How DDos-attacks are “ordered”: life story
Below is the story of how they ordered a DDos-attack on the e-commerce platform, the performers decided to “earn more” - they notified the victim and asked for more money. After they did not agree - the attack began, and then “accidentally” another letter came with a proposal to “protect” against DDos attacks, a more detailed note about how sites are “ordered” from us.
* For privacy reasons, all personal data is hidden.
This epic story began with a letter in which the site administration was informed that competitors had ordered a DDos attack on them.
')
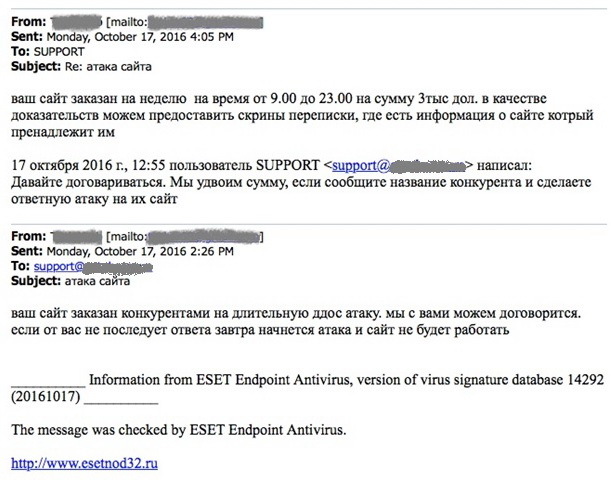
The administration, of course, tried to negotiate with the hackers to find out - who “ordered” the attack? There was no response to the letter, i.e. agree with the hackers failed. This correspondence took place on October 17, 2016 at the end of the working day - the first letter about the attack came at about 16:00.
The next day, the attacks began, at the beginning it was a UDP flood attack, to warm up, so to speak. After this attack was repulsed, a second wave of HTTP flood attacks followed. But all attacks were repulsed by the provider.
But here's another interesting thing: on October 17, the day before the attack, an hour after the first letter about the impending attack (at 17:08), a letter “by chance” received a proposal to protect against DDoS :)
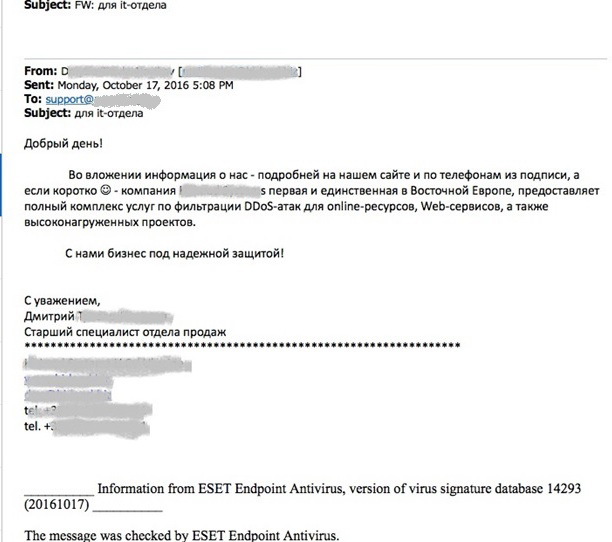
And what slogan, forgot to add a smiley!
As the saying goes "Coincidence? - I do not think! It is unlikely that hackers and “security specialists” are one and the same company, since it is not easy to combine 2 roles at once - and a “hacker” and a “security specialist” selling a solution from DDos attacks. But the one who sent the letter most likely knew about the impending attack from the hackers themselves and decided to also earn on the vulnerable position of the victim of a future attack (it is not known for sure, therefore all the contacts of the “security specialist” are hidden). On the other hand, it may well be that the “hackers” decided to make money without practicing the ordered attack.
In the case of the site of this client, the purpose of the attack was a week (!) Interruption in access to the site - in order to knock the site out of the search index. It would take up to 1 month or more to restore the previous, before the attack, positions of the site in search engines, which for the client is equivalent to a catastrophe.
The moral of this story is that it is better not to spend money and time to attack competitors, and it is much more profitable to invest these funds in the development / promotion of your own website / service.
