How hackers attack web applications: bots and simple vulnerabilities

Public web applications are an attractive target for attackers. Attacks on web applications provide them with ample opportunities: access to the company's internal resources, sensitive information, disrupting the functioning of the application or bypassing business logic - almost any attack can bring financial gain for the attacker and losses, both financial and reputational, for the owner web applications. In addition, users of web applications are at risk, since successful attacks can steal credentials, perform actions on sites on behalf of users, and also infect workstations with malware.
When investigating attacks on web applications, we, first of all, set ourselves the task of identifying which attacks are most popular with cybercriminals and what are the possible motives for their actions, and also identify the main sources of threats for various industries. Such data allows us to understand what aspects should be paid attention to when securing web applications. In addition, we consider the distribution of types of attacks and activity of attackers, depending on the scope of the company, as well as the dynamics of changes in the nature of attacks during the year.
')
To collect the initial data on the attacks, we used the data obtained during pilot projects for the implementation of the PT Application Firewall (PT AF) application-level firewall in 2016. The pilot projects were attended by government agencies, organizations in the field of education, finance, transport, industry and IT. Among the systems under consideration there are both Russian and foreign companies. All the examples of attacks in this study were manually checked for false positives and are reliable.
The popularity of attacks by industry
Most often, during the pilot projects, there were “Implementing SQL statements” and “Executing OS commands”; such PT AF attacks were recorded in more than 80% of the systems. Path Traversal ranks second in popularity among the identified attacks. It is obvious that first of all the attackers try to use the most simple attacks that do not require special conditions for execution. Basically, a lower percentage of attack detection indicates a higher level of complexity or the need for special conditions for its implementation, for example, the presence of the function of downloading files in a web application or performing certain actions by users.
When ranking the most popular attacks, we excluded attacks that were carried out by special software for automated scanning of a web application for vulnerabilities, for example, Acunetix, sqlmap.
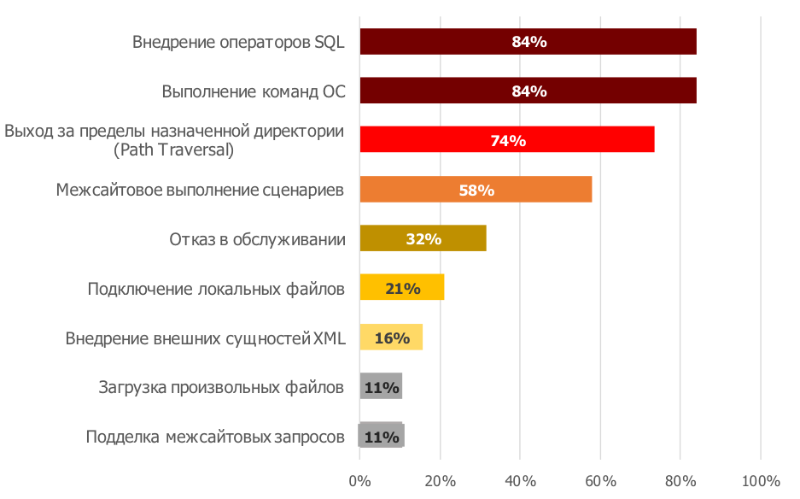
Rating of the most popular attacks (share of web applications)
Most of the attacks in this rating exploit critical vulnerabilities and can lead to a complete compromise of the web application and the server, which could allow an attacker to gain access to local network resources.
The ratio of types of attacks recorded during PT AF work and their number vary depending on the industry to which the system under study belongs. Malefactors pursue different goals, while the skill level and technical capabilities of violators also differ. The diagrams show the average number of attacks per day per system, as well as the ratio of the number of attacks that are performed manually and using automated scanning utilities.
