Hacksplaining - an online course on web vulnerabilities

Hacksplaining is a cataloged and visual online tutorial on major web vulnerabilities. For each vulnerability, a detailed description is presented of how often it is encountered, how difficult it is to exploit, and the level of its criticality. Each vulnerability has a detailed description, a vector of exploitation, a vulnerable code, and recommendations on how to fix and protect it. As an example, the article provides an analysis of one of the tasks for hacking virtual online banking using the sql injection.
Considered vulnerabilities:

SQL Injection
The introduction of SQL-code - one of the most common ways of hacking sites and programs working with databases, based on the introduction of a query in an arbitrary SQL-code.')
Cross-site Scripting (XSS)
XSS is a “cross-site scripting” type of attack on web systems, which consists in introducing a malicious code into a page issued by a web system (which will be executed on the user's computer when it opens this page) and the interaction of this code with the attacker's web server. In the context of the site, three types of such attacks are considered: stored, reflected and DOM-based.Command execution
An attack in which the goal is to execute arbitrary commands in the host operating system through a vulnerable web application.Clickjacking
Client-side attack vector: the user, making a click on a specially crafted page of the attacker, actually clicks the link on a completely different site.Cross-site Request Forgery
“Cross-site request forgery”, a type of attack against website visitors that uses the disadvantages of the HTTP protocol. If the victim enters the site created by the attacker, a request is secretly sent to another server (for example, to the server of the payment system), performing some kind of malicious operation (for example, transferring money to the attacker's account).Directory traversal
Directory traversal (or path traversal) is the use of insufficient security checking of user-supplied file names, so that characters representing the transition to the parent directory are passed through the API.File Upload Vulnerabilities
File downloads should be treated with caution - they are an easy way for an attacker to inject malicious code into your application.Broken access control
All resources on your site should have implemented access control, even if they are not intended for regular users. Relying on "security through obscurity" is impossible.Open redirects
