Fighting HTTPS traffic interception. Experience Yandex Browser
According to a study by employees of Mozilla, Google, Cloudflare and a number of universities, from 4 to 11% of secure connections are “tapped” as a result of installing questionable root certificates on users' computers that do not even realize the risk. Today I will talk about how our team draws attention to this problem with the help of Yandex. Browser.
It is unlikely on Habré to talk in detail about the SSL certificates and the tasks that they solve, but just in case, briefly recall the main point (you can just skip a couple of paragraphs, if you are well aware of the principles of work). Any site can now easily receive a closed lock in the address bar of the browser, so the certificate is in no way a sign of the site’s “reliability”, despite the appropriate labeling in Chromium . Nevertheless, it performs the important function of protecting our data with you from interception. The network administrator or an attacker who gains access to the traffic still needs to come up with a way to decrypt the stream, which is usually difficult to do with strong cryptography and the absence of a key.
')
If you can not decrypt the stream, you can redirect it through yourself, forcing the browser to establish a connection not with the site, but with its own server (man-in-the-middle attack). For example, you can hack a user's router and redirect it to a phishing site to steal passwords by spoofing DNS responses. An experienced user is unlikely to encounter this, and you can set up an alternative DNS server with DNSCrypt directly in your browser for your loved ones. But if the attacker wants to go further and begins to act as an intermediary between the user and the HTTPS site, then another task of the certificate will save us - authentication.
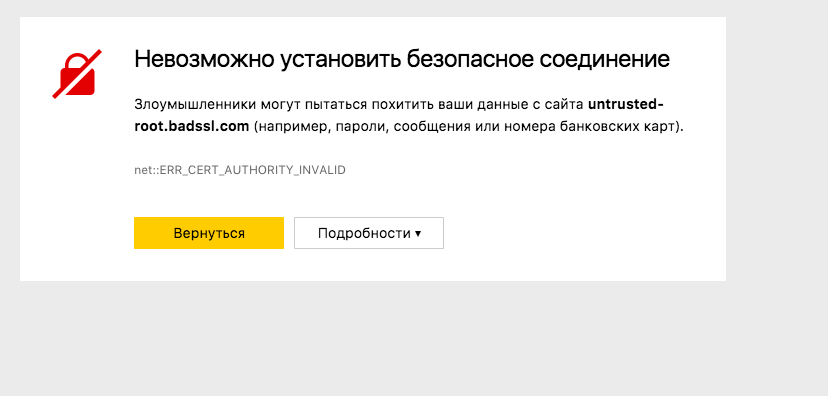
When the browser receives a certificate from the site, it must make sure that it was the site that sent it, and not the “man in the middle”. You can confirm this with the help of root certificates that are in the OS repository. If the certificate that allegedly sent the site cannot find the confirming root, then any modern browser will display something like this:
In order to circumvent such protection and hide the fact of their interference with traffic from the user, there remains only one thing - to place their root certificate in the system storage, which legalizes in the eyes of the browser the malicious certificates signed by them. And any application can do this. And with administrator rights also without warnings and questions to the user. A person installs a program from a questionable site, and receives a wiretap of traffic in the appendage. And not a single modern browser will respond to it at all. You will see all the same inscription "Reliable" and green lock. Unless in the case of Firefox, attackers will need to add their root certificate also to the storage of this browser, because it does not use the system one (but this is no more difficult to do).
If we exclude cases regarding the legal use of this feature by programs (antiviruses, ad blockers, Fiddler) and control of employees in organizations, then this practice usually leads to shocking and dangerous advertising on the pages visited. Users in most cases do not know about the causes, blame the site owners or even the developers of Yandex. Browser. You can imagine how sometimes it’s difficult for our support service to get to the cause and help a person. But so the problem is at least noticeable. But in some cases, no external manifestations occur, and the data is simply stolen.