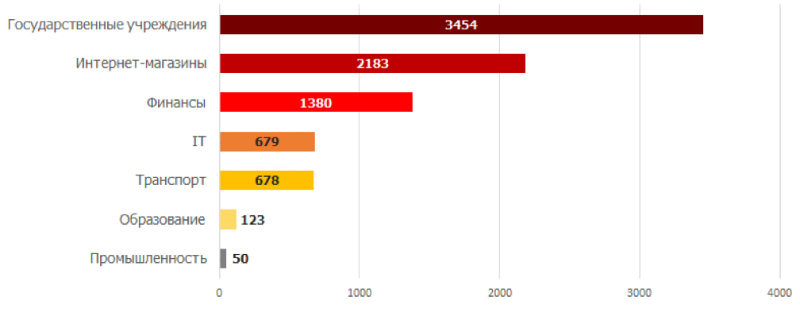
Average number of attacks per day per system
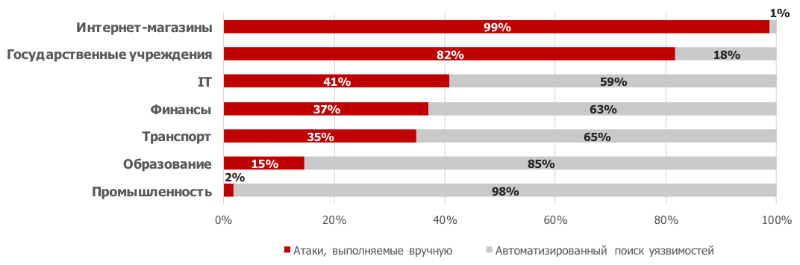
The ratio of automated scanning and manual attacks
Most of the attacks for all industries, except government agencies and online stores, are attacks carried out using specialized vulnerability scanner software. Automated scanning involves attempts to perform various types of attacks, for example, the introduction of SQL statements, Path Traversal, using ready-made software tools for instrumental analysis of security. Scanning results can be used by an attacker to exploit vulnerabilities and further develop the attack vector before gaining access to sensitive information, local network resources, critical systems or to launch attacks against users.
The figure below is an example of an automated scan detection using the sqlmap utility. PT AF has identified the objectionable content of the HTTP User-Agent header and a query containing the injection of SQL statements.
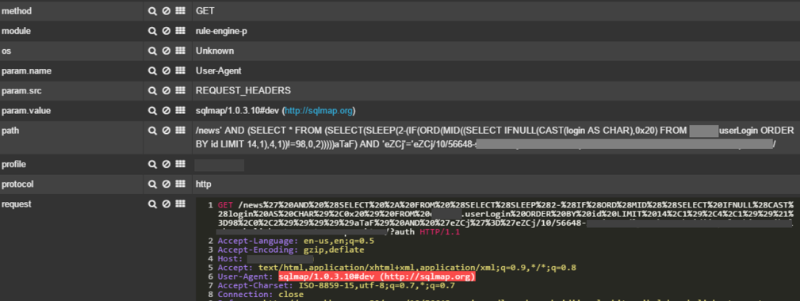
An example of an automated scan detection
The highest average number of attacks per day — approximately 3,500 attacks — was recorded during pilot projects in state institutions. An automated vulnerability scan accounts for only 18% of the total number of attacks. Online stores occupy the second line in this ranking: about 2,200 attacks were registered per day, while almost all of them were conducted without the use of automated scanning tools.
In the financial sphere, PT AF recorded about 1,400 attacks per day, among which automated vulnerability scan prevailed. Transport resources and IT companies account for an average of about 680 attacks per day, most of which also comprise an automated vulnerability scan.
The information-analytical center was excluded from the calculations of the average number of attacks per day for education, whose functions include processing the results of state examinations. The pilot project for this center took place in the summer, when school students passed the exam and GIA, and therefore there was an extremely large number of attacks on the web application - more than 20,000 attacks per day. At the same time, the most common were attacks using vulnerability scanning tools. Students with basic knowledge of information security and ways to circumvent security mechanisms could use open source software to scan the system. This explains the fact that most of the attacks of this type came from the United States: it is likely that public utilities or online services used proxy servers located in the United States. The purpose of attacks on the information and analytical center, most likely, was access to exam results and examination materials. Perhaps the students thought that in this way they could change their points for the exam. In addition, it can be assumed that the attackers were trying to find vulnerabilities, the exploitation of which would allow access to the database of examination materials for subsequent illegal distribution.
