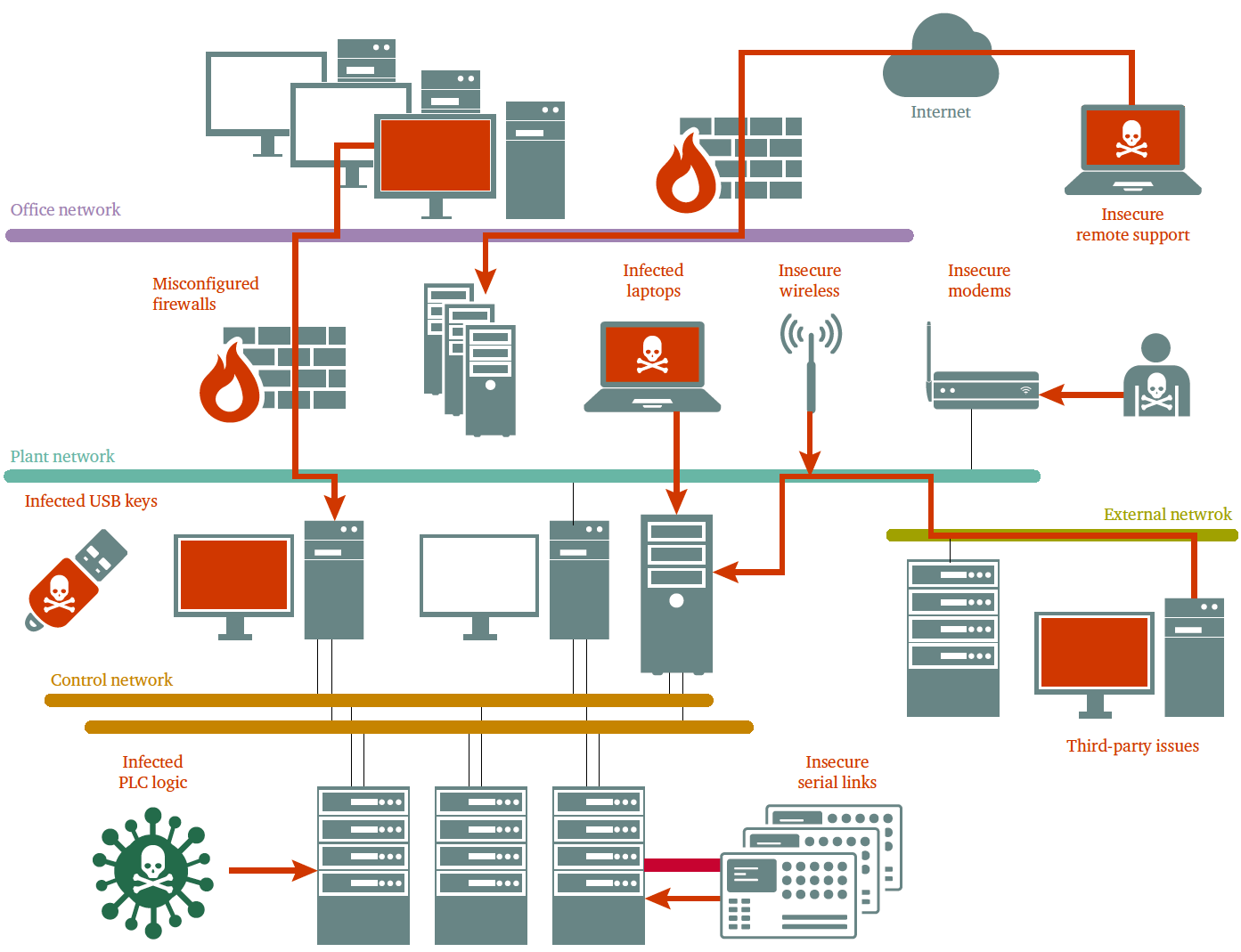
Figure 8. Vulnerabilities in process control systems (source: Byres Research Inc.)
Such vulnerabilities are: network perimeter, remote connections, firewalls, purchased equipment, removable media (primarily using USB ports), as well as controller software and communication lines.
Network segmentation
The basis for providing information security for the automated process control system is network segmentation and equipment zoning (this topic was discussed here ).
It is recommended to implement at least one demilitarized zone (DMZ) separating corporate and control local networks in the automated process control system.
