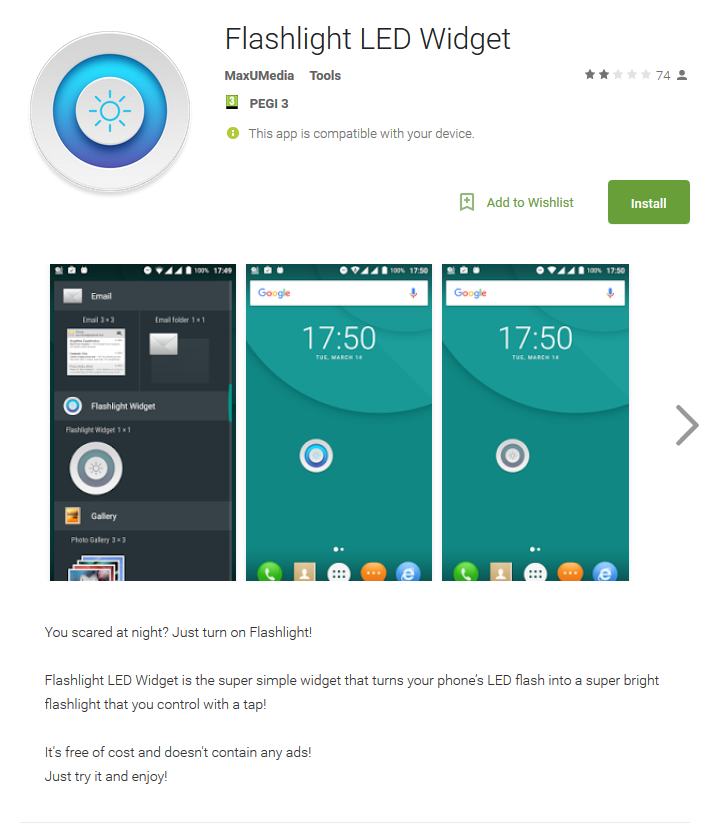
New mobile banking on Google Play - now disguised as a flashlight application
Never was and here again. On Google Play, we found an application with “undocumented features” - Flashlight LED Widget, hiding the functions of a mobile banking. The application appeared on March 30 and until the removal on April 10 it was downloaded up to five thousand times.
Unlike other malicious programs with a constant set of target applications, this Trojan changes its targets dynamically, depending on the software installed on the infected device.
')
After installation and launch, the application requests the device administrator rights and permission to display the screen on top of other applications (relevant for Android 6.0 and higher).
The Trojan then accesses the remote C & C server and sends information about the device and the list of installed applications, as well as the owner's photo taken by the front camera.
If the infected device is in Russia, Ukraine or Belarus, the managing server deactivates the Trojan - it seems that the attackers are thus trying to avoid criminal prosecution in their own country.
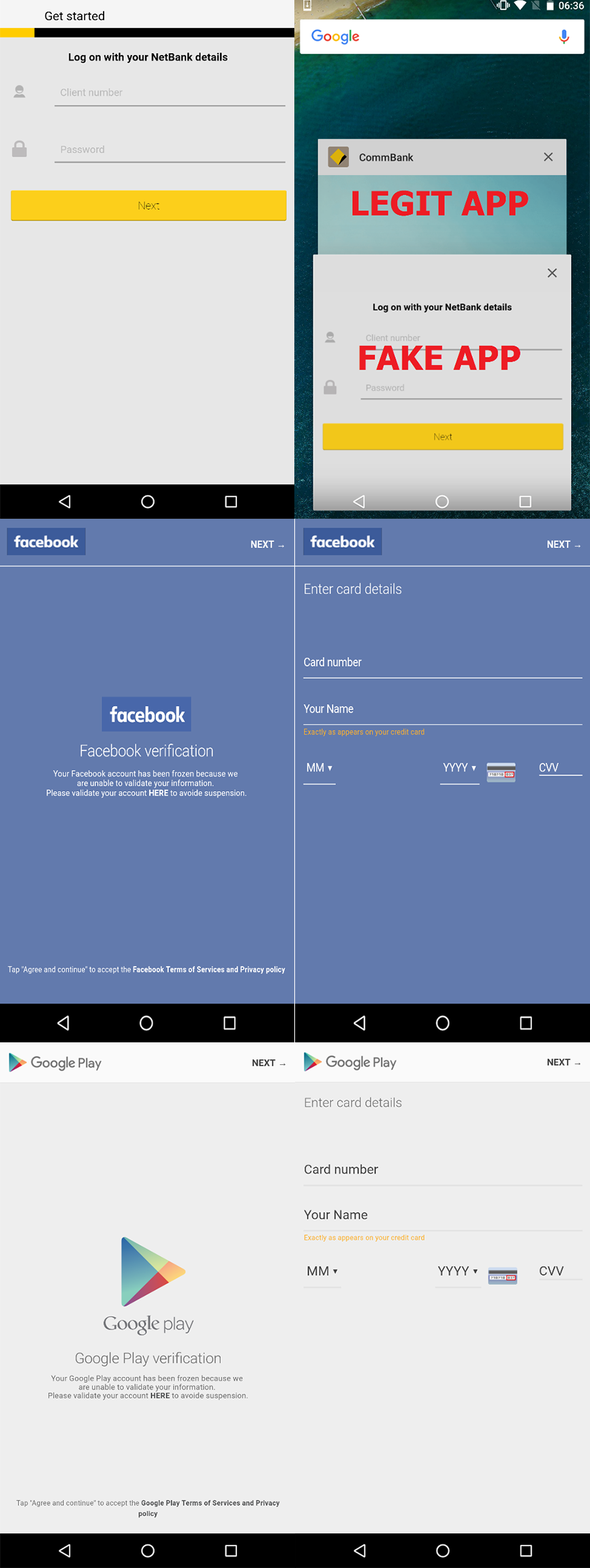
After receiving a list of installed applications, the C & C server simulates the corresponding activity and sends malicious HTML code to the device. This code is executed by WebView when the victim launches the target application. The fake screen hides legitimate activity and requests bank card details or usernames / passwords. The credentials entered in the fake form are sent unencrypted to the C & C server.
It is difficult to list target applications - the HTML code received from a remote server depends on which applications are installed on the device. During the study, we observed the interception of passwords Commbank, NAB and Westpac Mobile Banking, as well as Facebook, Instagram and Google Play.
The device blocking function is most likely used during the withdrawal of funds from compromised accounts. Attackers can remotely block a device using a fake update screen — it will hide malicious activity and prevent the victim from interfering with the process.