For industrial systems, PT AF recorded about 50 attacks a day, almost all were an automated vulnerability scan, and only 1% was conducted manually.
The following diagram for each industry presents the ratio of the types of attacks carried out by attackers, and the calculations that were made as part of automated scanning for vulnerabilities were excluded from the calculations, since they are not industry-specific.
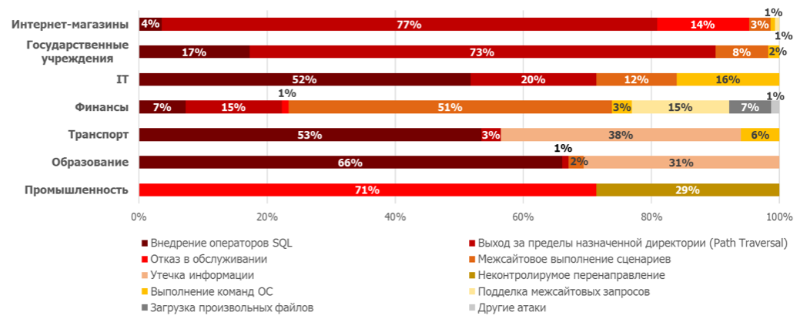
Manual attack type ratio
For government agencies, more than 70% were Path Traversal attacks, with which attackers tried to go beyond the current file system directory and gain access to the files on the server in order to steal sensitive information.
An example of detecting Path Traversal attacks is presented below. The attacker intended to go to the root directory of the server and get access to the file / etc / passwd, which contains a list of user accounts of the system.
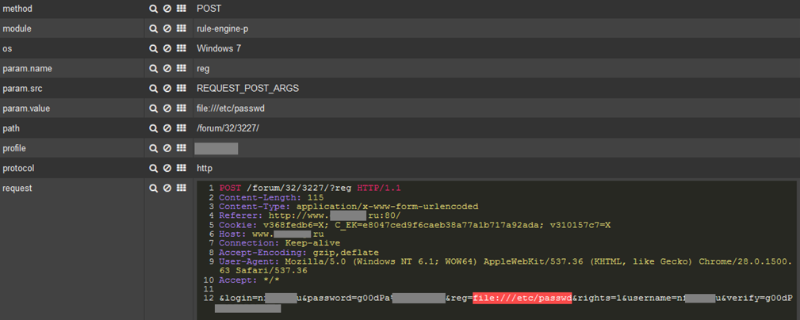
Path Traversal attack detection example
About 17% of attacks are attempts to embed SQL statements. A small part (about 8%) consists of “Cross-site scripting” attacks aimed at users of public services portals. The attackers tried to execute OS commands in 2% of cases.
Nearly three quarters of attacks on online stores amounted to Path Traversal attacks. Just like on the portals that provide public services, the attackers attempted to go beyond the current directory of the file system. A significant proportion (14%) is denial of service attacks. For an online store, the threat to the availability of a web application is critical. Attacks on users (“Cross-site scripting” and “Cross-site request forgery”) add up to 4%. In 4% of cases occur and the introduction of SQL statements.
In the financial sector, about 65% of the total accounted for the “Cross-site scripting” and “Cross-site request forging” attacks, aimed at system users. Such attacks are widespread in the financial industry and are particularly dangerous because they allow theft of cookie values and user credentials (using phishing), as well as performing actions on behalf of legitimate users.
The figure shows an example of identifying cross-site scripting attacks. The attacker tried to display Cookie values to check the web application’s vulnerability to this attack.
