Threats to the WPA2-Enterprise wireless corporate network and how to protect

Not so long ago, together with Digital Security, we conducted a pentest of our corporate wi-fi-network. Today, with colleagues, we’ll tell you what could threaten a wireless network built on the basis of WPA2-Enterprise with domain account authentication and how to protect against this.
About WPA2-Enterprise
Before we talk about attacks and ways to protect against them, let us recall the main features of the WPA2-Enterprise standard.
Authentication. In order to connect to the network, the client must authenticate to the AAA server. Often this is the RADIUS server. Authentication can be performed using a domain password, client certificate, etc. (EAP).
Encryption. Organized by the AES algorithm. The dynamic encryption key, individual for each client (802.1X), is generated at the time of authentication on the RADIUS server. This key can be updated periodically as you work without breaking the connection.
WPA2-Enterprise operation scheme.
The process of connecting a client to a wireless network can be briefly described as follows.
When connected, client data is transmitted to an access point / controller using the 802.1x protocol. The information is then sent to the RADIUS server, where the client is authenticated: the RADIUS server checks whether such a client with the specified login and password is in its lists and whether it can be connected.
After successful authentication, the access point connects the client to the network.
Let's take a closer look at the authentication process on the RADIUS server:
- A client wishing to be authenticated will request to start a communication session.
- In response, the callee (the RADIUS server) sends arbitrary, but different, information to the client each time.
- The client adds a password to the received request and calculates a hash from this line.
- The RADIUS server performs similar actions with the value sent and compares the result. If the hash values match, then authentication is considered successful.
Periodically, the RADIUS server sends a new challenge to the client, and the authentication procedure is repeated again.
Such an authentication mechanism is called “challenge – response” and occurs according to one of the EAP protocols - PEAP-MSCHAPv2 .
What are we protecting ourselves from?
You need to know the enemy in person, so here’s a brief look at the mechanics of possible attacks against the WPA2-Enterprise network with domain account authentication.
Connect clients to a false access point. Knowing the network name SSID (ESSID, if the network is built on several access points) and the MAC address of the access point (BSSID), an attacker can deploy an illegitimate access point.
To increase their chances of success, the attackers use the following simple techniques:
- an illegitimate access point has a more powerful signal than a legitimate one;
- an illegitimate access point is deployed where the signal of legitimate access points does not reach, but where there are clients that usually connect to this network.
In order to connect to this access point, the attacker deploys his RADIUS server, to which an illegitimate access point will connect. This RADIUS server has no task to authenticate the client and verify that it has entered the correct password. The main thing is to get the authorization data from the client, the login and the answer to the challenge presented by the false Radius-server. Their attacker will use for offline password guessing and subsequent connection to the target corporate wireless network.
Without monitoring the broadcast, locating an illegitimate access point is not always easy. An attacker is unlikely to look like a man with a huge backpack, a bunch of antennas and a diesel generator on a trolley.
For example, for their Pentest, colleagues from Digital Security use a portable household router with a built-in battery (like this ). Reflash using OpenWRT and install a custom package. The output is an access point with a built-in RADIUS server, which can, if necessary, listen to the air and collect data. If you wish, you can even use a regular phone.
The locations of such access points are limited only by the ingenuity of the cracker. If the victim's office is located in a business center, then you can deploy an access point in the lobby to the turnstiles or the lobby with sofas. It is convenient to place such an access point in the elevator car: it moves away from the legitimate access points with great speed, so the client device is trapped and is likely to connect to a false access point. The attacker can even ride with a false access point on corporate transport, which carries employees to the subway after work.
Forced deauthentication . If the client is already connected to a legitimate access point, then it must somehow be disconnected from it (forcibly deauthenticated) in order to reconnect to a false one. The attacker listens to the broadcast. To do this, he puts his wi-fi-adapter in monitor-mode. Usually for this purpose use a set of utilities aicrack-ng . With his help, the attacker begins to send messages to wireless clients that a legitimate access point to which the client is already connected is disconnected and leaves the air. This effect is achieved with the help of wi-fi (Management Frame) injection frames , namely: deassociation and deauthentication frames .
