“How it works”: introduction to SSL / TLS
We often talk about different technologies: from storage systems to backup . In addition, we share our own experience in optimizing the work of our IaaS provider - we are talking about managerial aspects and opportunities for improving the usability of the service .
Today we decided to talk about security and talk about SSL. Everyone knows that certificates provide a reliable connection, and we'll figure out exactly how this happens, and take a look at the protocols used.
 / Flickr / David Goehring / CC-BY
/ Flickr / David Goehring / CC-BY
')
SSL (secure sockets layer) is a cryptographic protocol for secure communication. Since version 3.0, SSL has been replaced with TLS (transport layer security), but the name of the previous version stuck, so today SSL is most often referred to as TLS.
The purpose of the protocol is to provide secure data transfer. At the same time, asymmetric encryption algorithms are used for authentication (public-private key pair), and symmetric (private key) is used to preserve confidentiality. The first type of encryption is more resource-intensive, so its combination with a symmetric algorithm helps to maintain high processing speed.
When a user visits the website, the browser requests certificate information from the server, which sends a copy of the SSL certificate with a public key. Further, the browser verifies the certificate, the name of which must match the name of the website.
In addition, the validity date of the certificate and the presence of a root certificate issued by a trusted certificate authority is checked. If the browser trusts the certificate, then it generates a pre-master secret of the session based on the public key, using the highest possible level of encryption that both parties support.
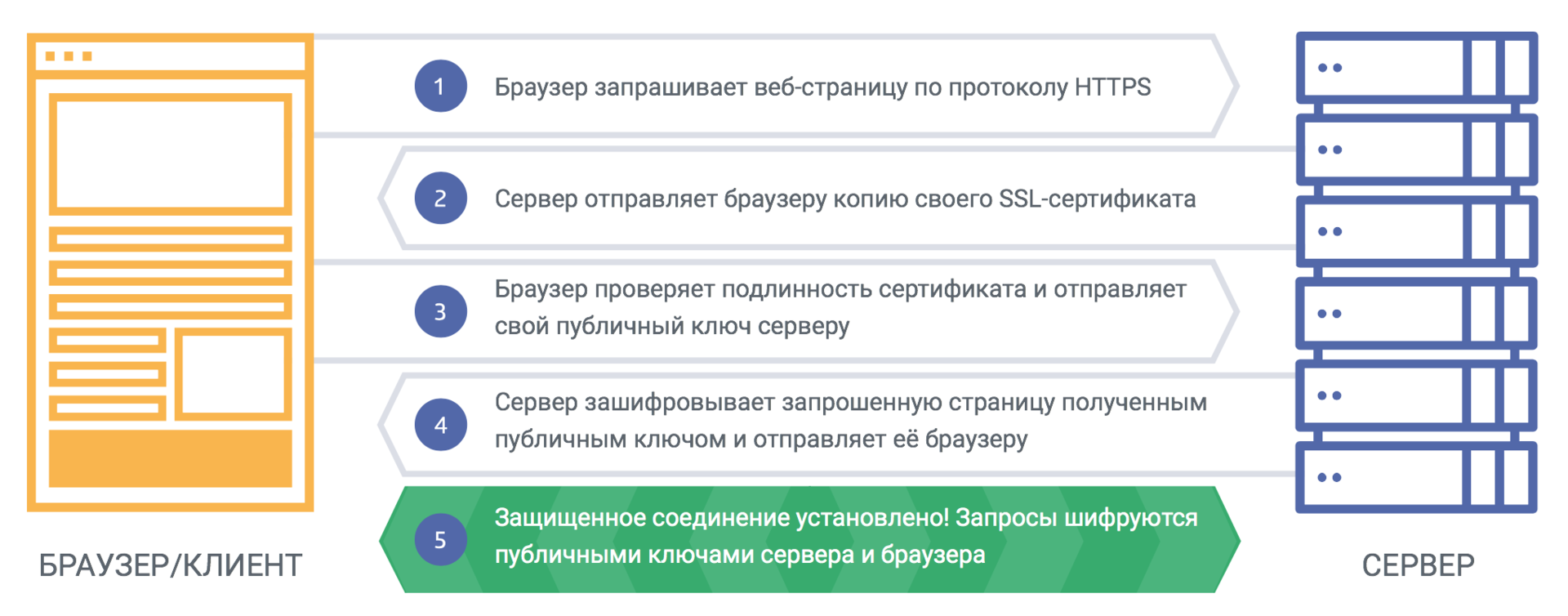
The server decrypts the pre-secret with its private key, agrees to continue the communication and create a master secret using a certain type of encryption. Now both parties use a symmetric key, which is valid only for this session. After its completion, the key is destroyed, and the next time you visit the site, the handshake process starts from the beginning.
