How to properly configure a firewall or Check Point Security Best Practices
I am sure that most system administrators or network engineers had a question: " Did I set up the firewall correctly and what else can I do to better protect? ". Naturally, in this matter it is worth relying on various guides (PCI DSS, ISO, NIST, etc.) and common sense. Help from more experienced colleagues is also welcome.
As part of this article, we will try to describe the main recommendations or best practices for setting up firewalls. This is a kind of “check-list”, following which you can significantly improve the quality of network protection. The manual was compiled specifically for Check Point hardware, but it can also be used as a basis for self-auditing a network built on other vendors' equipment (Cisco, Fortinet, Palo Alto, etc.). If you are interested in it, then welcome under the cat ...
Compliance Blade
')
Generally speaking, in the case of Check Point, the audit of the “correctness” of the settings can be performed automatically. This is done using the Compliance Software Blade, which is activated on the management server:
This blade performs the following functions:
- Software Blade Monitoring 24/7
- Permanent monitoring of the management system, software blades and security gateways is optimally tuned.
- Shows incorrect configuration settings and security vulnerabilities.
- Provides recommendations to improve security.
- Real Time Notifications
- Shows how a configuration change will affect security.
- Notifies about changes to policies that adversely affect security.
- Teaches users what the effects of the desired changes will be.
- Ready reports
- Translates thousands of regulatory requirements into practical recommendations.
- Continuous assessment of compliance with regulatory requirements (PCI DSS, ISO, NIST, DSD, and so on).
Evaluation settings:
Regulatory compliance assessment:
Performance evaluation of individual gateways and blades:
The Compliance Blade comes free with a 1-year subscription when you purchase a management server (be it a physical appliance Smart-1 or a virtual machine). This time is quite enough for the integrated configuration of protection with the subsequent evaluation of configurations. Thus, in the first year you get a free audit of network security (Check Point settings).
If you have never activated this blade, it is quite easy to do in the properties of the management server (Management Server), as was shown in the picture above. After that, install policies and wait a while (depending on the size of the network and the number of gateways). The result of the evaluation of configurations can be found on the corresponding Compliance tab in the SmartDashboard console:
It is worth noting that the continued use of the Compliance Blade requires the extension of the corresponding subscription, the price of which does not always correspond to the budget of small and medium-sized companies.
What to do after the end of the subscription?
Especially for such cases, we have created this manual, which will allow you to manually check the “adequacy” and security of the current settings in accordance with the recommendations of Check Point. At the same time, we will not consider the standards of various regulators (PCI DSS, ISO, etc.), but only touch upon the best practices (Best Practices) for configuring network protection tools.
Firewall Best Practices
1. There is a Management rule (the name may differ):

This rule is used for access from the management server (Management Server) and the administrator’s computer to the Security Gateway. The rest of the access should be denied.
2. Present the rule of Stealth (the name may differ):

This rule is used to block any attempt to access the gateway itself, which makes it “invisible” and eliminates the possibility of unauthorized access. Make sure that this rule is located lower than Management.
3. There is a rule of Clean up rule (the name may differ):

