How to choose an information security service provider
What is important when choosing a provider to neutralize DDoS attacks and network perimeter protection?
"The width of the channel to the server" - you say. Well, add: "Protection against different attack vectors." Maybe your list still has an active vulnerability scanner. What's so complicated?
')
It seems to many that the DDoS-mitigation solution is just a “fast and large-scale ban of bad IP”, which is not far from the truth, but still not completely true. Given that over the past year alone, the number of DDoS attacks increased one and a half times and was published by the media because of the devastating effect, not only clean and highly professional companies in the field of information security want to take advantage of the news wave.
In order not to guess, but to know for sure what basic parameters to pay attention to when choosing such an important thing as protecting the network infrastructure from denial of service attacks, we in Qrator, together with Wallarm and the NGENIX CDN provider, prepared a special page where The most important criteria that need to be addressed at the moment of choosing a specific solution, service, service, product are collected - it does not matter.
In our experience, the key thing is guarantees for the essence of what you are buying, because the complex services that your business depends on (no customer will enter the store with the door closed) are accompanied by large and detailed contracts for their provision.
It is important that you are going to choose and acquire something that will always protect your infrastructure from attacks, each of which risks putting the network business on the verge of existence. After all, the page on which the user can not get, ceases to exist for him at the moment.
The second problem, not considered by some in principle - and largely due to the absence or concealment of information, is that there are not so many DDoS-mitigation providers in the world: all companies can be listed on the fingers of two hands and each of them has been on the market for a long time. And a completely standard situation is the resale of services of a large company under its own patterns. This means that you buy a service, responsibility for the proper level of provision which will not be borne, absolutely, no one.
In the world of physical constants, there are well-known “standards” that set standards for weights and measures. In the world of electronic services, "standards" are most often the services of the largest companies, the leaders of their own markets. Having prepared their proposals, we have compiled a more or less universal list of requirements for expensive and complex services and products, the list of which without a doubt includes such a thing as neutralizing a wide variety of DDoS attacks.
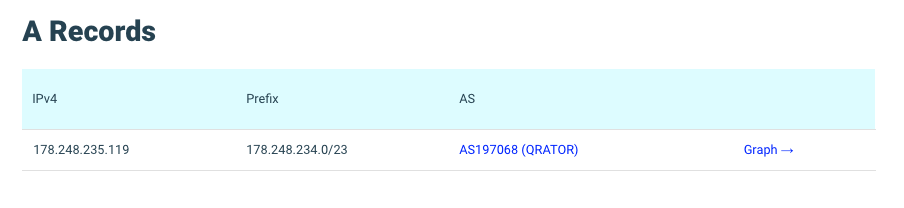
As a rule, if you are in the subject line, then the easiest way to check whose service you are actually buying is to look at the DNS A-records . This can be done using the free "Radar" . But since in business we are talking about the costs of purchasing or creating services, we need an exhaustive list of requirements that is understandable not only to network administrators.
The developed criteria are divided into two large groups: technical and business. Put aside the last and talk about what technical requirements must meet the decision in question.
- The presence of more than one point of presence in each of the key regions, with a connection to providers of communication not lower than Regional Tier 1 (exclusion of single points of failure due to the presence of a geodistributed network);
- Infrastructure created on the basis of hierarchically unrelated networks of Internet providers (which is especially important for small countries with a small number of key providers);
- More than one service provider per network prefix (which excludes the possibility of inheriting problems from the provider);
- The presence of the DNS protocol security (after the fall of Dyn, there is not even an argument here);
- Protection of all protocols used by the target application (and not just HTTP / HTTPS);
- Constant automatic filtering of traffic (minute and even second delays in putting the solution into work and neutralizing the attack is bad);
- Filtering throughout the ISO OSI network model, up to L7. The latter is especially important as attacks on the application layer are becoming more common. The compatibility of the solution with any products and services used before is also important here, which reduces implementation costs;
- Full filtering of encrypted traffic without disclosure of keys;
- False positive no more than 5% under attack;
- No UX changes (reverse Turing test) - guarantee that the user is not annoyed;
- The possibility of external protection testing by independent experts;
A separate, twelfth point is the presence of WAF in the list of services provided - and this item requires special attention, since the Web Application Firewall is a necessary and indispensable condition for any serious infrastructure protection system and neutralizing attacks. There are three separate technical requirements for WAF:
- The presence of an active and passive search for vulnerabilities, such a scanner will help you find out about the possible gaps of the network perimeter before the attacker does;
- The ability to apply virtual patches that do not need to comment: a bunch of vulnerabilities in systems of very different degrees of prevalence (Magento, Wordpress, and so on) are not closed by the developer for six months. Virtual patches allow you to effectively deal with this problem, while maintaining the full functionality of the application;
- Protection against brute force of various categories of passwords, from administrator to client, in different parts of the application.
We hope that this page will help you to better understand and carefully select the person to whom you entrust the information security of your own business. We will also be glad to hear your suggestions and comments to the criteria.
Source: https://habr.com/ru/post/327326/
All Articles