How software-defined Cisco TrustSec-based network segmentation can help a business
The article discusses network segmentation - an important tool for ensuring information security (IS), which makes it possible to significantly reduce the likelihood of security incidents and the associated damage even if intruders penetrate the perimeter of a corporate network.
The traditional approach to segmentation and its limitations are analyzed. A new approach to segmentation based on Cisco TrustSec technology is being considered, eliminating these limitations.
A number of typical IT and IS tasks related to segmentation are considered, and a comparison is made of the solutions of these tasks proposed by the traditional and new approaches.
The new features and business benefits offered by Cisco TrustSec are analyzed in detail.
')
The corporate network has become a crucial business tool for many companies, since it is this that provides the work of many business processes related to the transfer of information. At the same time, information security threats are constantly evolving, and the need for effective remedies is growing every day.
For a long time, the attention of information security specialists was mainly focused on the perimeter protection of the network. But in modern networks, the classic concept of perimeter is gradually blurring. Users connect to the network in a variety of ways, including access via wired and wireless segments, as well as VPN connections. At the same time, within the organization's IT infrastructure, as a rule, there are many types of users and devices that need access to various network resources to perform their work. Implementing proper access control in modern distributed and dynamic IT infrastructures is not an easy task. Given the large number of attack vectors that allow attackers and malicious software to penetrate the corporate IT infrastructure, the likelihood of breach of information security can be considered extremely high, as a rule, it is a matter of time.
One of the popular measures aimed at reducing damage from the intruder's penetration into the corporate IT infrastructure is network segmentation. The implied preliminary stage of segmentation is the separation of users and network resources into groups isolated from each other (closed groups of users and resources). Data exchange between these groups is controlled or blocked altogether depending on the requirements of the organization’s security policy.
The principles used to divide users into groups are determined by the organization’s security policy. As one of the typical options for separating users and devices into categories, the following can be given: employees, temporary staff, guests, users with devices that do not comply with corporate policy (quarantine), engineering subsystems of buildings, and so on. In addition, employees may not be placed in one group, but divided into several groups, for example, ordinary employees, management, top management, accounting, etc.
Network segmentation helps
information security by limiting the ability of attackers to damage if they penetrate inside the protected perimeter.
Dividing users into groups and network segmentation is not an end in itself, but can be very important for improving the security of business processes. In this sense, such business processes rely on segmentation. An organization's security policy may require that employees of different categories have access only to those corporate resources to which they need access to do their work. For example, access to a server group of an ERP system with confidential business information can only be provided to management, and access to confidential HR databases to employees of the HR department and, possibly, management. At the same time, low-level personnel or temporary employees can access only a limited set of corporate applications, such as the corporate CRM system and e-mail, and do not have access rights to all other network resources.
The impact of segmentation on business processes in the cases described is that segmentation is important for ensuring information security, and since IS incidents can lead to a violation of accessibility, segmentation also contributes to the increase in the availability of business processes.
In addition, there is a whole group of business processes, the implementation of which in the absence of segmentation is highly undesirable. For example, this group includes processes related to access to the corporate network of users who are not employees of the organization. A typical example is the provision of access to the network (or the Internet) by the so-called guest users. Other options include the access of employees of the partner company, the access of auditors, the connection to the network of devices belonging to other organizations, such as ATMs, digital signage, payment terminals. Another scenario in which the use of segmentation is recommended is the separation of access between employees of affiliated structures using the same network.
There may be many such scenarios, but they all lead to the task of implementing
segmentation in practice.
When implementing network segmentation, it is necessary to solve 3 key tasks:
Task 1 is usually solved using authentication and authorization using the 802.1x protocol on a RADIUS server (often using data from a corporate directory service, such as Active Directory). It is possible to use other methods - static placement of users depending on the connection port, VLAN, IP subnet, authorization by MAC address, and so on, depending on the capabilities of the AAA server and equipment used.
Task 2 is traditionally solved by creating separate virtual topologies for each user group. As a rule, this is done using some kind of network virtualization. In the case of small networks, these tools are usually VLANs and 802.1Q trunks. Tier 3 technologies such as Multi-VRF CE (VRF-Lite) are also often used. For large networks, MPLS VPN is typical.
Task 3 is usually solved by packet filtering based on IP addresses. Access control can be implemented using such “coarse” tools as access control lists (ACLs) on network infrastructure elements, or “fine” filtering on new generation protection systems (NGFW, NGIPS), but the fundamental principle remains the same - the basic criterion to decide on admission / non-admission is the IP address. Filtering is carried out in one or several places designed to exchange traffic between user groups.
Sometimes packet filtering is used without creating virtual topologies, i.e. packet filters simultaneously serve to solve both task 2 and task 3.
Traditional methods for solving problems (2) and (3) can lead to a significant amount of manual work, especially during network operation.
This circumstance becomes all the more tangible, the more the dynamics in the segmentation environment, for example:
Segmentation support becomes more complicated than having to deal with a large number of closed user groups.
The situation is aggravated by the fact that access control rules rely on IP addresses. With such rules it is difficult to work and easy to make mistakes. In addition, the use of IP addresses as a basic criterion for access control significantly limits the ability to make changes to the addressing scheme, and in some cases makes the changes almost impossible. In addition, the IP address cannot identify the user / device / state and is easy to replace.
Often, there are so many access control lists, and there are so many lines in the lists themselves (Access Control Entries, ACE) that administrators find it difficult to remember exactly what a particular line is needed for and they are afraid to change or delete these lines. Over time, lists grow and their maintenance becomes even more difficult. This is because the number of ACE lines is determined by the product ACE = S ∗ D ∗ P, where S is the number of source addresses, D is the number of destinations, and P is the number of access permissions. For example, even in the case of a relatively small network, in which access rules concern 4 VLANs, of which 30 subnets are allowed to 4 applications (which requires at least 4 permit entries in the ACL), administrators deal with at least 4 ∗ 30 ∗ 4 = 480 lines. What can we say about large networks with many subnets and applications!
The high complexity of working with access control lists sometimes leads to the fact that some organizations do not use segmentation at all or abandon it in the process of network growth. But even those who use segmentation often have to spend a lot of time and effort on coordination between IT, IS, business departments, exchange of applications, etc.
