Lazarus is omnipresent
 Hacking Sony Entertainment, robbing Bangladesh’s central bank and bold attacks on the SWIFT system around the world, destroying data from South Korean media and financial companies. It would seem that there is nothing in common between these shares. And every time it was the same guys from the group Lazarus .
Hacking Sony Entertainment, robbing Bangladesh’s central bank and bold attacks on the SWIFT system around the world, destroying data from South Korean media and financial companies. It would seem that there is nothing in common between these shares. And every time it was the same guys from the group Lazarus .Both the scale of the campaigns, the diversity and the volume of costs are impressive - only our researchers were able to link over 150 malicious tools to Lazarus! In fact, for each attack, hackers wrote new tools - from exploits to erasers. The code was new, but not completely, which eventually gave them away. A detailed report on the well-known activities of Lazarus contains 58 pages, but here I will give the most interesting moments.
Variability and heredity
In fact, linking all of the above attacks with Lazarus is very, very difficult. First of all, because the guys motto is a constant change in the tools used. In most cases, the compilation takes place no more than two days before the attack. This makes signature analysis tools completely useless and severely limits the effectiveness of Yara. That is why, at first glance, all these attacks are carried out by different people, but a complete immersion in the code tells us the opposite.
')
Having adopted the variability, hackers could not escape heredity. Writing code from scratch every time is not only difficult, but also extremely costly. Therefore, a certain continuity between different at first glance tools can be traced quite clearly. For example, a comparison of samples from Bangladesh and Southeast Asia shows that the function of writing to the log was transferred to a new code with minor modifications - the new code also writes to the log of the current process.
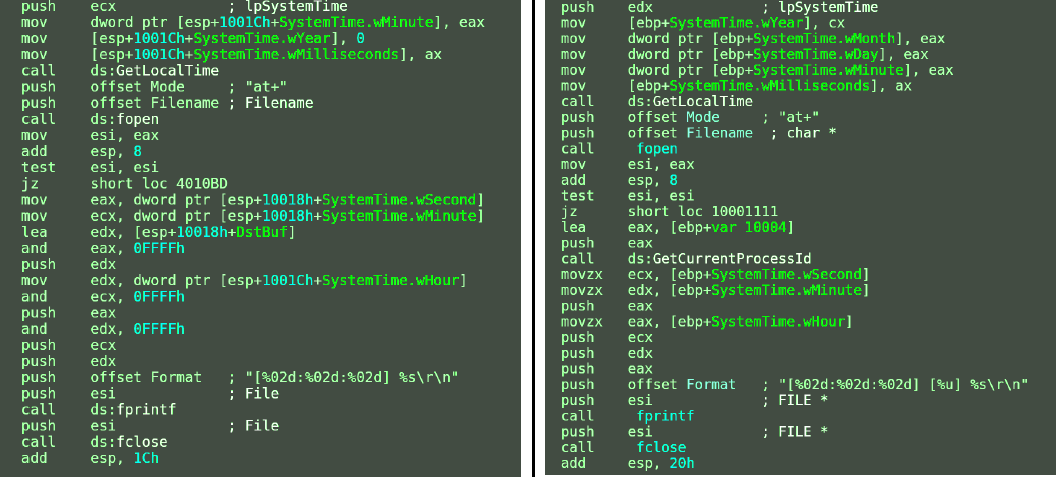
When comparing Malvari found after two other incidents, researchers from Novetta noticed the use of the same magic number 0xA0B0C0D0 of the configuration file in two different tools, which can not be exactly a coincidence (see lpFileData in the screenshot).
