How to approach the analysis of the site in terms of a hacker and identify vulnerabilities?
Step-by-step instructions on how to detect flaws in the security of web applications using Detectify to find vulnerabilities.
97% of applications tested by TrustWave are vulnerable to some kind of threat.

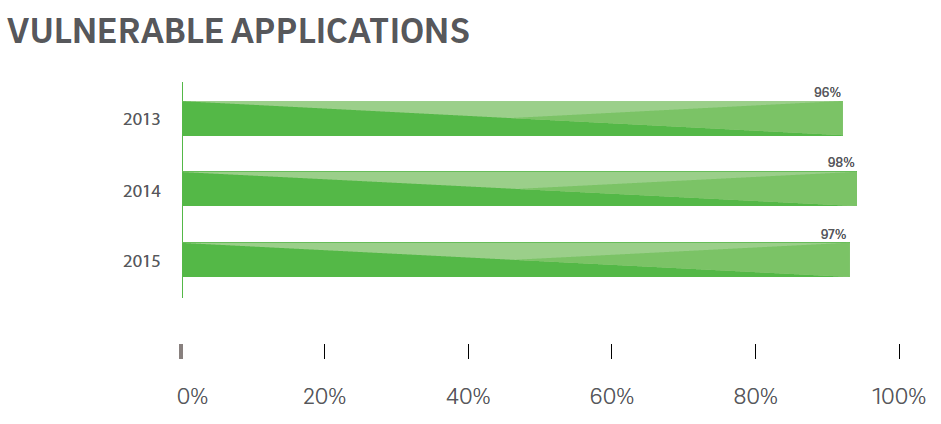
If the vulnerability of a web application is not resolved in time, it can damage the reputation and financial position of the company.
')
The sad truth is that most of the time most sites are in a vulnerable position. An interesting report was provided by White Hat Security , indicating the average number of days it takes to eliminate the vulnerability, depending on the industry.

How to ensure that known and unknown vulnerabilities of web applications are identified ?
There are many cloud tools to check . This article will discuss one of the promising SaaS platforms - Detectify .
Detectify is included in the development process, which allows you to identify security threats at an early stage of development (in a debugging / non-production environment) and eliminate them before running the application.
Integration into the development process is only one of many useful properties of the system, but it is not obligatory in the absence of a debugging environment.
In Detectify, it uses the automatic information collector about your site, optimizing tests based on the technologies used in the web application .
After verification, your site is scanned for more than 500 types of threats , including those from the OWASP Top-10 list with the creation of a report on each vulnerability found.
Among other things deserve attention:
Create reports. Test results can be exported as a short or full report. It is possible to upload the results to PDF, JSON or Trello. Also available to view only the list of OWASP Top-10 . Such a report will help you out if you are going to eliminate only threats from this list.
Integration. Using the Detectify API allows you to interact with your applications or the following:
A large number of available checks. As already mentioned, it is possible to search for more than 500 types of threats, which include:
Do not take all the work on yourself - invite colleagues to take part in tasks and share with them the results.
Setup tests for your requirements. Each application is unique. If necessary, you can use cookies that are suitable for you, client applications, headers, change the nature of the check, and conduct it for different devices.
Permanent security updates. This tool is updated regularly to ensure that all the latest threats are covered and monitored. For example, just last week more than 10 types of checks appeared .
CMS Security. If you are blogging, administering an information resource or an online store, most likely you are using a CMS , such as WordPress, Joomla, Drupal or Magento. Fortunately, a security check is also available for them.
Detectify performs detailed verification of the CMS to ensure that your site is not subject to potential threats emanating from them.
Check secure page. View pages with the need for authorization.
The free trial version of Detectify is valid for 14 days (no credit card details are required). Further, for example, I will create an account and check my website for security.
So, the account is created - you can add a site for the verification. Locate the "Scopes & Targets" menu on the toolbar and click on it.
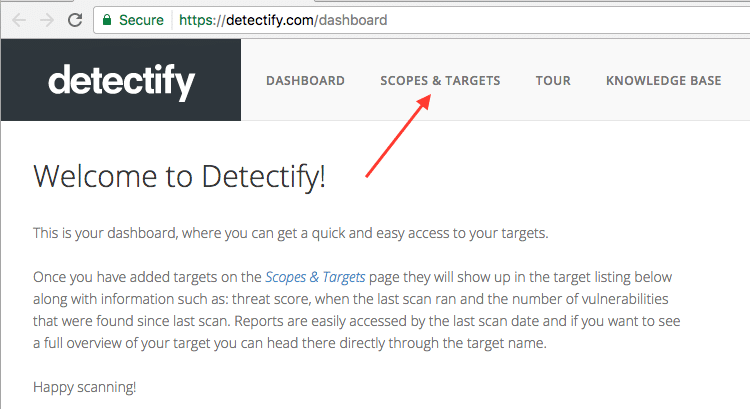
There are two ways to add a task (URL).
Choose what you like. I will import via Google Analytics .

