“Shaw, again?” Or hacking transport Citycard (Nizhny Novgorod)
I hasten to warn readers: This article is written only for information, and in no way calls to engage in fake travel tickets, as this contradicts article 327 of the Criminal Code of the Russian Federation. The author is not responsible for any illegal actions committed by people using the information from this article.
I am an ordinary girl, relatively recently working in the field of IT, I have no knowledge of hacking and hacking. But inspired by articles on Habré about hacking the Troika and Plantain transport cards (which are no longer available, the authors of Ammonia and antoo ), I decided to tell you about my own experience of hacking Citicart transport cards that operate in Nizhny Novgorod.

')
I’ll say right away that I’m not a hacker and not a cracker, but a simple front-end developer, my knowledge of working with PCs, if we discard knowledge in front-end development, can be described as an “experienced user”.
I did not develop special applications, as the authors of the mentioned articles did, but I will show you how you can easily hack transport maps with affordable means. Hacking methods have been known for a long time (years 5-7 exactly).
If I, as a developer, used the old versions of frameworks with known vulnerabilities, I would have long lost my employer head, but this, in my opinion, does not apply to transport system developers. Perhaps this is due to the low knowledge of the developers themselves.
But back to hacking. So, first things first.
I carried out all the actions I described last fall, but as far as I know, everything works now.
So, I have an inexpensive smartphone with NFC. I once bought Citycard transport cards (it turned out that I had several of them — sometimes I forgot the card at home or at work and I had to buy a new one).

I downloaded the official app of the Mifare NXP Taginfo card maker and scanned my shipping card:

It turned out that the card is based on the Mifare Plus S chip, but most importantly, it works in security mode No. 1. And this means that in essence it is a simple Mifare Classic card that is easily cracked.
I downloaded the wonderful Mifare Classic Tool application on Google Play and scanned the transport map with standard keys:
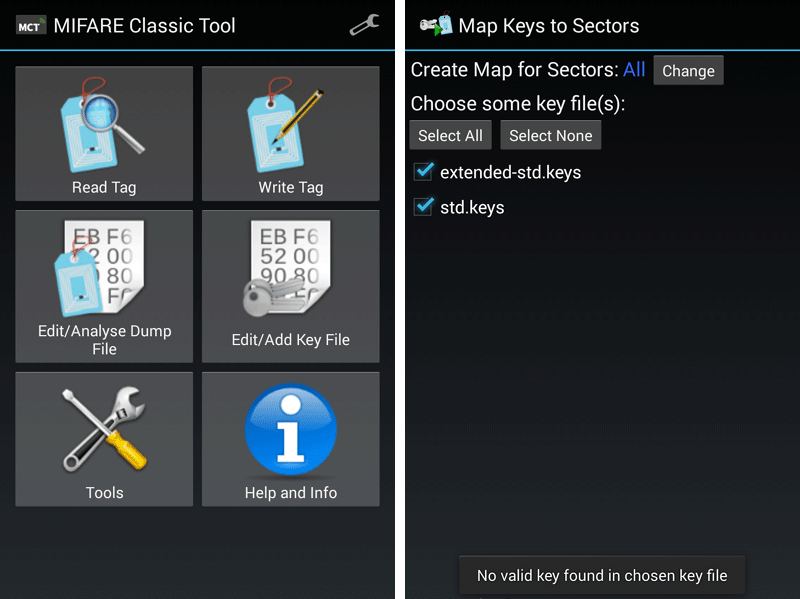
Here I was disappointed - none of the well-known keys came up. Accordingly, it was not possible to use hacking in the manner described in the article on “Plantain”.
“Wait a minute,” I thought, “but you can try the method as described in the Troika hacking article.
Indeed, Citicard also has an application from Google Play, which allows you to check the balance of the card, and subsequently screwed up the opportunity and replenish the card.