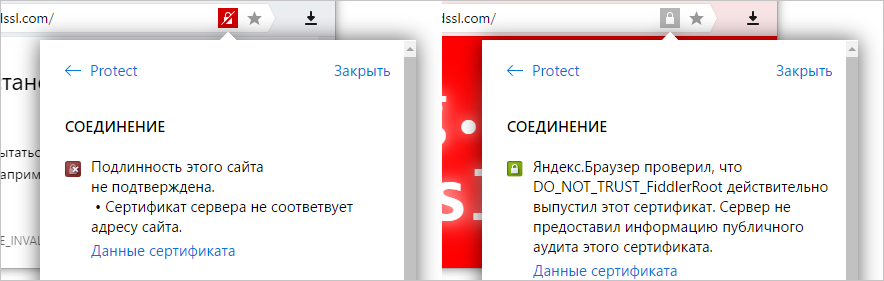
Moreover, the harm from intruders is not only direct (in the form of data interception and advertising), but also indirect. In the normal situation, we can click on the lock and find out which certification center issued the certificate, evaluate its reliability ( in Yandex Browser; in other browsers this information is often hidden). When replacing this data is hidden from us. And not only these, but any other problems with the connection. If an incorrect certificate is used on the site, which would inevitably lead to a full-fledged warning stub in any browser, then replacing the certificate masks the problem from the user - the usual closed lock is displayed in the address bar. All this leads to a general drop in the level of security.
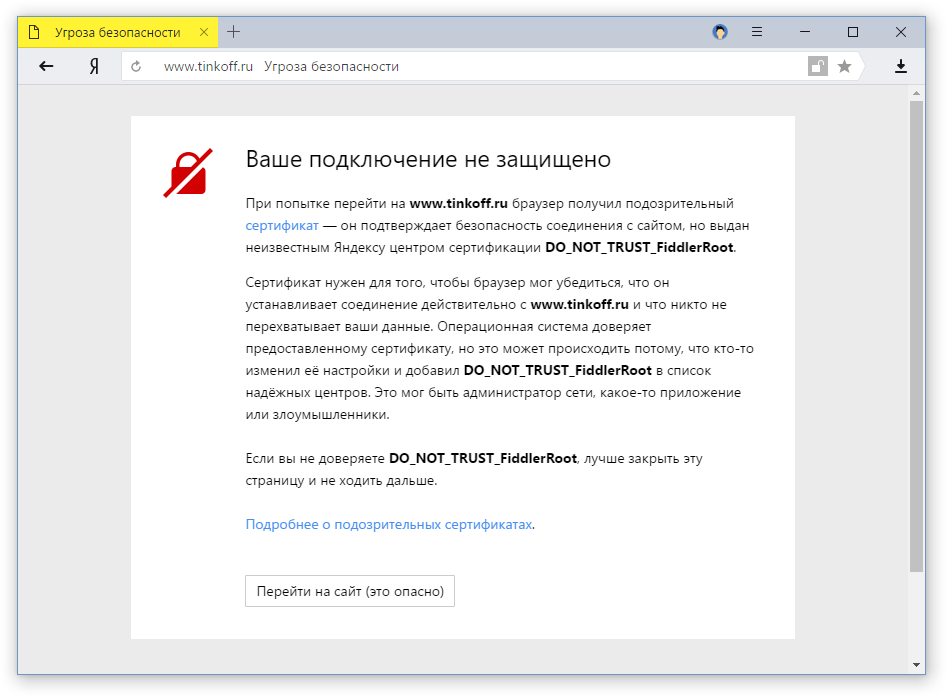
According to preliminary estimates, already about 400 thousand users from the weekly audience of Yandex. Browser live with the interception of traffic. And this is minus antiviruses! That is why we seriously took up the problem and began to experiment with revealing the fact that a doubtful root certificate was installed in the system. It works as follows. Now Yandex.Browser does not blindly trust the root certificate from the system storage, but checks it against the list of well-known authoritative certificate authorities. And if the root certificate is not familiar to the browser, then we open the lock and honestly report potential risk.

The solution with an open lock is relatively soft - watched the reaction of users. But a few days ago we moved on to the next stage. Now, when you download important sites, which include banks, payment and search engines, popular social networks, a full warning appears about the threat.
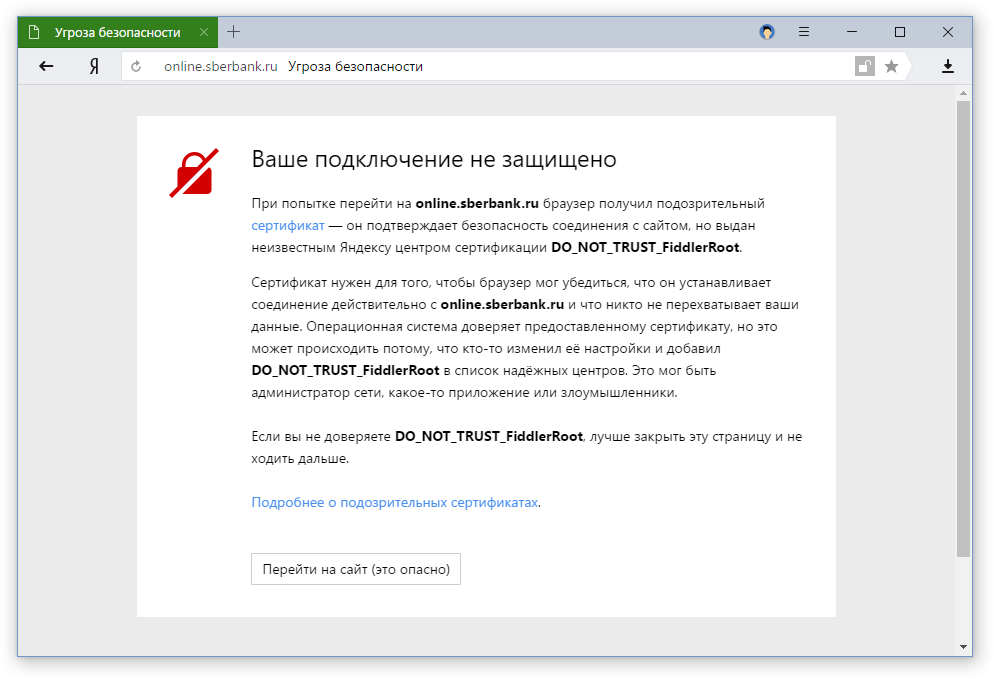
The warnings in Yandex Browser cannot be called a panacea, because they have no effect on the main source of the problem - the program that installs its root certificate. But we hope that informing users will draw their attention to the risk of data loss or at least simplify diagnostics. After all, even the fact of intercepting traffic to this point was hidden from people.