As a result, a significant burden is placed on the personnel of IT and IS services, which takes up working time in routine, but responsible and demanding operations. Typical consequences:
TrustSec is a segmentation technology developed by Cisco and allowing to overcome the difficulties discussed above through automation.
As in the case of traditional methods, Cisco TrustSec involves solving the problem of placing a user into the right group (task 1, in the TrustSec terminology - Classification, classification) by authenticating and authorizing the user via 802.1x using the access control server, which is Cisco Identity Services Engine ( Cisco ISE ). The Cisco ISE server can perform authentication and authorization using both the internal user database and external directories, such as Active Directory. TrustSec does not require the use of any specific types of user credentials (user credentials) - options are possible, for example, MSCHAPv2, Generic Token Card (GTC), one-time RSA password, and so on. Alternative methods are also possible, such as MAC Authentication Bypass, Web Authentication, AD-based Passive Identity (Easy Connect), etc. In addition, static methods are available - based on VLANs, IP addresses, interfaces, etc.
But further approaches are fundamentally different. Cisco TrustSec provides for assigning to the traffic of each closed user group a corresponding 16-bit security tag (SGT) when connecting to the network, more precisely, when entering the TrustSec domain. This is usually done on an access switch or other device at the edge of the corporate network.
The richness of the ability to classify and assign tags to groups of users and connections of all types — wired, wireless, VPN, server connections in the data center, and other organizations — allows you to create a single, comprehensive access policy for all types of devices and connections based on TrustSec (see Figure 1) .

Fig. 1. Cisco TrustSec allows you to create a unified, comprehensive access policy for
all types of devices and connections
SGT tag assigned
Cisco ISE server or a static element of the network infrastructure, and then TrustSec works with labels.
This is the fundamental difference between the solution of the problem of isolating traffic (task 2, in the terminology of TrustSec - Propagation, distribution). In the traditional approach, this requires the creation of a virtual topology for each group. In TrustSec, this is not necessary, as TrustSec provides for assigning SGT tags to the traffic of each group. This eliminates the need to create virtual topologies and greatly simplifies the network: all closed user groups can operate on the basis of a single network topology.
Further, TrustSec offers a fundamentally different, simpler and more effective solution to the problem of access control (tasks 3, in the terminology of TrustSec - Enforcement, application of policies). The traditional approach involves the use of IP-based access control lists (ACLs). TrustSec works with access control lists based not on IP addresses, but on SGT tags. These lists are called Cisco TrustSec Security Group ACL (SGACL). Using SGACL can significantly simplify work: instead of numerous and difficult to maintain ACLs based on IP addresses, administrators deal with SGACLs based on group labels and not dependent on addresses or on the presence of virtual topologies.
This concept is implemented in the Cisco ISE Server TrustSec Policy Matrix. Instead of a multitude of disparate access control lists, the administrator works with a centralized matrix (see Figure 2). The matrix rows are the traffic source groups (sources), the columns are destination groups (destinations). Access policies are defined in intersection cells in the form of an SGACL. Both simplest rules (permit / deny) for any traffic are possible, as well as more complex SGACLs with details of allowed and denied traffic in the same way as in an ACL, only the sources and destinations are determined by SGT tags, not by IP addresses.
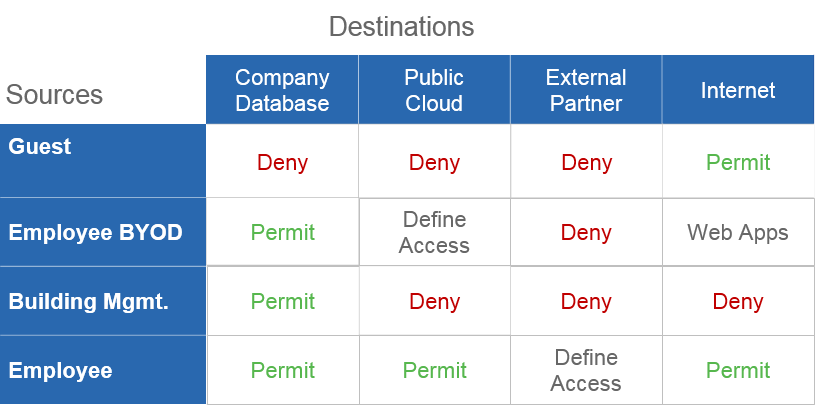
Fig. 2. Illustration of the Cisco TrustSec Policy Management Matrix Access Concept
It is not necessary to fill all cells of the matrix - unfilled cells follow the Default Policy, which can deny or allow all traffic by default. The filled cells follow the SGACL rules followed by the Default Policy.
The concept of the access matrix and the dynamic assignment of labels allow you to implement
access policy centrally, conveniently, consistently. TrustSec distributes this
network policy by dynamically transmitting SGT tags and SGACL rules.
SGT tags can be distributed over the network in three ways - from
as part of frame headers or packets of transmitted traffic (this is an inline method) using the SGT Exchange Protocol (SXP) running over TCP or using Cisco Platform Exchange Grid Technology ( pxGrid ).
The first method provides very high scalability and convenience, because the tags are transmitted along with the traffic, but the device must be able to work with tags embedded in frames or packets. This is not always available, especially in the case of working with labels in the Ethernet frames that require hardware implementation in integrated circuits (ASIC). In addition, the implementation of TrustSec may not have all the devices on the network, and then the task may arise of combining the “isolated areas” of TrustSec among themselves. In such cases, you can use the second method - the transfer of tags via the SXP protocol. The third way - based on pxGrid - provides integration with other information security solutions of Cisco and its partners.
Currently, Cisco has implemented TrustSec technology already in dozens of product lines , including switches for corporate and industrial networks, data centers, firewalls, routers, WLAN controllers, etc. In addition, although TrustSec is a proprietary development of Cisco, in 2014, Cisco published the IETF information draft describing the Source-group tag eXchange Protocol (SXP) to open the functionality of TrustSec and other vendors.
As for the SGACL rules propagation, network infrastructure elements automatically download them from the Cisco ISE server. When an administrator makes changes to TrustSec policies, he can immediately distribute them across the network using a push command on the Cisco ISE interface. In addition, it is possible to update the TrustSec policy locally on the device using the command in the CLI. Devices also periodically update policies as their expiry timeout expires.