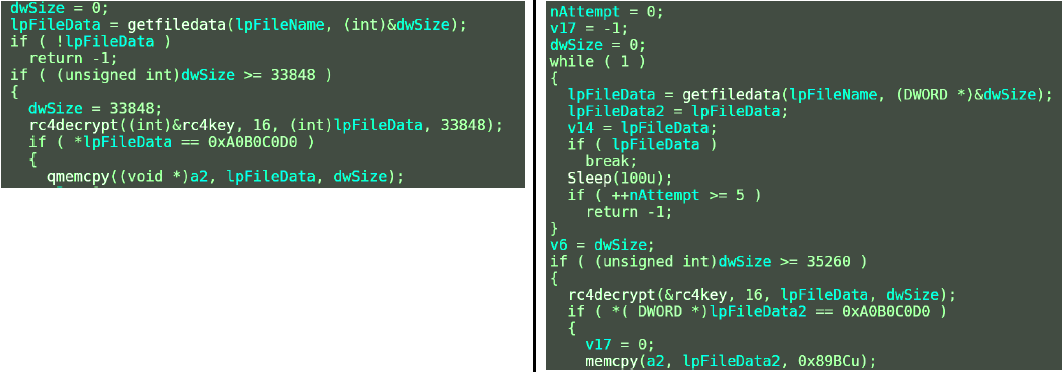
After the publication of the Novetta report, the hackers fixed it, but not quite - the number is different, but the verification algorithm is the same.
And, by the way, if you think that the successive evolution of Lazarus campaigns are described here, you are mistaken. According to our analysts, the attacks on the Central Bank of Bangladesh and the aforementioned bank from Southeast Asia were carried out simultaneously and practically synchronously, which means that these are parts of one big operation to extract hundreds of millions of dollars.
Swift at gunpoint
We believe that a separate unit within the group is involved in the extraction of money to finance Lazarus operations. Our analysts dubbed him Bluenoroff (after the name of one of the tools used in attacks on banks). Bluenoroffs are focused on banks, casinos, developers of financial software and cryptocurrency services. The motivation is transparent, the methods are clever, the geography is extremely extensive - from Mexico to Malaysia.

Bluenoroff is not interested in theft and destruction of data. Their goal is purely real money.
Bluenoroff's attack patterns on banks are simple but effective. The group has studied very well SWIFT software (international network of interbank transfers), and probably periodically reverses it. It all starts as usual, with hacking the bank's network.
Researchers have described several noteworthy vectors:
- Compromise of the bank’s freshly installed web server. In general, the bank acted cautiously, hiring pentesters to verify the protection of the site. Well, Lazarus hacked it right during the tests. There are two possibilities: either the hackers managed to take advantage of the vulnerability that was closed after the pentest, or they locked the shell, which the pentesters themselves did and stuck to the server. In any case, it is beautiful.
- Polish bank was infected through the website of the Polish financial regulator. Hackers introduced an exploit for IE to the site, which launched Malvari loader on the attacked machine.
- Exploit for Adobe Flash, posted on the site of the manufacturer of building materials. It is curious that hackers successfully exploited a long-closed vulnerability. As it turned out, there was a Flash version 20.0.0.235 on the infected machine, released back in December 2015. All this time, he regularly tried to update, but nothing worked - the updater could not find a proxy server on the bank’s network in order to connect to the update server.
Then the attack is secretly distributed over the network, while the keylogger collects the credentials of the employees (all of a sudden the administrator will be caught).
Some hardcore about keylogger
Known file names: NCVlan.dat
File size: 73216 bytes
Type: PE32 + (DLL) (GUI) x86-64, MS Windows
Linking Date: 2016.04.06 07:38:57 (GMT)
Linker Version: 10.0
Original title: grep.dll
Where caught: incident # 1 (attack on a bank in Southeast Asia)
Character: Nordic, sustained.Merciless to the enemies of the Reich.
The user-space keylogger, after launching, creates a new thread, which, apparently, must be loaded by some PE loader (for example, a DLL injector). The stream sets the class Shell TrayCls% RANDOM% ", where% RANDOM% is an integer random generated by the system generator from the grain in the form of system time. Then the stream creates a window“ Shell Tray% RANDOM%. The new window registers the keyboard interceptor and starts recording keystrokes and text from the clipboard.
Protocol keylogger leads in a file located in the user profile directory, the name is set as NTUSER {% USERNAME%}. TxS.blf. Data is encrypted on RC4 with a 64-byte key (hard-coded). The key is not completely random, it seems, inside an ASCII text fragment, or from a database, or from a database query:
Perhaps this is done to make it difficult to recognize the key when analyzing the code, or for false positives of the signature analysis, if someone guesses to include part of this key in the signature.
