Parse the qualified X.509 certificates in the search for TIN, SNILS and OGRN
 “Colleagues, we need to keep a register of issued qualified certificates with the ability to search on the TIN, SNILS and OGRN. How many days are needed to create the certificate parser and the first layout? ”- the next bulletin started with this question from the head.
“Colleagues, we need to keep a register of issued qualified certificates with the ability to search on the TIN, SNILS and OGRN. How many days are needed to create the certificate parser and the first layout? ”- the next bulletin started with this question from the head.Since I was asked to write the parser, I had to think and delve into memory in order to assess the complexity of the task and the approximate time frame for its implementation.
I once participated in a small SSL MITM modeling project, where I was responsible for generating keys and certificates for this very “man in the middle”. Therefore, it represented that a qualified certificate of the electronic signature verification key (hereinafter referred to as a qualified certificate ) is an X.509 certificate, for describing the internal structure of which
')
But I didn’t remember that then these INNs, SNILSs and OGRNs would come across. Therefore, he answered more than modestly: “Boss, two days, no less!”, Hoping to complete the task in a few hours.
Below is a story about how badly I made a mistake in the calculations, as well as a ready-made solution for parsing X.509 certificates in C # with the ability to extract fields and their attributes with given object identifiers (OID).
Step 1. Preliminary research and hypothesis testing
No, seriously, is it true that there is a SNILS in the X.509 certificate? To check, we will find a sample - we ask for help from Yandex on the request “register of issued qualified certificates”, on the very first page of issue we find the Register of certificates issued by TC GKU LO “OEP” certificates , download the first received certificate (number 10842) - Komarov_Aleksey_Petrovich_2017-03-31_a2ba20c4. cer .