Most web applications use redirection functionality. If your website redirects all the URLs specified in the query string, it can help an attacker to generate phishing attack vectors.Unencrypted Communication
Inadequate encryption can make you vulnerable to Man-in-the-Middle attacks. Be sure to use HTTPS when transmitting any type of sensitive information.User Enumeration
If an attacker can abuse the authentication feature to check if the username exists on your site, it will greatly simplify the exploitation of other vulnerabilities.Information leafage
Identification of proprietary information helps an attacker to learn about the technologies of your site, ways, etc. and may allow an attackerPassword mismanagement
Secure password handling is essential to a secure authentication system.Privilege Escalation
Privilege escalation — an attacker exploits a vulnerability to represent another user (usually with higher rights) or to obtain additional permissions.Session fixation
Insecure handling of session identifiers can lead to the seizure of a user session.Weak Session IDs
Estimated session IDs make your site vulnerable to session capture.Xml bombs
XML documents may include embedded macros. Insecure processing of these macros can make your server vulnerable to attacks from specially crafted XML files.XML External Entities
XML files may include embedded links to other documents. Insecure handling of external links allows an attacker to gain access to the file system.Case Analysis SQL Injection Vulnerability
In the first step, we see an authorization form for online banking and a notification of the presence of a possible vulnerability:

For convenience, the request log is located at the bottom of the page:
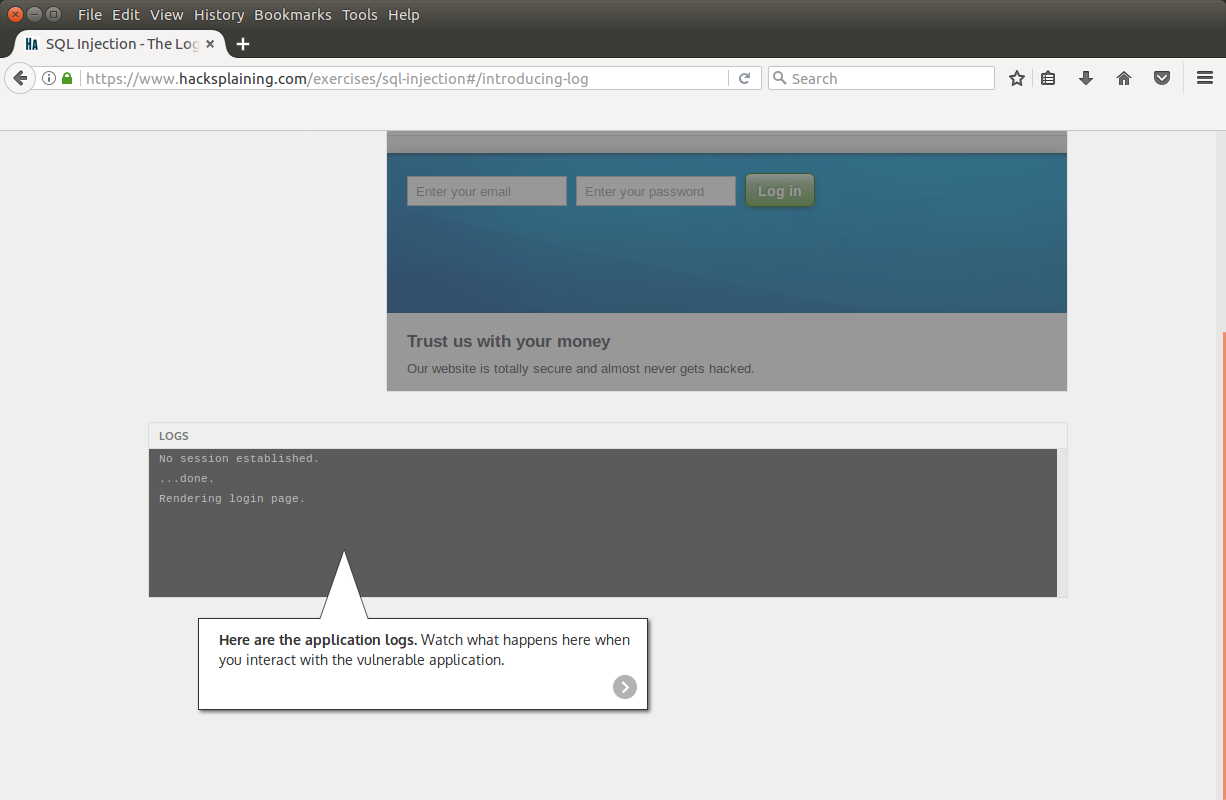
Next, we are asked to enter an arbitrary legitimate login and password:

The data is incorrect, let's try to bypass the authorization system:
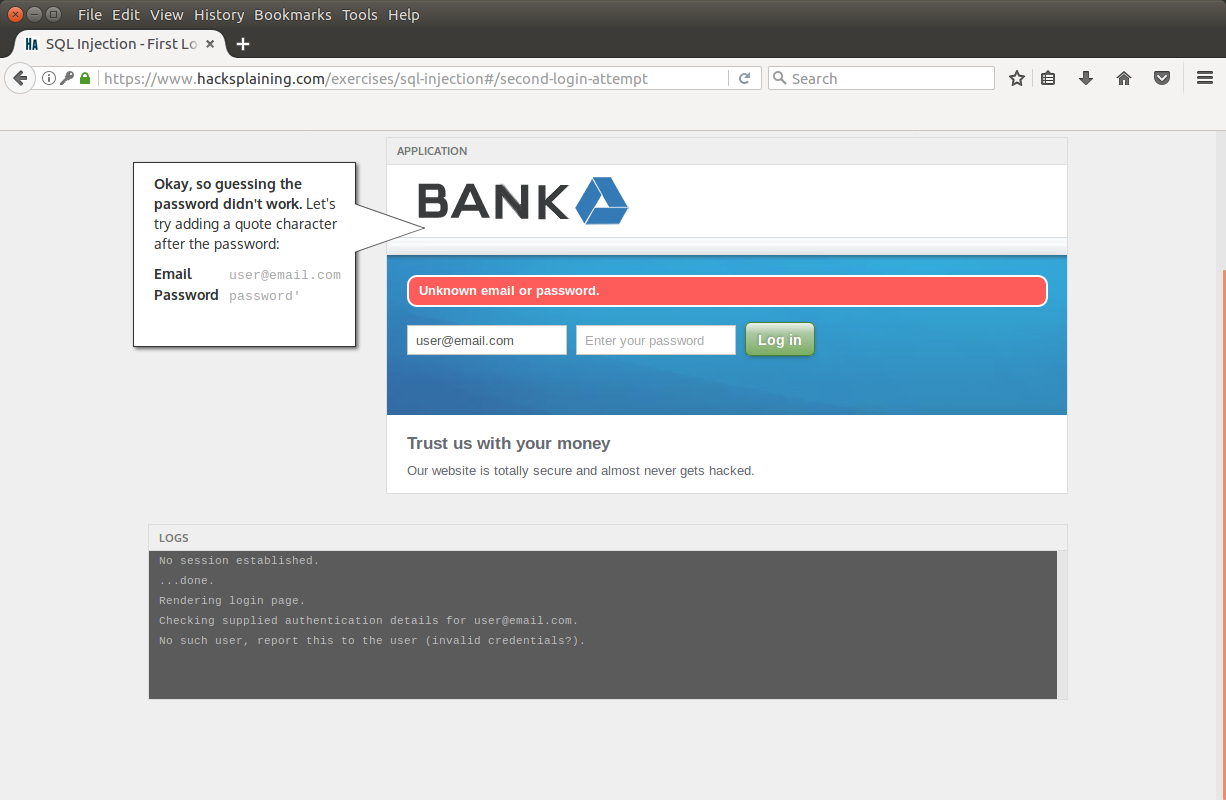
We get an error message (and more detailed information in the log):

On the CODE tab that appears, we reveal the nature of the error:
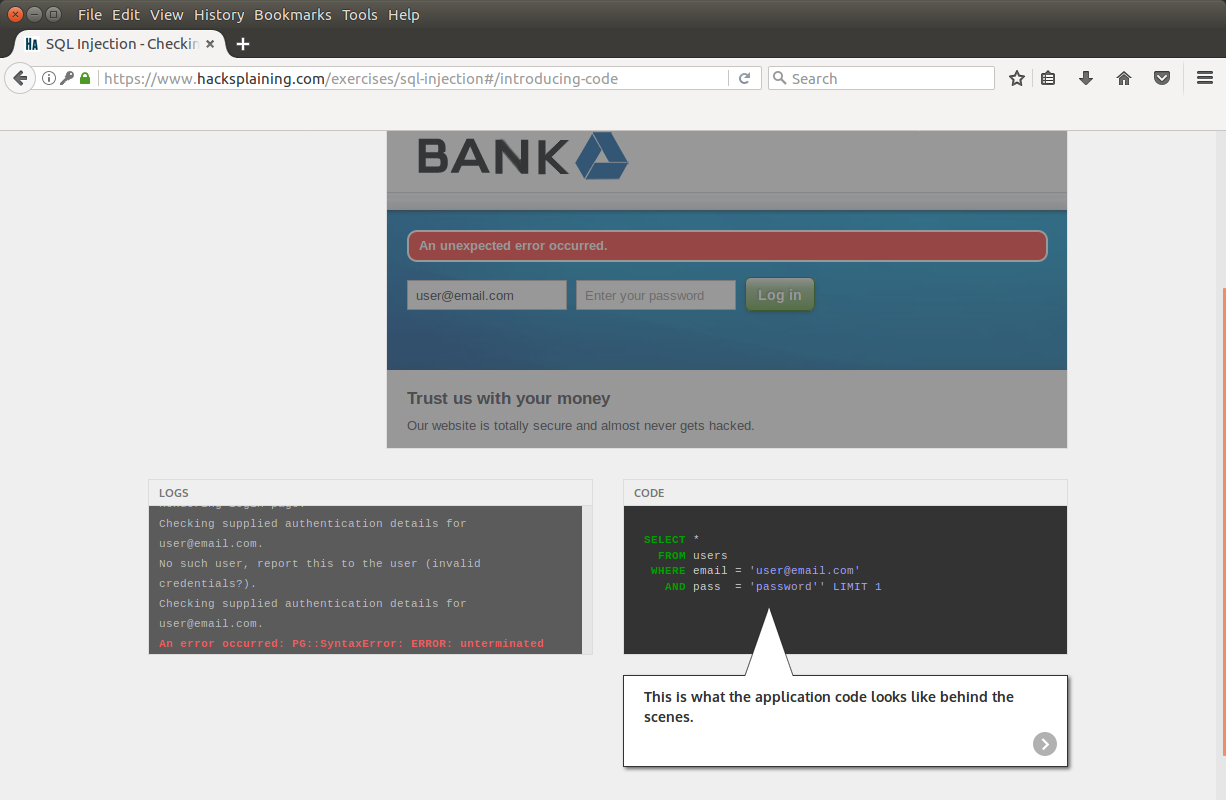
We see the completion of the request, now we will try to use this vulnerability to bypass online banking authorization:
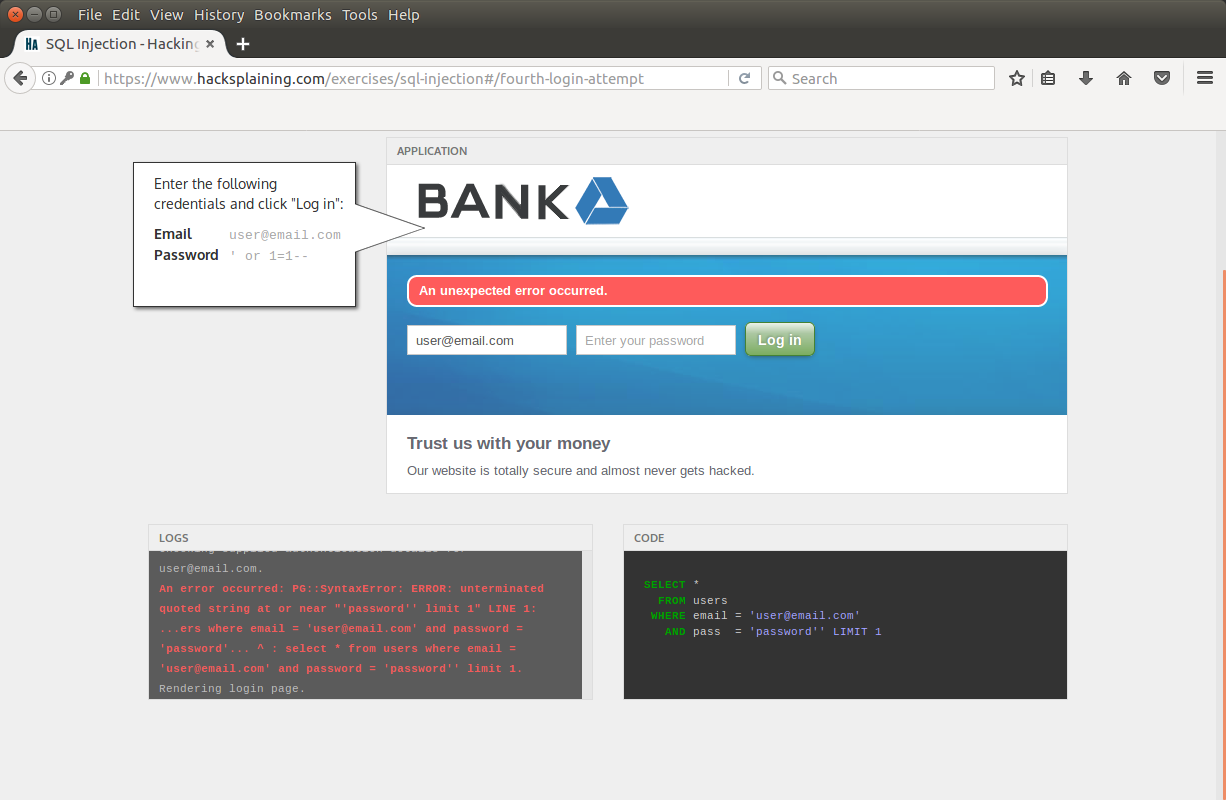
As you see, we added the condition “1 = 1”, which means the test criterion is “if login is 'user' or 1 = 1”, but 1 is always equal to 1. If we describe it in a simpler language, we try to log in with user user, with a password equal to the condition 1 = 1.