I downloaded and installed this application. But now I have a dilemma: the keys to the card are protected either in the application itself, or “arrive” from the server. Decompiling Android applications is simple enough, but I don't understand this very well.
Surely, a more or less intelligent developer can do this quite easily. I did not possess such skills and turned to my brother, who is engaged in repair of intercoms, I thought he had a familiar programmer, but he suggested a more elegant and simple solution.
By that time, he had received a fee from Kickstarter , which allows him to peek at the protocol between the reader and the card. It turns out that they began to use key chains in intercoms, inside which the same Mifare chip was sewn up, and he needed this board for some cases related to these key chains (I did not go into details).
So, he took his fee, put it to my smartphone, which acted as a reader, and the transport card itself acted as a card, and removed the data exchange log between the reader and the card.
Then the question arose what to do with the received log. But a short search on the Internet led to a utility called crapto1gui. Links will not lead, it is easy enough and so.
I provide the screenshot of the utility below (taken from one of the sites on the Internet, so the data there is not real, which we used).
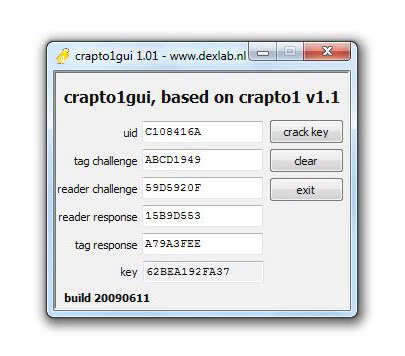
In general, it is enough to insert the necessary chunks of the log into this utility and the 6-byte key is instantly calculated. I myself was surprised how easy it was, the most difficult thing was to copy the necessary parts from the log and paste them into the appropriate fields of the program.
Then I opened the Mifare Classic Tool (MCT) application too, inserted the received key into the application, and this time the contents of the 0th and 8th sectors were displayed to me.
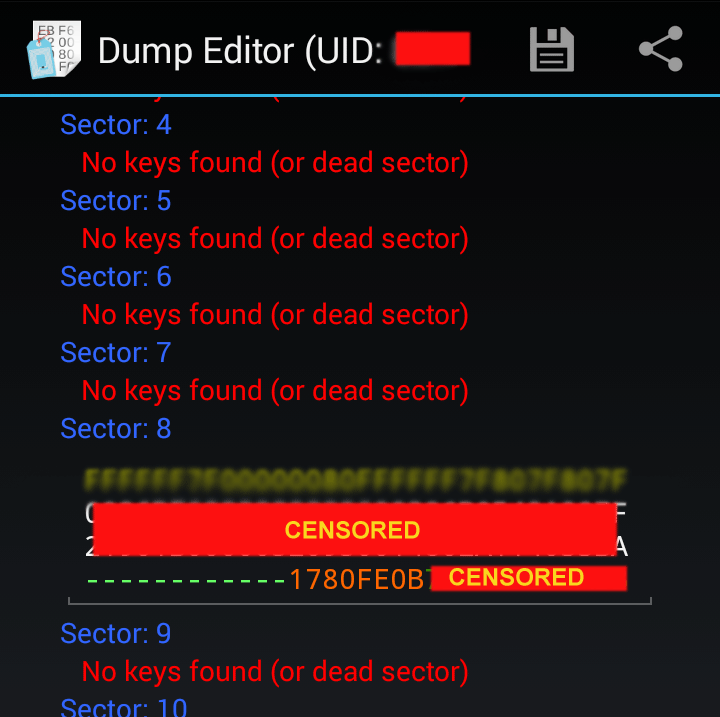
In the zero sector, basically there were only zeros, but in the eighth there were some data, from which I concluded that the data on the transport card are stored in the 8th sector (as in the Troika card, is it really the same the developer?), and the resulting key was the key B (the sector has two keys A and B).
Further, for the sake of interest, I received with the help of the open-source utility libnfc and the reader of contactless cards and all the other keys to the card (for more information, see the article on “Plantain” - I also used this method. It is also described on libnfc).
Using the obtained keys, I tried to read the contents of another transport card. It turned out that key A was the same, but key B was not. But with the help of the mentioned utility it also turned out to be easy to get.
Then I began to explore the contents of the transport card. The 8th sector consists of 4 blocks of 16 bytes each. With the help of MCT, it became clear that the first block is the so-called. Value block. First of all, the thought came that the balance of the card is stored in this block. With the help of MCT, it was possible to decode it - it contained the number 2147483647. It clearly did not look like the balance of the card, even if it was in kopecks.
Then I toured this map and, after reading the contents of the sector, I discovered that the value had not changed, but the contents of the other blocks had changed. From which it was concluded that the card balance is stored in them.
There was no special desire to parse the contents of the map, because I wanted to try the so-called replay attack (I later learned what it was called correctly).
In the morning before the trip to the subway, I saved the contents of the eighth sector, put a map to the turnstile and went to work. In the afternoon, having gone on business, with the help of MCT, I recorded the previous state of the map and tried to drive the subway ... And I did it!

(the picture is not mine - I didn’t want to attract attention at all)
So I realized that this way you can do the "eternal travel card". I decided to play around a bit and wrote down the contents of the transport card sector on the intercom keychain.

