Authentication in OpenSSH Putty by JaCarta PKI
This article describes the algorithm for configuring the Putty SSH client for Windows to work with the JaCarta PKI.
JaCarta PKI - tokens manufactured by Aladdin RD for strict two-factor authentication of users when accessing protected information resources of the enterprise, secure key storage and key containers of software SKZI.
SSH is an application level network protocol that allows remote control of the operating system and tunneling of TCP connections. Encrypts all traffic, including transmitted passwords. SSH allows the choice of various encryption algorithms. SSH clients and SSH servers are available for most network operating systems.
SSH supports RSA-key authentication, which provides the maximum level of security for the data channel, as well as two-factor authentication for remote users.
')
To configure SSH operation using RSA certificates, you need to configure an SSH server, as well as an SSH client on the client machine. This document describes the algorithm for configuring SSH operation using a smart card or a JaCarta PKI token for authentication and encryption of an established channel.
It is necessary to transfer the certificate to the smart card. To transfer, you need to collect all the necessary objects in an encrypted container and write it to a smart card.
ssh -I /usr/lib/x86-athena/libASEP11.so 127.0.0.1
To work requires version putty-cac 0.62
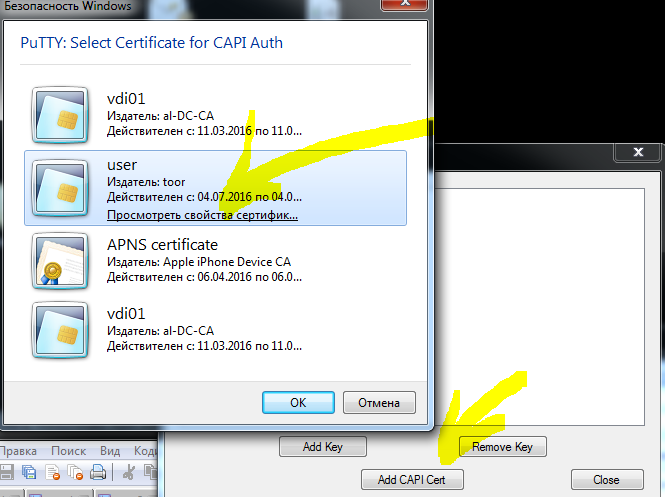
In general, the certificate appears in the certificate store automatically, but in some cases you may need to add it manually.
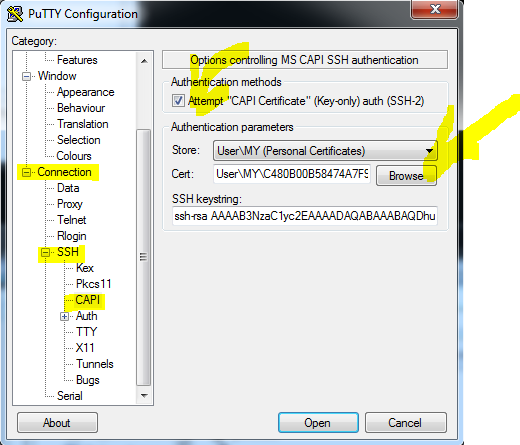
Connection / SSH / CAPI tab
After entering the user's PIN, an SSH session will be established.
JaCarta PKI - tokens manufactured by Aladdin RD for strict two-factor authentication of users when accessing protected information resources of the enterprise, secure key storage and key containers of software SKZI.
General information
Ssh
SSH is an application level network protocol that allows remote control of the operating system and tunneling of TCP connections. Encrypts all traffic, including transmitted passwords. SSH allows the choice of various encryption algorithms. SSH clients and SSH servers are available for most network operating systems.
SSH supports RSA-key authentication, which provides the maximum level of security for the data channel, as well as two-factor authentication for remote users.
')
Certificate Authentication
To configure SSH operation using RSA certificates, you need to configure an SSH server, as well as an SSH client on the client machine. This document describes the algorithm for configuring SSH operation using a smart card or a JaCarta PKI token for authentication and encryption of an established channel.
Setting up smart cards for SSH client
The order of the server side on the example of Ubuntu
