Sandbox technology. Check Point SandBlast. Part 3

Well, we got to the final part. The previous ones can be found here ( first , second ). We continue the theme of protection against targeted attacks. We have already discussed how to protect yourself at the network level, in particular, the organization’s perimeter. However, in the modern world this is not enough. This time we will talk about protecting users' computers.
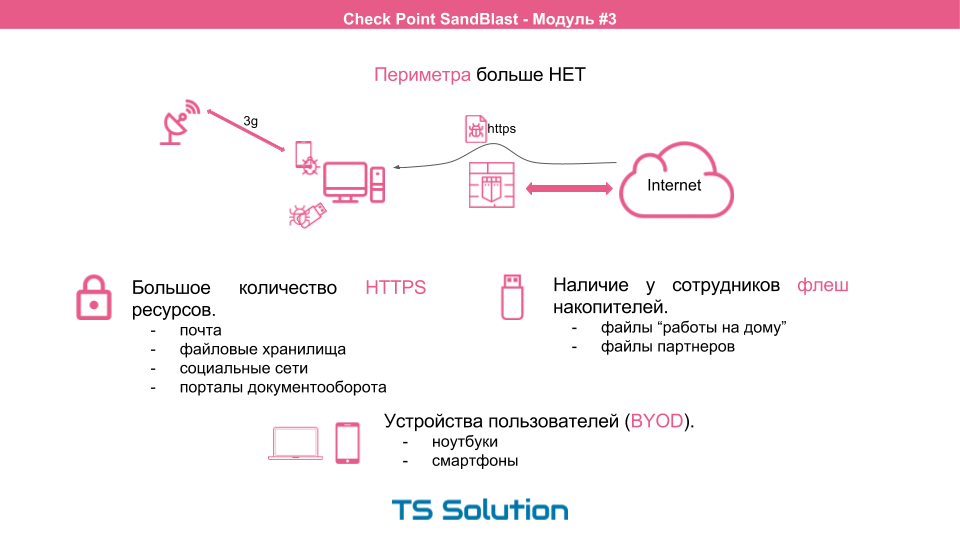
Perimeter
The concept of “perimeter” becomes very conditional and difficult to distinguish. Almost all Internet resources are transferred to the secure https protocol. This and mail and file storage, social networks, portals, workflow. Those. Transmitted data is encrypted, which makes it difficult to analyze at the network level. (All modern NGFWs are required to have an https inspection function).
Almost every employee has a flash drive on which he brings files from home. With flash drives can come and your partners. It’s very difficult to say where these flash drives were inserted before and what’s on them now.
')
Personal smartphones and laptops. These devices are increasingly used for work purposes. At the same time, the same smartphone allows you to establish Internet connections via 3G or LTE.
As a result, due to the means listed, we have a potential hole in our corporate network, through which attackers bypass all our network protection tools, no matter how cool (expensive) and reliable they are. You can of course prohibit the use of flash drives and personal smartphones for work, but very often this only harms the core business.
The only reasonable solution in this case is to organize an additional level of protection - the protection of users' computers.
Until now, the most common user protection tools have been desktop antivirus, desktop ME and desktop intrusion prevention system. But as mentioned earlier, all these tools work with already known malware. How to deal with zero-day attacks?
Check Point SandBlast Agent
To solve this problem, CheckPoint has released the SandBlast Agent. There are two versions of the agent: for the Browser (as an extension) and for the PC.