Fig. 3. An example of the application of the policy TrustSec
Consider the use of TrustSec policy by example (see Figure 3). User Alice connected to the network, authenticated and authorized on the Cisco ISE server, and was assigned to group 5 (Marketing) based on the results of the authorization. The access switch assigns SGT 5 to packets coming into the network from its computer. Suppose for simplicity that all switches shown in the figure are covered by the TrustSec domain and TrustSec policies are applied on the Nexus_SGACL switch interfaces to which the Nexus1 and Nexus2 switches are connected (although be used on other routed and switched interfaces of the TrustSec domain). An administrator configured Cisco ISE and distributed the access policy in the TrustSec domain shown in the table in Figure 2. 3
Suppose that Alice’s computer sent an IP packet to an HR group server belonging to an HR group. The packet is transmitted through the network and arrives at the Nexus_SGACL switch, which applies the policy already downloaded from the Cisco ISE server. As we remember, the access matrix should be read by the mnemonic "left-to-right-bottom-up", therefore, the policy presented in the example provides Deny for all traffic of the Marketing group (tag 5) directed to the recipients of the HR group (tag 20). Since the HR server with the address 10.1.100.52 belongs to the HR group, the switch removes the Alice package, thus fulfilling the segmentation policy requirement.
Switches use SGACL hardware at the speed of the communication channel, so tag-based filtering does not affect switching performance.
You can learn more about the details of setting up TrustSec policies on the Cisco ISE server in the technical documentation . Also in the documentation, you can find detailed information on configuring TrustSec on network infrastructure elements, such as Catalyst switches . On the Cisco website are available and Design Guides on the topic of TrustSec.
Thus, Cisco TrustSec offers dynamic distribution of access control policies across the entire network, including the ability to cover all types of network access — wired, wireless, VPN — within a single, centralized policy.
Cisco TrustSec covers not only the network infrastructure and the Cisco ISE server. Through the pxGrid interface , TrustSec integrates with other Cisco solutions (and its partners), such as Cisco Firepower , Cisco Web Security Appliance (WSA), Cisco Stealthwatch , etc. In particular, this integration allows creating very thin and granular access and application policies based on SGT tags using the arsenal of the next-generation Cisco Firepower firewall functions. Another example is the use of different privileges to access web resources using the SGT tags using Cisco WSA. The third example is the development of Stealthwatch policies to combat directed threats, taking into account the user's identity to a particular SGT group. The fourth example is a special case of the capabilities of the Cisco Rapid Threat Containment solution. In this example, Cisco Stealthwatch or Cisco Advanced Malware Protection detects an information security threat (for example, an infected computer) and sends a request to Cisco ISE to restrict access to this computer using the TrustSec toolkit (dynamic quarantine group).
In addition, TrustSec, being essentially a software-defined segmentation technology, integrates with the software-defined data center architecture of the Cisco Application Centric Infrastructure (ACI). Integration establishes a mutual correspondence between closed user groups, segmented using SGT tags, and applications with their components, segmented into ACI Endpoint Groups (EPG) groups. As a result, it is possible to create end-to-end software-defined security policies covering both the network and the data center.
Both technologies - TrustSec and ACI - are aimed at streamlining and automating processes in the areas of security and data center. In this sense, technologies complement each other and, when used together, offer additional synergistic benefits.
Consider a number of typical tasks of IT and IS departments and compare the expected results from solving these tasks in network scenarios in which segmentation is implemented based on traditional methods (let's call it AS-IS network) and a network with segmentation based on Cisco TrustSec technology (network TO- BE).
For definiteness, suppose that in both scenarios users are placed in the correct group (task 1) as a result of 802.1x authentication and authorization on the RADIUS server using the Active Directory directory service. Thus, the solution to this problem in both scenarios is not fundamentally different.
But user traffic isolation (task 2) is implemented in the AS-IS network by creating virtual topologies or applying ACLs, and in the TO-BE network - by assigning SGT tags to the frames.
Access control (task 3) in the AS-IS network scenario is implemented using ACLs, and in the TO-BE network scenario using the Security Group ACL (SGACL), which is dynamically distributed over the network from the Cisco ISE server.
We presume that the network equipment in the AS-IS scenario supports the necessary virtualization technologies, and in the TO-BE scenario, TrustSec functionality.
Consider these typical tasks.
5.1. Routine create / modify / delete operations
Tasks of this type include operations related to controlling access of existing users to network resources.
In the case of an initial network (AS-IS), the problem is solved by manually editing access control lists (ACLs) configured on one or many elements of the network infrastructure. Especially many revisions may be required when ACLs are used both to isolate traffic (instead of virtual topologies) and to control access.
To cope with a large number of ACLs as part of the traditional approach, you can try to centralize their application to traffic. This will require, first, to implement virtual topologies to isolate the traffic of closed user groups (solution of task 2), and second, to implement traffic exchange between these topologies and use ACL (solution of task 3) in the minimum acceptable number of network points.
Such a centralized traffic exchange can help reduce the number of ACLs, but does not completely eliminate the problems of the traditional approach. In addition, it contributes to the emergence of additional “bottlenecks” in the network, as well as reducing the optimality of traffic routes between groups. Suboptimal traffic paths between groups may appear because traffic must go through an exchange point, which may not be the shortest way. The difference between the shortest and actual paths in some English literature is called
In general, policing typically increases network stretch.
In a network with TrustSec (TO-BE), the solution of the problem is automated. Resource access control is implemented by configuring the TrustSec Policy Management Matrix centralized on the Cisco ISE access control server. Access policies are dynamically distributed across network infrastructure elements and implemented in the SGACL.
It also eliminates the need to set certain ACLs on the respective interfaces, as was the case with the AS-IS network. Instead, TrustSec policing is activated on the interfaces, but the SGACL device rules themselves are dynamically received. Therefore, it is no longer necessary to centralize the exchange of traffic between groups, it can be made distributed. As a result, it becomes possible to reduce the network stretch, optimize the ways of exchanging traffic between groups, and reduce the number of bottlenecks.
Thus, TrustSec offers:
5.2. Creating / changing / deleting resources and closed groups
Tasks of this type can be associated with creating or deleting closed user groups, starting or deleting network resources that rely on segmentation in their work, or changing the geographical coverage of user groups. Such tasks may arise, including within the framework of the “agile office” concept.
In the AS-IS network scenario, closed user groups are implemented by creating virtual topologies using tools such as VLAN, VRF, MPLS VPN, tunnels, etc. An alternative is to use ACL for both segmentation and access control.