For symmetric encryption different algorithms were used. The first was the DES block cipher developed by IBM. In the US, it was approved as a standard in the 70s. The algorithm is based on a Feistel network with 16 cycles. The key length is 56 bits, and the data block is 64.
The development of DES is the 3DES algorithm. It was created with the aim of improving the short key in the algorithm-progenitor. The key size and the number of encryption cycles increased threefold, which lowered the speed of work, but increased reliability.
There was also the RC2 variable-key block cipher , which worked faster than DES, and its 128-bit key was comparable to 3DES in reliability. The RC4 stream cipher was much faster than blocky cipher and was built on the basis of a pseudo-random bit generator. But today all these algorithms are considered unsafe or outdated.
The most up-to-date standard is AES, which officially replaced DES in 2002. It is based on the Rijndael block algorithm and is 6 times faster than 3DES. The block size here is 128 bits, and the key size is 128/192/256 bits, and the number of encryption rounds depends on the key size and can be 10/12/14, respectively.
As for asymmetric encryption, it is most often based on algorithms such as RSA, DSA, or ECC. RSA (named after the authors Rivest, Shamir and Adleman) is used for both encryption and digital signature. The algorithm is based on the complexity of factoring large numbers and supports all types of SSL certificates.
DSA (Digital Signature Algorithm) is used only to create a digital signature and is based on the computational complexity of taking logarithms in finite fields. For safety and performance is fully comparable with RSA.
ECC (Elliptic Curve Cryptography) determines a pair of keys using points on a curve and is used only for digital signatures. The main advantage of the algorithm is a higher level of security with a shorter key length (a 256-bit ECC key is comparable in reliability to a 3072-bit RSA key.
A shorter key also affects the processing time, which is noticeably reduced. This fact and the fact that the algorithm effectively handles a large number of connections made it a convenient tool for working with mobile communications. In SSL certificates you can use several encryption methods at once for greater security.
The purpose of the hash algorithm is to convert the entire contents of an SSL certificate into a bit-length string of fixed length. To encrypt the hash value, the certification authority's private key is used, which is included in the certificate as a signature.
The hash algorithm also uses the value required to verify the integrity of the transmitted data - the MAC (message authentication code). The MAC uses the display function to present the message data as a fixed length value, and then hash the message.
The TLS protocol uses an HMAC (hashed message authentication code) that uses a hash algorithm immediately with a shared secret key. Here, the key is attached to the data, and to confirm their authenticity, both parties must use the same secret keys, which provides greater security.
All encryption algorithms today support the SHA2 hashing algorithm, most often it is SHA-256. SHA-512 has a similar structure, but its word length is 64 bits (instead of 32), the number of rounds in the cycle is 80 (instead of 64), and the message is divided into blocks of 1024 bits (instead of 512 bits). Previously, the SHA1 and MD5 algorithms were used for the same purpose, but today they are considered vulnerable .
Talk about abandoning SHA1 was a long time ago, but at the end of February the algorithm was officially hacked . The researchers managed to achieve a collision of hashes, that is, the same hash for two different files, which proved the insecurity of using the algorithm for digital signatures. The first attempt was made back in 2015, although then it was possible to pick up only those messages whose hash coincided. Today we are talking about whole documents.
Now that we have figured out what the SSL / TLS protocol is and how connections are based on it, we can talk about the types of certificates.
Domain Validation, or domain-validated certificates, are suitable for non-commercial sites, as they only confirm the web server that serves the specific site to which the transition was made. This type of certificate is the cheapest and most popular, but cannot be considered completely safe, as it contains only information about a registered domain name.
Organization Validation, or certificates with verification of the organization, are more reliable, as they confirm the registration data of the company-owner. The legal entity is obliged to provide this information upon purchase of the certificate, and the certifying center may contact the company directly to confirm this information. The certificate meets RFC standards and contains information about who confirmed it, but information about the owner is not displayed.