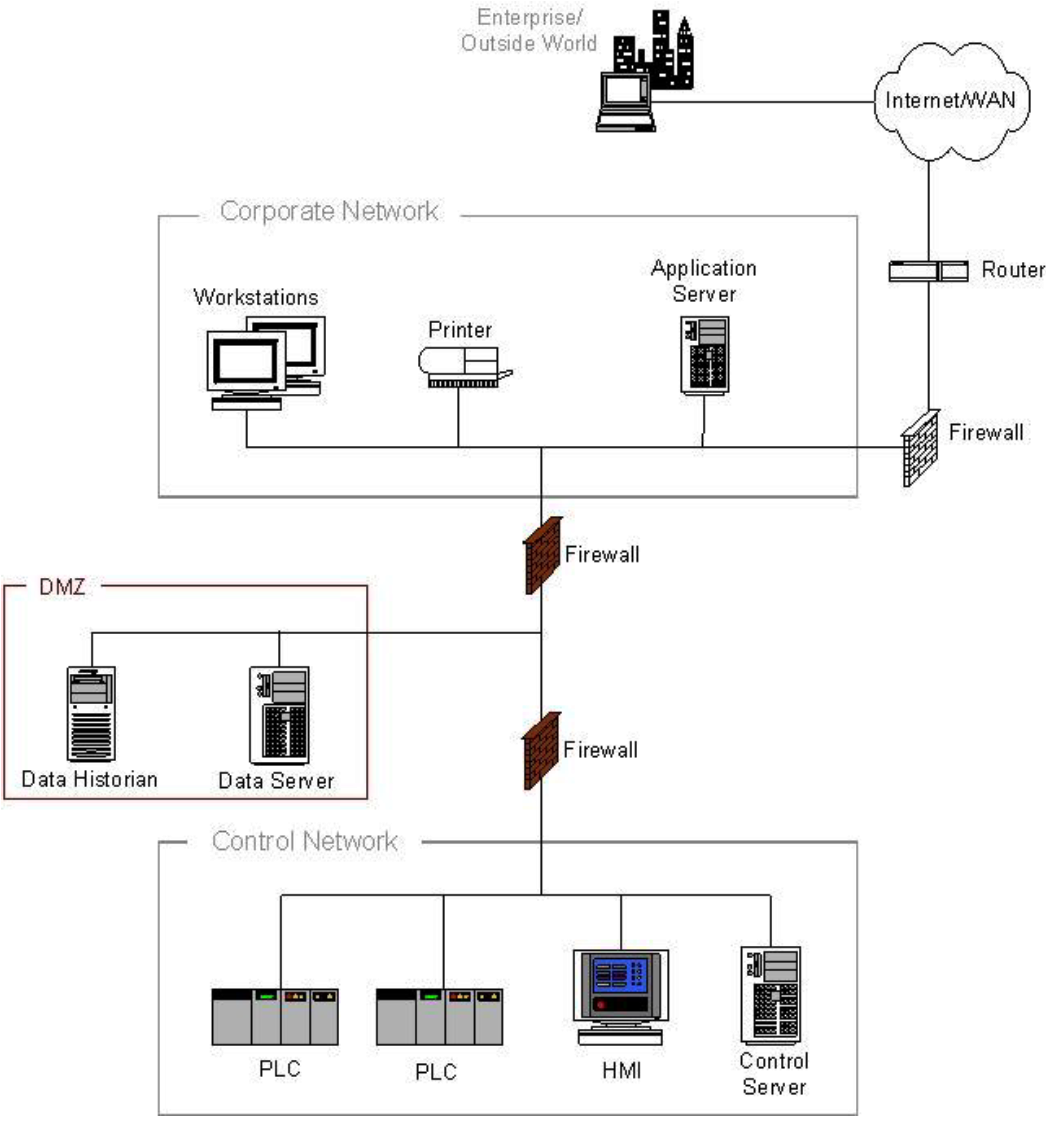
Figure 9. Network structure of the process control system with DMZ (source: NIST 800-82)
Access control
Another feature of providing information security systems is the active use of access control, which can be implemented in several ways.
Cabinets with equipment are supplied with locks and contact sensors for opening doors, which give out signals on the alarm panel.
Monitoring and preservation of a large amount of diagnostic data, including those related to information security, provides broad analytical capabilities.
Since communication lines are vulnerable components, access to them is also controlled, both at the physical and logical levels. The use of communication lines and ports should be reasonably limited. Security systems require the use of only unidirectional communications using proprietary protocols that differ from common industrial protocols.
To change the settings of the software and the software itself, as well as to change the hardware configuration, special authorization must be performed.
findings
Methods and means to ensure the security of management systems should ensure that risks are reduced below specified levels, both for the information and for the functional component of security. These methods include two groups: organizational and technical.
Organizational methods include: project management, documentation, implementation of the IB and PB life cycle, the use of advanced programming methods and standards, the use of certified translators, compilers and code libraries, quality control in the production of hardware components, the use of formal and semi-formal notations for the development of specifications and design.
Technical methods include: redundancy, separation and independence, diversification or diversity, protection against internal and external hazards, human-machine interface engineering, as well as various types of self-diagnostics.
Specific attack prevention techniques for control systems include access control and network segmentation.
PS This article concludes the cycle of publications on functional safety, on which I worked for several months. Thanks to all readers, especially those who with their caring comments helped to refine the material. In parallel to the publications, a video course on functional safety was prepared and recorded (it has no analogues in the world). The main provisions of the publications and the video course are devoted to approaches to certification of management systems for compliance with the requirements of IEC 61508. The topic of safety remains inexhaustible, and, therefore, there will be new publications.
Here is the full list of articles:
- Introduction to the subject of functional safety ;
- Standard IEC 61508: terminology ;
- IEC 61508 Standard: requirements structure ;
- The relationship between information and functional safety of the process control system ;
- Management processes and functional safety assessment ;
- The life cycle of information and functional security ;
- The theory of reliability and functional safety: basic terms and indicators ;
- Methods to ensure functional safety .
Source: https://habr.com/ru/post/327910/
All Articles