By default, Check Point blocks all connections that are not explicitly allowed. This rule is used exclusively for logging all packets that would be blocked without it. The rule should be the latest in the list.
4. There is a Do Not Log rule (the name may differ) for which logging is disabled:
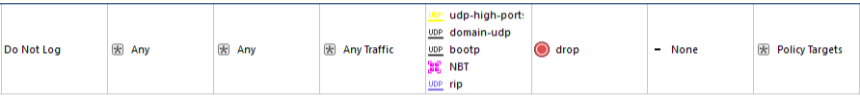
This rule is used to filter “spurious” broadcast traffic. Such traffic includes: udp-high-ports (UDP ports> 1024-65535), domain-udp, bootp, NBT (NetBios), rip (the list may differ, depending on your network). Logging is disabled intentionally in order not to overload the firewall logs with useless information. The rule should be as high as possible in the list (preferably first).
5. In the access lists in the source column there is no Any value, i.e. any traffic. Always specify a specific source in the rules, be it a network or a host. With the exception of Stealth, Clean up rule, Do Not Log.
6. There are no rules allowing all traffic (any any accept).
7. Incoming Internet traffic is prohibited for the segments of Accounting (Finance) and Human Resources (HR).
8. Prohibited FTP traffic from the Internet to the DMZ.
9. There are no unused rules. In the SmartDashboard console, you can view the hit count for each access list:
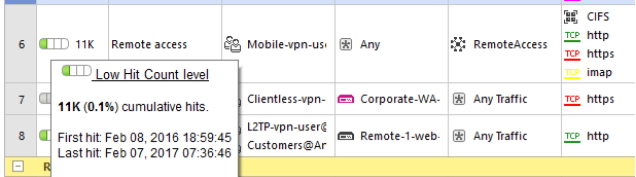
If the counter shows a zero value or the last match (Last hit) was more than 6 months ago, it is recommended to delete this rule in order not to overload the general list.
10. For all the rules in the Track field the option Log is set. In addition to the rules Do Not Log. So you can log all important events excluding broadcast traffic.
11. For all the rules indicated “adequate” name and there is a comment explaining the purpose of this rule.
12. Logging is enabled on all gateways.
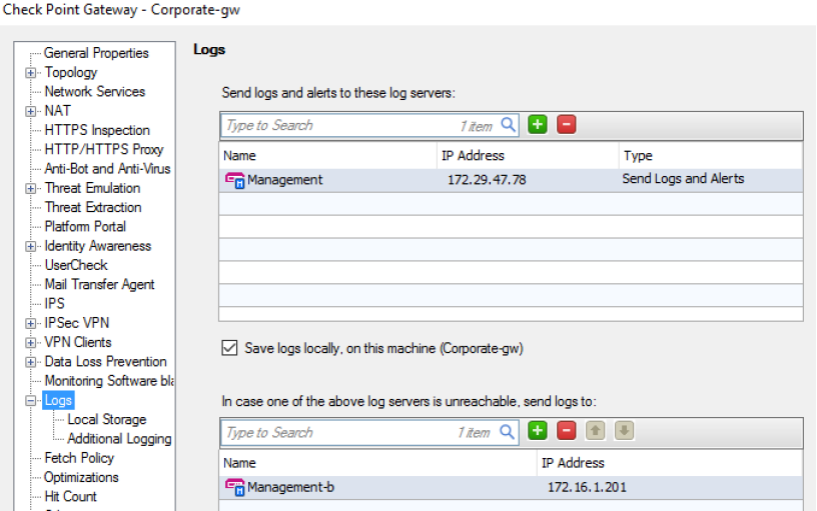
The management server (Management Server) or another third-party solution can act as a Log-server (it is possible to use SIEM or Log Management systems).
13. A backup Log Server is configured on all gateways. This will save important messages in case of failure of the main Log server.
14. On all gateways, the local log storage function is also enabled. This will allow to save information about events in case of unavailability of the Log server.
15. All gateways are configured to create a new Log file when a certain size of the old one is reached.
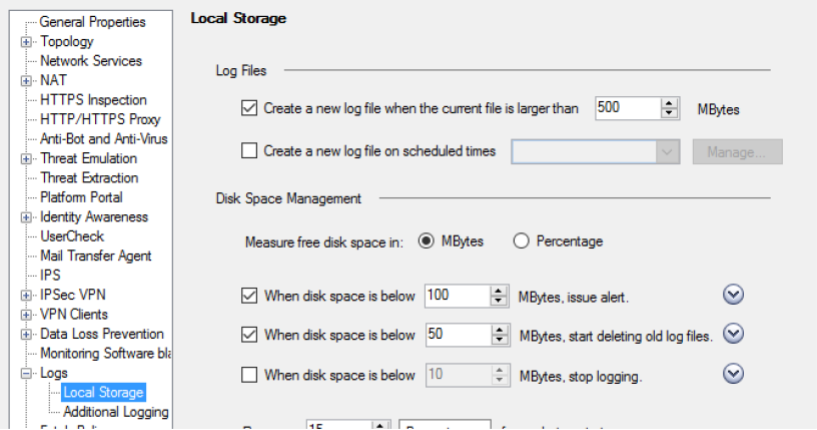
This will significantly speed up the processing of logs (display, search). You can go back to older logs by switching the Log file.
16. On all gateways, notifications are set to indicate a terminating disk space. The trigger level is selected depending on the total volume of the hard disk. Typically, the threshold is set in the region of 50-100 MB.
17. All gateways are configured to delete old Log files when disk space ends. The trigger level is selected depending on the total volume of the hard disk. Typically, the threshold is set in the region of 50 MB.
18. All gateways have scripts configured that are executed before deleting the old Log files.
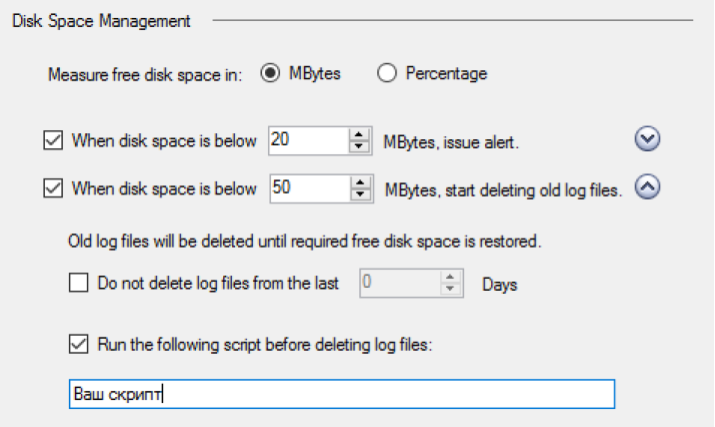
Using this function, you can make sure that log backups have been created.
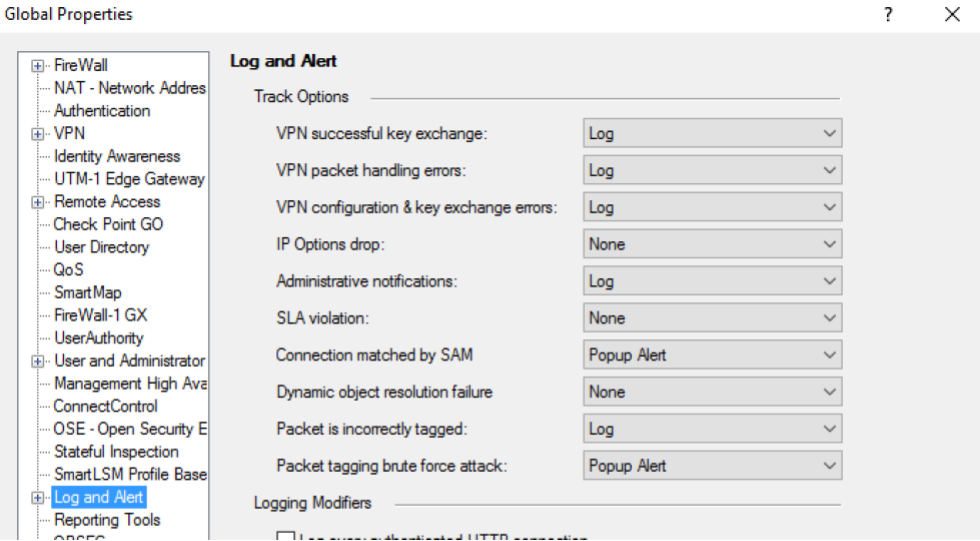
19. Global settings enable logging for “VPN packet handling errors”, “VPN successful key exchange”, “VPN configuration & key exchange errors”, “Administrative notifications”, “Packet is incorrectly tagged” and “Packet tagging brute force attack” :
20. On all gateways, Anti-Spoofing is enabled in prevent mode (for all interfaces):

