From Root CA to User Authorization in nginx + apache. Part 1. Create a Root & Intermediate Certificate Authority
Good time, Habrayuzer!
I want to share with you the idea of passwordless authentication. Recently I climbed through the sites of certification centers and came across an interesting thing. The CA uses certificate authentication instead of a password. I think this is convenient, for a company, and not for ordinary Internet sites where ordinary users gather, but it would be nice to enter the AD (admin center of the site).
I offer just such a certification structure inside the company.
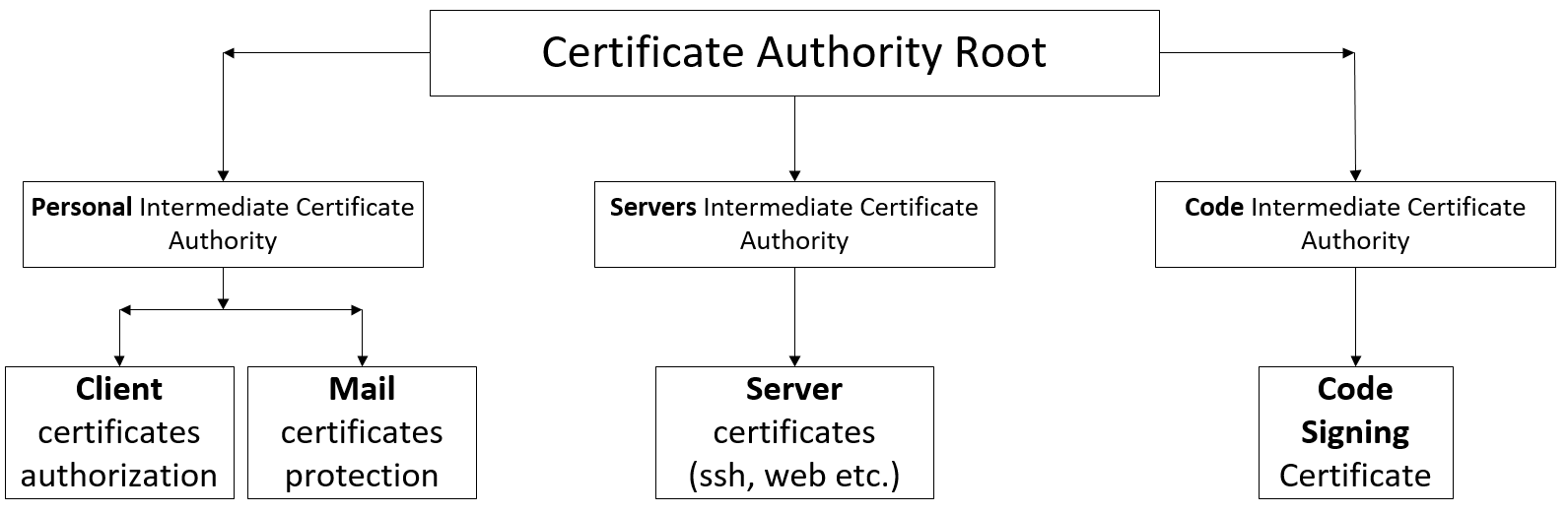
')
Conditionally we call the company CertService with the domain name CytService.info We also know that there are different departments, but we will not touch them. Now let's deal with the directory structure and talk about the openssl configuration.
Our main directory is / root / ca. But inside her already see the following:
Section [ca] is required. We will not bother with him and tell him that we want our section by default.
In the [CA_default] section, set the default values. First, write the paths of the main directories
Go ahead and specify now certain parameters.
We’ll write the policies we mentioned in a note
Here we will not stop, because everything is already written earlier. And I will tell about fields a little bit later.
Parameters from the [req] section apply when creating certificates or signing certificates for a certificate.
What can I say here:
As we have said, here we list the fields that we need for the certificate.
With this all, now we go further.
The next few sections are extensions that can be used to create certificates. For example, when passing an argument with the command -extensions root_ca, the [root_ca] section will be used.
For the root certificate, our section will be called root_ca.
