How Do I Apply?

Hi, Habr! It's about group policies and Security Filtering. Depending on the size of your domain, its logical structure and the number of OUs, Security Filtering can be very useful to you.
Using Security Filtering, you can apply a policy to users or PCs that are located on different OUs, placing your policy in the root of the domain and applying a filter.
')
A typical filtering task is to mount network folders and printers. But on printers and folders, everything just begins and ends with your imagination.
Read under the cat how to apply group policies to individual users / groups, and what to look for if your policies do not work when using Security Filtering.
The filtering mechanism is simple, the Security Filtering tab shows the groups to which the policy is applied, by default the policy is applied to the Authenticated Users group. Delete the Authenticated Users group and specify the user or PC groups to which your policy should be applied.
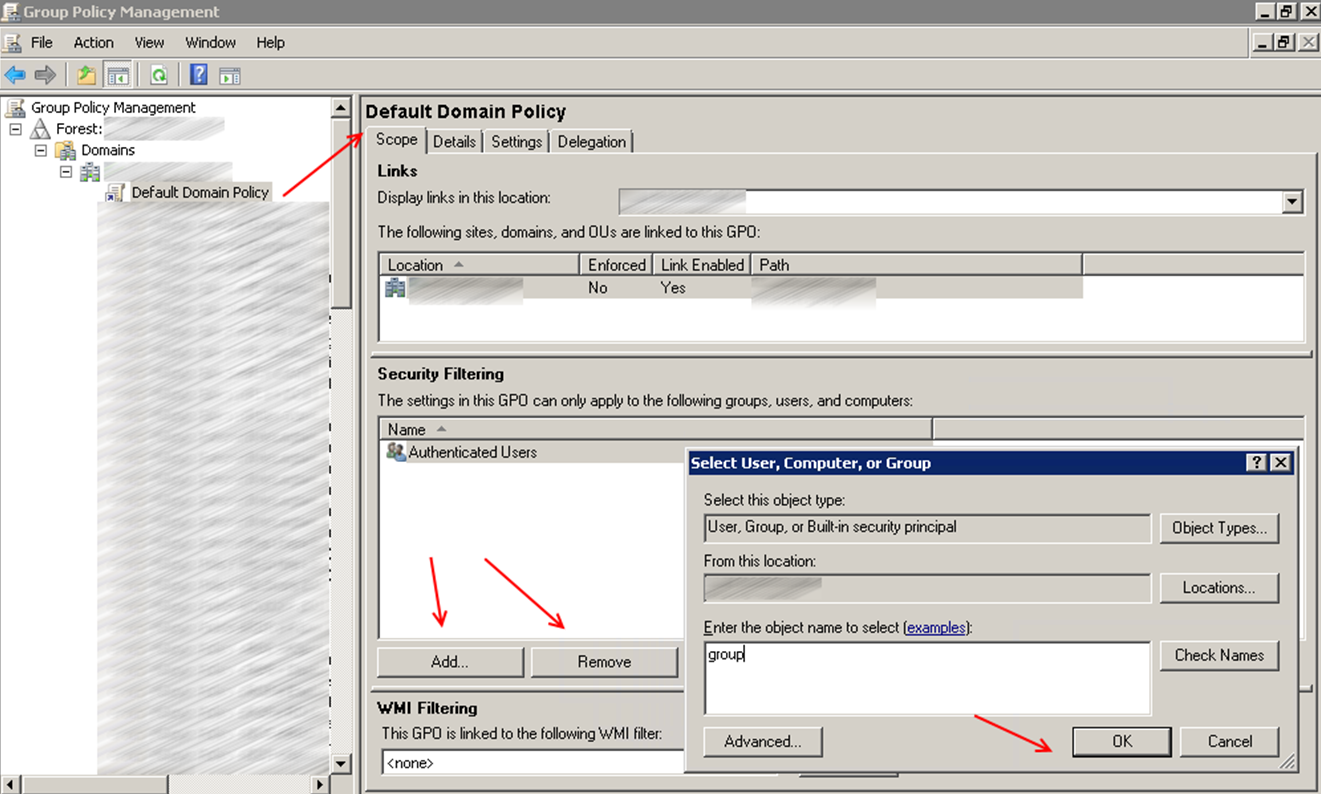
About problems and diagnostics
After installing updates, some policies stopped working.
