How to set up the next generation extended protection in the corporate network

Recently, we are increasingly talking about “next generation” security solutions that can provide enhanced protection for corporate networks against unknown threats, APT, cryptographers, targeted attacks and other zero-day threats. How difficult is it to configure such protection, and why is it so necessary? Consider the example of Adaptive Defense 360 .
In one of our articles, we have already discussed the effectiveness of next-generation information security solutions. Indeed, in an era of more advanced threats and attacks, which often no longer even use any malicious programs, new analytical capabilities are required, based on artificial intelligence and deep monitoring of not only all active processes as such, but also the relationships between them. This allows for a deeper and more thorough analysis, taking into account the context of the entire attack process. Such contextual analysis, among other things, makes it possible to understand: this operation is carried out by the user himself or, nevertheless, it is initiated by some process under the guise of the user.
')
Therefore, in Panda Security, we believe that current trends in the development of malware and attacks require the use of new solutions in corporate networks, combining not only traditional protection technologies, but also new advanced protection technologies, detection of unknown threats / attacks and response to them. For this reason, 1.5 years ago, the first and only cloud-based SaaS-solution Adaptive Defense 360 class EPP + EDR was launched on the market.
So, why and how is this enhanced protection configured?
Recommendations on the level of security of the IT structure of the company
Our users often ask us if you want to install extended protection on all devices in their IT infrastructure, including servers and computers in subnets and remote offices. Based on our experience and analysis of numerous real-world attacks on organizations of any type, size and field of activity, we can answer unequivocally: Yes, and this is not only necessary, but also necessary.
All endpoints and servers in a corporate network or subnet, as well as mobile devices, are at the sight of cyber criminals, who view them as a goal and means to achieve other goals in the attacked company. We strongly recommend that companies apply maximum protection for each endpoint (PC, laptop or server) in their corporate network, including all subnets and remote offices. This is the best way to prevent serious financial and reputational damage, avoid hacking systems and protect the company from any other incidents that could adversely affect the company's operations.
This recommendation is based on our experience and knowledge of the motivations of cyber criminals, whose first task is to find the most vulnerable device that could be used to access other computers and servers. Once installed on the network, their “creations” secretly begin to search for the weak link of the company to access workstations and servers - the real goals of many attacks. To do this, they are able to perform countless iterations and hidden actions to carry out their malicious actions and compromise the required server.
The only way to protect all devices is to closely monitor and control every action taken on all workstations and servers, classifying every process launched and identifying all interconnections with other processes, including legitimate processes that can help hackers to hack corporate applications and systems. / damage information.
Below are some examples of real attacks that clearly illustrate why direct protection of all network resources, including servers, office and remote workstations, is the only effective protection against cyber attacks and, most importantly, unknown threats.
Attacks on corporate servers
Each server in the corporate network is a desirable goal for each cyber criminal for various reasons:
• They have open ports and establish connections.
• Often there is no constant monitoring of server activity. Those. as a rule, only its performance is monitored.
• Servers do not always have all installed patches and are not always, it turns out, fully protected due to the fact that problems caused by performance issues, downtime, etc., are eliminated.
• They have a huge number of running processes, and therefore are more sensitive to the vulnerabilities that can be used by hackers.
The Adaptive Defense family of solutions with advanced protection features provides an opportunity to observe “first-hand” the techniques used by cyber-criminals to compromise various types of internal servers, even those that do not “look” to the Internet.
It is important to keep in mind that hackers usually do not launch a direct attack on their target, but they are selected to it gradually and very subtly. That is why we are seeing an increase in the number of attacks that do not use any malware. What hackers do is try to get closer to their target, without arousing suspicion, making various diversions and side movements. In most cases, the goal is servers, since they are usually the IT assets where the most confidential information is contained, and they can be used by criminals to launch attacks on other computers inside or outside the network.
Below we describe the most common attacks on servers that we have seen in the PandaLabs laboratory recently and which were blocked by the Adaptive Defense solution.