Komarov Alexey Petrovich: a view from the inside
----- BEGIN CERTIFICATE -----
MIIIzjCCCH2gAwIBAgIRAJ6w9zrKuNKX5xH + FfdJYxwwCAYGKoUDAgIDMIH4MRww
GgYJKoZIhvcNAQkBFg11ZGNAbGVucmVnLnJ1MRgwFgYFKoUDZAESDTExMjQ3MDMw
MDAzMzMxGjAYBggqhQMDgQMBARIMMDA0NzAzMTI1OTU2MQswCQYDVQQGEwJSVTEs
MCoGA1UECAwjNzgg0LMu0KHQsNC90LrRgi3Qn9C10YLQtdGA0LHRg9GA0LMxJjAk
BgNVBAcMHdCh0LDQvdC60YIt0J / QtdGC0LXRgNCx0YPRgNCzMR0wGwYDVQQKDBTQ
k9Ca0KMg0JvQniAi0J7QrdCfIjEgMB4GA1UEAwwX0KPQpiDQk9Ca0KMg0JvQniDQ
ntCt0J8wHhcNMTcwMzMxMTAyODEwWhcNMTgwMzMxMTAyODEwWjCCAo4xIzAhBgkq
hkiG9w0BCQEWFGFwX2tvbWFyb3ZAbGVucmVnLnJ1MRowGAYIKoUDA4EDAQESDDAw
Nzg0MjM1NDk2NjEWMBQGBSqFA2QDEgswNzMxMTk5NjY2ODEYMBYGBSqFA2QBEg0x
MDc3ODQ3MTkyNjA5MSwwKgYDVQQMDCPQk9C70LDQstC90YvQuSDRgdC / 0LXRhtC4
0LDQu9C40YHRgjFBMD8GA1UECww40JTQtdC / 0LDRgNGC0LDQvNC10L3RgiDQu9C1
0YHQvdC + 0LPQviDQutC + 0LzQv9C70LXQutGB0LAxajBoBgNVBAoMYdCa0L7QvNC4
0YLQtdGCINC / 0L4g0L / RgNC40YDQvtC00L3Ri9C8INGA0LXRgdGD0YDRgdCw0Lwg
0JvQtdC90LjQvdCz0YDQsNC00YHQutC + 0Lkg0L7QsdC70LDRgdGC0LgxKjAoBgNV
BAkMIdGD0Lsu0KLQvtGA0LbQutC + 0LLRgdC60LDRjywg0LQuNDEmMCQGA1UEBwwd
0KHQsNC90LrRgi3Qn9C10YLQtdGA0LHRg9GA0LMxLDAqBgNVBAgMIzc4INCzLtCh
0LDQvdC60YIt0J / QtdGC0LXRgNCx0YPRgNCzMQswCQYDVQQGEwJSVTEoMCYGA1UE
Kgwf0JDQu9C10LrRgdC10Lkg0J / QtdGC0YDQvtCy0LjRhzEXMBUGA1UEBAwO0JrQ
vtC80LDRgNC + 0LIxajBoBgNVBAMMYdCa0L7QvNC40YLQtdGCINC / 0L4g0L / RgNC4
0YDQvtC00L3Ri9C8INGA0LXRgdGD0YDRgdCw0Lwg0JvQtdC90LjQvdCz0YDQsNC0
0YHQutC + 0Lkg0L7QsdC70LDRgdGC0LgwYzAcBgYqhQMCAhMwEgYHKoUDAgIkAAYH
KoUDAgIeAQNDAARA2jaQisiN ++ YQULAiW4b8Llik90VIKNPqUcEOVlrfplASb2W /
qc9giz + rP1 / VvQXAmRKPaL3dM33MExypCJOlGaOCBEUwggRBMA4GA1UdDwEB / wQE
AwIDqDAdBgNVHQ4EFgQU7SOIwRLKC8mDQV / q2KtCaTA06Q8wNQYJKwYBBAGCNxUH
BCgwJeKoUDAgIyAQmDx + sNh / eeXoXlhVqDn / dWgZtags1fAgEBAgEAMIIBYwYD
VR0jBIIBWjCCAVaAFNGDmDS2EE52TJ + tKf2SJRHjAFYJoYIBKaSCASUwggEhMRow
GAYIKoUDA4EDAQESDDAwNzcxMDQ3NDM3NTEYMBYGBSqFA2QBEg0xMDQ3NzAyMDI2
NzAxMR4wHAYJKoZIhvcNAQkBFg9kaXRAbWluc3Z5YXoucnUxPDA6BgNVBAkMMzEy
NTM3NSDQsy4g0JzQvtGB0LrQstCwINGD0LsuINCi0LLQtdGA0YHQutCw0Y8g0LQu