The binary keylogger log file consists of records organized into blocks according to events:
1. Start the session. Within the user name, session type (conal, RDP, etc.), session identifier.
2. Actions in this session. Names of active windows and keystroke sequences.
3. End of the session. Username and session ID.
Each entry contains a time stamp in DWORD.
The keylogger also launches a watchdog thread that tracks the creation of the ODBCREP.HLP file in the directory of the current DLL. If the file is found, the keylogger deletes the keyboard interceptor and is unloaded from memory.
File size: 73216 bytes
Type: PE32 + (DLL) (GUI) x86-64, MS Windows
Linking Date: 2016.04.06 07:38:57 (GMT)
Linker Version: 10.0
Original title: grep.dll
Where caught: incident # 1 (attack on a bank in Southeast Asia)
Character: Nordic, sustained.
The user-space keylogger, after launching, creates a new thread, which, apparently, must be loaded by some PE loader (for example, a DLL injector). The stream sets the class Shell TrayCls% RANDOM% ", where% RANDOM% is an integer random generated by the system generator from the grain in the form of system time. Then the stream creates a window“ Shell Tray% RANDOM%. The new window registers the keyboard interceptor and starts recording keystrokes and text from the clipboard.
Protocol keylogger leads in a file located in the user profile directory, the name is set as NTUSER {% USERNAME%}. TxS.blf. Data is encrypted on RC4 with a 64-byte key (hard-coded). The key is not completely random, it seems, inside an ASCII text fragment, or from a database, or from a database query:
"SUM.0USD0,0>'DBT LIMITCUSD0,..CDT.SUM.1USD265,0.7CDT.LIMIT.USD0," Perhaps this is done to make it difficult to recognize the key when analyzing the code, or for false positives of the signature analysis, if someone guesses to include part of this key in the signature.
The binary keylogger log file consists of records organized into blocks according to events:
1. Start the session. Within the user name, session type (conal, RDP, etc.), session identifier.
2. Actions in this session. Names of active windows and keystroke sequences.
3. End of the session. Username and session ID.
Each entry contains a time stamp in DWORD.
The keylogger also launches a watchdog thread that tracks the creation of the ODBCREP.HLP file in the directory of the current DLL. If the file is found, the keylogger deletes the keyboard interceptor and is unloaded from memory.
Keylogger Friend - Injector
File size: 1515008 bytes
Type: PE32 + (DLL) (GUI) x86-64, MS Windows
Linking Date: 2016.12.08 00:53:43 (GMT)
Linker Version: 10.0
Export Name: wide_loader.dll
Where caught: incident # 2 (attack on a European bank)
The module is packed with Enigma Protector and implemented as a service binary with the ServiceMain procedure. At the start, it imports all the necessary functions of the system API and searches for the file% SYSTEMROOT% \ Help \% name% .chm, where% name% is the name of the current DLL of the module. The module then decrypts the code from .chm using the Spritz algorithm with a hard-coded 64-byte key.
Next, it searches for the target process and tries to inject the decrypted code into its address space. Able to perform injection with two processes to choose from - lsass.exe or in its own service process. Where exactly - is determined when compiling the module. The sample found injected the code into your process.
In Europe and the Middle East, several more injector samples were found, with the names srservice.dll, msv2_0.dll, SRService.dll and of different sizes. They differ in that they are not packed with an Enigma, and use 32-byte keys. They perform the same tasks — they embed the code in lsass.exe or in their process. And in these cases .chm contained an active backdoor.
Type: PE32 + (DLL) (GUI) x86-64, MS Windows
Linking Date: 2016.12.08 00:53:43 (GMT)
Linker Version: 10.0
Export Name: wide_loader.dll
Where caught: incident # 2 (attack on a European bank)
The module is packed with Enigma Protector and implemented as a service binary with the ServiceMain procedure. At the start, it imports all the necessary functions of the system API and searches for the file% SYSTEMROOT% \ Help \% name% .chm, where% name% is the name of the current DLL of the module. The module then decrypts the code from .chm using the Spritz algorithm with a hard-coded 64-byte key.
