Cry of the Soul - “Hacking” the LiteManager Infrastructure
Foreword
This text is, first of all, a warning for system administrators and ordinary users. Suddenly for me, it turned out that the relatively well-known remote administration program “LiteManager” (hereinafter LM) by itself, without modifications and any changes, is a backdoor for any computer where it is installed. That is, if LM is installed on a PC and a connection by ID is used (without an IP address), then with a very high, almost 100%, probability, this PC can be obtained by unauthorized remote access to a completely foreign user, with minimal effort. while not possessing any special hacking skills. A description of the “hacking” technology and a working example with the source code below.
I am a programmer in a small company, our software is not connected with network technologies, however, sometimes employees need remote access to work PCs. For various reasons, the choice fell on the LM, which is free for 30 employees. In addition to direct connections in the local network (a la Radmin), LM allows you to work without specifying the IP address of a remote computer, by ID, through the Company’s server (ha-ha) or user servers that anyone can deploy, subject to the availability of external IP addresses (at first glance, it looks like TeamViewer, but this is only the first).
How the network of NOIP servers LM is arranged
And here we have found that periodically, to some machines, remote access via LM is performed by some unidentified person. Those who had access passwords could not physically connect remotely at that moment. In general, the situation repeated more than once or twice, even after changing passwords. LM was removed from all the machines and I began to study the situation, starting, of course, with how the connections by ID are arranged. LM borrowed the name from a well-known international company and called their module LM NOIP server (also called a “router”).
Connection by ID, in programs of this kind, allows you to communicate, even if the remote (and / or local) computer is behind NAT. You specify the ID and password of the remote computer, press OK and get full control over the machine. At the same time, both the administrator’s computer (hereinafter referred to as the Viewer) and the remote PC (hereinafter Server, yes, in LM terminology, do not confuse it with the LM NOIP server, that is, the router) use only outgoing connections to the router.
And this is where the fun begins. Below is a description from the official site.

From the official site
Got an idea? To use your personal NOIP router and the free version, you need to open this router for everyone . It would seem that in this bad? To answer this question, let's deal with the general scheme of NOIP LM routers.
They have one, so-called “Main server”, which coordinates the other open routers, through which all traffic drives, including and commercial users. This is monitored by any TCP connection monitoring program — first, a request to the main server, then work through random (or not random, depending on the settings).
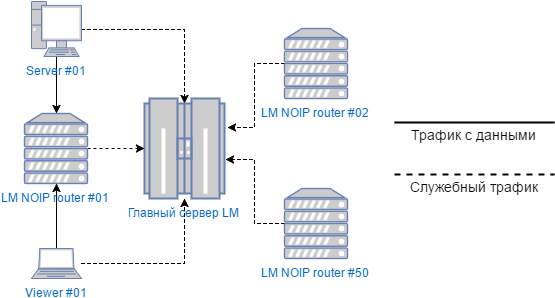
LM Server Schema
Tsymes is that in order to work by ID it is not necessary to deploy a personal NOIP server, by the way, we did not install our own server. Everything works out of the box due to the presence of already existing free NOIP routers, which are already several dozen, their list is available directly from the Viewer. The program chooses some server (it can be different every time) and the traffic goes through it. Thus, obviously, the Company decided to create a kind of torrent tracker, saving on traffic and servers.
Global vulnerability
But, as practice has shown, this idea is beautiful only as an idea. In fact, through completely random servers belonging to random people, traffic is proxied, including passwords for accessing remote PCs, of course, and not the new Star Wars series, as is the case with torrent.
Yes, of course, traffic is encrypted.

From the official site
')
RSA 2048, AES 256, everything. Only the Server <=> Viewer channel is encrypted, although even if the Serve <=> NOIP and Viewer <=> NOIP channels were encrypted, this would not change anything drastically. However, there is no server authentication in the program and there is no mention! Yes, even if such a check was, from the practice of working with RDP, I can responsibly state that few people pay attention to the warning that it is not possible to verify the authenticity of a remote computer.
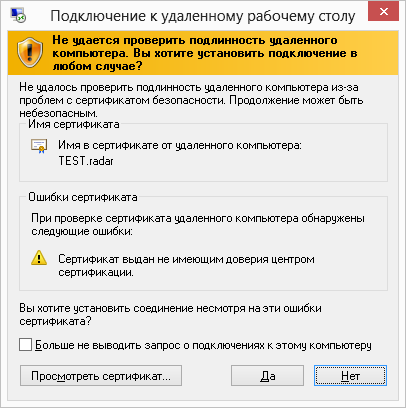
RDP version warning
But, I repeat, even such a check is not there. And here the abbreviation MITM comes to my mind. Attack "man in the middle." Almost immediately it became clear that the search for the hole was completed.