NzEsMCoGA1UECgwj0JzQuNC90LrQvtC80YHQstGP0LfRjCDQoNC + 0YHRgdC40Lgx
FTATBgNVBAcMDNCc0L7RgdC60LLQsDEcMBoGA1UECAwTNzcg0LMuINCc0L7RgdC6
0LLQsDELMAkGA1UEBhMCUlUxGzAZBgNVBAMMEtCj0KYgMSDQmNChINCT0KPQpoIR
BKgeQAWpGF6C5hHB / EETxEYwOQYDVR0lBDIwMAYIKwYBBQUHAwIGCCsGAQUFBwME
BggqhQMFARgCLAYIKoUDBQEYAgYGBiqFA2QCATBJBgkrBgEEAYI3FQoEPDA6MAoG
CCsGAQUFBwMCMAoGCCsGAQUFBwMEMAoGCCqFAwUBGAIsMAoGCCqFAwUBGAIGMAgG
BiqFA2QCATATBgNVHSAEDDAKMAgGBiqFA2RxATCCAQYGBSqFA2RwBIH8MIH5DCsi
0JrRgNC40L / RgtC + 0J / RgNC + IENTUCIgKNCy0LXRgNGB0LjRjyA0LjApDCoi0JrR
gNC40L / RgtC + 0J / QoNCeINCj0KYiINCy0LXRgNGB0LjQuCAyLjAMTtCh0LXRgNGC
0LjRhNC40LrQsNGCINGB0L7QvtGC0LLQtdGC0YHRgtCy0LjRjyDihJbQodCkLzEy
NC0zMDEwINC + 0YIgMzAuMTIuMjAxNgxO0KHQtdGA0YLQuNGE0LjQutCw0YIg0YHQ
vtC + 0YLQstC10YLRgdGC0LLQuNGPIOKEltCh0KQvMTI4LTI5ODMg0L7RgiAxOC4x
MS4yMDE2MDgGBSqFA2RvBC8MLSLQmtGA0LjQv9GC0L7Qn9GA0L4gQ1NQIiAo0LLQ
tdGA0YHQuNGPIDMuNi4xKTBWBgNVHR8ETzBNMCWgI6Ahhh9odHRwOi8vY2EubGVu
b2JsLnJ1L2UtZ292LTUuY3JsMCSgIqAghh5odHRwOi8vdWNsby5zcGIucnUvZS1n
b3YtNS5jcmwwOwYIKwYBBQUHAQEELzAtMCsGCCsGAQUFBzAChh9odHRwOi8vY2Eu
bGVub2JsLnJ1L2UtZ292LTUuY2VyMAgGBiqFAwICAwNBAEe1iKkhV4BQcDsBSAJa
kWfh5tNaPIp / jFc + HZtpmgJoGU8CpOdX3I5YAgJTx9O + Q4ylHwJl68rfCD44s0Q4
wqE =
----- END CERTIFICATE -----
MIIIzjCCCH2gAwIBAgIRAJ6w9zrKuNKX5xH + FfdJYxwwCAYGKoUDAgIDMIH4MRww
GgYJKoZIhvcNAQkBFg11ZGNAbGVucmVnLnJ1MRgwFgYFKoUDZAESDTExMjQ3MDMw
MDAzMzMxGjAYBggqhQMDgQMBARIMMDA0NzAzMTI1OTU2MQswCQYDVQQGEwJSVTEs
MCoGA1UECAwjNzgg0LMu0KHQsNC90LrRgi3Qn9C10YLQtdGA0LHRg9GA0LMxJjAk
BgNVBAcMHdCh0LDQvdC60YIt0J / QtdGC0LXRgNCx0YPRgNCzMR0wGwYDVQQKDBTQ
k9Ca0KMg0JvQniAi0J7QrdCfIjEgMB4GA1UEAwwX0KPQpiDQk9Ca0KMg0JvQniDQ
ntCt0J8wHhcNMTcwMzMxMTAyODEwWhcNMTgwMzMxMTAyODEwWjCCAo4xIzAhBgkq
hkiG9w0BCQEWFGFwX2tvbWFyb3ZAbGVucmVnLnJ1MRowGAYIKoUDA4EDAQESDDAw
Nzg0MjM1NDk2NjEWMBQGBSqFA2QDEgswNzMxMTk5NjY2ODEYMBYGBSqFA2QBEg0x
MDc3ODQ3MTkyNjA5MSwwKgYDVQQMDCPQk9C70LDQstC90YvQuSDRgdC / 0LXRhtC4
0LDQu9C40YHRgjFBMD8GA1UECww40JTQtdC / 0LDRgNGC0LDQvNC10L3RgiDQu9C1
0YHQvdC + 0LPQviDQutC + 0LzQv9C70LXQutGB0LAxajBoBgNVBAoMYdCa0L7QvNC4
0YLQtdGCINC / 0L4g0L / RgNC40YDQvtC00L3Ri9C8INGA0LXRgdGD0YDRgdCw0Lwg