Client (for authentication and mail)
Server
To sign the code
The rest (more on that later)
We have prepared the basic configuration, now you can go to the console too :)
Create working directories
Expose all private rights to 400
Create configuration files
Ready configurations
Create our underdo databases
Create a root private key
Create a root certificate
We check the validity of the certificate
We create intermediate and sign them with root
We check validation
Go ahead and create a certificate chain
Client (use -extensions user_cert )
Server (use -extensions server_cert )
For code (use -extensions code_cert )
In the next article, we will revoke certificates and configure OCSP.
Sources and more about openssl parameters:
x509v3_config (English)
Create the root pair (English)
GitHub (ready)
PS I tried to describe the necessary moments of creating SSL certificates in as much detail as possible. I understand that there are many such articles, but often the articles are not complete. Therefore, I will try to make a normal full version in several parts. I think there will be not enough defects, I will be glad to your remarks, habrayuzer.
I want to share with you the idea of passwordless authentication. Recently I climbed through the sites of certification centers and came across an interesting thing. The CA uses certificate authentication instead of a password. I think this is convenient, for a company, and not for ordinary Internet sites where ordinary users gather, but it would be nice to enter the AD (admin center of the site).
I offer just such a certification structure inside the company.
')
Conditionally we call the company CertService with the domain name CytService.info We also know that there are different departments, but we will not touch them. Now let's deal with the directory structure and talk about the openssl configuration.
Directory structure on the CA server
Our main directory is / root / ca. But inside her already see the following:
- RootCA - root certificate directory
- Config - configurations for OpenSSL
- PersonIntermediateCA - intermediate certificate for user certificates
- ServerIntermediateCA - intermediate certificate for server certificates
- CodeIntermediateCA - intermediate certificate for code signing certificates
- Inside these directories have their own, look at them: (/ root / ca / {RootCA, PersonIntermediateCA, ServerIntermediateCA, CodeIntermediateCA})
- certs - directory for certificates
- crl - directory for revoked certificates
- csr - this directory is only for intermediate certificates (requests to create a certificate)
- private (chmod 400) - directory for private keys
- index.txt - certificate text database file
- serial — The serial number of the next certificate.
- crlnumber - serial number for the next certificate revocation
- Slightly dealt with the directories and files that we need. Now let's move on to writing parts of the OpenSSL configuration for our CA
Configuration sections for OpenSSL
[ca]
Section [ca] is required. We will not bother with him and tell him that we want our section by default.
[ ca ] default_ca = CA_default [CA_default]
In the [CA_default] section, set the default values. First, write the paths of the main directories
[ CA_default ] # , # ( ) dir = /root/ca/RootCA certs = $dir/certs new_certs_dir = $certs private = $dir/certs crl_dir = $dir/crl serial = $dir/serial database = $dir/index.txt RANDFILE = $dir/private/.rand - dir is exclusively our variable in order to save us time. Here we specify let it be to the main directory of the CA for which the configuration will be intended;
- certs - this variable for certificates, we specify our folder to it;
- new_certs_dir is the same as certs (in different versions of OpenSSL there are different variables for certificates), therefore we specify both;
- private - in this variable we transfer the place of our private directory, in the description of directories, we have already said that we keep private keys here;
- crl_dir - as already said, there will be a path to the directory of revoked certificates;
- serial - we specify our file serial;
- database - text database, our index.txt;
- RANDFILE - random file for random data.
Go ahead and specify now certain parameters.
# , , # ( - ) private_key = $private/RootCA.key.pem certificate = $certs/RootCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/RootCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_root - private_key and certificate - specify the path and file names of the private key and certificate, respectively. These parameters are used when we sign a certificate. At the moment, the root certificate is specified (we will sign intermediate ones);
- crlnumber - as stated, the path to the file with the serial number for a response;
- crl - certificate revocation file (not sure if the statement is correct);
- crl_extensions - the extension that is called during crl;
- default_crl_days - the number of days before the new CRL;
- default_md - hashing algorithm;
- name_opt and cert_opt are responsible for the output and output format of information on the certificate being checked;
- default_days - how many days the certificate will be valid;
- preserve - make the final certificate match the order of the fields with the root (or intermediate);
- policy - the policy for signing the certificate;
policy
policy - we will specify different values in different configurations. We will have several: policy_root, policy_intermediate_person, policy_intermediate_server, policy_intermediate_code.
policy_root - will be in the configuration for the root certificate, and it will have strict rules for signing intermediate ones.
policy_intermediate - and this section of the rules will be in the intermediate configuration, and the signature rules will not be so strict.
