What is the Cyber-Kill Chain and why should it be taken into account in the protection strategy?

Modern targeted attacks are a whole range of activities, with the result that hacking and network infection do not occur “suddenly from nothing”. This is preceded by a whole set of actions. The Cyber-Kill Chain model and its enhanced version describe all phases of an attack.
The changing landscape of threats, their frequency of occurrence, complexity and target nature of attacks requires the evolution of existing security rules with a transition to a combination of technologies to prevent, detect and respond to cyber attacks.
')
Most organizations have the means to detect known attacks, although companies can sometimes occur without such solutions. The most difficult thing is to stop the unknown attacks , which are specifically designed to circumvent the existing protection by changing signatures and patterns of behavior.
Many organizations have already invested heavily in creating their own threat hunt team and / or in transferring to service providers the critical task of continually improving their protection techniques and finding the best tools and ways to secure their intellectual property and digital assets.
What for?
The current state of the threat landscape
Much has already been written about this, so we’ll dwell on this issue thesis.
In our opinion, there are 3 main factors for the success of the "bad guys."
Factor 1. Evolution of attacks
Malicious software is becoming more and more sophisticated. Techniques for attacking themselves are also developing: now, increasingly, the target is not chosen randomly. The attacks became directed, coordinated and using various vectors. In addition, financial motivation plays a significant role.
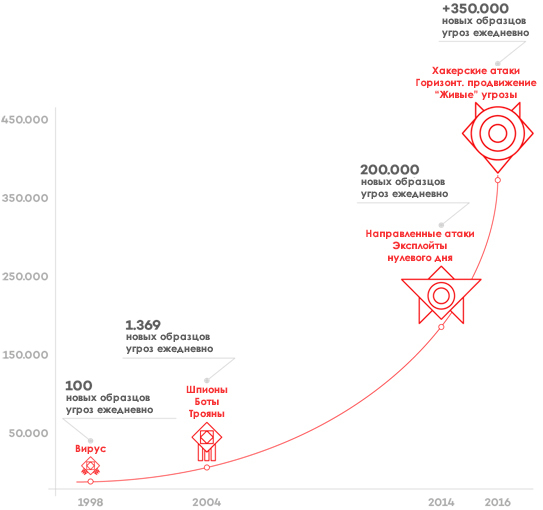
In general, the last phrase is the key. Cyber crime is a very attractive and profitable business. Malefactors use more and more technical and economic resources that allows them to develop more sophisticated attacks. As a result, more and more attacks and they are becoming more complex.
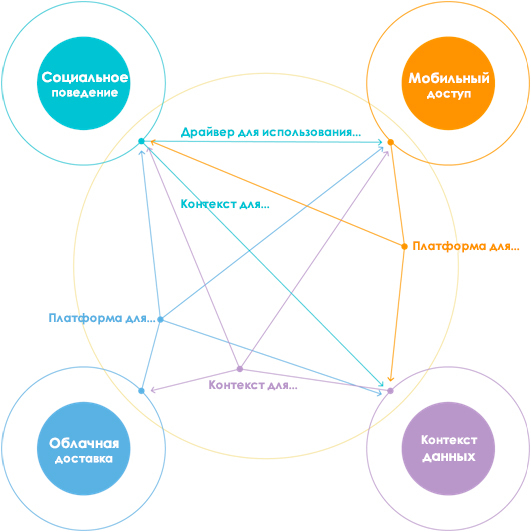
Factor 2. New digital life
Our modern digital behavior occurs in a complex, interconnected and hyperdynamic environment. Now the perimeter is where the user is. The complexity of IT systems increases vulnerability to cyber threats.
