Security Week 14: Hacking a bank with a Brazilian scale, ATMs throw money in bitch, 54 hours Mirai
 Do you know, friends, that antivirus analysts love more than anything else? Tell each other scary stories. So, for our annual analyst congress, Fabio Assolini and Dmitry Bestuzhev prepared a real crypot. Can you imagine an old respected bank with a capitalization of 25 yards of non-rubles and 500 branches, compromised from top to bottom? All of its 36 domains and the mail server were also infected, and they poured malware on all users.
Do you know, friends, that antivirus analysts love more than anything else? Tell each other scary stories. So, for our annual analyst congress, Fabio Assolini and Dmitry Bestuzhev prepared a real crypot. Can you imagine an old respected bank with a capitalization of 25 yards of non-rubles and 500 branches, compromised from top to bottom? All of its 36 domains and the mail server were also infected, and they poured malware on all users.At first it looked like an ordinary hacking site. You come in to see, say, the rates on deposits, and along the way you open the frame leading to the host with the malware. But when analysts began to dig, it turned out that the bank had such surprises everywhere, literally on all resources: on the Internet bank, on the investment portal, on the mobile website, and so on. And it was not just an infection, but an interactive attack - having understood that their activity was detected, the hackers cut down the bank’s mail server. Apparently, in order to make it more difficult for clients of the bank, its domain registrar and DNS provider to notify.
The captured malware contained eight modules, including an update module, a tool for stealing Exchange credentials and an address book, as well as a module for managing an Internet bank. All components are knocked on a command server located in Canada. By the way, one of the modules was initially a legitimate utility for removing rootkits from the system - hackers used it to demolish antivirus programs from compromised machines.
There was a double profit at the exit: not only did the guys could interfere in the operations of the clients of the hacked bank, they also infected the clients' machines, gaining access to their accounts in other banks. They also stole card billing data - for example, some bank sites were replaced with phishing pages with forms for entering card numbers and other payment information. An SSL certificate for phishing pages was issued to Let's Encrypt. Everything is as it should be: fast, free, automatically. And the fact that the certificate is missing information about the organization, the owner - well, who in Brazil care about such details?
')
Finally, the villains managed to take control of the DNS used by the bank, for which several phishing emails were enough. The diagnosis is obvious: due to the lack of a modern multi-level information security system, the bank and its customers have completed in full.
Fileless file gutted ATMs and disappears
News Research The title is not quite accurate - the ATMs in this story were gutted more or less traditional Trojans, but their infection was carried out with the help of a fileless file entrenched in the bank’s network. Fileless attack is difficult to detect and investigate. However, the experts still managed to find something.
In the memory of one of the AD-controllers found Meterpeter, a module for Metasploit. Presumably, cybercriminals used PowerShell scripts, NETSH and Mimikatz, which are not stored in files on infected machines, and the hackers cleaned up other traces.
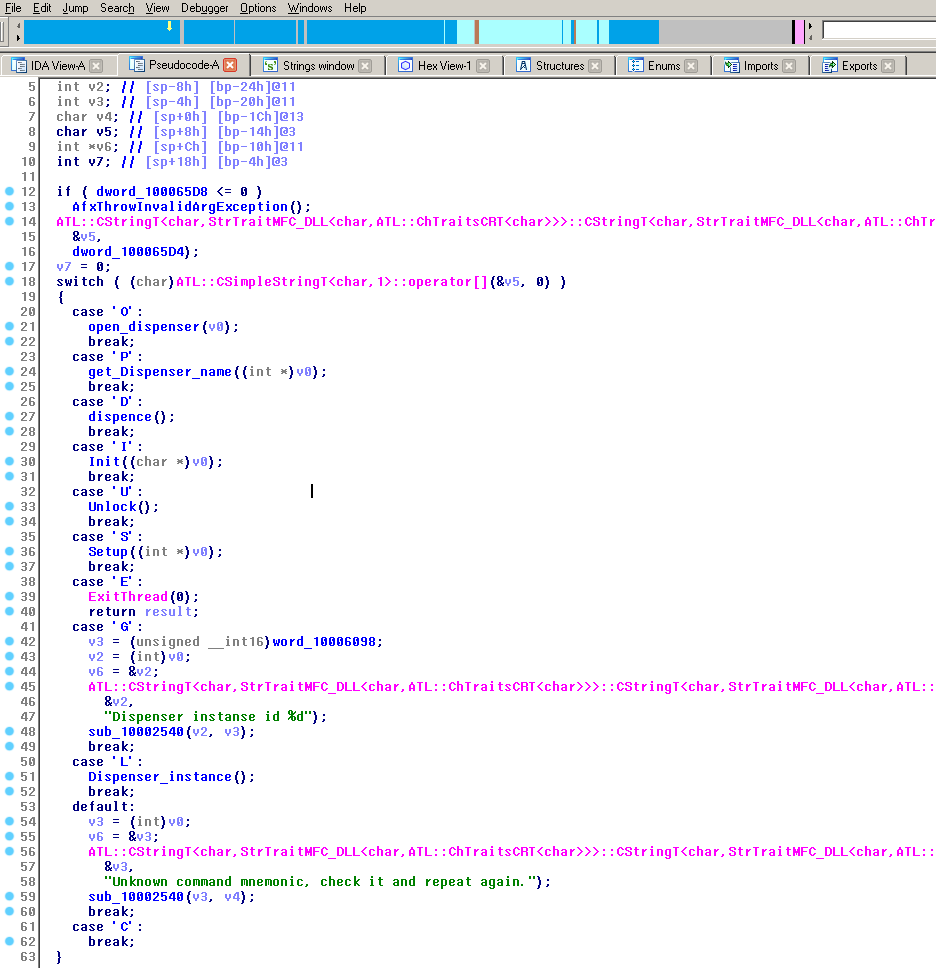
Having detected and infected the necessary computer in the bank, the attackers opened a RDP connection to the ATM and introduced the ATMitch Trojan through it. After starting at ATM, ATMitch read its command.txt command file containing a single character and executed the corresponding command:
'O' - open dispenser (money dispenser)
'D' - give money
'I' - Initialize the XFS library
'U' - Unlock XFS
'S' - Installation
'E' - Logout
'G' - Get dispenser identifier
'L' - Set dispenser identifier
'C' - Cancel