Options:
- match - Required, full match with Root CA
- supplied - Required, not necessarily a coincidence with Root CA
- optional - Optional field
We’ll write the policies we mentioned in a note
[ policy_root ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = supplied commonName = supplied emailAddress = optional subjectAltName = optional [ policy_intermediate_person ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = optional [ policy_intermediate_code ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional subjectAltName = optional [ policy_intermediate_server ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = supplied Here we will not stop, because everything is already written earlier. And I will tell about fields a little bit later.
[req]
Parameters from the [req] section apply when creating certificates or signing certificates for a certificate.
[ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca What can I say here:
- default_bits — The default RSA key size
- distinguished_name - this parameter will cause a section in which the parameters for the certificate are listed;
- string_mask - in what encoding will be our text in the certificate;
- default_md is the same hashing algorithm;
- x509_extensions - the section is indicated here, which will be used when the x509 parameter is specified;
[req_distinguished_name]
As we have said, here we list the fields that we need for the certificate.
[ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info - countryName - country, country code A2 (ISO) www.worldatlas.com/aatlas/ctycodes.htm ;
- localityName - City;
- 0.organizationName - the name of the organization;
- organizationalUnitName - department \ department of the organization;
- commonName - For servers, this is the domain name, SP address. for software - the name of the application, for the user - name For root and intermediate their name;
- emailAddress - mail;
- subjectAltName - alternative name (other domains, mail, etc.);
- _default - sets the default value;
With this all, now we go further.
Extensions
The next few sections are extensions that can be used to create certificates. For example, when passing an argument with the command -extensions root_ca, the [root_ca] section will be used.
For root certificate
For the root certificate, our section will be called root_ca.
[ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign - subjectKeyIdentifier - the identifier of the subject. It can be a hexadecimal string (hex) or a hash (hash);
- authorityKeyIdentifier - this parameter allows only two keyid and issuer values. Keyid - copies the keyword identifier from the parent, if it fails to get and is always, then an error will be returned. The issuer copies the issuer and the serial number from the certificate with which it is signed. It works only if the keyid is not working;
- basicConstraints - CA - if true, then allows to be an issuer, false - not (for clarification: issuer - emitat (signer), ie, can sign certificates);
- keyUsage - what the certificate can do;
Key value keyUsage | Description
- - serverAuth SSL / TLS web server authentication.
clientAuth SSL / TLS web client authentication.
codeSigning Code signing.
emailProtection Email Protection (S / MIME).
timeStamping Trusted time stamp.
msCodeInd Microsoft Individual code substitution (authentication).
msCodeCom Microsoft Commercial Code Signing (Authentication).
msCTLSign Microsoft Trusted Signature List.
msSGC Microsoft Server cryptographic protection.
msEFS Microsoft File System Encryption.
nsSGC Netscape Server Gated Crypto.
For intermediate certificates
[ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign Important note:
The parameter basicConstraints contains "pathlen: 0". pathlen indicates the maximum number of CAs that may appear below this in the chain. Therefore, if you have a zero point CA, it can only be used for signing end-user certificates, not for further CAs.
That is, if you want to create intermediate certificates for departments, and then for users, then pathlen will have to be equal to 1, and also recommend creating an extension for such certificates with the parameter equal to zero.