Attacks to SQL / MySQL database servers
Generally speaking, the first thing you will notice with this type of attack is an anomaly in the incoming traffic to the database server. It is used by hackers to search for and exploit vulnerabilities on the database server (which is not always “patched” due to idle time, etc.). Once the required vulnerability is found, hackers force the server to generate malicious files on the hard disk and run them in order to gain complete control over the system. Thanks to the advanced protection in Adaptive Defense, we see how hackers create users with specific profiles for remote access to servers and use the latter as launch pads for cyber-attacks against other network resources.
Attacks via Remote Desktop Connection (RDP)
This is a common way of attacking corporate servers, and it has become very popular over the past year in order to spread encryption. It is to access the target computer via the Internet so that it can be remotely controlled. As soon as cyber-criminals find a server with the Remote Desktop Protocol enabled, they launch a brute-force attack against it in order to select registration data (username and password). In the anti-virus laboratory, PandaLabs in recent months have found many examples of such attacks, for example:
• “Crysis” worldwide via remote desktop
• This is not ransomware, but in any case can “capture” your server.
• RDPPatcher sells access to your computer at a low price.
Attacks on domain and file servers
Regardless of the method used by the hacker to penetrate the corporate network, it is well known that one of the main objectives of any invasion is to get a user who can be used to perform certain actions within the IT structure. This makes domain management servers the primary goal of hackers, since such servers store domain administrator accounts (required to perform these “specific” actions) and have access to all computers in the domain.
Analysis of persistent threats of increased complexity (APT) in PandaLabs has shown that the use of domain management servers is a common practice for launching attacks on a network. For example, one of the Adaptive Defense clients used traditional anti-virus protection (not Panda) on their servers, while at the workstations in the domain, our extended protection was configured over this protection. At some point, extended protection began to work on workstations, since she began to identify and block attacks against them. The investigation revealed that these attacks were carried out from corporate servers - in fact, they were hacked.
The risk of infection by an unknown encryption key of mapped network drives
Network drives are often used to share information from different computers, but also pose a serious risk of infection.
If a computer with attached network drives has been infected by the encrypter, then the actions of this malicious program will not be limited only to the infected computer, but they will be extended to shared resources of network drives. To reduce this risk, organizations are encouraged to implement restrictive access control measures, removing write access to the network wherever possible.
To ensure proper protection of each computer on the network, we recommend installing Adaptive Defense or Adaptive Defense 360 enhanced protection solutions on each computer.
One of the most common mistakes is that extended protection is sufficient to protect only those computers that contain shared resources, while leaving the rest of the computers without extended protection. However, in such a scenario, if an unprotected computer was infected by the encrypter, then this malware will try to encrypt all the documents that it finds on the available drives in the system, including network drives.
In order to encrypt the contents of network drives remotely, the cryptographer uses remote procedure calls (RPC). From the point of view of the computer on which these network drives are physically located, this is a completely legitimate operation performed by the legitimate processes of the operating system (accessing and changing data files). Those. legitimate behavior will not be associated with malicious actions.
However, a malicious process is actually launched on the computer from which the attack is coming. Therefore, it must be identified and stopped there. That is why it is necessary that the extended protection be implemented on every computer.
Adaptive Defense 360 Extended Protection Configuration Example
As we have said, Adaptive Defense 360 is a cloud-based SaaS information security solution with advanced protection features. We have already talked about what this product is, how you can quickly implement it , how to integrate it with your own or third-party SIEM system. And in this article, using this product as an example, let's see how time-consuming it is to set up advanced protection against unknown threats.
Let's say right away, because Extended protection functions are automated to the maximum extent, the setup takes quite a bit of time.