That's all: you have added a URL to Detectify and now, when you wish, you can run a scan or set up a regular daily, weekly or monthly check.
It's time for some fun !

The verification process, which consists of seven stages , will begin, the progress of each of which will be displayed:

A full check will take some time (approximately 3-4 hours depending on the size of the site). The browser can be closed - upon completion of the check you will receive an email notification .
To check Geek Flare took about 3.5 hours. Here is what happened:

To view the report, you can follow the link from the letter or go to the toolbar.
Owners of the site and those responsible for security are primarily interested in reports. This is an extremely important feature, because you will have to troubleshoot problems that you will see.
When you enter the toolbar, you will see a list of your sites.
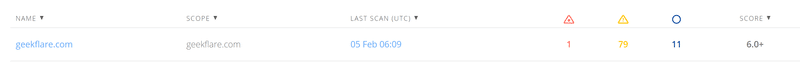
You can view the date and time of the last check, the results and the total score.
Threats with a high level of danger should be eliminated first.
And now let's consider a detailed report. In the toolbar, click on the website and you will be taken to the results page.
There are two options for viewing the threat level assessment. Results can either be viewed online or exported in PDF format.
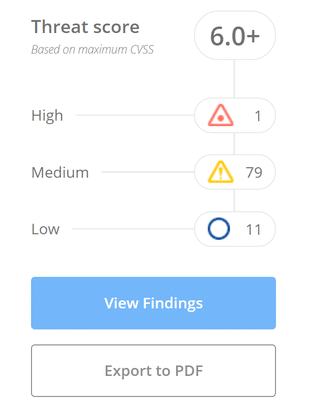
I have uploaded a PDF report, the volume of which was 351 pages. Here it is in detail !
Below is an example of a report on the site. Get more information by clicking on each of the sections.
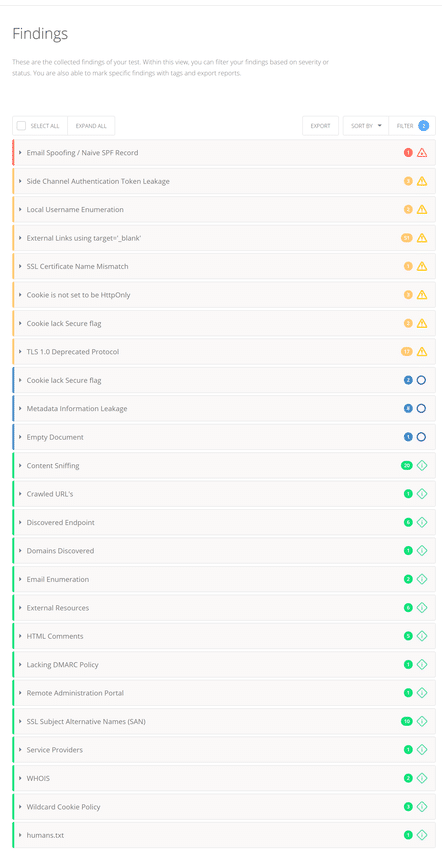
Each element of the report is accompanied by a clear explanation and recommendation . For the information security specialist, there should be enough to eliminate the threats.
Report on threats from the list of OWASP Top-10. If you are interested in threats exclusively from the OWASP Top-10 list, then you can view the results on them separately in the “Reports” section in the navigation panel on the left.
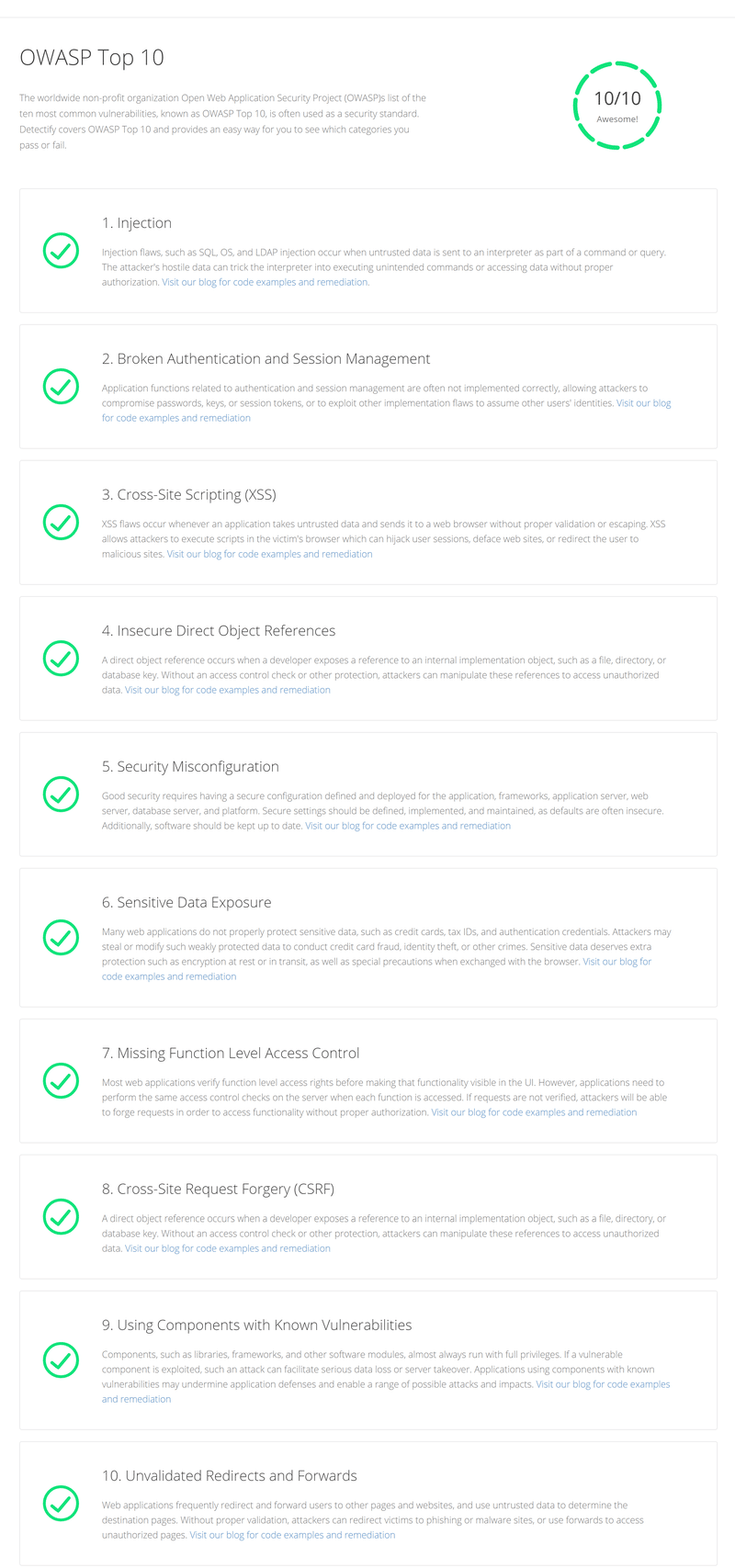
Examine the report and decide which threats to eliminate. After solving the problems in the report, you can rerun the test and check the results.
Based on your needs you can use many different useful settings.
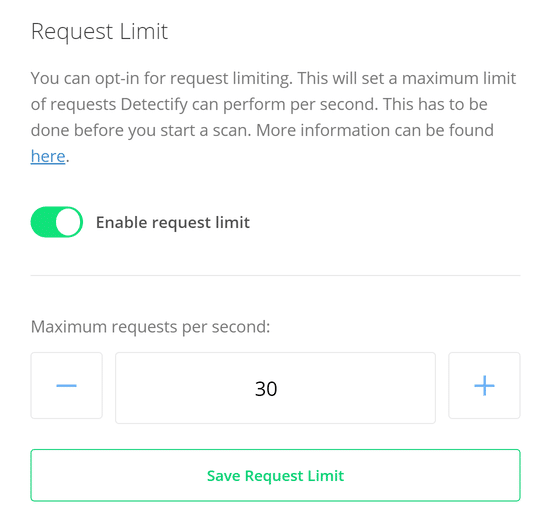
Limit the number of requests. If you want to limit the number of requests per second Detectify performs on your site, select the appropriate settings here. By default, this feature is disabled.
Subdomain The system can be configured so that Detectify does not check the subdomains. By default, the feature is enabled.