0JvQtdC90LjQvdCz0YDQsNC00YHQutC + 0Lkg0L7QsdC70LDRgdGC0LgxKjAoBgNV
BAkMIdGD0Lsu0KLQvtGA0LbQutC + 0LLRgdC60LDRjywg0LQuNDEmMCQGA1UEBwwd
0KHQsNC90LrRgi3Qn9C10YLQtdGA0LHRg9GA0LMxLDAqBgNVBAgMIzc4INCzLtCh
0LDQvdC60YIt0J / QtdGC0LXRgNCx0YPRgNCzMQswCQYDVQQGEwJSVTEoMCYGA1UE
Kgwf0JDQu9C10LrRgdC10Lkg0J / QtdGC0YDQvtCy0LjRhzEXMBUGA1UEBAwO0JrQ
vtC80LDRgNC + 0LIxajBoBgNVBAMMYdCa0L7QvNC40YLQtdGCINC / 0L4g0L / RgNC4
0YDQvtC00L3Ri9C8INGA0LXRgdGD0YDRgdCw0Lwg0JvQtdC90LjQvdCz0YDQsNC0
0YHQutC + 0Lkg0L7QsdC70LDRgdGC0LgwYzAcBgYqhQMCAhMwEgYHKoUDAgIkAAYH
KoUDAgIeAQNDAARA2jaQisiN ++ YQULAiW4b8Llik90VIKNPqUcEOVlrfplASb2W /
qc9giz + rP1 / VvQXAmRKPaL3dM33MExypCJOlGaOCBEUwggRBMA4GA1UdDwEB / wQE
AwIDqDAdBgNVHQ4EFgQU7SOIwRLKC8mDQV / q2KtCaTA06Q8wNQYJKwYBBAGCNxUH
BCgwJeKoUDAgIyAQmDx + sNh / eeXoXlhVqDn / dWgZtags1fAgEBAgEAMIIBYwYD
VR0jBIIBWjCCAVaAFNGDmDS2EE52TJ + tKf2SJRHjAFYJoYIBKaSCASUwggEhMRow
GAYIKoUDA4EDAQESDDAwNzcxMDQ3NDM3NTEYMBYGBSqFA2QBEg0xMDQ3NzAyMDI2
NzAxMR4wHAYJKoZIhvcNAQkBFg9kaXRAbWluc3Z5YXoucnUxPDA6BgNVBAkMMzEy
NTM3NSDQsy4g0JzQvtGB0LrQstCwINGD0LsuINCi0LLQtdGA0YHQutCw0Y8g0LQu
NzEsMCoGA1UECgwj0JzQuNC90LrQvtC80YHQstGP0LfRjCDQoNC + 0YHRgdC40Lgx
FTATBgNVBAcMDNCc0L7RgdC60LLQsDEcMBoGA1UECAwTNzcg0LMuINCc0L7RgdC6
0LLQsDELMAkGA1UEBhMCUlUxGzAZBgNVBAMMEtCj0KYgMSDQmNChINCT0KPQpoIR
BKgeQAWpGF6C5hHB / EETxEYwOQYDVR0lBDIwMAYIKwYBBQUHAwIGCCsGAQUFBwME
BggqhQMFARgCLAYIKoUDBQEYAgYGBiqFA2QCATBJBgkrBgEEAYI3FQoEPDA6MAoG
CCsGAQUFBwMCMAoGCCsGAQUFBwMEMAoGCCqFAwUBGAIsMAoGCCqFAwUBGAIGMAgG
BiqFA2QCATATBgNVHSAEDDAKMAgGBiqFA2RxATCCAQYGBSqFA2RwBIH8MIH5DCsi
0JrRgNC40L / RgtC + 0J / RgNC + IENTUCIgKNCy0LXRgNGB0LjRjyA0LjApDCoi0JrR
gNC40L / RgtC + 0J / QoNCeINCj0KYiINCy0LXRgNGB0LjQuCAyLjAMTtCh0LXRgNGC
0LjRhNC40LrQsNGCINGB0L7QvtGC0LLQtdGC0YHRgtCy0LjRjyDihJbQodCkLzEy
NC0zMDEwINC + 0YIgMzAuMTIuMjAxNgxO0KHQtdGA0YLQuNGE0LjQutCw0YIg0YHQ
vtC + 0YLQstC10YLRgdGC0LLQuNGPIOKEltCh0KQvMTI4LTI5ODMg0L7RgiAxOC4x
MS4yMDE2MDgGBSqFA2RvBC8MLSLQmtGA0LjQv9GC0L7Qn9GA0L4gQ1NQIiAo0LLQ
tdGA0YHQuNGPIDMuNi4xKTBWBgNVHR8ETzBNMCWgI6Ahhh9odHRwOi8vY2EubGVu
b2JsLnJ1L2UtZ292LTUuY3JsMCSgIqAghh5odHRwOi8vdWNsby5zcGIucnUvZS1n