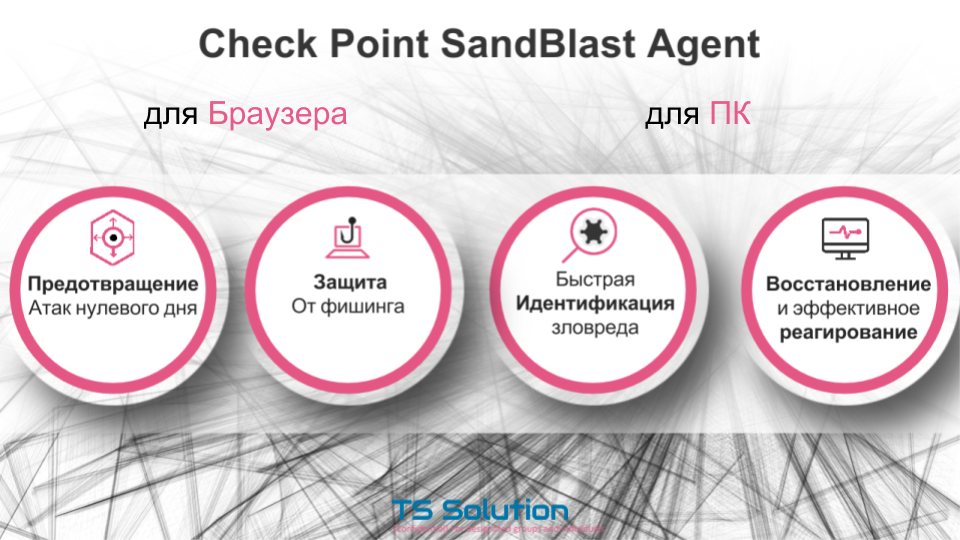
These agents allow you to implement protection against zero-day attacks, protection against phishing and cryptographers. They can quickly identify the malware and react effectively by placing it in quarantine or blocking an infected computer. In addition, the agent for the computer allows you to set data if a coder was running. But first things first.

Let's look at the work of SandBlast browser agent. The agent is placed in the browser as an extension. At the moment, extensions are only available for google chrome, but soon there will be support for other browsers.
This agent allows you to securely download files even from HTTPS resources. For example, one of your employees uses mail - gmail. He receives a letter with an attachment. The user starts the file download. The browser agent intercepts this download and allows you to either convert the source file to pdf format or clear all active content. Those. The previously described Threat Extraction technology is used. This is a very useful feature.
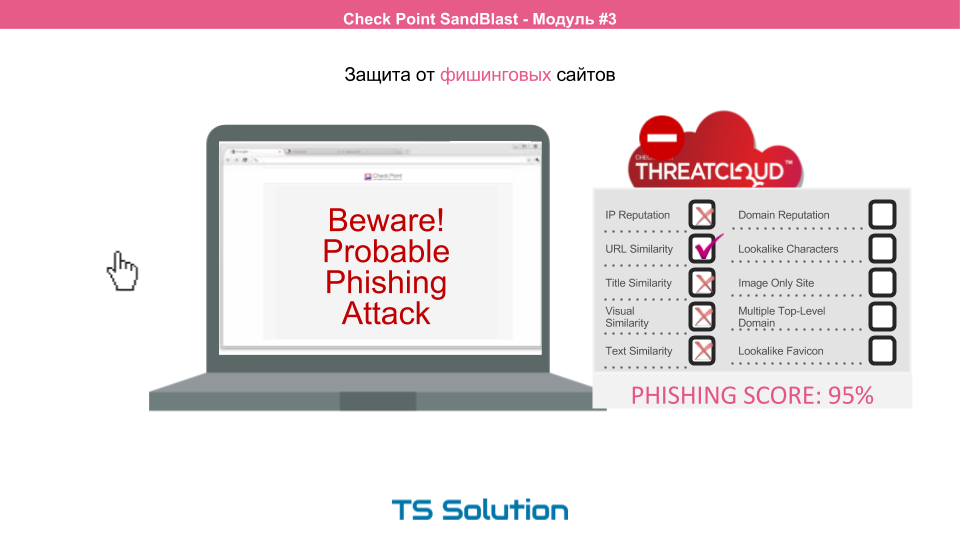
Also, a browser agent can protect against phishing. Those. You can protect users from getting to fake sites that are designed to collect passwords or spread viruses. And not only sites that are in common databases designated as malicious are prohibited. The agent has the function of analysis and, due to a large number of signs, it can determine that the site is fake and does not carry any payload. Even if this site was created 5 minutes ago.