Adding new groups or deleting old ones requires a considerable amount of time and manual labor, and is often associated with errors in customization and downtime of business processes due to the “human factor”.
In a network scenario with TrustSec (TO-BE), adding or deleting a closed user group is accomplished by creating or deleting a group label (SGT) on the Cisco ISE server and assigning users to the right groups. In this case, changes in network configuration, as a rule, are not required.
As a result, TrustSec provides:
The scenario assumes a change in the geographical coverage of closed user groups. For example, including a group of users from another building, an office in another city, physical movements of user groups when moving or changes in the composition of departments, within the framework of the concept of “agile office”, etc.
In an AS-IS network scenario, it is not enough to perform a set of segmentation tasks once — to integrate VLANs and VRFs into virtual topologies, apply ACLs (perhaps on multiple network interfaces), etc. Such work should be carried out in the future, with changes in segmentation policy.
Therefore, if you initially implement segmentation for all groups throughout the network, you will have to pay for this even more labor intensive operation. It would seem that it is possible to reduce the severity of the problem if you implement segmentation in the network only partially, laying virtual topologies only in those parts of the network and for those groups that are needed there at the moment. But when the requirements for the geography of groups change, it will have to be paid with additional time and labor costs for introducing segmentation in the desired area of the network - laborious configuration changes and associated configuration errors and business process downtime.
TrustSec in network scenarios (TO-BE) makes it possible for administrators to reduce their expenses to almost zero. TrustSec is deployed to the network once, even at this stage, requiring much less effort than creating virtual topologies and / or multiple ACLs on the elements of the network infrastructure. And TrustSec does not require hardware reconfiguration with policy changes. Therefore, considerations of labor-intensive operation do not interfere with the implementation of TrustSec across the entire network initially, when it is created or upgraded.
But still, if, when changing the geography of user groups, it turns out that for some reason, TrustSec was not initially implemented in the right part of the network, this can be done faster than in the AS-IS scenario by using a set of commands that is common to all user groups and not depending on their quantity.
If TrustSec is already implemented in the right part of the network, then administrators do not need to take any action at all to reconfigure the equipment, because TrustSec policies are dynamically distributed throughout the network.
TrustSec allows you to implement user segmentation and access control with much faster speed and granularity than basic AS-IS network facilities.
The effect of the introduction of TrustSec is greater, the greater the dynamics in the configuration of closed groups of users of the company, because TrustSec automates these changes instead of time-consuming manual work.
Also, the effect of TrustSec is greater, the more demanded is the granularity of user segmentation into groups. In the case of traditional segmentation based on virtual topologies, the more user groups there are, the more topologies and the greater the complexity. As a result, the number of topologies (and user groups) may not be optimal from a security point of view, but less so as to achieve a compromise between security and complexity. In turn, such a compromise is already not for the benefit of security. Thanks to automation, TrustSec eliminates this limitation and allows you to divide users into exactly the number of groups that would be optimal from the point of view of security.
TrustSec allows you to create a uniform, comprehensive access policy for all types of devices and connections, thereby helping to ensure a high level of security. Very serious additional possibilities are opened by the integration of TrustSec with other information security solutions thanks to the pxGrid technology.
In addition, TrustSec provides an increased level of security due to the strict mutual authentication of network infrastructure elements and the ability to encrypt traffic on the data link layer.
Thanks to the described advantages, Cisco TrustSec can significantly reduce the likelihood and damage associated with information security incidents.
Due to the benefits described in Section 5.3, TrustSec also offers significant gains in addressing and investigating security incidents.
Since TrustSec allows users to be segmented into closed groups much more granular than traditional methods, in the event of an information security incident (for example, if an intruder penetrates or an infection gets into the network), the expected damage will be much less than in the AS-IS network.
In addition, for this reason, TrustSec will save staff time to deal with the consequences of the incident.
Another advantage - TrustSec will eliminate the consequences of the incident, while maintaining user access to the network due to their transfer to a separate isolated group. This is especially important when it comes to VIP users. For example, it is possible to eliminate the consequences of infecting computers of top management, while retaining their access to the network, and with minimal risks for uninfected computers.
Since TrustSec allows much more granular user segmentation to be implemented than in the case of the AS-IS network, investigating incidents will require analyzing fewer devices. As a result, you can significantly speed up and facilitate the investigation of information security incidents.
For modern business is characterized by increasing dynamics. The network, as well as the policies implemented in it, must quickly adjust to changing business requirements. Changes in security policy, requiring days or weeks for their implementation, are less and less satisfied with business.
Critical and proper operation of business processes that rely on the network and are dependent on segmentation. Any changes to the segmentation policy must be implemented not only quickly but also reliably.
Therefore, the traditional means of segmentation, discussed in the article, no longer meet the needs of businesses today and tomorrow. You can support these queries with the help of modern network segmentation technology - Cisco TrustSec.
TrustSec meets modern business requirements and offers tools that implement segmentation environment changes quickly and reliably by automating and minimizing the “human factor”.
As a result, Cisco TrustSec offers business
in at least three areas:
The traditional approach to segmentation and its limitations are analyzed. A new approach to segmentation based on Cisco TrustSec technology is being considered, eliminating these limitations.
A number of typical IT and IS tasks related to segmentation are considered, and a comparison is made of the solutions of these tasks proposed by the traditional and new approaches.
The new features and business benefits offered by Cisco TrustSec are analyzed in detail.
')
1. Why is network segmentation needed?
The corporate network has become a crucial business tool for many companies, since it is this that provides the work of many business processes related to the transfer of information. At the same time, information security threats are constantly evolving, and the need for effective remedies is growing every day.
For a long time, the attention of information security specialists was mainly focused on the perimeter protection of the network. But in modern networks, the classic concept of perimeter is gradually blurring. Users connect to the network in a variety of ways, including access via wired and wireless segments, as well as VPN connections. At the same time, within the organization's IT infrastructure, as a rule, there are many types of users and devices that need access to various network resources to perform their work. Implementing proper access control in modern distributed and dynamic IT infrastructures is not an easy task. Given the large number of attack vectors that allow attackers and malicious software to penetrate the corporate IT infrastructure, the likelihood of breach of information security can be considered extremely high, as a rule, it is a matter of time.