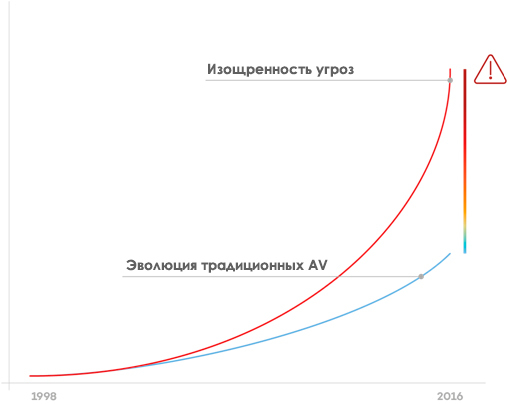
Factor 3. The traditional approach to protection
It is not by chance that we are increasingly hearing about solutions for the protection of the “next generation”. Indeed, in the overwhelming majority of cases, the defense is built on the basis of traditional solutions, which are characterized by the following points:
• Based on signature files. Their size becomes huge due to the huge number of malicious programs.
• Detect predominantly known threats. Since Since threats have become more sophisticated, companies need to devote more and more time and resources to researching attacks.
• Based, as a rule, on the behavior of old threats. These detection systems are outdated, they work, as a rule, only when an attempt is made to penetrate a computer of a known threat or, at best, an object suspicious from the point of view of traditional technologies. They do not perform deep activity monitoring with a causal relationship analysis.
• Do not offer attack information. Due to the increasing complexity of IT infrastructures, the emergence of new models of digital behavior and new platforms, and because of the lack of deep monitoring of activity, traditional protection cannot ensure the traceability of attacks and their effectiveness.
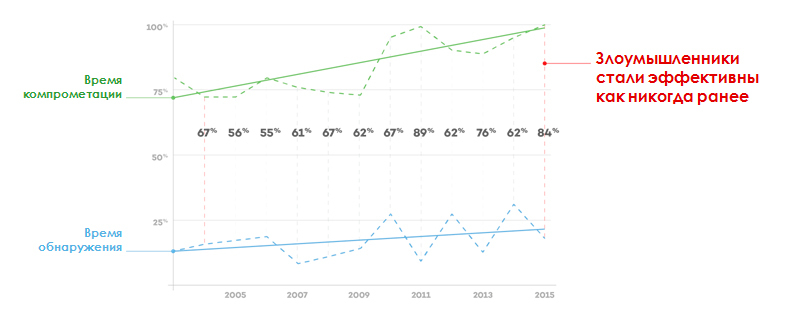
Detection gap
As a result, we see an increasing gap in the detection of unknown threats and attacks. For example, according to the Verizon Data Breach Investigations Report 2016, there has been a steady increase in incidents when the system’s compromise time took less than a day. Yes, while the number of incidents is also growing, when the time of their detection was less than a day, but the gap between these indicators is significant and it is growing. And this suggests that the attackers are becoming more effective.
In addition, unknown threats are a window of opportunity. According to IDG Research, DARK Reading, 18% of new malicious programs go unnoticed for the first 24 hours , and 2% of threats can go unnoticed even for 3 months after infection.
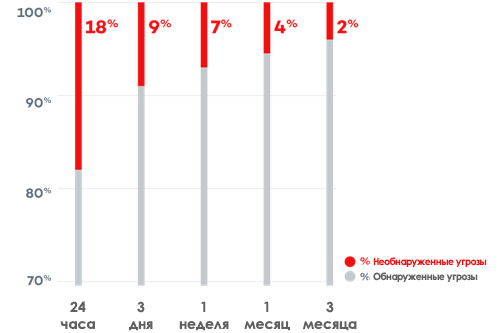
But beyond that, there is another serious problem: according to the Verizon Data Breach Investigations Report 2016 , 99% of the threat samples “live” for no more than 58 seconds ! In fact, most malware is only observed once. This shows how quickly hackers modify the packaging of their code if each sample “looks” differently to avoid detection.

And look: the threat can compromise the system in minutes or hours, while the reaction of companies usually takes weeks, months or even years .