It is unlikely on Habré to talk in detail about the SSL certificates and the tasks that they solve, but just in case, briefly recall the main point (you can just skip a couple of paragraphs, if you are well aware of the principles of work). Any site can now easily receive a closed lock in the address bar of the browser, so the certificate is in no way a sign of the site’s “reliability”, despite the appropriate labeling in Chromium . Nevertheless, it performs the important function of protecting our data with you from interception. The network administrator or an attacker who gains access to the traffic still needs to come up with a way to decrypt the stream, which is usually difficult to do with strong cryptography and the absence of a key.
')
If you can not decrypt the stream, you can redirect it through yourself, forcing the browser to establish a connection not with the site, but with its own server (man-in-the-middle attack). For example, you can hack a user's router and redirect it to a phishing site to steal passwords by spoofing DNS responses. An experienced user is unlikely to encounter this, and you can set up an alternative DNS server with DNSCrypt directly in your browser for your loved ones. But if the attacker wants to go further and begins to act as an intermediary between the user and the HTTPS site, then another task of the certificate will save us - authentication.
When the browser receives a certificate from the site, it must make sure that it was the site that sent it, and not the “man in the middle”. You can confirm this with the help of root certificates that are in the OS repository. If the certificate that allegedly sent the site cannot find the confirming root, then any modern browser will display something like this:

In order to circumvent such protection and hide the fact of their interference with traffic from the user, there remains only one thing - to place their root certificate in the system storage, which legalizes in the eyes of the browser the malicious certificates signed by them. And any application can do this. And with administrator rights also without warnings and questions to the user. A person installs a program from a questionable site, and receives a wiretap of traffic in the appendage. And not a single modern browser will respond to it at all. You will see all the same inscription "Reliable" and green lock. Unless in the case of Firefox, attackers will need to add their root certificate also to the storage of this browser, because it does not use the system one (but this is no more difficult to do).
If we exclude cases regarding the legal use of this feature by programs (antiviruses, ad blockers, Fiddler) and control of employees in organizations, then this practice usually leads to shocking and dangerous advertising on the pages visited. Users in most cases do not know about the causes, blame the site owners or even the developers of Yandex. Browser. You can imagine how sometimes it’s difficult for our support service to get to the cause and help a person. But so the problem is at least noticeable. But in some cases, no external manifestations occur, and the data is simply stolen.

Moreover, the harm from intruders is not only direct (in the form of data interception and advertising), but also indirect. In the normal situation, we can click on the lock and find out which certification center issued the certificate, evaluate its reliability ( in Yandex Browser; in other browsers this information is often hidden). When replacing this data is hidden from us. And not only these, but any other problems with the connection. If an incorrect certificate is used on the site, which would inevitably lead to a full-fledged warning stub in any browser, then replacing the certificate masks the problem from the user - the usual closed lock is displayed in the address bar. All this leads to a general drop in the level of security.

According to preliminary estimates, already about 400 thousand users from the weekly audience of Yandex. Browser live with the interception of traffic. And this is minus antiviruses! That is why we seriously took up the problem and began to experiment with revealing the fact that a doubtful root certificate was installed in the system. It works as follows. Now Yandex.Browser does not blindly trust the root certificate from the system storage, but checks it against the list of well-known authoritative certificate authorities. And if the root certificate is not familiar to the browser, then we open the lock and honestly report potential risk.

The solution with an open lock is relatively soft - watched the reaction of users. But a few days ago we moved on to the next stage. Now, when you download important sites, which include banks, payment and search engines, popular social networks, a full warning appears about the threat.

The warnings in Yandex Browser cannot be called a panacea, because they have no effect on the main source of the problem - the program that installs its root certificate. But we hope that informing users will draw their attention to the risk of data loss or at least simplify diagnostics. After all, even the fact of intercepting traffic to this point was hidden from people.
Source: https://habr.com/ru/post/326796/
All Articles