The first thing I noticed was that the policy that mounted the network drive to users stopped working. For a long time I didn’t understand and closed this problem with the Item-level targeting tools, and in the Security Filtering settings I returned the standard Authenticated Users group.
Item-level targeting can only be used for group policy preferences, and therefore this is not applicable in all cases.
What is the reason?
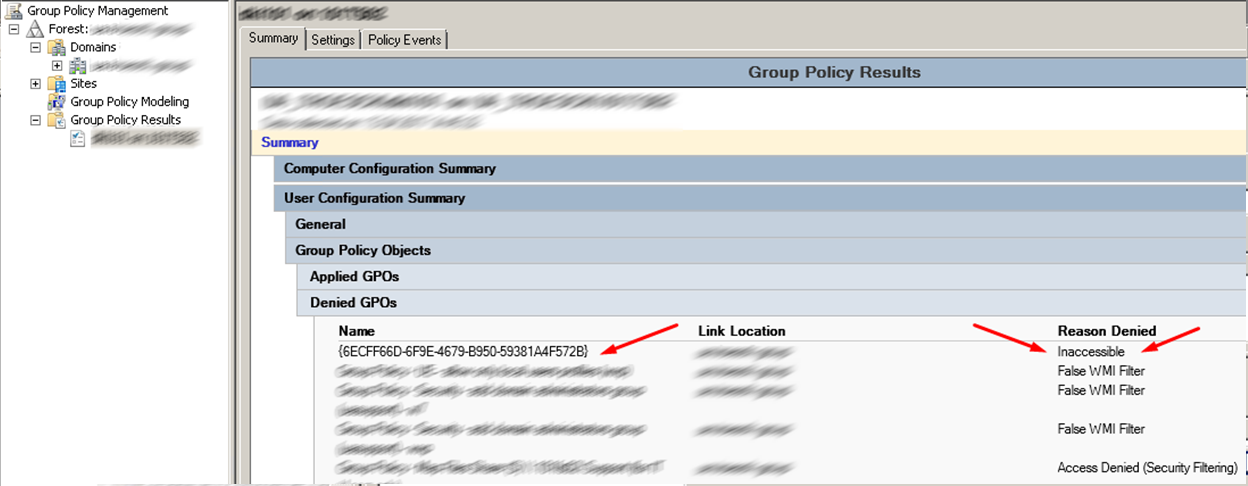
If you run the Group Policy Results wizard, you can see that the policy with the security filter was not applied due to an Inaccessable error.
I found a solution on GROUP POLICY CENTRAL , this is an excellent resource dedicated to group policies, and it has two articles on Security Filtering.
Individual computer or computer
Posted by Alan Burchill on 26 May 2010