Set up a regular check. Modify the schedule so that the security check runs daily, weekly, or monthly. By default, the test runs weekly.
Customize cookies and headers. Select cookies and headers for verification.
Check with mobile devices. Validation can be run from various client applications. This will help those who want to check as a user of a mobile device, from their own client, etc.

Disable a specific type of check. What if you do not want to check for the presence of certain threats? In this section, such checks can be disabled.

Now you.
If you really want to understand how a hacker sees vulnerabilities, then try Detectify. Try a free trial and learn all the features.
HOSTING.cafe offers tools for searching virtual and dedicated servers, shared hosting and SSL certificates.
97% of applications tested by TrustWave are vulnerable to some kind of threat.


If the vulnerability of a web application is not resolved in time, it can damage the reputation and financial position of the company.
')
The sad truth is that most of the time most sites are in a vulnerable position. An interesting report was provided by White Hat Security , indicating the average number of days it takes to eliminate the vulnerability, depending on the industry.

How to ensure that known and unknown vulnerabilities of web applications are identified ?
There are many cloud tools to check . This article will discuss one of the promising SaaS platforms - Detectify .
Detectify is included in the development process, which allows you to identify security threats at an early stage of development (in a debugging / non-production environment) and eliminate them before running the application.
Integration into the development process is only one of many useful properties of the system, but it is not obligatory in the absence of a debugging environment.
In Detectify, it uses the automatic information collector about your site, optimizing tests based on the technologies used in the web application .
After verification, your site is scanned for more than 500 types of threats , including those from the OWASP Top-10 list with the creation of a report on each vulnerability found.
Detectify Features
Among other things deserve attention:
Create reports. Test results can be exported as a short or full report. It is possible to upload the results to PDF, JSON or Trello. Also available to view only the list of OWASP Top-10 . Such a report will help you out if you are going to eliminate only threats from this list.
Integration. Using the Detectify API allows you to interact with your applications or the following:
- Slack, Pager Duty, Hipchat - to receive instant alerts;
- JIRA - to create tasks based on search results;
- Trello - to display the results on the Trello panel;
- Zapier - to automate workflows.
A large number of available checks. As already mentioned, it is possible to search for more than 500 types of threats, which include:
- SQL / Blind / WPML / NoSQL SQL injection;
- cross-site scripting (XSS);
- cross-site request forgery (CSRF);
- remote / local file injection;
- SQL errors;
- unencrypted authorization session;
- data leakage;
- email spoofing;
- listing users or email;
- interrupted session;
- XPATH;
- malicious code.
Do not take all the work on yourself - invite colleagues to take part in tasks and share with them the results.
Setup tests for your requirements. Each application is unique. If necessary, you can use cookies that are suitable for you, client applications, headers, change the nature of the check, and conduct it for different devices.
Permanent security updates. This tool is updated regularly to ensure that all the latest threats are covered and monitored. For example, just last week more than 10 types of checks appeared .
CMS Security. If you are blogging, administering an information resource or an online store, most likely you are using a CMS , such as WordPress, Joomla, Drupal or Magento. Fortunately, a security check is also available for them.
Detectify performs detailed verification of the CMS to ensure that your site is not subject to potential threats emanating from them.
Check secure page. View pages with the need for authorization.
Getting Started with Detectify
The free trial version of Detectify is valid for 14 days (no credit card details are required). Further, for example, I will create an account and check my website for security.
- Fill out the information on the test account creation page and click “Continue”.