(I used the same key ring to write a transport card to it)
I tried to go through the turnstile, putting the key fob, but then I was disappointed - the key fob, to my surprise, did not work. I thought that my transport card was blocked (after all, the key fob was its clone), but when I applied the “original” (transport card) I managed to get through the turnstile.
I talked to my brother, wanted to find out what he thinks about this, and he told me that each card and keychain has its own identification number. Apparently, my “clone” was not complete, and the content in the map was somehow tied to its number.
But it turned out that there was a way out of this situation: there are some types of key chains that look exactly the same, but they can change their number (conventional transport cards will not do this). Moreover, MCT has such a function of rewriting a number, since it is stored in the first block of the zero sector.
True, for some reason, changing the number using MCT did not work. But it turned out to do this with the help of a reader and all the same libnfc.
This time I had a complete clone of the transport card in the form of a keychain, because even the number was the same. I tried to go through the turnstile on the intercom keychain, and I did it easily. I did not dare to put a key on the bus, because the aunt could have been very surprised, but the “eternal” transport card worked without any problems.
So, summing up, we can say the following: transport cards for fare payment in Nizhny Novgorod are just as easily cracked as Troika (Moscow) and Podorozhnik (St. Petersburg).
Even I, a girl, not having special knowledge, but able to download Android applications and use Google and Yandex search, was able to do it using available tools and programs and utilities available in the public domain (if I were a developer, it would probably be even easier , although it’s much easier ...) Yes, it took me some time to search the Internet and study the forums, but everything turned out to be very simple.
I want to note right away, anticipating the questions that no damage was caused to the metro - I took into account all the trips made on the “perpetual travel card”, so the balance on the map did not spend the corresponding sum of such trips, and then destroyed the map itself.
But after all, the attackers are not so conscious, for sure they use this vulnerability and damage the urban transport. We receive regularly increasing fares (perhaps due to losses due to fake transport cards). By the way, the deposit for the transport card is 50 rubles. But exactly the same security cards Mifare Classic cost 12.5 rubles and below.
One gets the feeling that all transport systems where transport cards are used are unsafe. I do not want to argue why this is happening (this topic is not for Habr), it remains only to ask the question: who (which city) is next and when to wait for this article on Habr?
PS This story, of course, invented. All characters are fictional, all coincidences are random. Well, you get the idea ...
I am an ordinary girl, relatively recently working in the field of IT, I have no knowledge of hacking and hacking. But inspired by articles on Habré about hacking the Troika and Plantain transport cards (which are no longer available, the authors of Ammonia and antoo ), I decided to tell you about my own experience of hacking Citicart transport cards that operate in Nizhny Novgorod.

')
I’ll say right away that I’m not a hacker and not a cracker, but a simple front-end developer, my knowledge of working with PCs, if we discard knowledge in front-end development, can be described as an “experienced user”.
I did not develop special applications, as the authors of the mentioned articles did, but I will show you how you can easily hack transport maps with affordable means. Hacking methods have been known for a long time (years 5-7 exactly).
If I, as a developer, used the old versions of frameworks with known vulnerabilities, I would have long lost my employer head, but this, in my opinion, does not apply to transport system developers. Perhaps this is due to the low knowledge of the developers themselves.
But back to hacking. So, first things first.
I carried out all the actions I described last fall, but as far as I know, everything works now.
So, I have an inexpensive smartphone with NFC. I once bought Citycard transport cards (it turned out that I had several of them — sometimes I forgot the card at home or at work and I had to buy a new one).

I downloaded the official app of the Mifare NXP Taginfo card maker and scanned my shipping card:

It turned out that the card is based on the Mifare Plus S chip, but most importantly, it works in security mode No. 1. And this means that in essence it is a simple Mifare Classic card that is easily cracked.
I downloaded the wonderful Mifare Classic Tool application on Google Play and scanned the transport map with standard keys:

Here I was disappointed - none of the well-known keys came up. Accordingly, it was not possible to use hacking in the manner described in the article on “Plantain”.
“Wait a minute,” I thought, “but you can try the method as described in the Troika hacking article.
Indeed, Citicard also has an application from Google Play, which allows you to check the balance of the card, and subsequently screwed up the opportunity and replenish the card.

I downloaded and installed this application. But now I have a dilemma: the keys to the card are protected either in the application itself, or “arrive” from the server. Decompiling Android applications is simple enough, but I don't understand this very well.
Surely, a more or less intelligent developer can do this quite easily. I did not possess such skills and turned to my brother, who is engaged in repair of intercoms, I thought he had a familiar programmer, but he suggested a more elegant and simple solution.
By that time, he had received a fee from Kickstarter , which allows him to peek at the protocol between the reader and the card. It turns out that they began to use key chains in intercoms, inside which the same Mifare chip was sewn up, and he needed this board for some cases related to these key chains (I did not go into details).
So, he took his fee, put it to my smartphone, which acted as a reader, and the transport card itself acted as a card, and removed the data exchange log between the reader and the card.
Then the question arose what to do with the received log. But a short search on the Internet led to a utility called crapto1gui. Links will not lead, it is easy enough and so.
I provide the screenshot of the utility below (taken from one of the sites on the Internet, so the data there is not real, which we used).