21. In global properties (global properties), check the default time interval values for stateful inspection:
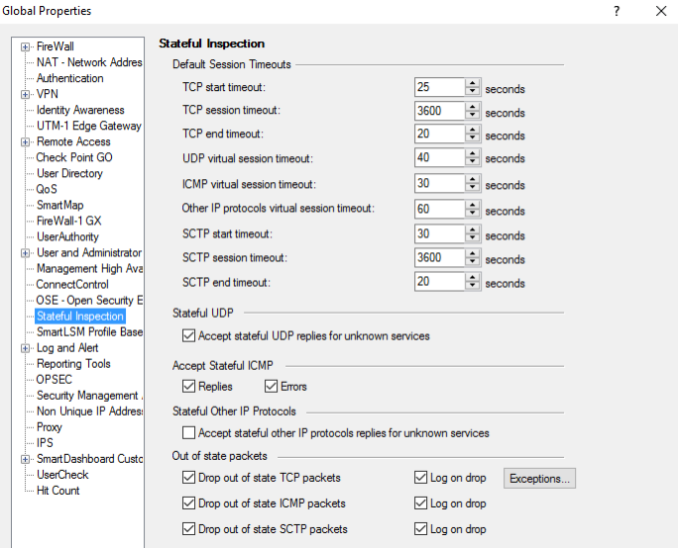
If necessary, change to meet your network requirements.
22. For the “Drop out of state TCP packets”, “Drop out of state ICMP packets” and “Drop out of state SCTP packets” fields, Log on drop is enabled (see picture above).
23. In the properties of each gateway, the Hit Count is enabled:

This will allow you to see the number of matches for each rule (access list) and remove unused ones.
24. In the gateway optimization settings, specify the maximum number of competitive sessions.

This parameter depends on the gateway model and helps prevent overloading.
25. In global settings (global properties), user account (User Accounts) and Administart (Accounts) account passwords expire no later than 180 days.

The expiring password notification should also be configured.
26. When integrating with Active Directory, a password change is configured:

27. In the global settings (global properties) the blocking of Administrators is activated. The account is blocked for 30 minutes in case of 3 unsuccessful login attempts.

Also, a notification about blocking and resetting the control session, inactive for 15 minutes, is configured.
28. In the properties of gateways the option “Rematch connections” is set.

This will allow you to block forbidden connections immediately after installing a new policy and not to wait for the session to end.
29. Configured time synchronization (NTP)
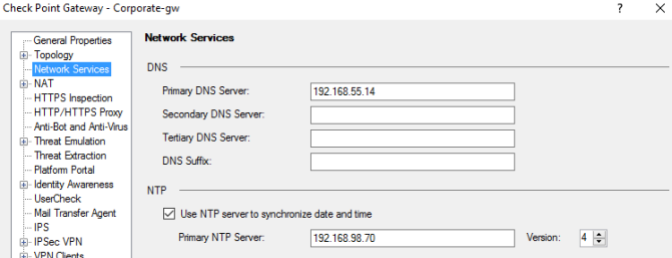
This will allow you to see the current date and time for all events (logs).
These are the Check Point recommendations for configuring the Firewall blade. But I think many have noticed that most of the tips are applicable to other vendors. There are similar recommendations for all blades (IPS, DLP, Application Control, URL Filtering, etc.), which we may consider in the following articles.
More information on Check Point can be found in our corporate blog .
Source: https://habr.com/ru/post/327316/
All Articles