b3YtNS5jcmwwOwYIKwYBBQUHAQEELzAtMCsGCCsGAQUFBzAChh9odHRwOi8vY2Eu
bGVub2JsLnJ1L2UtZ292LTUuY2VyMAgGBiqFAwICAwNBAEe1iKkhV4BQcDsBSAJa
kWfh5tNaPIp / jFc + HZtpmgJoGU8CpOdX3I5YAgJTx9O + Q4ylHwJl68rfCD44s0Q4
wqE =
----- END CERTIFICATE -----
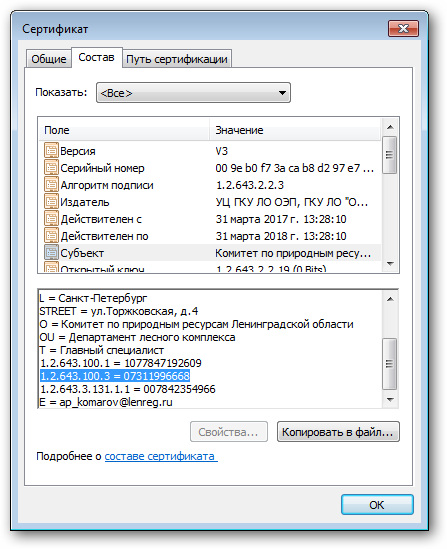
We open the certificate using the standard Windows OC viewer and find in the subject description a suspiciously similar string with the object identifier 1.2.643.100.3, consisting of 11 digits. SNILS ?
Lyrical digression
The fact that such an object identifier (OID) in general is best read here . How object identifiers are used in the description of the structure of X.509 certificates - see Survival Guide - TLS / SSL and SSL certificates (X.509) .
We open the certificate in a virtual machine with an established crypto-provider CryptoPRO CSP, which certainly knows the specifics of the country, and confirm the guess.
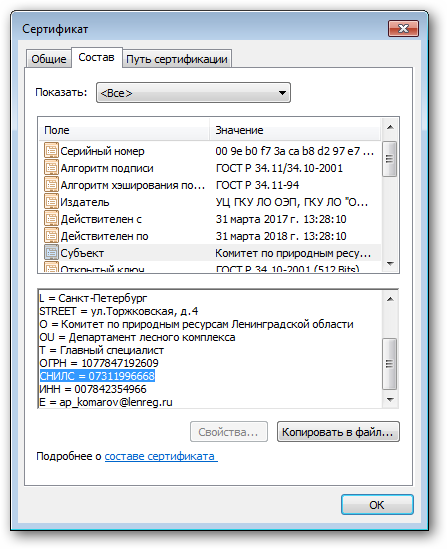
So, the task posed is potentially feasible, there is a SNILS in a qualified certificate. Go ahead.
Step 2. Acquaintance with the regulatory framework
Naturally, it is not possible to find the TIN, SNILS and OGRN in any X.509 certificate. For example, if in the browser you click on the lock next to the address bar “https://yandex.ru/” and export the certificate, then there will not be any long numeric sequences.
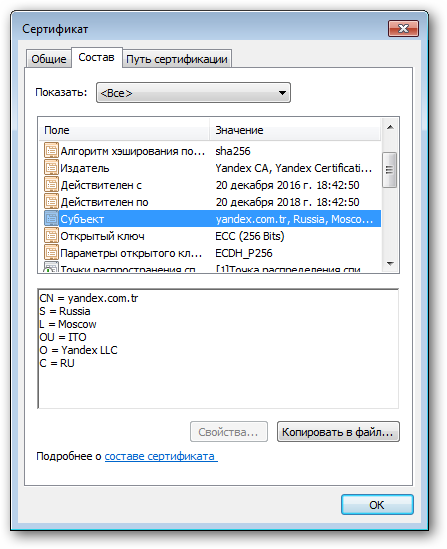
It should be noted that the standard X.509 does not limit the set of attributes that can be specified in the name of the publisher and / or subject. The standard only recommends maintaining a number of attributes, among which are a country, an organization, a region, a common name, etc., but not a word is said about SNILS and other things.
The data we are interested in is precisely contained in certificates that fall within the scope of the Federal Law “On Electronic Signature” of April 6, 2011 No. 63-FZ. We carefully study article 17 and make sure that the INN, SNILS and OGRN really should be contained in qualified certificates.
