Security Week 17: DoublePulsar broke free, a hundred thousand Linksys found holes, SMSVova expelled from Google Play
 While the security men sighed and gasped over the archive of the NSA's hacking tools, which were merged into the ShadowBrokers Network, serious uncles from the dark side launched new state exploits into the business. And, as it turned out , not only the exploits - a superficial scanning of the Internet revealed a large number of machines infected with the freshly-powered DoublePulsar backdoor.
While the security men sighed and gasped over the archive of the NSA's hacking tools, which were merged into the ShadowBrokers Network, serious uncles from the dark side launched new state exploits into the business. And, as it turned out , not only the exploits - a superficial scanning of the Internet revealed a large number of machines infected with the freshly-powered DoublePulsar backdoor.The situation is more serious nowhere. DoublePulsar is a tricky fileless backdoor and allows you to remotely run code that will do everything the hacker wants you to do with the system. Here you can see a detailed analysis of the work of DoublePulsar, we'll talk a little about that.
For infection, exploits are used for vulnerabilities in Windows SMB Server. Back in March, Microsoft patched these holes in the MS17-010 update. But let's remember a similar story nine years ago, when the MS08-067 update covered a hole through which the Conflicker worm ran. And you know what? Almost ten years have passed, and you can still find vulnerable Windows servers for him. Because "it works - do not touch." That does not touch, and will not touch.
Dan Tentler, founder of the Phobos Group, decided to scan the Internet for leakage vulnerabilities. Of course, he found millions of holes in servers - the patch was released only a month and a half ago, administrators do not like to fuss. And then "polled" the systems found, knocking on port 445. From within 65 thousand cars (about 3.1% of the vulnerable) responded lively to the DoublePulsar. ¯ \ _ (ツ) _ / ¯
')
It is unlikely that the NSA spread its tentacles so widely. Rather, it is the result of the ShadowBrokers Benefit. They laid out a ready-made cyber-opener, simple to use and very dangerous, and the result was not long in coming. And even the fact that DoublePulsar does not work on new versions of Windows is not particularly inspiring. Pandora’s box is open, the number of compromised servers on the Internet will multiply. Roll patches, gentlemen admins!
20 models of linksys routers contain vulnerabilities
Remember linksys? In ancient times, this was the name of the network devices that Cisco made for simple SOHO users. Four years ago, they were bought by Belkin, known for their USB cables and network filters. However, this did not really change anything; quite decent home switches and routers continue to appear under the brand Linksys. What is it for me? And, IOActive found a bunch of holes in them.
News Research Vulnerabilities in network devices of this class are often found. This time, IOActive went through the latest Linksys models, in which they found a dozen vulnerabilities. Holes allow you to remotely “hang up” and reboot the device, drain the firmware from it (who needs it?), And steal the WPS PIN code, which is more interesting. And even more interesting is the ability to organize a backdoor in a router to execute any commands with root-rights. True, for this you must first authenticate to the device.
 IOActive called vulnerable models - these are new devices of the EA and WRT series, with a total number of 20 pieces. Having scanned the Internet with the help of their beloved Shodun guards, they found 7,000 vulnerable routers. Such a modest figure did not suit them, so IOActive analysts speculatively counted the number of devices hidden behind firewalls - and counted one hundred thousand pounds! 70% of them work in the US, 10% in Canada, but we have almost none - less than 1%. Even Chile has overtaken us in using vulnerable Linksys, how can we live now?
IOActive called vulnerable models - these are new devices of the EA and WRT series, with a total number of 20 pieces. Having scanned the Internet with the help of their beloved Shodun guards, they found 7,000 vulnerable routers. Such a modest figure did not suit them, so IOActive analysts speculatively counted the number of devices hidden behind firewalls - and counted one hundred thousand pounds! 70% of them work in the US, 10% in Canada, but we have almost none - less than 1%. Even Chile has overtaken us in using vulnerable Linksys, how can we live now?As usual, the vendor was told about vulnerabilities long ago - back in January - but he is still working on preparing the update. In the meantime, the standard recommendations are to turn off the guest WiFi network, enable automatic update installation, change the admin password.