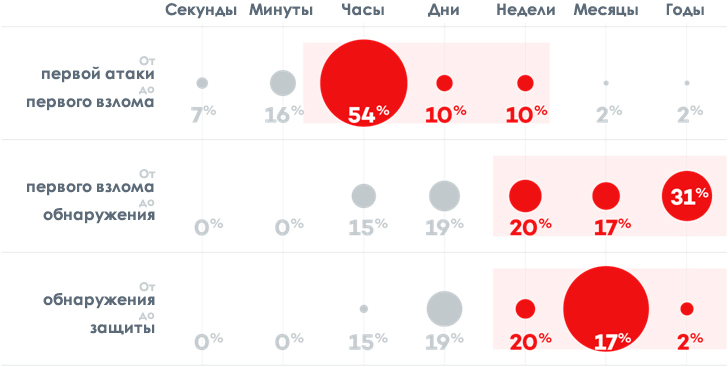
Where, where and what to expect threats
If we talk about the types of attacks, we can distinguish the following main types:
• Malicious software. Executable files and sometimes fileless threats
• Exploits. Built-in malicious code, script-based attacks
• Insiders. Theft of usernames and passwords, data leakage
• Hacker attacks. Horizontal advance and coordinated attacks
It is interesting to look at the statistics of the sources of information security incidents presented according to the Global State of Cybersecurity - PwC.
Internal sources

External sources

In addition, according to the Verizon Data Breach Investigations Report 2016, endpoints are becoming more desirable goals. Attackers need to get to the end point, because from there they can access other targets, extract information, steal credentials, gather information, or deploy other attacks. Here, for example, the distribution of incidents depending on the purpose:
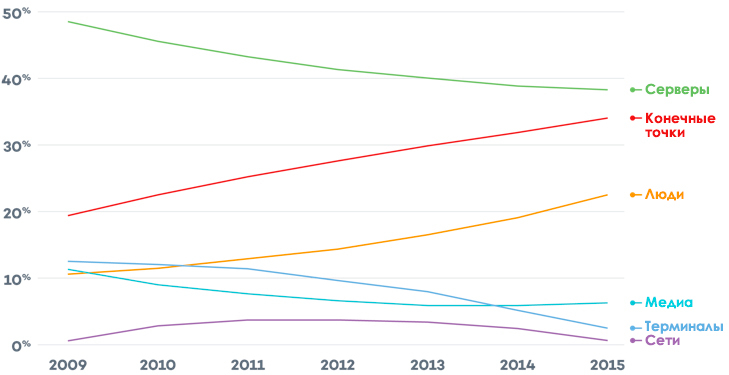
Moreover, modern attacks have become “hung up” on endpoint activity, user behavior, and data access. Often, enterprise information security budgets are focused on the perimeter of the network, and not on the end point. For this reason, according to Gartner, from 2% to 8% of corporate computers are infected.
Understanding how cyber attacks are carried out, and comparing the enterprise security strategy with their life cycle, show how to detect, stop and disrupt these attacks, recover from them, and where security operations should be strengthened.
In this article we want to talk a little about the well-known model of the life cycle of cyber-attacks called Cyber-Kill Chain (CKC) and its extension to the entire network. In general, this model is an excellent tool for understanding how companies can significantly enhance the defenses of their surroundings, catching and stopping threats at each phase of the attack life cycle. CKC shows us that while hackers need to go through all stages of the process, we, the defensive side, need only “stop” the attack at any stage of the process in order not to allow the attack to fully achieve its goal.
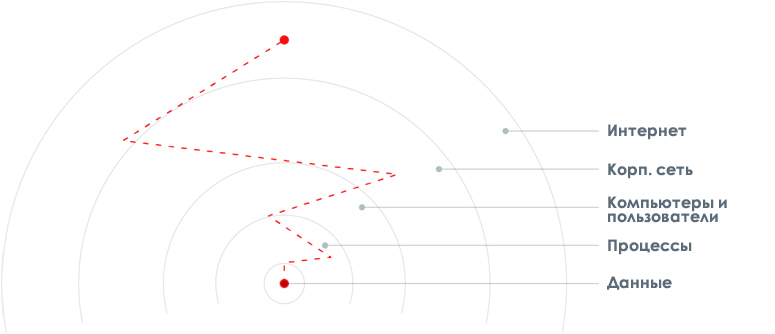
Also note that most of the company's valuable assets are stored on workstations and servers. Thus, all intruders want to reach them by gaining access to these critical assets. Stopping a hacker at an endpoint significantly reduces the likelihood of his success, simplifying efforts to break the chain and significantly increasing the efficiency and effectiveness of security solutions.