The Trojan uses Firebase Cloud Messages (FCM) to communicate with the managing server. This is the first Android malware studied by us that uses this communication channel.
We found out that this trojan is a modified version of Android / Charger, first discovered by Check Point in January 2017 . But unlike the first version, which was used primarily as an extortionist (device locking is a ransom demand), in our case the attackers switched to banking data theft - a relatively rare evolution for Android.
Due to the use of phishing windows and the blocking function, Android / Charger.B resembles a mobile banker, which we analyzed in February . However, the new find is more dangerous - there is no hard-coded list of targets in this Trojan, you can attack almost any application. This opens up almost unlimited possibilities for the future use of Malvari.
Search for malicious applications: Settings - Application Manager / Applications - Flashlight Widget.

Detect the application is easy, remove - more difficult. The trojan does not allow the victim to disable administrator privileges by closing the screen with a pop-up window. In this case, the device must be restarted in safe mode, you can act in accordance with our video instructions .
ESET NOD32 anti-virus products detect malware as Trojan.Android/Charger.B.
Android / Charger.B
com.flashscary.widget
CA04233F2D896A59B718E19B13E3510017420A6D
For a new report, thanks to virus expert Lukasz Stefanko .
Unlike other malicious programs with a constant set of target applications, this Trojan changes its targets dynamically, depending on the software installed on the infected device.

')
How it works?
After installation and launch, the application requests the device administrator rights and permission to display the screen on top of other applications (relevant for Android 6.0 and higher).
The Trojan then accesses the remote C & C server and sends information about the device and the list of installed applications, as well as the owner's photo taken by the front camera.
If the infected device is in Russia, Ukraine or Belarus, the managing server deactivates the Trojan - it seems that the attackers are thus trying to avoid criminal prosecution in their own country.
After receiving a list of installed applications, the C & C server simulates the corresponding activity and sends malicious HTML code to the device. This code is executed by WebView when the victim launches the target application. The fake screen hides legitimate activity and requests bank card details or usernames / passwords. The credentials entered in the fake form are sent unencrypted to the C & C server.
It is difficult to list target applications - the HTML code received from a remote server depends on which applications are installed on the device. During the study, we observed the interception of passwords Commbank, NAB and Westpac Mobile Banking, as well as Facebook, Instagram and Google Play.
The device blocking function is most likely used during the withdrawal of funds from compromised accounts. Attackers can remotely block a device using a fake update screen — it will hide malicious activity and prevent the victim from interfering with the process.


The Trojan uses Firebase Cloud Messages (FCM) to communicate with the managing server. This is the first Android malware studied by us that uses this communication channel.
We found out that this trojan is a modified version of Android / Charger, first discovered by Check Point in January 2017 . But unlike the first version, which was used primarily as an extortionist (device locking is a ransom demand), in our case the attackers switched to banking data theft - a relatively rare evolution for Android.
Due to the use of phishing windows and the blocking function, Android / Charger.B resembles a mobile banker, which we analyzed in February . However, the new find is more dangerous - there is no hard-coded list of targets in this Trojan, you can attack almost any application. This opens up almost unlimited possibilities for the future use of Malvari.
How to delete?
Search for malicious applications: Settings - Application Manager / Applications - Flashlight Widget.

Detect the application is easy, remove - more difficult. The trojan does not allow the victim to disable administrator privileges by closing the screen with a pop-up window. In this case, the device must be restarted in safe mode, you can act in accordance with our video instructions .
ESET NOD32 anti-virus products detect malware as Trojan.Android/Charger.B.
Sample:
Android / Charger.B
com.flashscary.widget
CA04233F2D896A59B718E19B13E3510017420A6D
For a new report, thanks to virus expert Lukasz Stefanko .
Source: https://habr.com/ru/post/327284/
All Articles