Now it is necessary to find out which OID corresponds to the TIN value, and which one - the SNILS and OGRN. With this question, the review of the regulatory framework , which refers to the Order of the Federal Security Service of the Russian Federation of December 27, 2011 No. 795 “On approval of requirements for the form of a qualified certificate ...”, will help. Open the order and find the information we are interested in:
18. Additional attributes of the name, the need to use which is established in accordance with federal law, include:
1) OGRN.
The value of the OGRN attribute is a string consisting of 13 digits and representing the OGRN of the owner of a qualified certificate - a legal entity. The object identifier of the attribute type OGRN is 1.2.643.100.1 , the attribute type OGRN is described as follows: OGRN :: = NUMERIC STRING SIZE 13;
2) SNILS (SNILS).
The value of the SNILS attribute is a string consisting of 11 digits representing the SNILS of the owner of a qualified certificate - an individual. The object identifier of the attribute type SNILS is 1.2.643.100.3 , the attribute type SNILS is described as follows: SNILS :: = NUMERIC STRING SIZE 11;
3) INN (INN).
The value of the INN attribute is a 12-digit string representing the TIN of the owner of the qualified certificate. The object identifier of the type of the INN attribute is 1.2.643.3.131.1.1 , the attribute type of the INN is described as follows: INN :: = NUMERIC STRING SIZE 12.
You can try to check yourself - knowing the OID, find the object described by it. For example, we take OID = 1.2.643.100.3 (SNILS). We turn to the official register of identifiers and "walk" on the tree:
1 - International Organization for Standardization (ISO) 1.2 - ISO Member Bodies 1.2.643 - Russian federation The value 1.2.643.100 can no longer be found, this OID is not listed in the lists of the official catalog. Follow the link to the national registry , continue to search. Detected identifiers that you managed to “descend” through the tree:
1.2.643.100 ( OID' 1.2.643.100.1, , OID' 1.2.643.100.3, ) - 1.2.643.3.131 ( OID' 1.2.643.3.131.1.1, ) - Check yourself will not work, because not all tiers are displayed on the site of the national register of object identifiers. But hope dies last, we try to send an official request to the operator of the national tree - to OJSC Infoteks Internet Trust. We quote the correspondence:
- Tell me , is it possible on the site oid.iitrust.ru to clarify which objects correspond to OIDs: 1.2.643.3.131.1.1, 1.2.643.100.1, 1.2.643.100.3? They are not in the search, but we assume that this is an TIN, OGRN and SNILS. How can I get confirmation of this?
- Good afternoon! The OID specified by you was approved by order No. 795 of the FSB of Russia of December 27, 2011.
The circle is closed, we believe that the test was carried out successfully.
We continue to study the Order of the Federal Security Service of the Russian Federation of December 27, 2011 No. 795 and draw attention to the fact that the filling in of fields and their attributes depends on the owner of a qualified certificate - a natural or legal person. For example, the description of filling in the attribute commonName (common name):
As the value of this attribute of the name, you should use a text string containing the name, surname and patronymic (if any) - for an individual, or the name - for a legal entity. The object identifier of the commonName attribute type is 2.5.4.3.
In our case (Komarov_Aleksey_Petrovich_2017-03-31_a2ba20c4.cer) the value of the commonName attribute is the string “Committee on Natural Resources of the Leningrad Region”, therefore, the certificate holder is a legal entity.
For a legal entity, we establish the following correspondence of object identifiers (not all selectively interesting for us) to attribute types:
2.5.4.3 – 2.5.4.8 - 1.2.643.3.131.1.1 – 1.2.643.100.1 – 1.2.643.100.3 – 1.2.840.113549.1.9.1 – Step 3. Development of the parser X.509 certificate in #
It so happened that we are developing in C #, so the example of the parser will be in C #, nothing personal and no holivar.
For simplicity, we formalize the problem as follows. Given: file of a qualified certificate in the system of restrictions CER (Canonical encoding rules). Required: parse (parse) the certificate and extract the values of TIN, SNILS and OGRN from the subject field (Subject).