As a result, the client disconnects from the access point and begins to search for a new access point with the same ESSID. In this situation, an access point with a more powerful signal just comes in handy. The client device is trying to connect to it. If the client authenticates to a false RADIUS server, the attacker can capture the user name and authentication MSCHAPv2 session.
How to defend
These attacks can be prevented by using the following protection measures:
| Attack | Measure |
|---|---|
| Connecting clients to a false access point | monitoring of the air to identify fake access points; user authentication using client certificates |
| Client Forced Deauthentication | monitoring of the air to detect attempts to forcibly deauthenticate customers of wireless networks; 802.11w activation (Protected Management Frames, PMF) on the controller |
Further we will tell how each of the methods of protection is implemented in our case.
Monitor the air and identify false access points. It is possible to organize monitoring of the air using standard means of access points and a WLAN controller. The following discussion focuses on Cisco devices.
To do this, the Off Channel Scanning mechanism is activated on access points, in which it periodically scans the air on all channels. As a result of such monitoring, it identifies the least loaded channel and third-party access points (in Cisco terminology, Rogue AP). Data from access points is sent to the controller to which they are connected.
On the controller itself, the rule of classification of third-party access points is configured, according to which all extraneous access points with an SSID equivalent to ours are considered illegitimate (Jore in Cisco terminology). You can read more about configuring a Cisco controller in this series of articles.
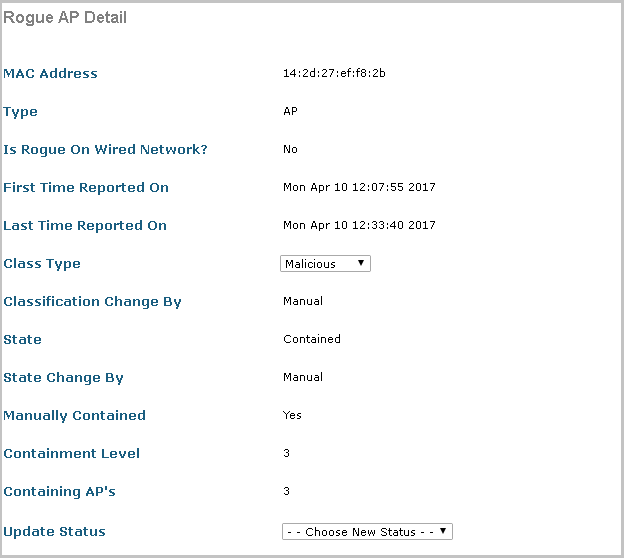
This is the message about the found illegitimate access point in the web interface of the controller.
681 Mon Apr 10 12:10:55 2017 Rogue AP: 14: 2d: 27: ef: f8: 2b.
682 Mon Apr 10 12:10:55 2017 Rogue AP 14: 2d: 27: ef: f8: 2b is advertising our SSID. Auto containing as per WPS policy
Messages in the controller logs when detecting an illegitimate access point.
In the monitoring system (in our case, it is Nagios), the SNMP poll of the controller is configured. When an illegitimate access point is detected, a message is displayed on the monitoring screen containing:
- MAC address of an illegitimate access point;
- The MAC address of the access point that detected it.
Using the table of the MAC address of the access point and its location, you can determine the approximate location of the illegitimate access point.
The message in the monitoring system that an illegitimate access point was recorded.
Monitor the air for attempts to forcibly deauthenticate wireless clients . As part of the intrusion detection system (IDS), the Cisco controller has a standard set of standard signatures with which it can recognize the potentially dangerous behavior of customers and neighboring access points. This includes multiple attempts to deauthenticate, authenticate, associate, etc.
Wed Apr 12 10:17:53 2017 IDS Signature attack detected. Signature Type: Standard, Name: Auth flood, Description: Authentication Request flood, Track: Per-signature, Detecting AP Name: OST_Reception, Radio Type: 802.11b / g, Preced: 5, Hits: 500, Channel: 11, srcMac: 14: 2d: 27: ef: f8: 2b
Multiple Authentication Messages in Cisco Controller Logs
The controller in question also has intrusion prevention mechanisms (IPS). For example, if you identify an illegitimate access point, you can counteract the invasion by the same means that are used in the attacks - deauthentication and deassociation. The controller can be configured so that when an access point appears with an SSID that matches the controller being advertised, the auto contain mechanism will start: access points that capture the signal of the illegitimate access point start sending deauthentication frames to the clients on behalf of this access point. As a result, it becomes very difficult for the client to work and transmit data to an illegitimate access point.