UPD:
1. It is interesting and interesting to read some commentators, conspiracy therapists in relation to the “multi-provider”
2. The story has continued, as they say. I was contacted, as he says, the author of the second letter. And he reported something important. In general, see yourself evaluate what's what. Screenshots of correspondence:
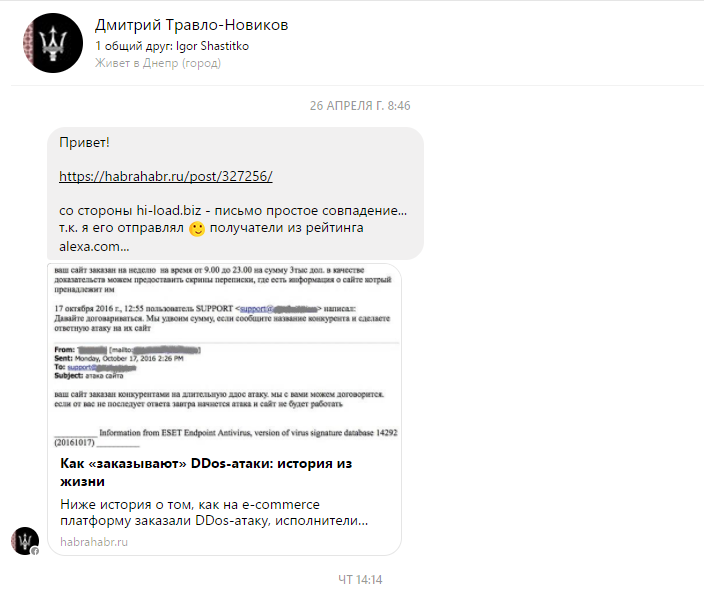
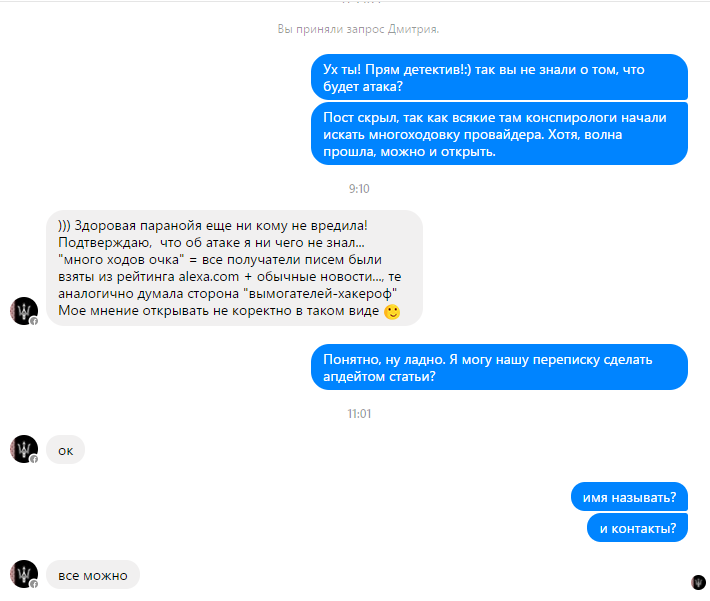
* For privacy reasons, all personal data is hidden.
This epic story began with a letter in which the site administration was informed that competitors had ordered a DDos attack on them.
')

The administration, of course, tried to negotiate with the hackers to find out - who “ordered” the attack? There was no response to the letter, i.e. agree with the hackers failed. This correspondence took place on October 17, 2016 at the end of the working day - the first letter about the attack came at about 16:00.
The next day, the attacks began, at the beginning it was a UDP flood attack, to warm up, so to speak. After this attack was repulsed, a second wave of HTTP flood attacks followed. But all attacks were repulsed by the provider.
Little touch: cherry on the cake!
But here's another interesting thing: on October 17, the day before the attack, an hour after the first letter about the impending attack (at 17:08), a letter “by chance” received a proposal to protect against DDoS :)

And what slogan, forgot to add a smiley!
As the saying goes "Coincidence? - I do not think! It is unlikely that hackers and “security specialists” are one and the same company, since it is not easy to combine 2 roles at once - and a “hacker” and a “security specialist” selling a solution from DDos attacks. But the one who sent the letter most likely knew about the impending attack from the hackers themselves and decided to also earn on the vulnerable position of the victim of a future attack (it is not known for sure, therefore all the contacts of the “security specialist” are hidden). On the other hand, it may well be that the “hackers” decided to make money without practicing the ordered attack.
In the case of the site of this client, the purpose of the attack was a week (!) Interruption in access to the site - in order to knock the site out of the search index. It would take up to 1 month or more to restore the previous, before the attack, positions of the site in search engines, which for the client is equivalent to a catastrophe.
The moral of this story is that it is better not to spend money and time to attack competitors, and it is much more profitable to invest these funds in the development / promotion of your own website / service.
UPD:
1. It is interesting and interesting to read some commentators, conspiracy therapists in relation to the “multi-provider”
2. The story has continued, as they say. I was contacted, as he says, the author of the second letter. And he reported something important. In general, see yourself evaluate what's what. Screenshots of correspondence:
Source: https://habr.com/ru/post/327256/
All Articles