In general, it is enough to insert the necessary chunks of the log into this utility and the 6-byte key is instantly calculated. I myself was surprised how easy it was, the most difficult thing was to copy the necessary parts from the log and paste them into the appropriate fields of the program.
Then I opened the Mifare Classic Tool (MCT) application too, inserted the received key into the application, and this time the contents of the 0th and 8th sectors were displayed to me.

In the zero sector, basically there were only zeros, but in the eighth there were some data, from which I concluded that the data on the transport card are stored in the 8th sector (as in the Troika card, is it really the same the developer?), and the resulting key was the key B (the sector has two keys A and B).
Further, for the sake of interest, I received with the help of the open-source utility libnfc and the reader of contactless cards and all the other keys to the card (for more information, see the article on “Plantain” - I also used this method. It is also described on libnfc).
Using the obtained keys, I tried to read the contents of another transport card. It turned out that key A was the same, but key B was not. But with the help of the mentioned utility it also turned out to be easy to get.
Then I began to explore the contents of the transport card. The 8th sector consists of 4 blocks of 16 bytes each. With the help of MCT, it became clear that the first block is the so-called. Value block. First of all, the thought came that the balance of the card is stored in this block. With the help of MCT, it was possible to decode it - it contained the number 2147483647. It clearly did not look like the balance of the card, even if it was in kopecks.
Then I toured this map and, after reading the contents of the sector, I discovered that the value had not changed, but the contents of the other blocks had changed. From which it was concluded that the card balance is stored in them.
There was no special desire to parse the contents of the map, because I wanted to try the so-called replay attack (I later learned what it was called correctly).
In the morning before the trip to the subway, I saved the contents of the eighth sector, put a map to the turnstile and went to work. In the afternoon, having gone on business, with the help of MCT, I recorded the previous state of the map and tried to drive the subway ... And I did it!

(the picture is not mine - I didn’t want to attract attention at all)
So I realized that this way you can do the "eternal travel card". I decided to play around a bit and wrote down the contents of the transport card sector on the intercom keychain.

(I used the same key ring to write a transport card to it)
I tried to go through the turnstile, putting the key fob, but then I was disappointed - the key fob, to my surprise, did not work. I thought that my transport card was blocked (after all, the key fob was its clone), but when I applied the “original” (transport card) I managed to get through the turnstile.
I talked to my brother, wanted to find out what he thinks about this, and he told me that each card and keychain has its own identification number. Apparently, my “clone” was not complete, and the content in the map was somehow tied to its number.
But it turned out that there was a way out of this situation: there are some types of key chains that look exactly the same, but they can change their number (conventional transport cards will not do this). Moreover, MCT has such a function of rewriting a number, since it is stored in the first block of the zero sector.
True, for some reason, changing the number using MCT did not work. But it turned out to do this with the help of a reader and all the same libnfc.
This time I had a complete clone of the transport card in the form of a keychain, because even the number was the same. I tried to go through the turnstile on the intercom keychain, and I did it easily. I did not dare to put a key on the bus, because the aunt could have been very surprised, but the “eternal” transport card worked without any problems.
So, summing up, we can say the following: transport cards for fare payment in Nizhny Novgorod are just as easily cracked as Troika (Moscow) and Podorozhnik (St. Petersburg).
Even I, a girl, not having special knowledge, but able to download Android applications and use Google and Yandex search, was able to do it using available tools and programs and utilities available in the public domain (if I were a developer, it would probably be even easier , although it’s much easier ...) Yes, it took me some time to search the Internet and study the forums, but everything turned out to be very simple.
I want to note right away, anticipating the questions that no damage was caused to the metro - I took into account all the trips made on the “perpetual travel card”, so the balance on the map did not spend the corresponding sum of such trips, and then destroyed the map itself.
But after all, the attackers are not so conscious, for sure they use this vulnerability and damage the urban transport. We receive regularly increasing fares (perhaps due to losses due to fake transport cards). By the way, the deposit for the transport card is 50 rubles. But exactly the same security cards Mifare Classic cost 12.5 rubles and below.
One gets the feeling that all transport systems where transport cards are used are unsafe. I do not want to argue why this is happening (this topic is not for Habr), it remains only to ask the question: who (which city) is next and when to wait for this article on Habr?
PS This story, of course, invented. All characters are fictional, all coincidences are random. Well, you get the idea ...
Source: https://habr.com/ru/post/325776/
All Articles