You can do similar actions in parallel in the Panda Adaptive Defense 360 demo console (all you need is a browser - preferably Chrome or Firefox, you do not need to install anything):
Console: demologin.pandasecurity.com
Login: DRUSSIAN_FEDERATION_C14@panda.com
Password: DRUSSIAN # 123
So, logging into the Panda Cloud console, click on the button with the Panda Adaptive Defense 360 product and go to the management console, and then in the main menu select the Settings section:
This section contains computer groups on the left and security profiles on the right. Extended protection is managed on the basis of profiles. Therefore, you must select the desired profile in which you want to configure it. For example, take the Default profile:
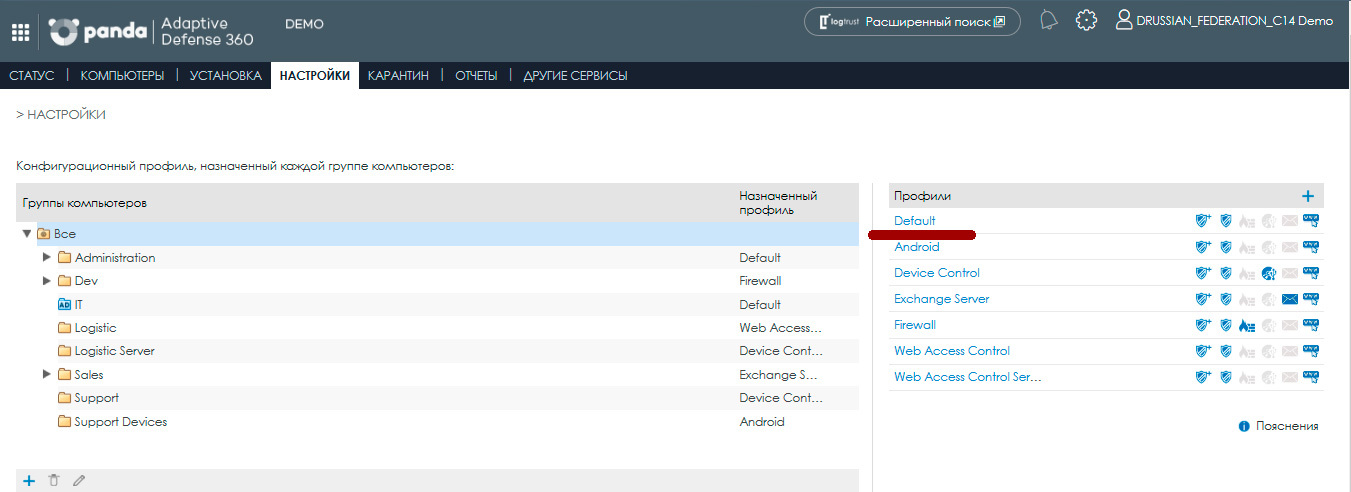