The condition is met - 1 = 1, and the password field is discarded!
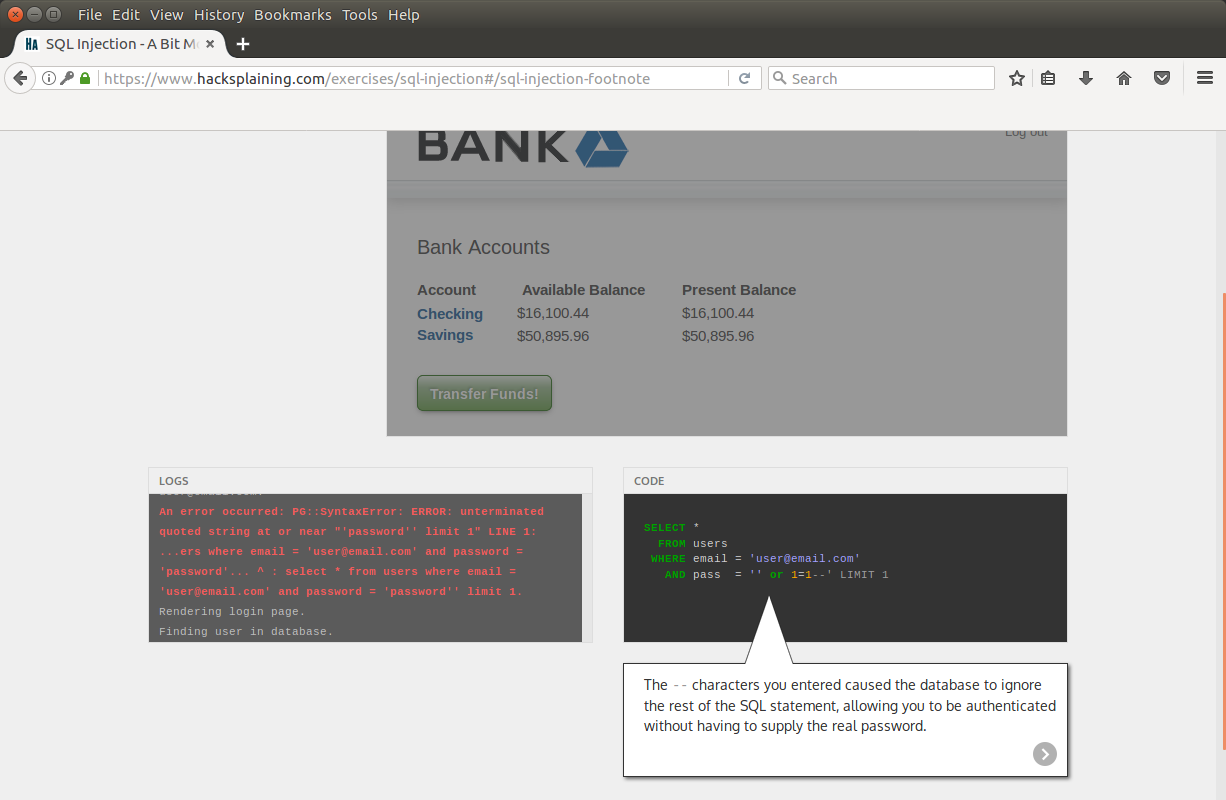
In this way we got inside the online banking. Next, we are provided with a description of protection methods against injections: code examples, description of risks, etc.
Additionally
As a supplement to the operation of the vector SQL injection, I recommend to familiarize yourself with: the following material:
- Methods for circumventing web application security tools when using SQL injection
- Cheat sheet for sql-injections
Conclusion
The online tutorial is quite detailed and well-made and recommended to developers first of all as a visual aid for “how not to write code.” For information security specialists, this is a good cheat sheet and web visualization tool with good description and step-by-step demonstration of the attack vector.
www.hacksplaining.com
Source: https://habr.com/ru/post/327270/
All Articles