Extended Validation, or certificate with extended verification, is considered the most reliable. Actually, a green lock or a shortcut in the browser means that the site has such a certificate. You can read about how different browsers inform users about the presence of a certificate or errors that occur.
He needs websites that conduct financial transactions and require a high level of confidentiality. However, many sites prefer to redirect users to make payments to external resources, confirmed by certificates with extended verification, while using OV certificates, which are quite enough to protect other users' data.
In addition, certificates may vary depending on the number of domains for which they were issued. Single-domain certificates (Single Certificate) are bound to a single domain, which is indicated upon purchase. Multi-domain certificates (such as Subject Alternative Name, Unified Communications Certificate, Multi Domain Certificate) will be valid for a larger number of domain names and servers, which are also defined when ordering. However, for the inclusion of additional domains, above a certain rate, you will need to pay separately.
There are also sub-domain certificates (such as WildCard), which cover all the subdomains of the domain name specified during registration. Sometimes you may need certificates that will simultaneously include not only several domains, but also subdomains. In such cases, you can purchase certificates such as Comodo PositiveSSL Multi-Domain Wildcard and Comodo Multi-Domain Wildcard SSL or (life hacking) a usual multi-domain certificate, where you can also specify the required subdomain names in the list of domains.
You can get an SSL certificate yourself: a pair of keys for this is generated through any generator, for example, free OpenSSL . And it is quite possible to use such a secure communication channel for internal purposes: between devices of your network or applications. But to use the website, the certificate must be acquired officially, so that in the certificate confirmation chain there must be a root certificate, browsers do not show messages about an unsafe connection, and users are comfortable with their data.
PS In addition on a subject from the blog IaaS-provider 1cloud:
Today we decided to talk about security and talk about SSL. Everyone knows that certificates provide a reliable connection, and we'll figure out exactly how this happens, and take a look at the protocols used.
 / Flickr / David Goehring / CC-BY
/ Flickr / David Goehring / CC-BY')
SSL (secure sockets layer) is a cryptographic protocol for secure communication. Since version 3.0, SSL has been replaced with TLS (transport layer security), but the name of the previous version stuck, so today SSL is most often referred to as TLS.
The purpose of the protocol is to provide secure data transfer. At the same time, asymmetric encryption algorithms are used for authentication (public-private key pair), and symmetric (private key) is used to preserve confidentiality. The first type of encryption is more resource-intensive, so its combination with a symmetric algorithm helps to maintain high processing speed.
Handshake
When a user visits the website, the browser requests certificate information from the server, which sends a copy of the SSL certificate with a public key. Further, the browser verifies the certificate, the name of which must match the name of the website.
In addition, the validity date of the certificate and the presence of a root certificate issued by a trusted certificate authority is checked. If the browser trusts the certificate, then it generates a pre-master secret of the session based on the public key, using the highest possible level of encryption that both parties support.

The server decrypts the pre-secret with its private key, agrees to continue the communication and create a master secret using a certain type of encryption. Now both parties use a symmetric key, which is valid only for this session. After its completion, the key is destroyed, and the next time you visit the site, the handshake process starts from the beginning.
Encryption algorithms
For symmetric encryption different algorithms were used. The first was the DES block cipher developed by IBM. In the US, it was approved as a standard in the 70s. The algorithm is based on a Feistel network with 16 cycles. The key length is 56 bits, and the data block is 64.
The development of DES is the 3DES algorithm. It was created with the aim of improving the short key in the algorithm-progenitor. The key size and the number of encryption cycles increased threefold, which lowered the speed of work, but increased reliability.
There was also the RC2 variable-key block cipher , which worked faster than DES, and its 128-bit key was comparable to 3DES in reliability. The RC4 stream cipher was much faster than blocky cipher and was built on the basis of a pseudo-random bit generator. But today all these algorithms are considered unsafe or outdated.
The most up-to-date standard is AES, which officially replaced DES in 2002. It is based on the Rijndael block algorithm and is 6 times faster than 3DES. The block size here is 128 bits, and the key size is 128/192/256 bits, and the number of encryption rounds depends on the key size and can be 10/12/14, respectively.
As for asymmetric encryption, it is most often based on algorithms such as RSA, DSA, or ECC. RSA (named after the authors Rivest, Shamir and Adleman) is used for both encryption and digital signature. The algorithm is based on the complexity of factoring large numbers and supports all types of SSL certificates.