Generating a key pair with ssh-keygen utility
- Go to the /home/user/.ssh directory
- ssh-keygen -t rsa
- Set a key name, for example, key
- Set the key password (to encrypt the private key), for example, 12345678
- At the output we get two files, for example, key and key.pub
Generating a certificate request with keys from p. 1
- openssl req -new -out user.req -key key
Certificate issue in CA openssl
- Config openssl CA
- cd / etc / ssl
- sudo -i
- echo “01”> serial
- cp / dev / null index.txt
- Editing /etc/ssl/openssl.cnf nano openssl.cnf
- dir = ./
- certs = $ dir / certs
- crl_dir = $ dir / crl
- database = $ dir / index.txt
- new_certs_dir = $ dir / certs
- certificate = $ dir / ca.crt
- serial = $ dir / serial
- crl = $ dir / crl.pem
- private_key = $ dir / ca.key
- dir = ./
- openssl req -new -x509 -keyout ca.key -out ca.crt -days 3650
- mkdir crl
- Download
- Run makehashlink
- chmod + x make_hash_link.sh
- ./make_hash_link.sh / etc / ssl
- ./make_hash_link.sh / etc / ssl / crl
- cd / etc / ssl
- Signing a user certificate (release)
- sudo -i
- cd /home/user/.ssh
- openssl ca-out user.crt -infiles user.req
- sudo -i
Import public key in Autorized_keys
- The /home/user/.ssh directory should contain a public key file containing ssh-rsa {KEY}. In the example, we created a file named key.pub
- Import this key into the authorized_keys file
- echo key.pub> authorized_keys
Donastroyka server part
- chmod 700 authorized_keys
- Openssh settings In /etc/ssh/sshd.conf, edit the authentication configuration
- RSAAuthentication yes
- PubkeyAuthentication yes
- PasswordAuthentication no - failure to authenticate by password (optional)
- RSAAuthentication yes
Writing a certificate to a smart card
It is necessary to transfer the certificate to the smart card. To transfer, you need to collect all the necessary objects in an encrypted container and write it to a smart card.
- openssl pkcs12 -export -in user.crt -inkey key -certfile ca.crt -name "user" -out user.pfx
- Transferring the user.pfx file to a Windows system with the installed JaCarta Single Client software , or JC Client
- Enter user PIN
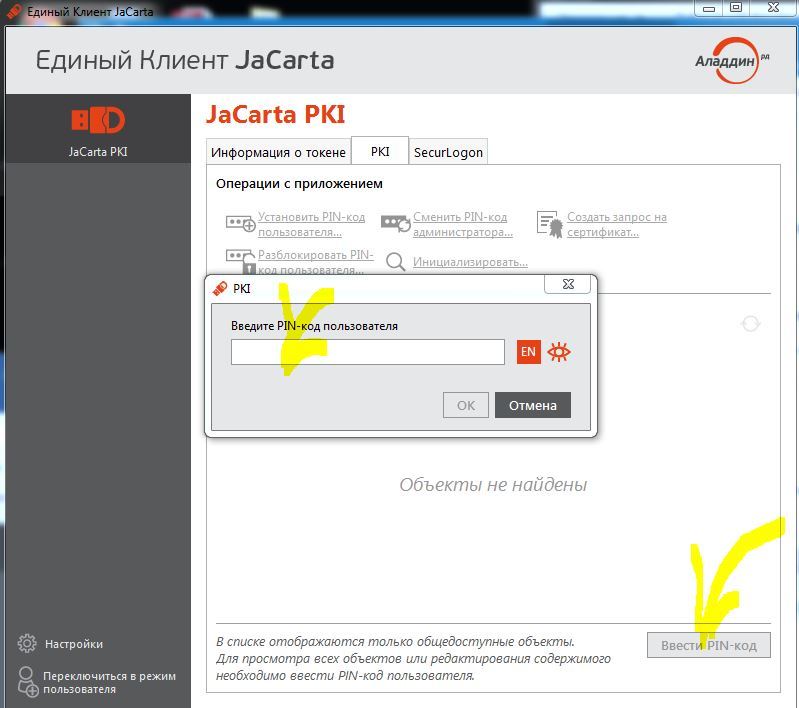
- Import certificate to token

- Select the file user.pfx and click "Import"
Certificate validation
ssh -I /usr/lib/x86-athena/libASEP11.so 127.0.0.1
Configuring an SSH Putty client on Windows OS
Run utilities from the distribution kit putty-cac \ executables
- pageant.exe
- putty.exe
To work requires version putty-cac 0.62
Select a certificate in pageant

In general, the certificate appears in the certificate store automatically, but in some cases you may need to add it manually.
Starting and Configuring Putty
Connection / SSH / CAPI tab

Login to SSH session by certificate
After entering the user's PIN, an SSH session will be established.
Source: https://habr.com/ru/post/327868/
All Articles