Next, it searches for the target process and tries to inject the decrypted code into its address space. Able to perform injection with two processes to choose from - lsass.exe or in its own service process. Where exactly - is determined when compiling the module. The sample found injected the code into your process.
In Europe and the Middle East, several more injector samples were found, with the names srservice.dll, msv2_0.dll, SRService.dll and of different sizes. They differ in that they are not packed with an Enigma, and use 32-byte keys. They perform the same tasks — they embed the code in lsass.exe or in their process. And in these cases .chm contained an active backdoor.
Finally, when a SWIFT server is detected and infected on the network, hackers intercept the administrator session and manipulate the database. As a result, millions of dollars (in the case of the Bangladesh Central Bank - $ 81 million) go to the wrong address.
After the sensational attack on Bangladesh, SWIFT updated its software, adding additional checks for the integrity of the code and database. It must be said that it didn’t bother the Bluenoroffs - in the next attack, their malware deftly turned off these checks. Tellingly, she also knows how to return software to its original state.
Obfuscation traces
A curious thing - hackers monitor hacked systems through a set of backdoors, through a TCP tunnel. However, not directly: infected machines form a relay chain, and all the backdoor traffic goes through one tunnel with one of the machines. This complicates the detection and localization of infection. Even if the admin detects a machine that maintains a connection to the C & C server, it will not be so difficult to identify other compromised nodes.
Chain TCP tunnel
Known file names: winhlp.exe, msdtc.exe
Date of discovery: 2016.08.12 01: 11.31
Discovery path: C: \ Windows \ winhlp.exe
File size: 20480 bytes
Last start time: 2016.08.12 21:59
Runs from: svchost.exe (standard Windows signed binary)
Type: PE32 (DLL) (GUI) 80386, MS Windows
Compilation Date: 2014.09.17 16:59:33 (GMT)
Linker Version: 6.0
Where caught: incident # 1 (attack on a bank in Southeast Asia)
This thing works as a TCP relay that encrypts communications with the command server. Can be configured remotely. It is started with at least two parameters: IP and port of host A. There are two optional parameters: IP and port of host B (for outgoing connections). These parameters can also be transferred from the management server.
The process of connecting to the command server begins with generating the key of the handshake using a simple algorithm:
The key is obtained if you are interested: 2c 2d 2e 2f 28 29 2a 2b 24 25 26 27 20 21 22.
After that, the message body is created - a string from 64 to 192 bytes in length. The fifth DWORD is replaced with the special code 0x00000065 (“e”). The message is encrypted with the handshake key and sent to the command server.
The packet structure is as follows (blue lines are data encrypted by RC4 with the handshake key):
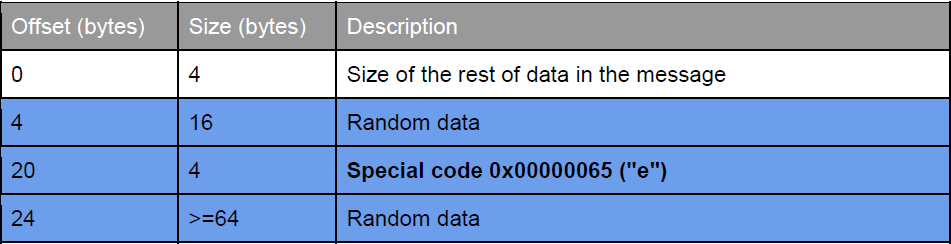
The server responds with a similar package, in which the first DWORD is the size, in the rest of the package there is only one meaningful value, at offset 0x14. If the handshake is unsuccessful, there should be 0x00000066 (“f”). If the handshake is successful, the tunnel creates a stream of TCP connections to the command server, encrypted on RC4 with a hard-coded 4-byte key.
The analyzed sample uses a binary protocol for communication, exchanging encrypted 40-byte blocks with the server. In each DWORD block at offset 0x4 sets the command.