DSA (Digital Signature Algorithm) is used only to create a digital signature and is based on the computational complexity of taking logarithms in finite fields. For safety and performance is fully comparable with RSA.
ECC (Elliptic Curve Cryptography) determines a pair of keys using points on a curve and is used only for digital signatures. The main advantage of the algorithm is a higher level of security with a shorter key length (a 256-bit ECC key is comparable in reliability to a 3072-bit RSA key.
A shorter key also affects the processing time, which is noticeably reduced. This fact and the fact that the algorithm effectively handles a large number of connections made it a convenient tool for working with mobile communications. In SSL certificates you can use several encryption methods at once for greater security.
Hash and MAC
The purpose of the hash algorithm is to convert the entire contents of an SSL certificate into a bit-length string of fixed length. To encrypt the hash value, the certification authority's private key is used, which is included in the certificate as a signature.
The hash algorithm also uses the value required to verify the integrity of the transmitted data - the MAC (message authentication code). The MAC uses the display function to present the message data as a fixed length value, and then hash the message.
The TLS protocol uses an HMAC (hashed message authentication code) that uses a hash algorithm immediately with a shared secret key. Here, the key is attached to the data, and to confirm their authenticity, both parties must use the same secret keys, which provides greater security.
All encryption algorithms today support the SHA2 hashing algorithm, most often it is SHA-256. SHA-512 has a similar structure, but its word length is 64 bits (instead of 32), the number of rounds in the cycle is 80 (instead of 64), and the message is divided into blocks of 1024 bits (instead of 512 bits). Previously, the SHA1 and MD5 algorithms were used for the same purpose, but today they are considered vulnerable .
Talk about abandoning SHA1 was a long time ago, but at the end of February the algorithm was officially hacked . The researchers managed to achieve a collision of hashes, that is, the same hash for two different files, which proved the insecurity of using the algorithm for digital signatures. The first attempt was made back in 2015, although then it was possible to pick up only those messages whose hash coincided. Today we are talking about whole documents.
Certificates are different
Now that we have figured out what the SSL / TLS protocol is and how connections are based on it, we can talk about the types of certificates.
Domain Validation, or domain-validated certificates, are suitable for non-commercial sites, as they only confirm the web server that serves the specific site to which the transition was made. This type of certificate is the cheapest and most popular, but cannot be considered completely safe, as it contains only information about a registered domain name.
Organization Validation, or certificates with verification of the organization, are more reliable, as they confirm the registration data of the company-owner. The legal entity is obliged to provide this information upon purchase of the certificate, and the certifying center may contact the company directly to confirm this information. The certificate meets RFC standards and contains information about who confirmed it, but information about the owner is not displayed.
Extended Validation, or certificate with extended verification, is considered the most reliable. Actually, a green lock or a shortcut in the browser means that the site has such a certificate. You can read about how different browsers inform users about the presence of a certificate or errors that occur.
He needs websites that conduct financial transactions and require a high level of confidentiality. However, many sites prefer to redirect users to make payments to external resources, confirmed by certificates with extended verification, while using OV certificates, which are quite enough to protect other users' data.
In addition, certificates may vary depending on the number of domains for which they were issued. Single-domain certificates (Single Certificate) are bound to a single domain, which is indicated upon purchase. Multi-domain certificates (such as Subject Alternative Name, Unified Communications Certificate, Multi Domain Certificate) will be valid for a larger number of domain names and servers, which are also defined when ordering. However, for the inclusion of additional domains, above a certain rate, you will need to pay separately.
There are also sub-domain certificates (such as WildCard), which cover all the subdomains of the domain name specified during registration. Sometimes you may need certificates that will simultaneously include not only several domains, but also subdomains. In such cases, you can purchase certificates such as Comodo PositiveSSL Multi-Domain Wildcard and Comodo Multi-Domain Wildcard SSL or (life hacking) a usual multi-domain certificate, where you can also specify the required subdomain names in the list of domains.
You can get an SSL certificate yourself: a pair of keys for this is generated through any generator, for example, free OpenSSL . And it is quite possible to use such a secure communication channel for internal purposes: between devices of your network or applications. But to use the website, the certificate must be acquired officially, so that in the certificate confirmation chain there must be a root certificate, browsers do not show messages about an unsafe connection, and users are comfortable with their data.
PS In addition on a subject from the blog IaaS-provider 1cloud:
Source: https://habr.com/ru/post/326292/
All Articles