OWASP Top 10 2017 RC

The list of Top 10 vulnerabilities from OWASP - the most critical security risks of web applications - has been updated.
The OWASP Top-10 project is referenced by many standards, tools, and organizations, including MITER, PCI DSS, DISA, FTC, and many others. The OWASP Top 10 is a recognized methodology for assessing web application vulnerabilities worldwide.
The Open Web Application Security Project (OWASP) is an open source web application security project. The OWASP community includes corporations, educational organizations and individuals from around the world. The community is working to create articles, tutorials, documentation, tools and technologies that are freely available.
')
The standard version is updated approximately once every three years and reflects current trends in web application security.
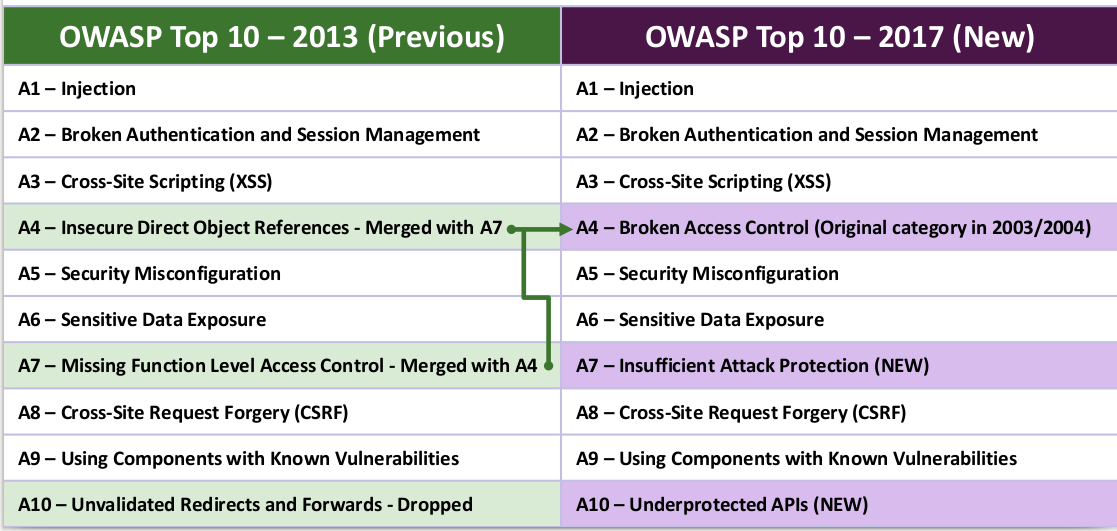
OWASP Top 10 2013
The list of the most dangerous risks (vulnerabilities) of web applications from 2013:
- A1 Code Implementation
- A2 Incorrect authentication and session management
- A3 Crossite scripting
- A4 Insecure Direct Object Links
- A5 Unsafe Configuration
- A6 Leaked sensitive data
- A7 Lack of access control to the functional level
- A8 Cross-Site Request Forgery
- A9 Using components with known vulnerabilities
- A10 Unvalidated Redirects
OWASP Top 10 2017 RC
The list of the most dangerous risks (vulnerabilities) of web applications from 2017:
- A1 Code Implementation
- A2 Incorrect authentication and session management
- A3 Crossite scripting
- A4 Access Control Violation
- A5 Unsafe Configuration
- A6 Leaked sensitive data
- A7 Insufficient attack protection (NEW)
- A8 Cross-Site Request Forgery
- A9 Using components with known vulnerabilities
- A10 Insufficient logging and monitoring
Changes
The first three - code injections, lack of management and storage of the session and cross-site scripting remained unchanged, this indicates that despite the large number of best practices for writing secure code, data cleaning tools, implementing various tokens and other things, the web application is not safer are becoming.
The old category returned to the 4th place - Broken Access Control, which in the new edition consists of the merger of A4 and A7 from the 2013 edition.
7th place now takes a new category - Insufficient Attack Protection. Most web applications and environments lack the ability to detect, prevent, and respond to modern attacks — both automatic and manual. Detection and protection against attacks goes far beyond the verification of basic input (usually this is validation of input values) and should include automatic detection, logging, response, and even blocking attempted exploitation. Application owners should also be able to quickly deploy patches to protect against attacks. In other words, it is a direct recommendation to use a web application firewall to protect a web application.
Unvalidated redirects disappeared from 10th place, and their place was taken by unprotected class API tools such as JavaScript, SOAP / XML, REST / JSON, RPC, GWT, and so on. These classes are often unprotected and contain many vulnerabilities.
Participants of the Open Web Application Security Project (OWASP) for over 13 years have been compiling a list of the top 10 most dangerous vulnerabilities in web applications, trying to attract the attention of web developers. On the OWASP site, each of the vulnerabilities is parsed in detail.
→ OWASP project
Source: https://habr.com/ru/post/326272/
All Articles