Even after a cursory examination of the Wireshark traffic and viewing the program modules under the debugger, it became clear that this is it.
To implement the MITM, you need to somehow get access to the infrastructure / equipment / communication channel, they need social engineering and other tricks, this is a single product that does not represent much harm to the masses. In general, professional hackers who I am not doing are engaged in this.
But LM provides, I apologize for another exclamation mark, this infrastructure to anyone who wants to, at the same time, as they like to repeat on their website - for free! Install an open LM router and “listen” to all the traffic that goes through it. A kind of fishing ID and passwords to access remote machines. It remains only to intercept traffic and decrypt it.
As a result, we have a global, architectural vulnerability of the entire LM infrastructure. Was this intended to be done or because of the lack of basic knowledge in the field of network security? The question is open.
Traffic interception
Attached to this article is a fully working sample program, with source code that can intercept almost all the IDs and passwords of connections passing through the LMNOIP router. The only requirement is an external IP address.
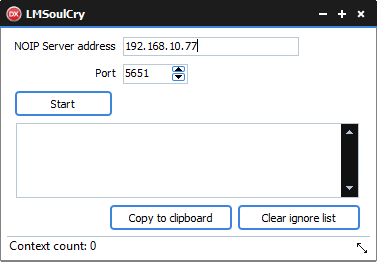
Lmsoulcry.exe
LMSoulCry needs to be installed on the network in front of the LM NOIP router.
LM NOIP router is designed in such a way that when it starts up, it accesses the Global LM Server, apparently, for registration. The global server, in turn, tries to establish a reverse TCP connection to this router. If this succeeds, the router can be transferred to a free mode and used, i.e. it is open to all.
We need to make sure that our LMSoulCry accepts incoming TCP connections (it, in turn, will redirect them to the LM router). And the outgoing connections LM router will send independently straight to the Global server, without our participation.
Here is a typical setup. Your PC has an external IP address. Install a virtual machine to run the LM NOIP router on it. We connect it via the built-in NAT adapter (it is in VMWare) to your main PC. We configure the Internet in a virtual machine (often, you do not need to configure anything, everything works by itself). We start on the physical computer, with external IP, LMSoulCry.exe and indicate in it the internal address of the virtual machine. Next, turn on the LMSoulCry and start the LM NOIP router (which is on the virtual machine). Casual users will not be long in coming.
If the external IP address is not on your PC, but on the router, then you just need to specify port-forwarding in the settings of this router itself.
If there is no external IP address, then in practice you will not check anything.
MITM implementation
As for the implementation of MITM, everything is trite there. LM uses the MS Crypto API, which makes it even easier to replace keys. The LMSoulCry source code is generously supplied with comments, I don’t see any sense in transferring it to the article.
Probably, this example will cause a condescending smile from professional hackers, but it is valuable in that it can even understand a very average programmer or student who, at least in general terms, knows how to use a debugger to understand and implement. In the example, there are no patches or API interception.
This example can also be easily extended to intercept anything that the LM passes through. Since the traffic is actually not protected by NOIP.
Here, as they say, we must not talk, but show.
Soul cry, lyrics and conclusions
After detecting this vulnerability, a letter was sent to the LM developers. To which the answer was never received.
Responsible
Perhaps you will be answered. Try happiness.
I am not sure that the developers of the product called “LiteManager” will bear the deserved responsibility for putting thousands of unsuspecting users (both free and commercial, which is important), including me, for already seven years old. After all, it is not written anywhere that the program is not protected in any way and, having installed it on a PC, you are guaranteed to open the door to it for anyone who wants it, the lock does not work.
But I have confidence that professional hackers have been very, very long in the know about this “architectural feature” of this software and have been using it for a long time.
Yes, in many products a similar scheme is used to bypass NAT, but in all these programs, the servers (routers) belong either to the Company producing the product, or are located on the customer’s side and are controlled only by them. That is, there is no third party, it is always clear who to ask, in case of problems.
Yes, I can understand and forgive the Company when personal data flow from its servers. When they find some rare vulnerability and slyly exploit it. But, when it has been proposed for more than 5 years, excuse the expression, scam, and a mass one, there is no forgiveness and understanding. I hope at least this article will take power.
I strongly recommend that all users immediately remove LiteManager, I recommend that antivirus check mark LM and its site as malicious.
I highly recommend “keep your eyes open” to everyone who misfortune has passed, and also keep in mind the statement about free cheese and mousetrap.
→ Github
Source: https://habr.com/ru/post/327742/
All Articles