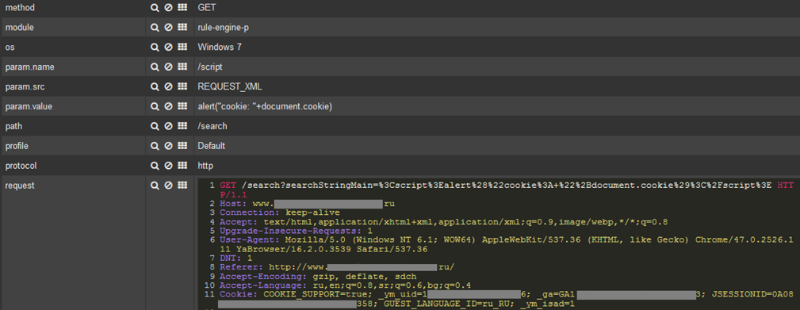
Cross-site scripting attack detection example
The attackers tried to gain access to sensitive information using the Path Traversal attack (15% of the total) and the introduction of SQL statements (7% of the total). The proportion of “Download arbitrary files” attacks was 7%. Such attacks are often used to gain access to the execution of OS commands, while direct execution of OS commands was registered in 3% of cases. In general, the nature and complexity of the attacks indicate a higher level of technical training of intruders compared to other considered industries.
In IT, more than half of the attacks detected are attempts to introduce SQL statements. There are also Path Traversal attacks (20% of the total). In addition, 16% are attempts to execute OS commands, and 12% of attacks against web applications of IT companies are aimed at system users.
For web applications of transport companies, the number of attacks “Introduction of SQL statements” exceeds 50%, about 38% is information leakage, and 6% is the execution of OS commands.
In the field of education, approximately 70% of manual attacks were “Implementing SQL statements”. This attack is often quite simple in execution, it can be used to gain access to personal user accounts or database contents. About 30% of the attacks are exploiting the Information Leakage Vulnerability, which could allow an attacker to obtain sensitive data or find out additional information about the system.
In the figure, you can see an example of detecting the introduction of SQL statements, the attacker entered his database query in the GET-parameter id to check whether the vulnerability could be exploited.

An example of an attack detection "The introduction of SQL statements"
Nearly two thirds of attacks against industrial applications accounted for denial of service (DDoS) attacks. The figure below shows an example of detecting three chains of attacks, including DDoS. The PT AF firewall builds such chains automatically, by identifying correlations between events that are separated in time, but are part of a single attack.
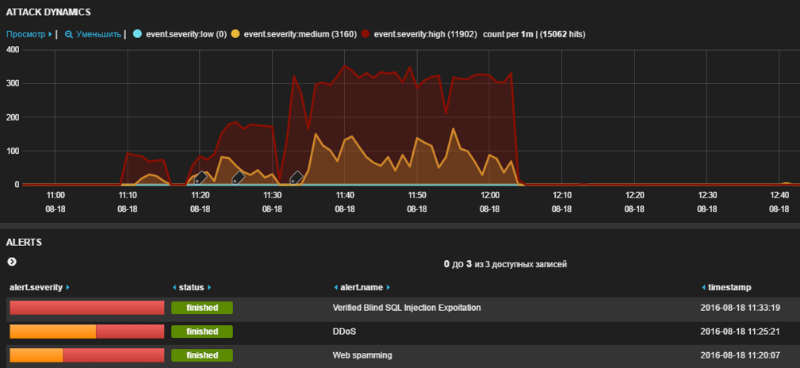
Example detection of related events, including DDoS
Sources of attacks
The analysis of the sources of attacks was carried out only in relation to the Russian systems that participated in the pilot projects. The largest number of recorded attacks emanate from the Russian-speaking countries, in the first positions are Russia and Ukraine. The percentage of attacks originating from the Netherlands and the United States is quite high, since in these countries there are a large number of providers providing proxy services.