Understanding Cyber-Kill Chain
The term Cyber Kill-Chain was originally proposed by Lockheed Martin as part of their Intelligence Driven Defense [1] model to identify and prevent cyber-invasion processes.
This model defines what attackers must do in order to achieve their goals by attacking the network, retrieving data and maintaining a presence in the organization. Thanks to this model, we know that blocking hackers at any stage breaks the entire chain of attack. Again, to achieve success, hackers have to go through all the stages, and, in turn, we, the defending side, need only block them at any stage in order to achieve at least minimal success.
The end point is the inevitable point through which all attacks go, and, consequently, stopping the attack at this level significantly increases the chances of counteracting any cyber attack. The probability of success will be higher if hackers are stopped in the early stages.
In addition, each invasion, and the traces that it leaves at the end point, are a chance to learn more about the hacker's actions and use this information to your advantage. The better we understand hackers and their methods of carrying out attacks, the more likely we will be able to build a more effective defense.
The Cyber-Kill Chain model indicates that to accomplish their atrocities, hackers must always go through the following basic steps:
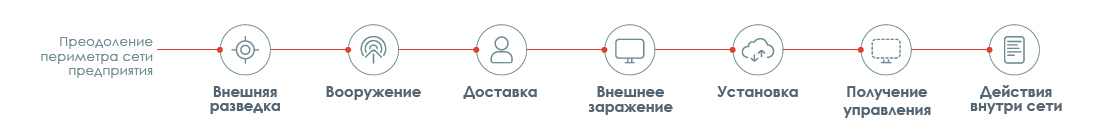
Stage 1. Foreign Intelligence
This stage can be defined as a phase of choosing a goal, identifying features of an organization, specific requirements in a given industry, choosing technologies, studying company activity in social networks or via mailings.
In essence, a hacker is trying to get answers to such questions: “Which attack methods will work with the greatest degree of success?” Or, for example, “Which of them will heal the whole from the point of view of investments and resources?”
Stage 2. Armament and packaging
Various forms are possible: web application exploitation, standard or specially crafted malware, vulnerabilities in various documents (PDF, Office or other document formats) or watering hole attacks [2]. Usually they are prepared with very specific knowledge of the goal.
Stage 3. Delivery
Transferring the required (malicious) content either at the initiative of the victim (for example, the user visits a malicious website, as a result of which malicious programs are transmitted, or he opens a malicious PDF file), or at the initiative of a hacker (SQL injection or compromised network service).
Stage 4. Infection
After delivery to the user's computer or device, the required (malicious) content is deployed, being established in the environment. This usually happens when using a known vulnerability for which a patch was previously available. In most cases (depending on the target), hackers are not required to incur additional costs for finding and operating unknown vulnerabilities.
Stage 5. Installation
Often the installation (implementation) occurs on the background of some external connections. Typically, the malware hides in these operations, imperceptibly penetrating the endpoints that can be accessed. Then the hacker can control this application without the knowledge of the victim.
Stage 6. Getting control
At this stage, hackers begin to control the victim’s assets using management methods (usually remote), such as DNS, Internet Control Message Protocol (ICMP), websites and social networks.
As a result, the hacker sends the required commands to the controlled "assets": what to do next and what information to collect. Methods used for data collection: screenshots, keystroke monitoring, password cracking, network monitoring for credentials, collection of critical content and documents. Often, an intermediate host is assigned to which all data is copied, and then they are compressed / encrypted for later transmission.
Stage 7. Performing actions at the victim
At the final stage, the hacker sends the collected data and / or disables IT assets while in the victim’s network. Then, measures are taken to identify other goals, expand their presence within the organization and (most importantly) retrieve data.