How to exclude Group Policy Objects
Posted by Alan Burchill on 19 May 2010
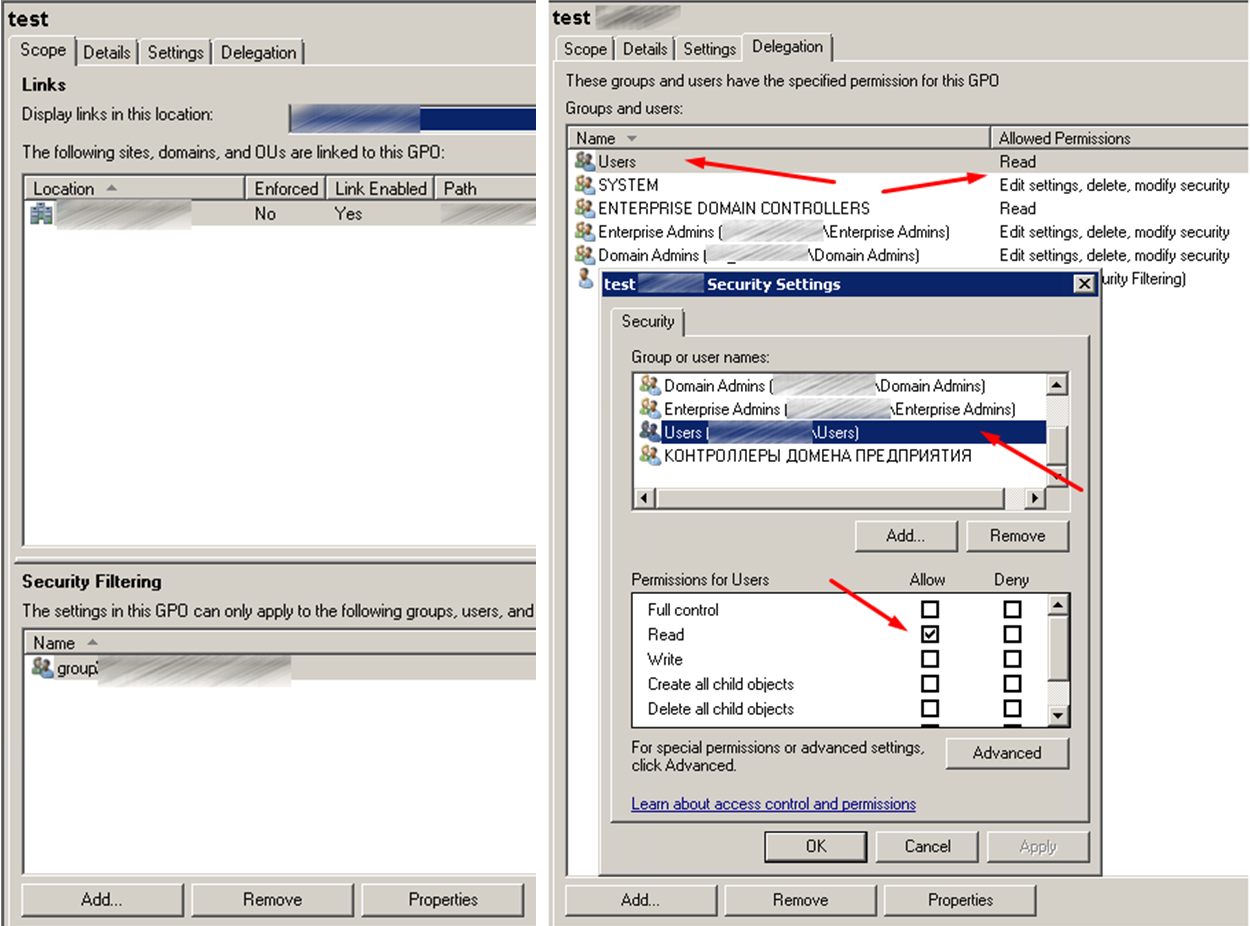
The author writes about the fact that the Authenticated Users group cannot be removed from the security filter and recommends using the GPO Delegation Advanced tab for filtering. It also says that the policy will work, but microsoft more often surprises with its updates.
You can never get “Inaccessible” (see image below). This is why the GPO will not be able to read the contents of the GPO.
I decided to just delegate the Users group read-only rights.
We check the Group Policy Results, the policy has been applied and is normally read.
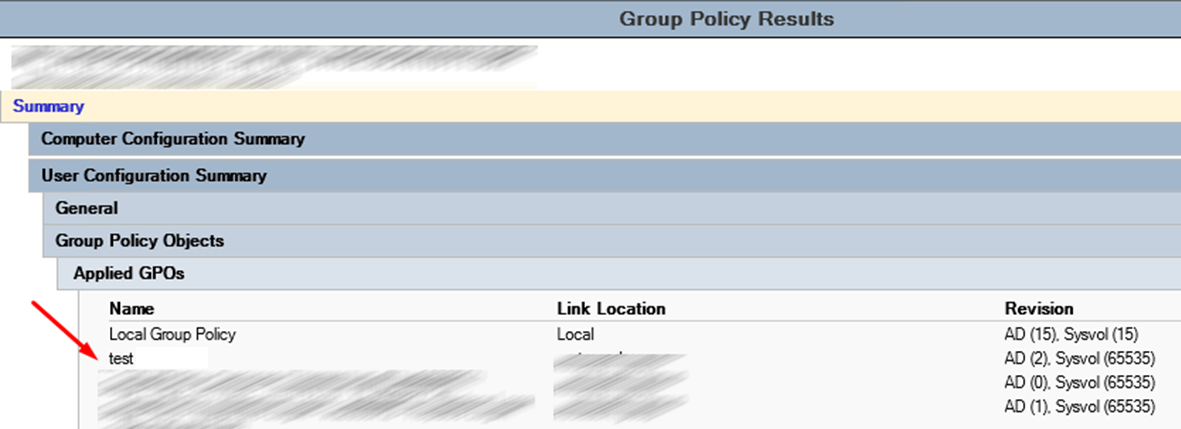
If you exclude a user from a group, the reason for the denial will be Access Denied (Security Filtering), everything works as intended.