For end certificates
Client (for authentication and mail)
[ user_cert ] # ( basicConstraints = CA:FALSE nsCertType = client, email nsComment = "Client certificates" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment extendedKeyUsage = clientAuth, emailProtection - nsCertType - certificate type. Valid values: client, server, email, objsign, reserved, sslCA, emailCA, objCA;
- nsComment - a comment to the certificate;
Server
[ server_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Server Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth To sign the code
[ code_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Code Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = digitalSignature extendedKeyUsage = codeSigning, msCodeInd, msCodeCom The rest (more on that later)
[ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning Go to the console
We have prepared the basic configuration, now you can go to the console too :)
Create working directories
mkdir -p /root/ca/config mkdir -p /root/ca/{RootCA,PersonIntermediateCA,ServerIntermediateCA,CodeIntermediateCA}/{certs,crl,newcerts,private} mkdir -p /root/ca/{PersonIntermediateCA,ServerIntermediateCA,CodeIntermediateCA}/csr Expose all private rights to 400
chmod 400 /root/ca/RootCA/private chmod 400 /root/ca/PersonIntermediateCA/private chmod 400 /root/ca/ServerIntermediateCA/private chmod 400 /root/ca/CodeIntermediateCA/private Create configuration files
touch /root/ca/config/RootCA.cnf touch /root/ca/config/PersonIntermediateCA.cnf cp touch /root/ca/config/ServerIntermediateCA.cnf cp touch /root/ca/config/CodeIntermediateCA.cnf RootCA.cnf
[ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/RootCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/RootCA.key.pem certificate = $certs/RootCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/RootCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_root [ policy_root ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = supplied commonName = supplied emailAddress = optional subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning PersonIntermediateCA.cnf
[ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/PersonIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/PersonIntermediateCA.key.pem certificate = $certs/PersonIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/PersonIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_person [ policy_intermediate_person ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ user_cert ] basicConstraints = CA:FALSE nsCertType = client, email nsComment = "Client certificates" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment extendedKeyUsage = clientAuth, emailProtection [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning ServerIntermediateCA.cnf
[ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/ServerIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/ServerIntermediateCA.key.pem certificate = $certs/ServerIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/ServerIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_server [ policy_intermediate_server ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = supplied [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ server_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Server Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning CodeIntermediateCA.cnf
[ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/CodeIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/CodeIntermediateCA.key.pem certificate = $certs/CodeIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/CodeIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_code [ policy_intermediate_code ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ code_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Code Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = digitalSignature extendedKeyUsage = codeSigning, msCodeInd, msCodeCom [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning Ready configurations
Create our underdo databases
touch /root/ca/RootCA/index.txt touch /root/ca/PersonIntermediateCA/index.txt touch /root/ca/ServerIntermediateCA/index.txt touch /root/ca/CodeIntermediateCA/index.txt echo 1000 > /root/ca/RootCA/serial echo 1A00000000000000 > /root/ca/PersonIntermediateCA/serial echo 1B00000000000000 > /root/ca/ServerIntermediateCA/serial echo 1C00000000000000 > /root/ca/CodeIntermediateCA/serial echo 1000 > /root/ca/RootCA/crlnumber echo 1FA0000000000000 > /root/ca/PersonIntermediateCA/crlnumber echo 1FB0000000000000 > /root/ca/ServerIntermediateCA/crlnumber echo 1FC0000000000000 > /root/ca/CodeIntermediateCA/crlnumber We work with certificates
Create a root private key
openssl genrsa -aes256 -out /root/ca/RootCA/private/RootCA.key.pem 4096 chmod 400 /root/ca/RootCA/private/RootCA.key.pem Create a root certificate
openssl req -config /root/ca/config/RootCA.cnf \ -key /root/ca/RootCA/private/RootCA.key.pem \ -new -x509 -days 7300 -sha256 -extensions root_ca \ -out /root/ca/RootCA/certs/RootCA.cert.pem chmod 444 /root/ca/RootCA/certs/RootCA.cert.pem We check the validity of the certificate
openssl x509 -noout -text -in /root/ca/RootCA/certs/RootCA.cert.pem We create intermediate and sign them with root
# openssl genrsa -aes256 \ -out /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem 4096 chmod 400 /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem # openssl req -config /root/ca/config/PersonIntermediateCA.cnf -new -sha256 \ -key /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem \ -out /root/ca/PersonIntermediateCA/csr/PersonIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/PersonIntermediateCA/csr/PersonIntermediateCA.csr.pem \ -out /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem The remaining two intermediate
# openssl genrsa -aes256 \ -out /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem 4096 chmod 400 /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem # openssl req -config /root/ca/config/ServerIntermediateCA.cnf -new -sha256 \ -key /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem \ -out /root/ca/ServerIntermediateCA/csr/ServerIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/ServerIntermediateCA/csr/ServerIntermediateCA.csr.pem \ -out /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem # openssl genrsa -aes256 \ -out /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem 4096 chmod 400 /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem # openssl req -config /root/ca/config/CodeIntermediateCA.cnf -new -sha256 \ -key /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem \ -out /root/ca/CodeIntermediateCA/csr/CodeIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/CodeIntermediateCA/csr/CodeIntermediateCA.csr.pem \ -out /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem We check validation
openssl verify -CAfile /root/ca/RootCA/certs/RootCA.cert.pem \ /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem #result: /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem: OK Go ahead and create a certificate chain
certificate chain - we need this chain when the client does not have a root or intermediate certificate.