One of the popular measures aimed at reducing damage from the intruder's penetration into the corporate IT infrastructure is network segmentation. The implied preliminary stage of segmentation is the separation of users and network resources into groups isolated from each other (closed groups of users and resources). Data exchange between these groups is controlled or blocked altogether depending on the requirements of the organization’s security policy.
The principles used to divide users into groups are determined by the organization’s security policy. As one of the typical options for separating users and devices into categories, the following can be given: employees, temporary staff, guests, users with devices that do not comply with corporate policy (quarantine), engineering subsystems of buildings, and so on. In addition, employees may not be placed in one group, but divided into several groups, for example, ordinary employees, management, top management, accounting, etc.
Network segmentation helps
significantly reduce risks
Quotes:
- Digital Guardian: “Eataly's network distribution and other locations across the globe”.
- US-CERT: “Effective network segmentation ... reduce the extent to the network”.
- If you’re trying to get the best of your health, you’ll be able to do this.
information security by limiting the ability of attackers to damage if they penetrate inside the protected perimeter.
Dividing users into groups and network segmentation is not an end in itself, but can be very important for improving the security of business processes. In this sense, such business processes rely on segmentation. An organization's security policy may require that employees of different categories have access only to those corporate resources to which they need access to do their work. For example, access to a server group of an ERP system with confidential business information can only be provided to management, and access to confidential HR databases to employees of the HR department and, possibly, management. At the same time, low-level personnel or temporary employees can access only a limited set of corporate applications, such as the corporate CRM system and e-mail, and do not have access rights to all other network resources.
The impact of segmentation on business processes in the cases described is that segmentation is important for ensuring information security, and since IS incidents can lead to a violation of accessibility, segmentation also contributes to the increase in the availability of business processes.
In addition, there is a whole group of business processes, the implementation of which in the absence of segmentation is highly undesirable. For example, this group includes processes related to access to the corporate network of users who are not employees of the organization. A typical example is the provision of access to the network (or the Internet) by the so-called guest users. Other options include the access of employees of the partner company, the access of auditors, the connection to the network of devices belonging to other organizations, such as ATMs, digital signage, payment terminals. Another scenario in which the use of segmentation is recommended is the separation of access between employees of affiliated structures using the same network.
There may be many such scenarios, but they all lead to the task of implementing
segmentation in practice.
2. Traditional network segmentation methods
When implementing network segmentation, it is necessary to solve 3 key tasks:
- Determine the user's belonging to the desired group when it is connected to
network (task 1). - Isolate the traffic of the user of this group from the traffic of users of other
groups during transmission over the network (task 2). - Provide user access to the resources to which he should have access.
and, as a rule, block access to all other resources (task 3).
Task 1 is usually solved using authentication and authorization using the 802.1x protocol on a RADIUS server (often using data from a corporate directory service, such as Active Directory). It is possible to use other methods - static placement of users depending on the connection port, VLAN, IP subnet, authorization by MAC address, and so on, depending on the capabilities of the AAA server and equipment used.
Task 2 is traditionally solved by creating separate virtual topologies for each user group. As a rule, this is done using some kind of network virtualization. In the case of small networks, these tools are usually VLANs and 802.1Q trunks. Tier 3 technologies such as Multi-VRF CE (VRF-Lite) are also often used. For large networks, MPLS VPN is typical.
Task 3 is usually solved by packet filtering based on IP addresses. Access control can be implemented using such “coarse” tools as access control lists (ACLs) on network infrastructure elements, or “fine” filtering on new generation protection systems (NGFW, NGIPS), but the fundamental principle remains the same - the basic criterion to decide on admission / non-admission is the IP address. Filtering is carried out in one or several places designed to exchange traffic between user groups.
Sometimes packet filtering is used without creating virtual topologies, i.e. packet filters simultaneously serve to solve both task 2 and task 3.
3. Limitations of traditional segmentation methods
Traditional methods for solving problems (2) and (3) can lead to a significant amount of manual work, especially during network operation.
This circumstance becomes all the more tangible, the more the dynamics in the segmentation environment, for example:
- The network may change the rules of access control - both in connection with the updating of security service requirements, and with changes in the composition of resources and users.
- The network may change the composition of user groups - for example, due to reorganizations within the company, changes in the composition of network resources, etc.
- Changes in the geography of user groups are possible, which may require extending segmentation to new parts of the network.
Segmentation support becomes more complicated than having to deal with a large number of closed user groups.
The situation is aggravated by the fact that access control rules rely on IP addresses. With such rules it is difficult to work and easy to make mistakes. In addition, the use of IP addresses as a basic criterion for access control significantly limits the ability to make changes to the addressing scheme, and in some cases makes the changes almost impossible. In addition, the IP address cannot identify the user / device / state and is easy to replace.
Often, there are so many access control lists, and there are so many lines in the lists themselves (Access Control Entries, ACE) that administrators find it difficult to remember exactly what a particular line is needed for and they are afraid to change or delete these lines. Over time, lists grow and their maintenance becomes even more difficult. This is because the number of ACE lines is determined by the product ACE = S ∗ D ∗ P, where S is the number of source addresses, D is the number of destinations, and P is the number of access permissions. For example, even in the case of a relatively small network, in which access rules concern 4 VLANs, of which 30 subnets are allowed to 4 applications (which requires at least 4 permit entries in the ACL), administrators deal with at least 4 ∗ 30 ∗ 4 = 480 lines. What can we say about large networks with many subnets and applications!
The high complexity of working with access control lists sometimes leads to the fact that some organizations do not use segmentation at all or abandon it in the process of network growth. But even those who use segmentation often have to spend a lot of time and effort on coordination between IT, IS, business departments, exchange of applications, etc.
As a result, a significant burden is placed on the personnel of IT and IS services, which takes up working time in routine, but responsible and demanding operations. Typical consequences:
- The risks of information security are growing due to possible errors and “holes” resulting from manual editing of access control lists.
- Risks of business process failures due to errors resulting from changes in equipment configurations are growing.
- It takes a lot of time just to keep the segmentation up to date. There is no time to do important, but not urgent things, and often they are not done. Time, which could be used to solve strategic, creative tasks - for example, related to network development, planning, optimization of business process support, network optimization, etc., goes to the routine. As a rule, there is no time left even to keep the documentation up to date, which again increases the risks of information security and business process failures!
- Longer time-to-market: it takes more time to launch new applications or
achievement of business results related to segmentation to one degree or another
network.