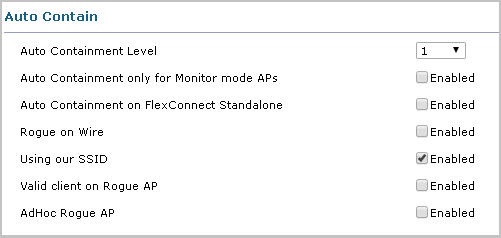
Configure automatic deauthentication of clients that connect to an illegitimate access point on a Cisco controller.
You can receive information from the controller about IDS events in two ways: sending SNMP traps to the monitoring system or parsing the controller log.
The monitoring system also receives a message with the MAC address of the illegitimate access point and the MAC address of the legitimate access point that detected it.
To protect against forced deauthentication, 802.11w is activated on the controller (Protected Management Frames, PMF). This mode prevents attacks aimed at forcibly disconnecting the client from the legitimate access point and reconnecting to the illegitimate one. When using 802.11w, the frames of Disassociation, Reassociation, Deauthentication are signed by a key known only to authorized clients and legitimate access points. As a result, the client can determine whether this frame was received from a legitimate point or not.
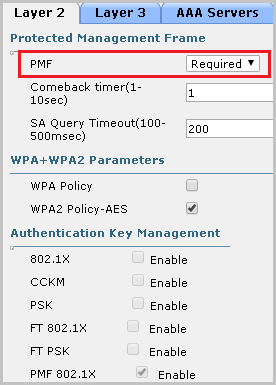
Enable 802.11w PMF in the Cisco Controller Web Interface .
Authentication by user certificates. The essence of the method lies in the fact that the client is authenticated by a user certificate issued by a trusted certification authority. This certificate is placed in the user certificate store of each wireless device. When connected, an authentication server (AAA server) verifies the certificate presented by the device with the established policies.
An attacker can penetrate a network with authentication under a client certificate only by stealing a device with a certificate and having a login / password to log on to the device. But here too, the loophole quickly closes: when the theft becomes known, the certificate can be quickly withdrawn at the certification authority. The authentication server is notified that the certificate has been revoked, so the attacker will not be able to connect to the target network using the certificate.
Below is a diagram of how a WPA2-Enterprise wireless network with user certificate authentication is implemented with us.
Let us consider in more detail the following components of this scheme.
RADIUS server. Accepts requests from devices to connect wireless devices (radius-clients).
Network Policy Server, NPS . Performs authentication and authentication. The conditions for connecting to a wireless network are also configured here. For example:
- certificate request;
- certificate issuer;
- connection schedule.
Active Directory Domain Server ( AD DS ). Contains database with user accounts and user groups. In order for NPS to receive user data, you must register NPS with AD DS.
Active Directory Certificate services. Public Key Infrastructure (PKI).
Root server. Root certifying center. Here, the certificate of the certificate authority is generated on the basis of the private key. With this certificate, a certificate is signed for the intermediate certification authority.
Usually, this certificate, together with the key, is exported to a USB flash drive, hidden in the basement, in a safe, so that there is no physical access to outsiders. The server itself is disabled.- Subordinate server. Intermediate Certification Authority. The certificate of the intermediate certifying center is stored here. In the future, client certificates are issued here, which are signed by an intermediate certificate. Using Active Directory group policies, it instructs client devices to request a certificate for a user. The certificate is issued and goes to the user device storage.
The scheme with a subordinate server is advantageous in that when the intermediate certificate is compromised, the root certificate will not be affected in any way. In this case, the compromised certificate is simply revoked through the root server, and the subordinate server is deleted.
That's all for today, ask your questions in the comments.
')
Source: https://habr.com/ru/post/327542/
All Articles