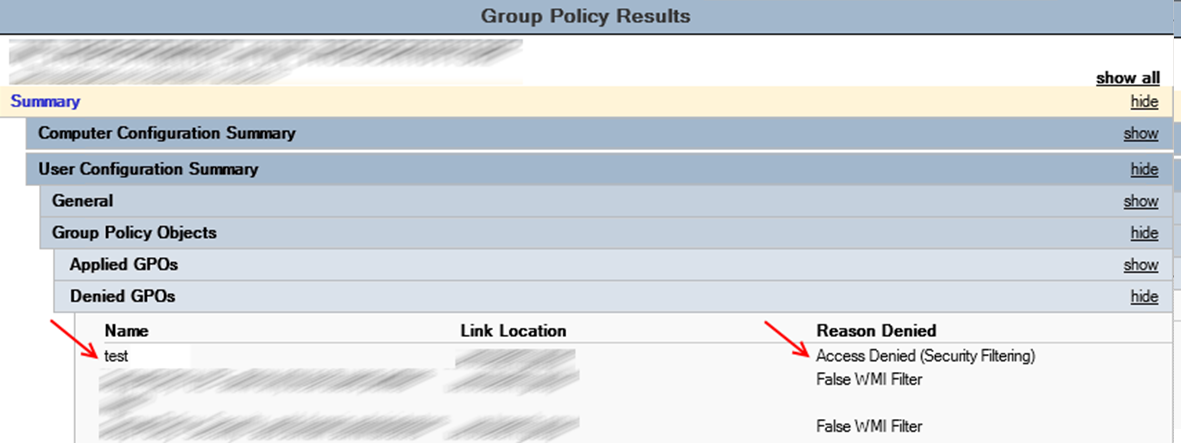
That's what they write about problems with Security Filtering in microsoft
Microsoft colleagues write that you need to grant read permissions to the Authenticated Users or Domain Computers group.
MS16-072: Security update for Group Policy: June 14, 2016
Symptoms
This is a grouping of computers that have been chosen.
Cause
This can be a group of users.
Resolution
Use the Group Policy Management Console (GPMC.MSC) and follow one of the following steps:
- Add the Authenticated Users Policy group (GPO).
- If you are using security, add the Domain Computers group with read permission.
Detailed parsing MS16-072 is already present at Habré - a great article
Update MS16-072 breaks Group Policy. What to do with it?
Posted by Vital Koshalew on June 27, 2016
More experienced colleagues suggest changing the domain scheme. An interesting solution, but for myself I do not see the problem with my hands setting up the security of the GPO.
A few words about the exclusion of users.
This is a great tool when you need to exclude users or PCs from the policy area.
Example: With such a policy on terminal servers, I hide local disks in Explorer from users. The policy is applied to the standard Authenticated Users group, and in the security settings for the Administrators group, I assign Denay rights to the Allow Apply group policy.
This has to be done because by applying the policy to the default Authenticated Users group, you automatically apply it to all users, because administrators are automatically members of the Authenticated Users group.

PS I hope this article will be useful.
Pps
This article is primarily intended for less experienced and novice domain administrators. The way in which you will solve the task or problem is yours and only your responsibility. Use the Users, Authenticated Users, Domain Computers groups or change the domain scheme, this should be your conscious decision. You need to understand what you are doing, why, and where to look if something went wrong.
Source: https://habr.com/ru/post/327648/
All Articles