If we haven't added anything to AD, then the client needs a final + intermediate + root bundle.
If we add only root certificate to AD, then we need the certificate chain in the bundle final + intermediate.
If intermediate certificates are also added to AD, then we do not need a certificate chain.
cat /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/PersonIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/PersonIntermediateCA/certs/ca-chain.cert.pem cat /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/CodeIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/CodeIntermediateCA/certs/ca-chain.cert.pem cat /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/ServerIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/ServerIntermediateCA/certs/ca-chain.cert.pem Create one certificate for each unit
Client (use -extensions user_cert )
openssl genrsa -aes256 -out /root/ca/PersonIntermediateCA/private/User1.key.pem 2048 chmod 400 /root/ca/PersonIntermediateCA/private/User1.key.pem openssl req -config /root/ca/config/PersonIntermediateCA.cnf \ -key /root/ca/PersonIntermediateCA/private/User1.key.pem \ -new -sha256 -out /root/ca/PersonIntermediateCA/csr/User1.csr.pem openssl ca -config /root/ca/config/PersonIntermediateCA.cnf \ -extensions user_cert -days 375 -notext -md sha256 \ -in /root/ca/PersonIntermediateCA/csr/User1.csr.pem \ -out /root/ca/PersonIntermediateCA/certs/User1.cert.pem chmod 444 /root/ca/PersonIntermediateCA/certs/User1.cert.pem Server (use -extensions server_cert )
openssl genrsa -aes256 -out /root/ca/ServerIntermediateCA/private/certservice.info.key.pem 2048 chmod 400 /root/ca/ServerIntermediateCA/private/certservice.info.key.pem openssl req -config /root/ca/config/ServerIntermediateCA.cnf \ -key /root/ca/ServerIntermediateCA/private/certservice.info.key.pem \ -new -sha256 -out /root/ca/ServerIntermediateCA/csr/certservice.info.csr.pem openssl ca -config /root/ca/config/ServerIntermediateCA.cnf \ -extensions server_cert -days 375 -notext -md sha256 \ -in /root/ca/ServerIntermediateCA/csr/certservice.info.csr.pem \ -out /root/ca/ServerIntermediateCA/certs/certservice.info.cert.pem chmod 444 /root/ca/ServerIntermediateCA/certs/certservice.info.cert.pem # - openssl rsa -in /root/ca/ServerIntermediateCA/private/certservice.info.key.pem -out /root/ca/ServerIntermediateCA/private/certservice.info.keynopass.pem chmod 400 /root/ca/ServerIntermediateCA/private/certservice.info.keynopass.pem For code (use -extensions code_cert )
openssl genrsa -aes256 -out /root/ca/CodeIntermediateCA/private/Calculator.key.pem 2048 chmod 400 /root/ca/CodeIntermediateCA/private/Calculator.key.pem openssl req -config /root/ca/config/CodeIntermediateCA.cnf \ -key /root/ca/CodeIntermediateCA/private/Calculator.key.pem \ -new -sha256 -out /root/ca/CodeIntermediateCA/csr/Calculator.csr.pem openssl ca -config /root/ca/config/CodeIntermediateCA.cnf \ -extensions code_cert -days 375 -notext -md sha256 \ -in /root/ca/CodeIntermediateCA/csr/Calculator.csr.pem \ -out /root/ca/CodeIntermediateCA/certs/Calculator.cert.pem chmod 444 /root/ca/CodeIntermediateCA/certs/Calculator.cert.pem In the next article, we will revoke certificates and configure OCSP.
Sources and more about openssl parameters:
x509v3_config (English)
Create the root pair (English)
GitHub (ready)
PS I tried to describe the necessary moments of creating SSL certificates in as much detail as possible. I understand that there are many such articles, but often the articles are not complete. Therefore, I will try to make a normal full version in several parts. I think there will be not enough defects, I will be glad to your remarks, habrayuzer.
Source: https://habr.com/ru/post/325956/
All Articles