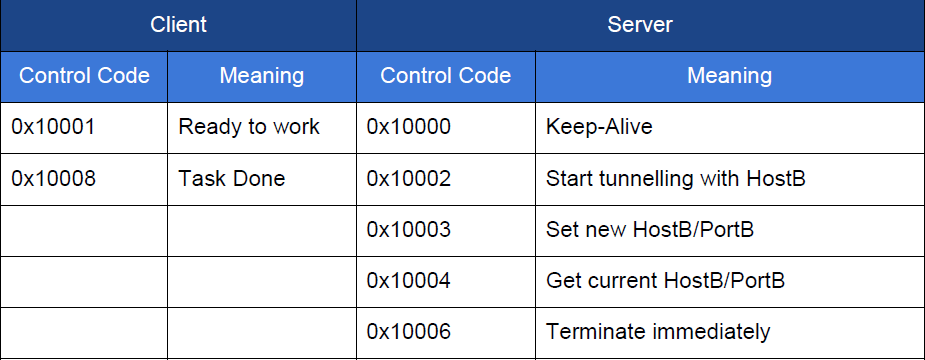
In the case of the 0x10003 command, the block also specifies the IP and port by the offsets 0x10 and 0x14, respectively. In other cases, the remaining block space is filled with random values. Connection to host B is initialized by the command 0x10002. This opens a TCP session with host A, a handshake is executed, and then the data is transmitted from A to B and back without changes.
Different versions of this tool were found in Costa Rica and Ethiopia, and another option was loaded into the multi-scanner from Bangladesh.
Date of discovery: 2016.08.12 01: 11.31
Discovery path: C: \ Windows \ winhlp.exe
File size: 20480 bytes
Last start time: 2016.08.12 21:59
Runs from: svchost.exe (standard Windows signed binary)
Type: PE32 (DLL) (GUI) 80386, MS Windows
Compilation Date: 2014.09.17 16:59:33 (GMT)
Linker Version: 6.0
Where caught: incident # 1 (attack on a bank in Southeast Asia)
This thing works as a TCP relay that encrypts communications with the command server. Can be configured remotely. It is started with at least two parameters: IP and port of host A. There are two optional parameters: IP and port of host B (for outgoing connections). These parameters can also be transferred from the management server.
The process of connecting to the command server begins with generating the key of the handshake using a simple algorithm:
i = 0; do { key[i] = 0xDB * i ^ 0xF7; ++i; } while ( i < 16 ); The key is obtained if you are interested: 2c 2d 2e 2f 28 29 2a 2b 24 25 26 27 20 21 22.
After that, the message body is created - a string from 64 to 192 bytes in length. The fifth DWORD is replaced with the special code 0x00000065 (“e”). The message is encrypted with the handshake key and sent to the command server.
The packet structure is as follows (blue lines are data encrypted by RC4 with the handshake key):

The server responds with a similar package, in which the first DWORD is the size, in the rest of the package there is only one meaningful value, at offset 0x14. If the handshake is unsuccessful, there should be 0x00000066 (“f”). If the handshake is successful, the tunnel creates a stream of TCP connections to the command server, encrypted on RC4 with a hard-coded 4-byte key.
The analyzed sample uses a binary protocol for communication, exchanging encrypted 40-byte blocks with the server. In each DWORD block at offset 0x4 sets the command.

In the case of the 0x10003 command, the block also specifies the IP and port by the offsets 0x10 and 0x14, respectively. In other cases, the remaining block space is filled with random values. Connection to host B is initialized by the command 0x10002. This opens a TCP session with host A, a handshake is executed, and then the data is transmitted from A to B and back without changes.
Different versions of this tool were found in Costa Rica and Ethiopia, and another option was loaded into the multi-scanner from Bangladesh.
Lazarus use several new interesting techniques. We believe that the attackers are aware of what problems in the investigation of cyber attacks are caused by the division of responsibility between SWIFT and the bank. And they began to divide their equipment in such a way that one part was stored in systems connected to SWIFT, and the other on its own bank systems. So they try to make it difficult to detect traces of the attack from both the bank and SWIFT - and this is where a third party, for example, Kaspersky Lab, has an advantage. We can see the big picture.