For the first sketches, we refer to the capabilities of the System.Security.Cryptography.X509Certificates namespace:
using System.IO; using System.Security.Cryptography.X509Certificates; using System.Diagnostics; namespace X509Parser { class Program { static void Main(string[] args) { string fileName = @"c:\Komarov_Aleksey_Petrovich_2017-03-31_a2ba20c4.cer"; X509Certificate cert = new X509Certificate(File.ReadAllBytes(fileName)); Debug.Print(" : {0}", cert.GetSerialNumberString()); Debug.Print(" : {0}", cert.GetExpirationDateString()); Debug.Print(": {0}", cert.Subject); } } } At the output we get:
: 009EB0F73ACAB8D297E711FE15F749631C : 31.03.2018 13:28:10 : CN= , SN=, G= , C=RU, S=78 .-, L=-, STREET="., .4", O= , OU= , T= , OID.1.2.643.100.1=1077847192609, OID.1.2.643.100.3=07311996668, OID.1.2.643.3.131.1.1=007842354966, E=ap_komarov@lenreg.ru The X509Certificate.Subject property returns the subject name of the certificate of type string.
At first glance, it is possible to stop with simple regular expressions ( example ) to select the values of interest from the row, knowing their OIDs and types of values. But agree, the elegance of such a decision is clearly not enough. In addition, the installed cryptographic provider can replace OID codes with symbolic notation, which will lead to unnecessary complication of the code.
We try further, carefully review the .NET class library in search of a suitable solution. After several attempts to access the subject field as a sequence of bytes, it becomes clear that using standard tools of the .NET platform, it is quite inconvenient to implement viewing the certificate structure with the ability to search by OIDs.
StackOverflow gives a hint - use third-party libraries, choose the most quoted - BouncyCastle .
The library is connected in one click by adding reference to the project. The proposed level of abstraction allows you to intuitively view data in the format of ASN.1. It remains only to clarify the “offset” of the values of interest to us relative to the beginning of the certificate file in order to correctly specify the position for the parser.
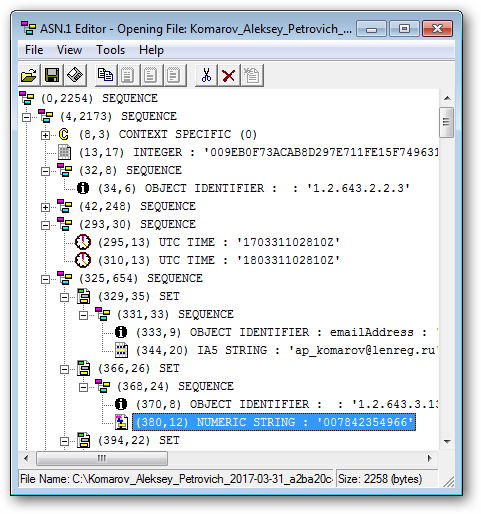
Open the certificate in the ASN.1 Editor and set the correspondence with the certificate structure:
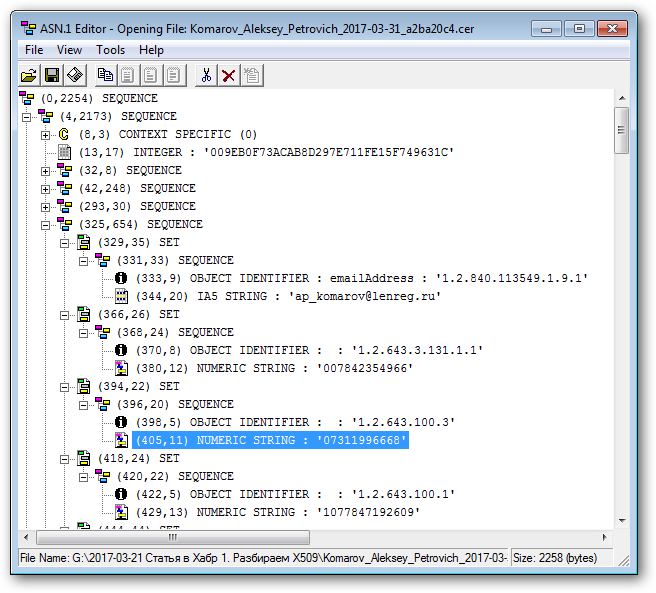
(0, 2254) SEQUENCE - root sequence, in brackets hereinafter (offset, length) (4, 2173) SEQUENCE - certificate (8, 3) CONTEXT SPECIFIC - Certificate Version (13, 17) INTEGER - serial number (32, 8) SEQUENCE - the signature algorithm identifier (42, 248) SEQUENCE - publisher name (293, 30) SEQUENCE - period of validity (325, 654) SEQUENCE - the name of the subject
We are interested in the “Name of the Subject” field, in which the values of the TIN, SNILS and OGRN are recorded. If you look closely at the picture, you can draw the following conclusion: the Subject Name field (325, 654) SEQUENCE is a sequence (SEQUENCE) of sets (SET) consisting of sequences (SEQUENCE) of key / value pairs.