4. What is Cisco TrustSec and what is the difference from the traditional approach to segmentation?
TrustSec is a segmentation technology developed by Cisco and allowing to overcome the difficulties discussed above through automation.
As in the case of traditional methods, Cisco TrustSec involves solving the problem of placing a user into the right group (task 1, in the TrustSec terminology - Classification, classification) by authenticating and authorizing the user via 802.1x using the access control server, which is Cisco Identity Services Engine ( Cisco ISE ). The Cisco ISE server can perform authentication and authorization using both the internal user database and external directories, such as Active Directory. TrustSec does not require the use of any specific types of user credentials (user credentials) - options are possible, for example, MSCHAPv2, Generic Token Card (GTC), one-time RSA password, and so on. Alternative methods are also possible, such as MAC Authentication Bypass, Web Authentication, AD-based Passive Identity (Easy Connect), etc. In addition, static methods are available - based on VLANs, IP addresses, interfaces, etc.
But further approaches are fundamentally different. Cisco TrustSec provides for assigning to the traffic of each closed user group a corresponding 16-bit security tag (SGT) when connecting to the network, more precisely, when entering the TrustSec domain. This is usually done on an access switch or other device at the edge of the corporate network.
The richness of the ability to classify and assign tags to groups of users and connections of all types — wired, wireless, VPN, server connections in the data center, and other organizations — allows you to create a single, comprehensive access policy for all types of devices and connections based on TrustSec (see Figure 1) .

Fig. 1. Cisco TrustSec allows you to create a unified, comprehensive access policy for
all types of devices and connections
SGT tag assigned
dynamically
Dynamic label assignment is the easiest and most effective way to achieve label consistency across the entire network.
Cisco ISE server or a static element of the network infrastructure, and then TrustSec works with labels.
This is the fundamental difference between the solution of the problem of isolating traffic (task 2, in the terminology of TrustSec - Propagation, distribution). In the traditional approach, this requires the creation of a virtual topology for each group. In TrustSec, this is not necessary, as TrustSec provides for assigning SGT tags to the traffic of each group. This eliminates the need to create virtual topologies and greatly simplifies the network: all closed user groups can operate on the basis of a single network topology.
Further, TrustSec offers a fundamentally different, simpler and more effective solution to the problem of access control (tasks 3, in the terminology of TrustSec - Enforcement, application of policies). The traditional approach involves the use of IP-based access control lists (ACLs). TrustSec works with access control lists based not on IP addresses, but on SGT tags. These lists are called Cisco TrustSec Security Group ACL (SGACL). Using SGACL can significantly simplify work: instead of numerous and difficult to maintain ACLs based on IP addresses, administrators deal with SGACLs based on group labels and not dependent on addresses or on the presence of virtual topologies.
This concept is implemented in the Cisco ISE Server TrustSec Policy Matrix. Instead of a multitude of disparate access control lists, the administrator works with a centralized matrix (see Figure 2). The matrix rows are the traffic source groups (sources), the columns are destination groups (destinations). Access policies are defined in intersection cells in the form of an SGACL. Both simplest rules (permit / deny) for any traffic are possible, as well as more complex SGACLs with details of allowed and denied traffic in the same way as in an ACL, only the sources and destinations are determined by SGT tags, not by IP addresses.

Fig. 2. Illustration of the Cisco TrustSec Policy Management Matrix Access Concept
It is not necessary to fill all cells of the matrix - unfilled cells follow the Default Policy, which can deny or allow all traffic by default. The filled cells follow the SGACL rules followed by the Default Policy.
The concept of the access matrix and the dynamic assignment of labels allow you to implement
access policy centrally, conveniently, consistently. TrustSec distributes this
network policy by dynamically transmitting SGT tags and SGACL rules.
SGT tags can be distributed over the network in three ways - from
node to node
In the Cisco Meta Data (CMD) field of frames or traffic packets. Ethernet technologies (including MACsec IEEE 802.1ae), IPSec VPN, DMVPN, GETVPN are supported.
as part of frame headers or packets of transmitted traffic (this is an inline method) using the SGT Exchange Protocol (SXP) running over TCP or using Cisco Platform Exchange Grid Technology ( pxGrid ).
The first method provides very high scalability and convenience, because the tags are transmitted along with the traffic, but the device must be able to work with tags embedded in frames or packets. This is not always available, especially in the case of working with labels in the Ethernet frames that require hardware implementation in integrated circuits (ASIC). In addition, the implementation of TrustSec may not have all the devices on the network, and then the task may arise of combining the “isolated areas” of TrustSec among themselves. In such cases, you can use the second method - the transfer of tags via the SXP protocol. The third way - based on pxGrid - provides integration with other information security solutions of Cisco and its partners.
Currently, Cisco has implemented TrustSec technology already in dozens of product lines , including switches for corporate and industrial networks, data centers, firewalls, routers, WLAN controllers, etc. In addition, although TrustSec is a proprietary development of Cisco, in 2014, Cisco published the IETF information draft describing the Source-group tag eXchange Protocol (SXP) to open the functionality of TrustSec and other vendors.
As for the SGACL rules propagation, network infrastructure elements automatically download them from the Cisco ISE server. When an administrator makes changes to TrustSec policies, he can immediately distribute them across the network using a push command on the Cisco ISE interface. In addition, it is possible to update the TrustSec policy locally on the device using the command in the CLI. Devices also periodically update policies as their expiry timeout expires.

Fig. 3. An example of the application of the policy TrustSec
Consider the use of TrustSec policy by example (see Figure 3). User Alice connected to the network, authenticated and authorized on the Cisco ISE server, and was assigned to group 5 (Marketing) based on the results of the authorization. The access switch assigns SGT 5 to packets coming into the network from its computer. Suppose for simplicity that all switches shown in the figure are covered by the TrustSec domain and TrustSec policies are applied on the Nexus_SGACL switch interfaces to which the Nexus1 and Nexus2 switches are connected (although be used on other routed and switched interfaces of the TrustSec domain). An administrator configured Cisco ISE and distributed the access policy in the TrustSec domain shown in the table in Figure 2. 3
Suppose that Alice’s computer sent an IP packet to an HR group server belonging to an HR group. The packet is transmitted through the network and arrives at the Nexus_SGACL switch, which applies the policy already downloaded from the Cisco ISE server. As we remember, the access matrix should be read by the mnemonic "left-to-right-bottom-up", therefore, the policy presented in the example provides Deny for all traffic of the Marketing group (tag 5) directed to the recipients of the HR group (tag 20). Since the HR server with the address 10.1.100.52 belongs to the HR group, the switch removes the Alice package, thus fulfilling the segmentation policy requirement.