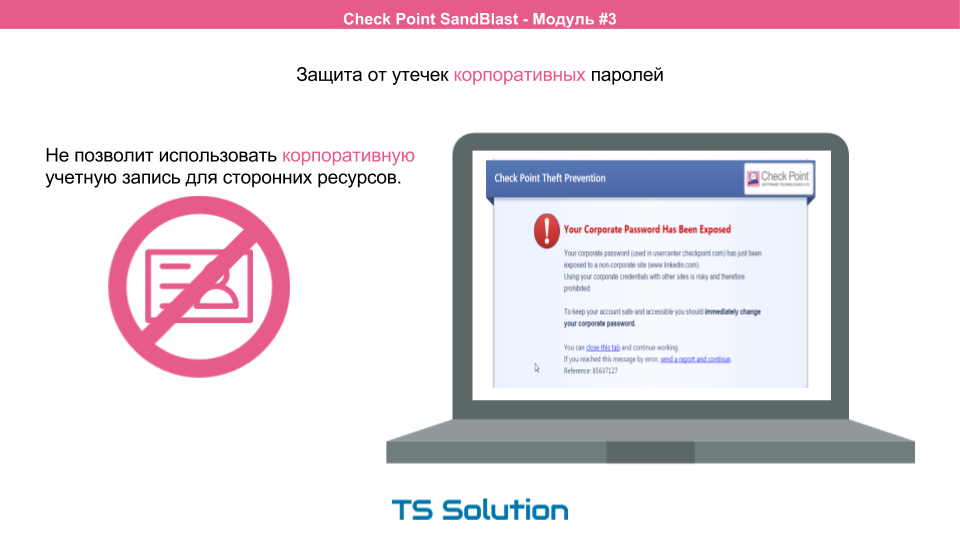
The browser agent has another great feature. This is a protection against leakage of corporate accounts and passwords. Unfortunately, quite a large number of users use their passwords many times in order not to forget it by chance. Those. The password for the domain account can also be used to access the social network or torrent tracker. It is rather unsafe. SandBlast Agent makes it possible to determine that corporate passwords were used on any site and immediately informed the administrator and the user about this. The user is immediately recommended to change the working password.
Agent for browser is a great addition to protect your corporate network. But what to do if the file is still on the victim's computer? For example, using the same flash drive. To do this, there is a desktop version of the agent SandBlast.

This agent, in addition to browser functionality, also has a built-in antibot, can place virus files in quarantine, or block the entire system so that the virus does not spread further.
In addition, the desktop agent is very useful in investigating various incidents. The agent constantly collects information about the applications and processes used. files, network activity. In the case of detection and identification of malware, analysis and generation of an incident report automatically takes place. Moreover, if you use SmartEvent, then these reports are integrated with the general analysis system. Thus, you see the whole picture in one place, which is very convenient and allows you to respond more quickly to various incidents.

An example of the report can be seen on this slide. Here you can see from which application everything started, what processes were launched after that, and how the virus got to this computer in principle. We will review this report in more detail in the following labs.