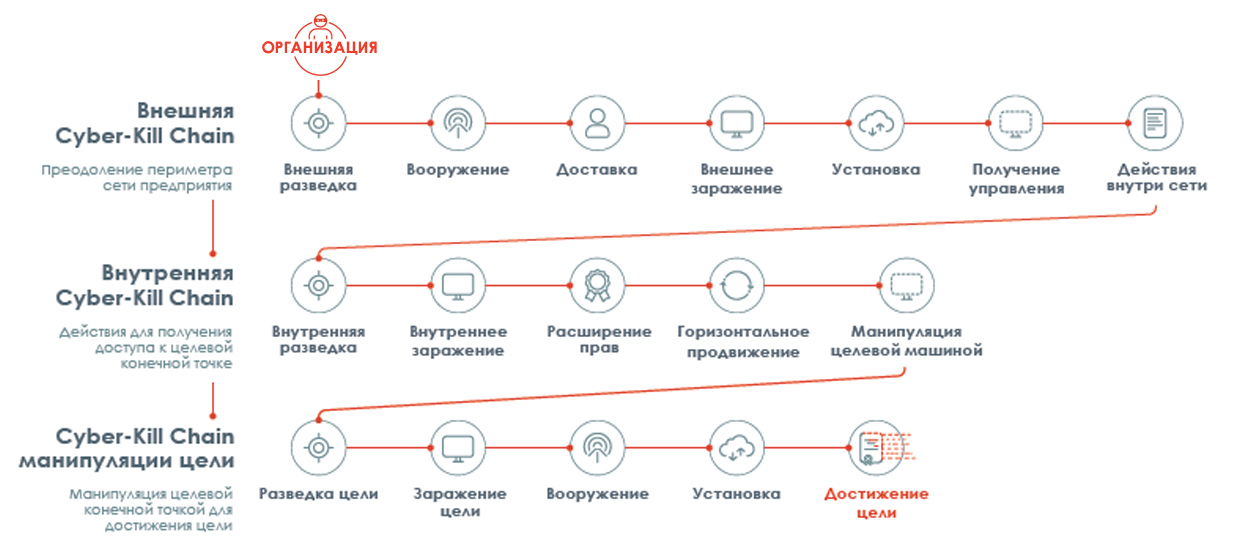
Then the chain repeats. In general, a feature of the Cyber-Kill Chain is that it is circular, not linear. As soon as the hacker has penetrated the network, he again begins this chain within the network, carrying out additional reconnaissance and performing horizontal promotion within your network.
In addition, it must be borne in mind that although the methodology is the same, but while inside the network, hackers will use other methods for the internal chain steps than when they are outside the network. In fact, after the hacker penetrates the network, he becomes an insider (a user with certain rights and presence on the network), and this prevents the company's security experts from suspecting the attack and realizing that the advanced stages of the expanded Cyber-Kill Chain are already underway.
Extended Cyber-Kill Chain Model
Cyber-Kill Chain is a circular and non-linear process when a hacker performs continuous horizontal promotion within the network. The steps that are performed within the network are the same as those that are performed if the goal is to gain access to the network. Although it uses various techniques and tactics.
The combination of external and internal Cyber-Kill Chain is called the expanded Cyber-Kill Chain model. This means adding additional stages, which actually represent almost the same set of stages, only have the word “internal” in their name, so the Cyber-Kill Chain becomes an internal Cyber-Kill Chain with its own stages (internal intelligence, internal armament, etc.) .).
Each stage of the attack after penetrating the victim’s network can take from several minutes to several months, including the final waiting time, when everything is ready on the spot and the attack can be launched.
Note that the hacker will wait for the optimal time to launch an attack in order to get the most out of it. The stages of reconnaissance and armament can take several months. By the way, it is very difficult to intercept these stages, because they are performed without connecting to the hacker. That is why it is very important that endpoint security tools analyze and control all systems and applications running on devices. This will significantly hamper the work of hackers, as a result of which the attack may become financially unprofitable for them.