Switches use SGACL hardware at the speed of the communication channel, so tag-based filtering does not affect switching performance.
You can learn more about the details of setting up TrustSec policies on the Cisco ISE server in the technical documentation . Also in the documentation, you can find detailed information on configuring TrustSec on network infrastructure elements, such as Catalyst switches . On the Cisco website are available and Design Guides on the topic of TrustSec.
Thus, Cisco TrustSec offers dynamic distribution of access control policies across the entire network, including the ability to cover all types of network access — wired, wireless, VPN — within a single, centralized policy.
Cisco TrustSec covers not only the network infrastructure and the Cisco ISE server. Through the pxGrid interface , TrustSec integrates with other Cisco solutions (and its partners), such as Cisco Firepower , Cisco Web Security Appliance (WSA), Cisco Stealthwatch , etc. In particular, this integration allows creating very thin and granular access and application policies based on SGT tags using the arsenal of the next-generation Cisco Firepower firewall functions. Another example is the use of different privileges to access web resources using the SGT tags using Cisco WSA. The third example is the development of Stealthwatch policies to combat directed threats, taking into account the user's identity to a particular SGT group. The fourth example is a special case of the capabilities of the Cisco Rapid Threat Containment solution. In this example, Cisco Stealthwatch or Cisco Advanced Malware Protection detects an information security threat (for example, an infected computer) and sends a request to Cisco ISE to restrict access to this computer using the TrustSec toolkit (dynamic quarantine group).
In addition, TrustSec, being essentially a software-defined segmentation technology, integrates with the software-defined data center architecture of the Cisco Application Centric Infrastructure (ACI). Integration establishes a mutual correspondence between closed user groups, segmented using SGT tags, and applications with their components, segmented into ACI Endpoint Groups (EPG) groups. As a result, it is possible to create end-to-end software-defined security policies covering both the network and the data center.
Both technologies - TrustSec and ACI - are aimed at streamlining and automating processes in the areas of security and data center. In this sense, technologies complement each other and, when used together, offer additional synergistic benefits.
5. How can Cisco TrustSec help a business?
Consider a number of typical tasks of IT and IS departments and compare the expected results from solving these tasks in network scenarios in which segmentation is implemented based on traditional methods (let's call it AS-IS network) and a network with segmentation based on Cisco TrustSec technology (network TO- BE).
For definiteness, suppose that in both scenarios users are placed in the correct group (task 1) as a result of 802.1x authentication and authorization on the RADIUS server using the Active Directory directory service. Thus, the solution to this problem in both scenarios is not fundamentally different.
But user traffic isolation (task 2) is implemented in the AS-IS network by creating virtual topologies or applying ACLs, and in the TO-BE network - by assigning SGT tags to the frames.
Access control (task 3) in the AS-IS network scenario is implemented using ACLs, and in the TO-BE network scenario using the Security Group ACL (SGACL), which is dynamically distributed over the network from the Cisco ISE server.
We presume that the network equipment in the AS-IS scenario supports the necessary virtualization technologies, and in the TO-BE scenario, TrustSec functionality.
Consider these typical tasks.
5.1. Routine create / modify / delete operations
access control lists (ACLs)
Tasks of this type include operations related to controlling access of existing users to network resources.
In the case of an initial network (AS-IS), the problem is solved by manually editing access control lists (ACLs) configured on one or many elements of the network infrastructure. Especially many revisions may be required when ACLs are used both to isolate traffic (instead of virtual topologies) and to control access.
To cope with a large number of ACLs as part of the traditional approach, you can try to centralize their application to traffic. This will require, first, to implement virtual topologies to isolate the traffic of closed user groups (solution of task 2), and second, to implement traffic exchange between these topologies and use ACL (solution of task 3) in the minimum acceptable number of network points.
Such a centralized traffic exchange can help reduce the number of ACLs, but does not completely eliminate the problems of the traditional approach. In addition, it contributes to the emergence of additional “bottlenecks” in the network, as well as reducing the optimality of traffic routes between groups. Suboptimal traffic paths between groups may appear because traffic must go through an exchange point, which may not be the shortest way. The difference between the shortest and actual paths in some English literature is called
network stretch.
White, Russ and Tantsura, Jeff. Navigating Network Complexity: Next-Generation Routing
with SDN, Service Virtualization, and Service Chaining. (Chapter 5. Design Complexity).
Indianapolis, IN: Addison-Wesley Professional, 2016. Print.
with SDN, Service Virtualization, and Service Chaining. (Chapter 5. Design Complexity).
Indianapolis, IN: Addison-Wesley Professional, 2016. Print.
In general, policing typically increases network stretch.
In a network with TrustSec (TO-BE), the solution of the problem is automated. Resource access control is implemented by configuring the TrustSec Policy Management Matrix centralized on the Cisco ISE access control server. Access policies are dynamically distributed across network infrastructure elements and implemented in the SGACL.
It also eliminates the need to set certain ACLs on the respective interfaces, as was the case with the AS-IS network. Instead, TrustSec policing is activated on the interfaces, but the SGACL device rules themselves are dynamically received. Therefore, it is no longer necessary to centralize the exchange of traffic between groups, it can be made distributed. As a result, it becomes possible to reduce the network stretch, optimize the ways of exchanging traffic between groups, and reduce the number of bottlenecks.
Thus, TrustSec offers:
- Significant reduction in labor costs and time to make changes.
- Significant reduction in the likelihood of unavailability of applications associated with them
failures of business processes and IS incidents arising due to errors in the configuration of the ACL and other manifestations of the "human factor". - Immediate entry into force of new access policies.
- Change static access control to dynamic.
- Automated network segmentation.
- Indirect optimization of ways to transfer traffic between groups of users.
5.2. Creating / changing / deleting resources and closed groups
users
Tasks of this type can be associated with creating or deleting closed user groups, starting or deleting network resources that rely on segmentation in their work, or changing the geographical coverage of user groups. Such tasks may arise, including within the framework of the “agile office” concept.
