“Now Required”: Issuing SSL Certificates with DNS Records
This year, the public organizations responsible for distributing certificates will necessarily take into account special DNS records. These records allow domain owners to determine the “circle of people” who are allowed to issue SSL / TLS certificates (we wrote about them in our previous post ) for their domain.

/ Flickr / jim pennucci / cc
DNS records have been used since 2013, but their use was more of an advisory nature, because CAs (certificate authorities) were not required to obey these rules. But here the participants of the CA / Browser forum, which unites the creators of popular browsers and certification companies, voted to make the Certification Authority Authority Authorization (CAA) verification procedure part of the certificate issuance process.
')
“CAA will not become a“ silver bullet ”, but it will be another level of protection,” said Scott Helme, information security consultant.
This requirement will come into force on September 8, and those CAs that cannot satisfy it will risk fines. Thus, certificate authorities will now have to verify that requests for issuing an SSL / TLS certificate are received from the domain owner.
The purpose of this solution is to reduce the number of unauthorized issuance of certificates when a certification authority is compromised or a domain is hacked, when an attacker can request a valid certificate for a compromised domain from any certificate authority and subsequently use it to conduct MITM attacks or redirect users to phishing resources.
To create a record for domain owners, you can use the CAA Record Generator tool, which automatically generates the correct command lines.
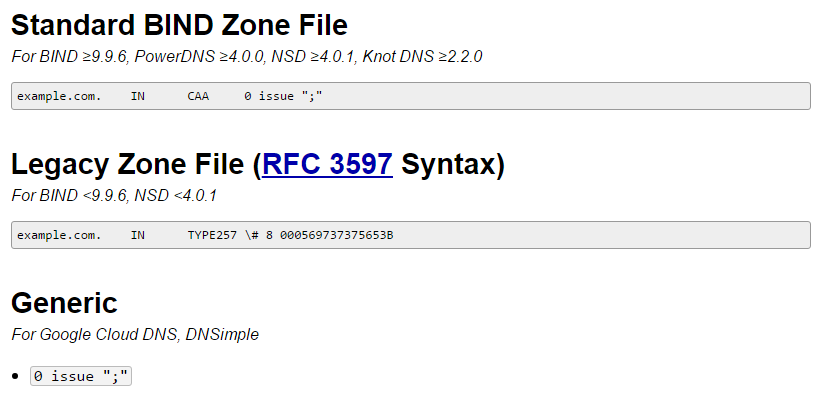
In addition to the issue tag, which defines legitimate CAs, the entry will support the iodef tag, which verification will also be mandatory. This tag will allow the domain owner to specify email addresses or URLs to which CAs will be required to send suspicious certificate request notifications.
PS Here are some more materials on the topic from the IaaS provider blog 1cloud:

/ Flickr / jim pennucci / cc
DNS records have been used since 2013, but their use was more of an advisory nature, because CAs (certificate authorities) were not required to obey these rules. But here the participants of the CA / Browser forum, which unites the creators of popular browsers and certification companies, voted to make the Certification Authority Authority Authorization (CAA) verification procedure part of the certificate issuance process.
')
“CAA will not become a“ silver bullet ”, but it will be another level of protection,” said Scott Helme, information security consultant.
This requirement will come into force on September 8, and those CAs that cannot satisfy it will risk fines. Thus, certificate authorities will now have to verify that requests for issuing an SSL / TLS certificate are received from the domain owner.
The purpose of this solution is to reduce the number of unauthorized issuance of certificates when a certification authority is compromised or a domain is hacked, when an attacker can request a valid certificate for a compromised domain from any certificate authority and subsequently use it to conduct MITM attacks or redirect users to phishing resources.
To create a record for domain owners, you can use the CAA Record Generator tool, which automatically generates the correct command lines.

In addition to the issue tag, which defines legitimate CAs, the entry will support the iodef tag, which verification will also be mandatory. This tag will allow the domain owner to specify email addresses or URLs to which CAs will be required to send suspicious certificate request notifications.
PS Here are some more materials on the topic from the IaaS provider blog 1cloud:
Source: https://habr.com/ru/post/326734/
All Articles