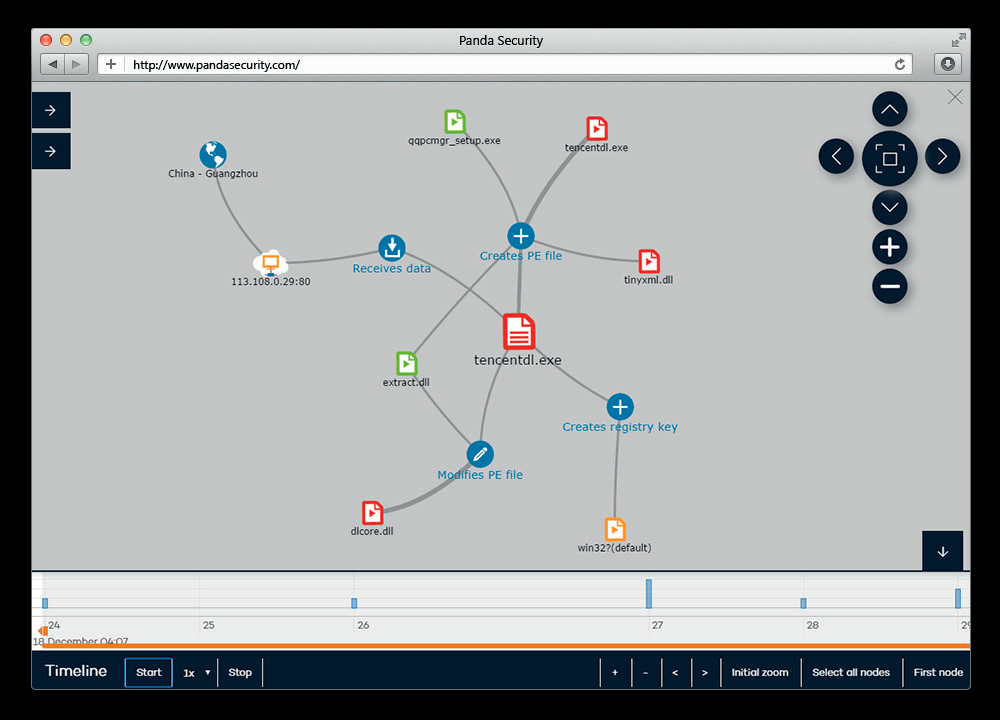
During the internal intelligence phase, attackers have access to the workstation of a certain user, where they will extract data from local files, network folders, browser history, as well as connect to Wiki and SharePoint. The goal is to find out how this machine can help you explore the network and allow you to reach other more valuable assets.
Taking advantage of missing patches, visibility of web applications and data transfer protocols, spoofing or even such simple things as default credentials, hackers will be able to move from workstations to servers using rights extension, horizontal promotion within the network and affecting individual target machines.
What is the solution?
Adaptive Defense within the framework of Cyber-Kill Chain
Hackers have goals, and they are willing to spend certain resources to achieve them. If endpoint security mechanisms can increase the cost of an attack (money, people, or time) beyond the expected cost, then hackers will be less likely to succeed or may even refuse to attack the organization.
All organizations must be prepared for a situation where the hacker gained access to the internal corporate network, logins and passwords, to all documentation and all network device specifications, systems, backups and applications, and to be able to act immediately.
A better security strategy for endpoints and an organization’s assets is needed to build a more sustainable enterprise. It will not prevent all attacks, but will stop most of them at earlier stages. One of the goals is to have effective defense mechanisms with extended Cyber-Kill Chain in order to slow down the hackers' actions, make the development of their attacks more expensive, and make it difficult for them to go to each subsequent stage.
If hackers cannot achieve their goals in an economically viable way, then they will most likely switch to other goals or will achieve similar goals when attacking other organizations.
The organization’s security strategy should take into account attacks that are carried out not only from the outside, but, most importantly, from the inside, because after the hacker penetrates the network, he becomes an insider with access to the end points along with their assets.
The traditional approach to security should be extended with methods based on understanding Cyber-Kill Chain and using technologies that can prevent a hacker from gaining access to endpoints, as well as stop them at any possible stage within the internal Cyber-Kill Chain.