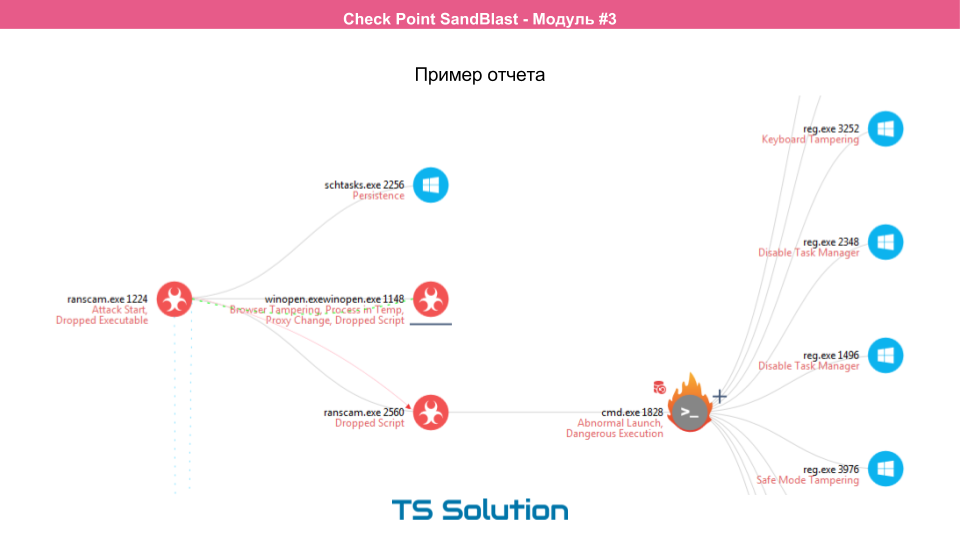
SandBlast Agent can be implemented in three ways:

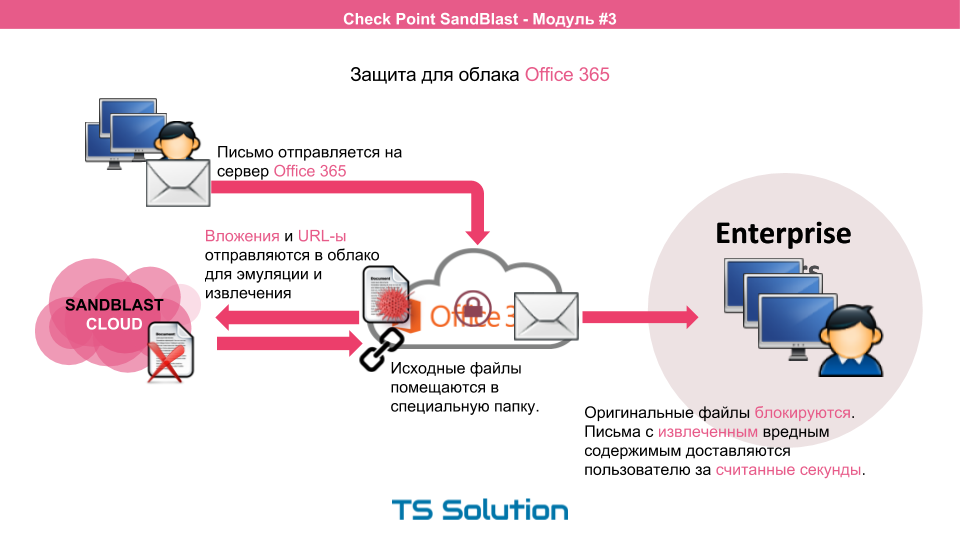
In addition, if you are using Office 365, then you can also use SandBlast security mechanisms. The Microsoft cloud will automatically send all incoming files to the SandBlast cloud for analysis. At the same time, Threat Extraction can also be configured, which will allow users to deliver either cleaned or converted files to users. All this will happen in seconds. In addition, Google mail support will soon be available.
This theoretical part is over. You can watch it in video format:
Now we can proceed to laboratory work.
Lab 6: Browser Agents
In the course of laboratory work, we learned about the features of the CheckPoint SandBlast Zero-Day Protection plugin. We also reviewed its basic settings in conjunction with the SMESG security gateway. In practice, we considered the process of converting files to pdf and cleaning up malicious content.
Lab 7 - Desktop Agents
During the work, we will configure SandBlast Agent, download and run the infected file and see what happens. We will also analyze the available reports.
PS Thanks to everyone who got acquainted with this course. I hope we managed to at least partially sanctify modern sandbox technology, in particular from Check Point. I would also like to note that absolutely all the solutions described can be tried absolutely free by leaving an application on our website .
Source: https://habr.com/ru/post/326288/
All Articles