Having executed the command, the Trojan recorded the result in the log and deleted command.txt.
It must be said that such a hardware does nothing at all with ATM money, because its computer interacts with the periphery through the standard XFS software interface, which has been well studied by black hats. In this case, the Trojan gave all the money from the tapes and removed itself from the device. The one who was at this moment near the ATM was very lucky. Although, of course, it was not a casual passer-by, but a bitch to which, according to the log, the malvar addressed.
[Date — Time] [%d %m %Y — %H : %M : %S] > Entering process dispense. [%d %m %Y — %H : %M : %S] > Items from parameters converted successfully. 4 40 [%d %m %Y — %H : %M : %S] > Unlocking dispenser, result is 0 [%d %m %Y — %H : %M : %S] > Catch some money, bitch! 4000000 [%d %m %Y — %H : %M : %S] > Dispense success, code is 0 Due to a strange mistake, ATMitch did not manage to delete his log, and this gave the researchers a clue. Based on the analysis of the log data, it was possible to create rules for Yara, with which they found a sample.
It’s not at all news that ATMs still work for the most part under outdated Windows XP, the holes of which can be compared to the tunnel under the English Channel in size and frequency of their use. And yet the use of at least the same waisting would not allow Malvari to start.
Mirai-botnet conducted a 54-hour DDoS attack
News Research The sect of witnesses Mirai continues to grow by leaps and bounds. This time, some fans of the Internet of things have collected a botnet from 9793 IP cameras, routers and video recorders of surveillance systems. Apparently, these were bored students who did not find a better use for their botnet than to check the website of an American college for 54 hours in a row. Wow, someone's parents found out about the deduction of the kiddie three days later!

The organizers did not split hairs, and chose an HTTP attack — the bots contacted the web server 30,000 times a second, which, of course, could not withstand any college. The young talents had the skills to remake in their version the hard-coded user agent. However, by all indications, it was the same good old Mirai.

Antiquities
"RedX-796"
Non-resident non-dangerous virus. Typically infects .COM files in the current directory and in directories marked in the PATH. Depending on the number of affected files, it is shown by a rather funny video effect - the picture passes through the screen to the sound of a siren from left to right:
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 81.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/325972/
All Articles