- You will receive a confirmation email to verify your credentials.

- Click “Verify the email to get it started” and you will be taken to the toolbar with the familiarization guide.
- Here you can look through step-by-step instructions or watch a video, but for now I’m closing this window.
So, the account is created - you can add a site for the verification. Locate the "Scopes & Targets" menu on the toolbar and click on it.

There are two ways to add a task (URL).
- Manually - enter the URL manually.
- Automatically - Import URLs with Google Analytics.
Choose what you like. I will import via Google Analytics .
- Click “Use Google Analytics” (use Google Analytics) and enter your Google account details to get the URL information. After adding information about the URL.

That's all: you have added a URL to Detectify and now, when you wish, you can run a scan or set up a regular daily, weekly or monthly check.
Run security check
It's time for some fun !
- Go to the toolbar and click on the newly added URL.
- Click “Start Scan” at the bottom right of the screen.

The verification process, which consists of seven stages , will begin, the progress of each of which will be displayed:
- Start;
- collection of information;
- Search;
- creating a digital print;
- information analysis;
- exploitation;
- completion

A full check will take some time (approximately 3-4 hours depending on the size of the site). The browser can be closed - upon completion of the check you will receive an email notification .
To check Geek Flare took about 3.5 hours. Here is what happened:

To view the report, you can follow the link from the letter or go to the toolbar.
Examining the Detectify Report
Owners of the site and those responsible for security are primarily interested in reports. This is an extremely important feature, because you will have to troubleshoot problems that you will see.
When you enter the toolbar, you will see a list of your sites.

You can view the date and time of the last check, the results and the total score.
- red icon - high level of danger;
- yellow icon - medium danger level;
- blue icon - low level of danger.
Threats with a high level of danger should be eliminated first.
And now let's consider a detailed report. In the toolbar, click on the website and you will be taken to the results page.
There are two options for viewing the threat level assessment. Results can either be viewed online or exported in PDF format.

I have uploaded a PDF report, the volume of which was 351 pages. Here it is in detail !
Below is an example of a report on the site. Get more information by clicking on each of the sections.

Each element of the report is accompanied by a clear explanation and recommendation . For the information security specialist, there should be enough to eliminate the threats.
Report on threats from the list of OWASP Top-10. If you are interested in threats exclusively from the OWASP Top-10 list, then you can view the results on them separately in the “Reports” section in the navigation panel on the left.

Examine the report and decide which threats to eliminate. After solving the problems in the report, you can rerun the test and check the results.
Detectify Settings Study
Based on your needs you can use many different useful settings.
In the Settings section, select basic.
Limit the number of requests. If you want to limit the number of requests per second Detectify performs on your site, select the appropriate settings here. By default, this feature is disabled.

Subdomain The system can be configured so that Detectify does not check the subdomains. By default, the feature is enabled.

Set up a regular check. Modify the schedule so that the security check runs daily, weekly, or monthly. By default, the test runs weekly.
In the Settings section, select Advanced.
Customize cookies and headers. Select cookies and headers for verification.
Check with mobile devices. Validation can be run from various client applications. This will help those who want to check as a user of a mobile device, from their own client, etc.

Disable a specific type of check. What if you do not want to check for the presence of certain threats? In this section, such checks can be disabled.

Now you.
If you really want to understand how a hacker sees vulnerabilities, then try Detectify. Try a free trial and learn all the features.
HOSTING.cafe offers tools for searching virtual and dedicated servers, shared hosting and SSL certificates.
Source: https://habr.com/ru/post/326832/
All Articles