Overlaying the protection strategy on the advanced Cyber-Kill Chain model shows how an organization can prevent, detect, neutralize, and carry out recovery actions throughout all phases of an attack, orienting the company's security to the same success criteria that hackers use.
This is difficult to achieve due to a number of factors: applications are becoming more complex and interconnected, they are vulnerable, because many programs are designed without the use of strict security principles, plus the human factor. Employees and partners also remain the main risk vector, and therefore there are opportunities for attacks based on social engineering.
For example, Adaptive Defense and Adaptive Defense 360 take into account the main factors that allow companies, when using these managed services, to prevent and detect more complex techniques and tactics of attacks at each stage of the advanced Cyber-Kill Chain . This helps security professionals within the organization to develop a security strategy that focuses on the advanced Cyber-Kill Chain.
Basic Adaptive Defense Principles
Prevent Known Threats
The search for known threats will not protect against their options or unknown attacks, but its enhancement with additional levels of security can preventively stop known threats when they are attempted to be deployed on the endpoint. Adaptive Defense 360 uses an extensive collection of reputation services to proactively block hackers during delivery using data from the cloud.
Detection of sophisticated malware and unknown threats
Adaptive Defense and Adaptive Defense 360 detect and block unknown malware and targeted attacks thanks to a security model based on three principles: continuous deep monitoring of all applications running on endpoints, automatic classification of processes on endpoints using big data of machine learning techniques on the cloud platform, and the possibility of in-depth analysis of the threat behavior of a technical expert if the process is not automatically classified.
Dynamic Exploit Detection [3]
At the stage of infection in the advanced Cyber-Kill Chain model, hackers use exploits to exploit code-level vulnerabilities, so that they can hack applications and systems, install and run malware. Internet downloads are a common vector for exploit attacks. Panda Adaptive Defense and Panda Adaptive Defense 360 provide dynamic anti-exploit options to protect against attacks against applications and memory.
Panda Adaptive Defense and Adaptive Defense 360 detect and block the current techniques used by hackers during the infection phase (heap spraying, stack substitution, ROP attacks and memory rights modification ...). Also, these solutions dynamically detect unknown attacks by monitoring all processes running on devices, and by using data correlation via machine learning algorithms in the cloud, they are able to stop any known and unknown infection attempts.
Adaptive Defense's anti-exploit technologies stop hackers in the early stages of an internal attack, detecting when a reliable application / process is compromised.
Mitigate attack
Protection of the next-generation endpoints should prevent and detect hackers at various stages of the Cyber-Kill Chain, but detection must be accompanied by a quick mitigation of the attack at its initial stages.
Panda Adaptive Defense 360 automatically and timely mitigates the attack, quarantining malware, stopping compromised processes or even completely shutting down the system to minimize damage.
Recovery
During its execution, malware often creates, modifies, or deletes system files and registry settings, and also changes configuration settings.
These changes or residues that may remain after may cause system malfunctions or even “open the door” for new attacks. Panda Adaptive Defense 360 restores the endpoints to their stable position before being infected with malware.
Expert Information
During the highly variable "landscape" of threats, their frequency of appearance, the complexity and directional nature of hackers, there can be no security technology that guarantees 100% efficiency, and therefore it should be possible to obtain expert information on each endpoint in real time to ensure complete visibility.
Employees of information security departments in enterprises should have an implemented plan to combat disruption of the reporting systems, to interact with law enforcement agencies, etc.
Panda Adaptive Defense and Panda Adaptive Defense 360 provide a clear and timely overview of malicious activity within an organization. This visibility allows security companies to quickly assess the scale of the attack and take appropriate action.