Technically, this is done by separating the files that need to be collected back to get a functioning malware process. We have already observed this twice and firmly believe that this is not a coincidence.
When investigating a security incident, it is common to analyze the system as a whole, examining the memory dump and disk image. Few people would think that the system could be half infected, and that the second ingredient of the attack lives somewhere else. The analyst can easily not see the forest because of the trees, shutting himself to the analysis of the closed system. Actually because we believe that this technique is used in order to complicate the investigation.
Even if you managed to get all the components of all stages of the attack, it will be difficult to reproduce the attack. The point is in the ingenious chain launching scheme - each component requires a password to decrypt the code that the previous component must pass in the launch parameters. And without the first password, which is known only to the very first component, the installer, the researchers will not be able to observe the behavior of the malware, and it will be almost impossible to disassemble the code.
By the way, all the activities of Lazarus are in the outside hours of the time zone of the victim, and carefully clean up the logs.
Lazarus does not burn at all
Investigations of many shares of the group pointed to North Korea, but the signs were completely indirect. Basically, the conclusions were based on a possible motive. For example, the attack on Sony Entertainment was carried out shortly before the premiere of "Interview", a comedy in the finals of which North Korean leader Kim Jong-un is murdered. As a result, the prime minister had to be postponed (but not canceled). Similarly, the attacks on the South Korean sites - no one could think of who would need it, except for the "northern neighbor." But in the case of bank robberies, this logic does not apply - everyone needs money.
Lazarus painstakingly wipes out traces and leaves false flags to prevent accurate attribution. Often try to translate the arrows on the famous Rashn hackers. In particular, Russian words were found in the exploit code taken to attack Polish banks in January 2017. And what! Xoroshspat, vyzov_chainika, podgotovkaskotiny. I don't know who else, but I just call tags when I write code. The backdoor also showed words like kliyent2podklyuchit, ustanavlivat, poluchit, nachalo. It all sounds very strange, as if a foreigner was choosing words from a phrase book.
 Summed up our heroes and another small negligence. The researchers managed to capture the European management and control server that the group used. The analysis showed that the hackers installed Apache Tomcat, configured it, downloaded a JSP script for remote control of malware and started testing. And after testing, they decided to make some extra money, - and the truth is, why idle processor resources, - and put a miner on the Monero cryptocurrency server. Miner was crooked, and hung the server completely. That one became unavailable, and the hackers could not clear all the tracks, in particular, the Apache log.
Summed up our heroes and another small negligence. The researchers managed to capture the European management and control server that the group used. The analysis showed that the hackers installed Apache Tomcat, configured it, downloaded a JSP script for remote control of malware and started testing. And after testing, they decided to make some extra money, - and the truth is, why idle processor resources, - and put a miner on the Monero cryptocurrency server. Miner was crooked, and hung the server completely. That one became unavailable, and the hackers could not clear all the tracks, in particular, the Apache log.And in the log there was an interesting one. The operator connected to the server test settings backdoor, carefully using a proxy and VPN. Therefore, IP addresses from France and South Korea appear in the log, but there is also a short-term connection from the very unusual range of 175.45.176.0 - 175.45.179.255, which belongs to the North Korean provider Star JV. Perhaps the operator by mistake came from his IP, although this, of course, cannot be called proof: since there are computers from the DPRK on the Internet, they can also be hacked and used to sweep away traces.
In conclusion, we say that the process of extracting the pulp from the banks at Bluenoroff is not very fast: in most cases, they graze inside the network for a long time, slowly studying it, collecting administrative credentials and testing different methods on SWIFT servers. For example, the attack on the Asian bank, from where we received part of the samples, lasted more than nine months. And this can be called an excellent proof of the postulate "even if you were hacked, the damage can still be prevented." The victims had enough time for this, only they did not have enough internal expertise to understand that they were being robbed - slowly but surely.
Source: https://habr.com/ru/post/326366/
All Articles