SMSVova Trojan Spy removed from Google Play
News On Google Play, there was recently a great System Update application for keeping the OS updated. It seems like you are putting it, and it is your Android patch, patch, patch without getting tired. This is the solution to all problems with mobile vulnerabilities. We will not wait for favors from the vendor, we will take them from Google Play! And yet you will laugh, but several million users have bought it.
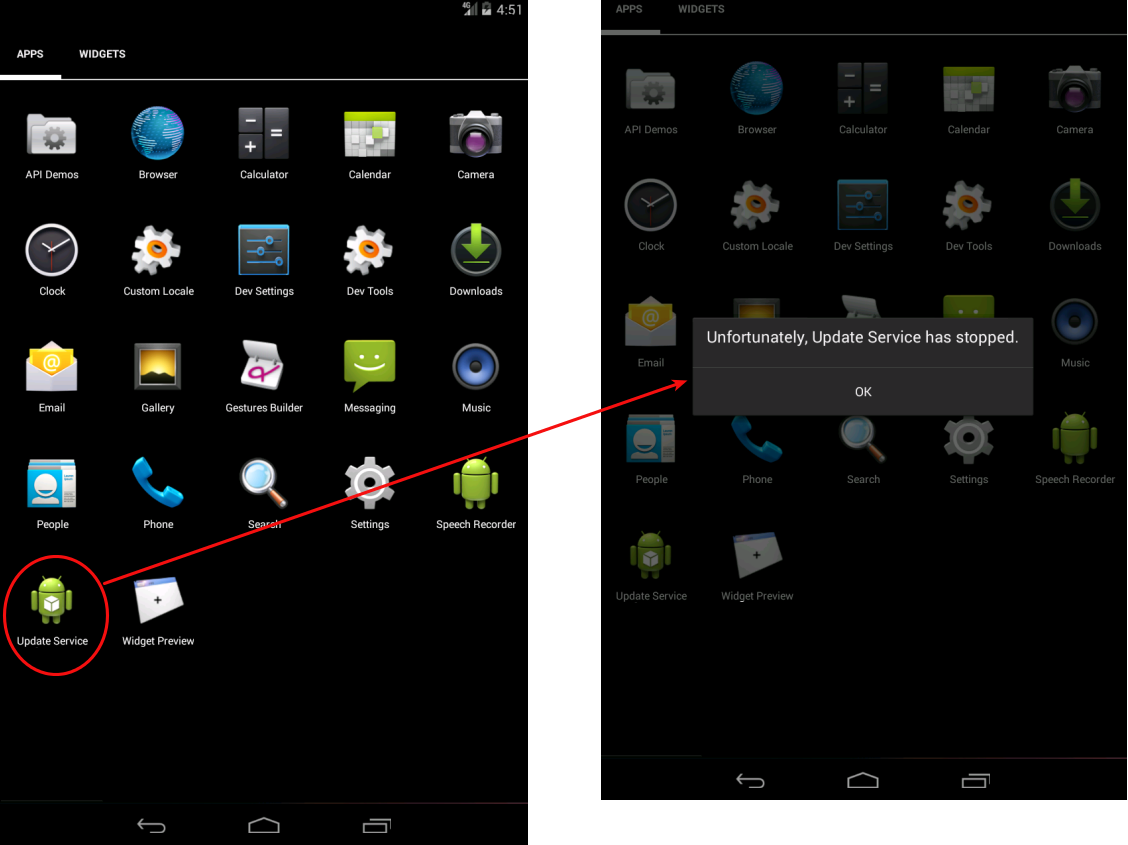
When System Update started, it showed a sad message that the service was stopped and supposedly closed. In fact, the SMSVova Trojan-spy (again these Russians!), Hidden in its depths, continued to work and sent somewhere to SMS-users all the data about the user's location. In addition, SMSVova can receive commands from the outside, also via SMS.
The useful utility has been on Google Play since 2014, VirusTotal has not been detected, and Google has bypassed all the increasing checks by simply not updating it, and there was no reason to check. Now, of course, from the System Update store is removed. Enough for him to follow us!

Antiquities
"GoodBye-839"
Resident non-hazardous virus, standardly affects loaded into memory COM-, EXE-and OVL-files. On Sunday, he performs the tune “Goodbye America” by the rock group “Nautilus Pompilius”. Intercepts int 1Ch, 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 68.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/327598/
All Articles