Do not believe the navigator: GPS and GLONASS vulnerabilities
Image: 2Tales , Flickr
Now the GPS / GLONASS receiver is not only in every smartphone, but even in those devices that do not move much - in industrial installations, in telemetry sensors, in ATMs. In addition, such receivers provide navigation in automatically controlled systems, from urban transport to military drones. Global positioning systems have penetrated so deeply into all areas of our lives that most people use them without thinking about how much they can be trusted.
')
Meanwhile, there are already many examples confirming that such systems are vulnerable to various attacks, including spoofing, that is, signal substitution. More than 5 years ago, the Iranian military was able to land an American drone using this technique . And at the end of 2016, the topic of many media was the distortion of GPS and GLONASS in the center of Moscow, near the Kremlin: the navigators suddenly showed their users that they were at Vnukovo airport . We decided to find out whether you really need the capabilities of the special services in order to provoke such failures.
Principles of global positioning
To begin with, let us clarify that now there is not one or even two global positioning systems in the world. In addition to the well-known American GPS, there is a Russian GLONASS, European Galileo, Chinese BeiDou, Japanese QZSS, Indian IRNSS, as well as the SBAS system consisting of almost every one of them. Together, they are called Global Navigation Satellite Systems (GNSS). However, only the first two provide complete global coverage at the moment. QZSS and IRNSS work only in certain parts of the globe, and full coverage is not planned. But all these systems are subject to the same vulnerabilities, since they use the same principle of operation and similar technologies for transmitting signals from satellites. We look at these vulnerabilities on the example of GPS.
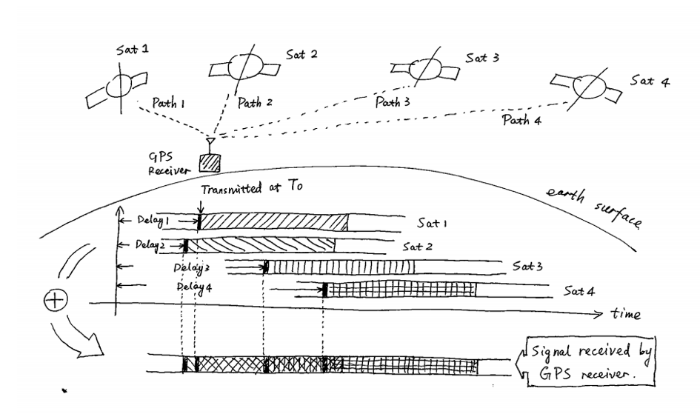
Global positioning systems operate on the basis of satellites that transmit accurate time signals (each of them has an atomic clock), as well as its location. The message structure looks like this:

The receiver receives a signal from several such satellites with different delays, depending on the distance to each satellite. Thus, by solving a system of equations, you can determine the distance to each of them, and then, knowing the coordinates of the satellites, calculate your location.
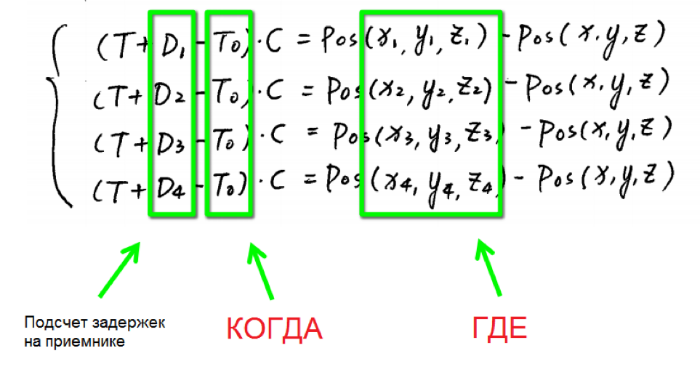
Using this knowledge, you can generate a signal with given parameters of coordinates and time. Good people have already taken care of this, and now anyone can build an application from source that allows you to generate such signals . And then, using an SDR (Software Defined Radio) transceiver, an attacker can send such a signal to the user's device instead of the real GPS signal, that is, to replace the coordinates and time. Thus, you need only $ 350 per SDR plus any laptop to get a “navigation weapon”. Below are examples of attacks that it allows.
Control drones . Civilian quadcopters have in their program prohibited coordinates of objects over which they cannot fly, for example, airports and stadiums. Using the above-described "navigation weapon", you can convince the quadcopter that he was at Vnukovo, as a result of which he will not be able to fly further and sit down. It is assumed that it is this kind of protection from drones that explains GPS crashes around the Kremlin.
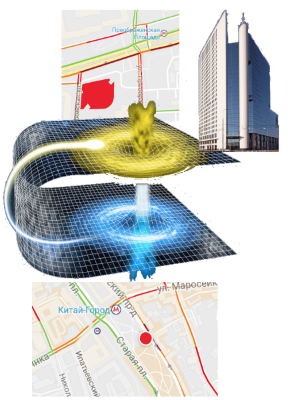 The curvature of space . In one of our experiments, GPS spoofing lasted several days. After that, Google indexed the Wi-Fi access points and mobile operators base stations around us, as a result of which he now believes that our business center is located in China Town (in fact, it is located 7 km from China Town).
The curvature of space . In one of our experiments, GPS spoofing lasted several days. After that, Google indexed the Wi-Fi access points and mobile operators base stations around us, as a result of which he now believes that our business center is located in China Town (in fact, it is located 7 km from China Town).Here again, it is worth emphasizing that such attacks do not need to be a special service. In 2016, these techniques massively "went to the people" thanks to the game with augmented reality Pokémon Go. There are manuals on the Internet that clearly explain how using GPS spoofing you can “distort the map” and catch Pokémon without leaving your home.
Time machine More unexpected consequences brought our experiments to change the time. Apple devices unconditionally and without the knowledge of the user translate the time according to the GPS signal, substituting the last year. As a result, phones lose their call history, SSL certificates are invalid, many sites and mail stop working. And smart watches worth more than $ 500 just went to warranty repair after they received the GPS time from last year. By the way, time can be transferred not only to the past, but also to the future - which will also lead to various failures.

Such attacks can threaten not only user gadgets. For example, the Avtodoria automatic speeding systems, which calculate the average speed of all vehicles by measuring the travel time of a certain section of the road, use GPS to synchronize the time between two devices and to calculate the distance between them. Therefore, it is not difficult to disable this system using the above described “time machine”.

Even more dangerous is the forgery of satellite signals in the case of industrial synchronization systems - in the power industry or in the mining industry. For example, to calculate electricity or to select power supply schemes at different sites, time synchronization is used according to the same GPS system. Deceiving such a system for just a few seconds will cause the system to miss megawatts of electricity.

Image: Ricardo Diaz , Flickr
What to do
To protect against such attacks, we recommend using combined GPS / GLONASS / Galileo / BeiDou receivers, as well as backup time sources (for example, NTP) and alternative navigation systems (for example, targeting base stations and Wi-Fi) to verify the satellite signal. Well, ordinary travelers should not forget about the existence of classic paper maps, road signs and talkative locals.
Authors : Pavel Novikov, Arthur Garipov
Source: https://habr.com/ru/post/326786/
All Articles