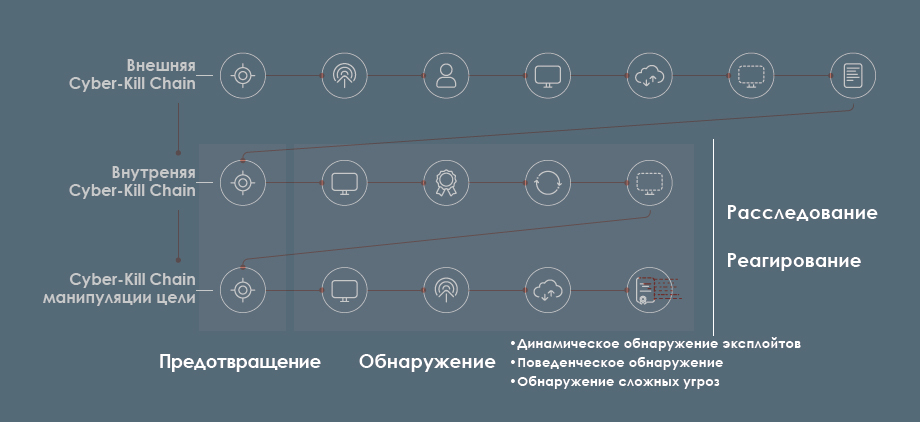
As a result, the mapping of Adaptive Defense 360 with the extended Cyber-Kill Chain model is as follows:
Conclusion
We see more and more complex threats and an increasing number of attacks. It is frightening that anyone can launch an attack thanks to the democratization of technology, the black market and open source tools. Moreover, any company is the target of modern attacks. Therefore, it is necessary to take this as a given and improve security policies, use more effective solutions.
Since hackers are driven by money and profit, then we must do everything to make their attacks unprofitable or too expensive. In most cases, this will stop intruders from further action.
In addition, it is necessary to fix the expert information for the traceability of the attack. In this case, we will be able to act more adequately in accordance with where the attacks came from, what techniques they used, what their actions were, what they did, why we did not find them earlier, etc.
All protection mechanisms should be aimed not only at preventing attempts to launch certain threats, but it is necessary to use mechanisms for detecting, blocking and eliminating the consequences of any type of attack before they can fully achieve their final goals.
In preparing the article used the following materials:
• Lockheed Martin's Cyber-Kill Chain: www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf
• Sean T. Mallon, Strategic Cybersecurity Leader & Executive Consultant, Black Hat 2016: Extended Cyber kill chain
• Verizon Data Breach Investigations Report 2016: regmedia.co.uk/2016/05/12/dbir_2016.pdf
• Miter's Cybersecurity Threat-Based Defense
• Microsoft's Security Development Life Cycle
• Gartner Research, G00298058, Craig Lawson, 07 April 2016
[1] Eric M. Hutchins, Michael J. Cloppert, and M. Rohan M.Amín, Ph.D., lntellígence-Dríven Computer Networking and Analysis of Adversary Campaigns and lntrusion Kili Chains.
[2] Watering hole attacks . A specific type of targeted attack, when the victim belongs to a particular group (organization, field of activity or region). In this attack, a hacker identifies a set of websites that are frequently visited by members of this group, and infects one or more of them with malware. In the end, some members of this group are infected. Malicious programs used in such attacks usually collect information about the user.
The name of this type of attack is associated with predators in nature, who expect to be able to attack their prey next to a watering place. Relying on websites trusted by team members makes this strategy very effective, even when attacking those groups that are resistant to target phishing (spear phishing) or other forms of phishing.
[3] Dynamic exploit detection . It is an innovative technology from Panda Security, based on monitoring all running processes on the endpoint or server and analyzing them in the cloud using machine learning technologies (ML), aimed at detecting attempts to use exploits to reliable applications.
This new technology is designed to stop attacks on workstations and servers in the very early stages of Cyber-Kill Chain. Restraining hackers and hindering their access to the device to such an extent that the economic meaning of the attack is lost, will prevent further attempts to attack. Ultimately, this will significantly increase the level of protection.
Demo Console Adaptive Defense 360
( Chrome Firefox) .
: demologin.pandasecurity.com
: DRUSSIAN_FEDERATION_C14@panda.com
: DRUSSIAN#123
- Adaptive Defense 360
1 .
Source: https://habr.com/ru/post/327488/
All Articles