In accordance with this logic, we implement the parser:
using System.Diagnostics; using System.IO; using Org.BouncyCastle.Asn1; using Org.BouncyCastle.X509; namespace X509Parser { class Program { static void Main(string[] args) { // 27.12.2011 №795 string fileName = @"c:\Komarov_Aleksey_Petrovich_2017-03-31_a2ba20c4.cer"; X509CertificateParser parser = new X509CertificateParser(); X509Certificate cert = parser.ReadCertificate(File.ReadAllBytes(fileName)); Debug.Print(" : {0}", cert.SerialNumber.ToString(16).ToUpper()); Debug.Print(" : {0}", cert.NotAfter.ToString("dd.MM.yyyy")); // subject = SEQ of SET of SEQ of {OID/value} DerSequence subject = cert.SubjectDN.ToAsn1Object() as DerSequence; foreach (Asn1Encodable setItem in subject) { DerSet subSet = setItem as DerSet; if (subSet == null) continue; // SET - SEQ of {OID/value} DerSequence subSeq = subSet[0] as DerSequence; foreach (Asn1Encodable subSeqItem in subSeq) { DerObjectIdentifier oid = subSeqItem as DerObjectIdentifier; if (oid == null) continue; string value = subSeq[1].ToString(); if (oid.Id.Equals("2.5.4.3")) Debug.Print(" / : {0}", value); if (oid.Id.Equals("2.5.4.8")) Debug.Print(" : {0}", value); if (oid.Id.Equals("1.2.643.3.131.1.1")) Debug.Print(": {0}", value); if (oid.Id.Equals("1.2.643.100.1")) Debug.Print(": {0}", value); if (oid.Id.Equals("1.2.643.100.3")) Debug.Print(": {0}", value); if (oid.Id.Equals("1.2.840.113549.1.9.1")) Debug.Print(" : {0}", value); } } } } } We look at the conclusion, agree:
: 9EB0F73ACAB8D297E711FE15F749631C : 31.03.2018 : ap_komarov@lenreg.ru : 007842354966 : 07311996668 : 1077847192609 : 78 .- / : Problem solved.
Summarizing
So, summing up the work done, we:
- We have dealt with the structure of X.509 qualified certificates that fall within the scope of the Federal Law "On Electronic Signature".
- We learned that the Order of the Federal Security Service of the Russian Federation No. 795 defines additional attributes - TIN, SNILS, OGRN and others. The corresponding object identifiers (OID) are also indicated here.
- Developed a parser for X.509 certificates in C # with the ability to extract fields and their attributes with given object identifiers. The BouncyCastle library added simplicity to the solution.
There was an error in the time calculations - instead of the planned several hours, I had to sort it all day. And two more days on preparation of research for Habr.
Thanks for attention!
List of sources
- X.509 Specification
- Federal Law “On Electronic Signature” of April 06, 2011 No. 63-FZ
- Order of the Federal Security Service of the Russian Federation dated December 27, 2011 No. 795 “On approval of requirements for the form of a qualified electronic signature verification key certificate”
- Official register of object identifiers OID
- National Register of Object Identifiers OID
- Survival Guide - TLS / SSL and SSL Certificates (X.509)
- ASN.1 in simple terms (REAL type encoding)
- Parse the x.509 certificate
- Electronic signature in simple words
- BouncyCastle Library
Source: https://habr.com/ru/post/325998/
All Articles