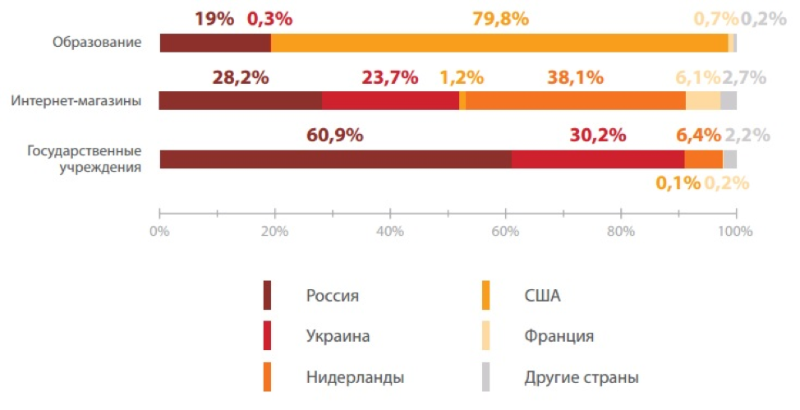
External sources of attacks by industry
Sources of external attacks on Russian organizations vary by industry. Most of the attacks on state institutions are carried out from Russian IP addresses, about a third are made from IP addresses belonging to Ukrainian providers, in 6% of cases the source is the Netherlands.
The source of attacks for online stores in approximately equal shares (about a quarter of the total) are Russia and Ukraine. More than a third of the attacks pass through the IP addresses of the Netherlands.
As was shown above, public services and utilities for scanning web applications for vulnerabilities are widely used for attacks on the sphere of education. To conceal the actual IP address of the source of the attack, such software mainly uses servers located in the United States. The fifth part of the attacks comes from Russian IP-addresses.
It is interesting to note that the source of more than a third of the attacks on the web applications of universities are internal intruders (on average for the education sector, this figure is 8%). These are probably students who have access to wireless networks of an educational institution, as well as access to a local network in classrooms.
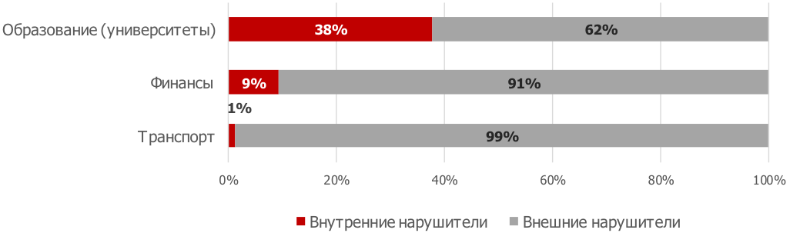
The ratio of external and internal violators
In the financial sphere, about 10% of attacks emanate from internal violators. It also does not exclude the option that in some cases an intruder may be a system administrator conducting testing of defense mechanisms.
Conclusion
Based on the results of the PT AF pilot projects, it can be concluded that the majority of attacks made by hackers are quite simple both in execution and in detection by WAF-type defenses.
At the same time, in the second half of 2016, there was a significant increase in the number of attacks on web resources, primarily from the IP addresses of Ukraine and Turkey. Taking into account the reports of the Federal Security Service on planned cyber attacks, Russian companies, in particular, financial organizations, are advised to take appropriate measures in advance to protect critical components and make sure that the protective equipment is effective.
Despite the large number of simple attacks, it should also be borne in mind that the level of technical training of modern attackers allows you to implement attacks of a high level of complexity that require a series of actions that occur at different times and at first glance are not interrelated. To identify the chains of such attacks, including the detection of long-term targeted attacks and during the investigation of incidents, it is necessary to use the tools of correlation analysis.
The full version of the study is available here .
Authors : Ekaterina Kilyusheva, Evgeny Gnedin
PS On Thursday, April 27 at 2:00 pm , Positive Technologies' senior expert Vsevolod Petrov will hold a free webinar, during which he will talk about why hackers manage to launch successful attacks on web applications, and how this can be prevented.
In addition, the discussion will focus on the technological capabilities of the PT Application Firewall application-level firewall, which help it to strengthen traditional perimeter protection and ensure security on all fronts.
Participation in the webinar is free, you can register at www.ptsecurity.com/ru-ru/research/webinar/226999/
Source: https://habr.com/ru/post/327344/
All Articles