5.2.1. Create / delete closed user groups
In the AS-IS network scenario, closed user groups are implemented by creating virtual topologies using tools such as VLAN, VRF, MPLS VPN, tunnels, etc. An alternative is to use ACL for both segmentation and access control.
Adding new groups or deleting old ones requires a considerable amount of time and manual labor, and is often associated with errors in customization and downtime of business processes due to the “human factor”.
In a network scenario with TrustSec (TO-BE), adding or deleting a closed user group is accomplished by creating or deleting a group label (SGT) on the Cisco ISE server and assigning users to the right groups. In this case, changes in network configuration, as a rule, are not required.
As a result, TrustSec provides:
- Significant time gain for service personnel, which can be used not for routine, but for solving more creative, strategic tasks for which there is often not enough time (for example, planning network development, preparing and updating documentation, optimizing network equipment settings, etc.) .
- Significant acceleration of launching a new closed user group or a new one
business process based on network segmentation. - Prevention of errors that may occur when performing a large number of routine operations. It is much easier to check the access matrix (both in working order and in the course of a formal audit) than hundreds of ACEs distributed among dozens of ACLs.
5.2.2. Change in geographic coverage of user groups
The scenario assumes a change in the geographical coverage of closed user groups. For example, including a group of users from another building, an office in another city, physical movements of user groups when moving or changes in the composition of departments, within the framework of the concept of “agile office”, etc.
In an AS-IS network scenario, it is not enough to perform a set of segmentation tasks once — to integrate VLANs and VRFs into virtual topologies, apply ACLs (perhaps on multiple network interfaces), etc. Such work should be carried out in the future, with changes in segmentation policy.
Therefore, if you initially implement segmentation for all groups throughout the network, you will have to pay for this even more labor intensive operation. It would seem that it is possible to reduce the severity of the problem if you implement segmentation in the network only partially, laying virtual topologies only in those parts of the network and for those groups that are needed there at the moment. But when the requirements for the geography of groups change, it will have to be paid with additional time and labor costs for introducing segmentation in the desired area of the network - laborious configuration changes and associated configuration errors and business process downtime.
TrustSec in network scenarios (TO-BE) makes it possible for administrators to reduce their expenses to almost zero. TrustSec is deployed to the network once, even at this stage, requiring much less effort than creating virtual topologies and / or multiple ACLs on the elements of the network infrastructure. And TrustSec does not require hardware reconfiguration with policy changes. Therefore, considerations of labor-intensive operation do not interfere with the implementation of TrustSec across the entire network initially, when it is created or upgraded.
But still, if, when changing the geography of user groups, it turns out that for some reason, TrustSec was not initially implemented in the right part of the network, this can be done faster than in the AS-IS scenario by using a set of commands that is common to all user groups and not depending on their quantity.
If TrustSec is already implemented in the right part of the network, then administrators do not need to take any action at all to reconfigure the equipment, because TrustSec policies are dynamically distributed throughout the network.
5.3. Preventing Information Security Incidents
TrustSec allows you to implement user segmentation and access control with much faster speed and granularity than basic AS-IS network facilities.
The effect of the introduction of TrustSec is greater, the greater the dynamics in the configuration of closed groups of users of the company, because TrustSec automates these changes instead of time-consuming manual work.
Also, the effect of TrustSec is greater, the more demanded is the granularity of user segmentation into groups. In the case of traditional segmentation based on virtual topologies, the more user groups there are, the more topologies and the greater the complexity. As a result, the number of topologies (and user groups) may not be optimal from a security point of view, but less so as to achieve a compromise between security and complexity. In turn, such a compromise is already not for the benefit of security. Thanks to automation, TrustSec eliminates this limitation and allows you to divide users into exactly the number of groups that would be optimal from the point of view of security.
TrustSec allows you to create a uniform, comprehensive access policy for all types of devices and connections, thereby helping to ensure a high level of security. Very serious additional possibilities are opened by the integration of TrustSec with other information security solutions thanks to the pxGrid technology.
In addition, TrustSec provides an increased level of security due to the strict mutual authentication of network infrastructure elements and the ability to encrypt traffic on the data link layer.
Thanks to the described advantages, Cisco TrustSec can significantly reduce the likelihood and damage associated with information security incidents.
5.4. Correction / investigation of information security incidents
Due to the benefits described in Section 5.3, TrustSec also offers significant gains in addressing and investigating security incidents.
5.4.1. Limiting damage / spread of infection
Since TrustSec allows users to be segmented into closed groups much more granular than traditional methods, in the event of an information security incident (for example, if an intruder penetrates or an infection gets into the network), the expected damage will be much less than in the AS-IS network.
In addition, for this reason, TrustSec will save staff time to deal with the consequences of the incident.
Another advantage - TrustSec will eliminate the consequences of the incident, while maintaining user access to the network due to their transfer to a separate isolated group. This is especially important when it comes to VIP users. For example, it is possible to eliminate the consequences of infecting computers of top management, while retaining their access to the network, and with minimal risks for uninfected computers.
5.4.2. Accelerate the investigation of security incidents
Since TrustSec allows much more granular user segmentation to be implemented than in the case of the AS-IS network, investigating incidents will require analyzing fewer devices. As a result, you can significantly speed up and facilitate the investigation of information security incidents.
6. Conclusion
For modern business is characterized by increasing dynamics. The network, as well as the policies implemented in it, must quickly adjust to changing business requirements. Changes in security policy, requiring days or weeks for their implementation, are less and less satisfied with business.
Critical and proper operation of business processes that rely on the network and are dependent on segmentation. Any changes to the segmentation policy must be implemented not only quickly but also reliably.
Therefore, the traditional means of segmentation, discussed in the article, no longer meet the needs of businesses today and tomorrow. You can support these queries with the help of modern network segmentation technology - Cisco TrustSec.
TrustSec meets modern business requirements and offers tools that implement segmentation environment changes quickly and reliably by automating and minimizing the “human factor”.
As a result, Cisco TrustSec offers business
winnings
Forrester Consulting TrustSec, 2016 .
in at least three areas:
- Money.The monetary effect of the Expected Value by reducing the risks of information security and reducing the risks of business process downtime.
- Man hours. Profit of staff time expressed in man-hours due to reduction of routine work. There is an opportunity to focus on solving strategic, creative tasks that are often postponed or not performed at all.
- . / -, .
Source: https://habr.com/ru/post/326356/
All Articles