In the opened profile in the menu on the left, select the Extended Protection section:
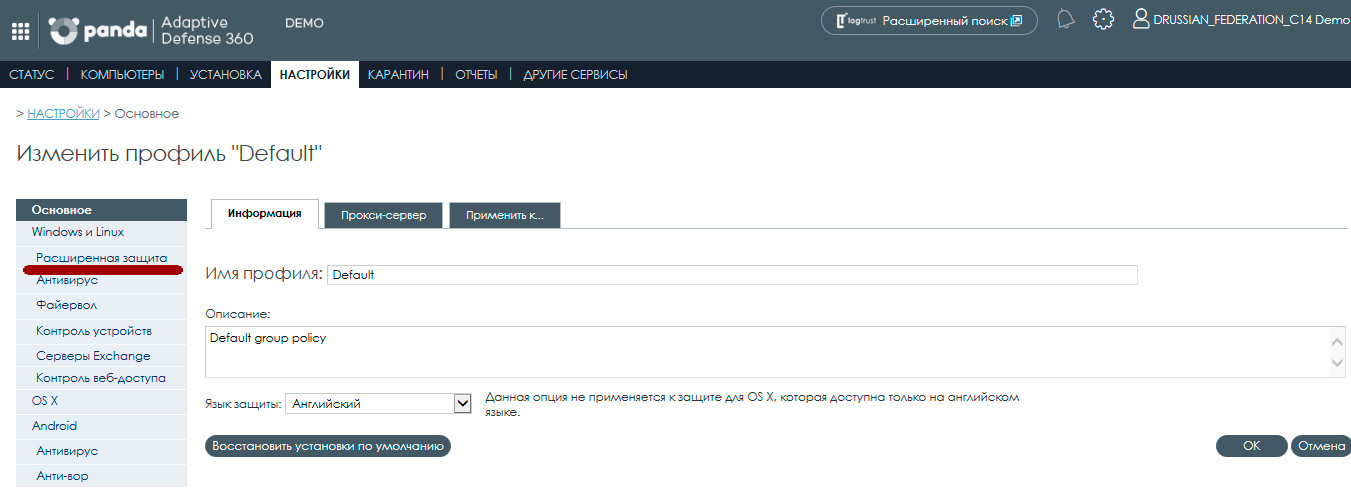
As a result, a page with advanced protection settings will open:
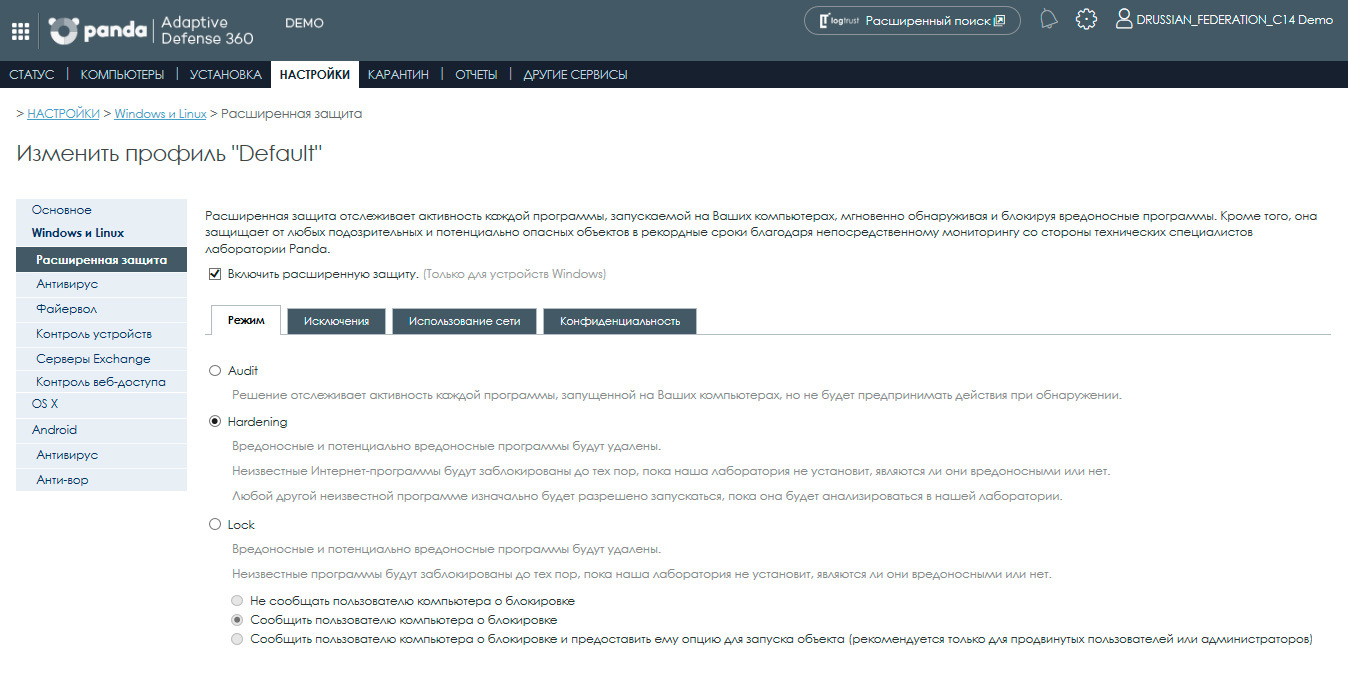
To enable extended protection for this profile, check the box next to Enable extended protection. We draw your attention to the fact that at the moment this functionality is offered only for devices with Windows.
After this, the settings options will be available to you, divided into four tabs: Mode, Exceptions, Network Usage and Privacy. Consider them in more detail.
Mode
Enhanced protection allows you to set various security modes to block unknown malware and protect computers from current threats and constant threats of increased complexity.
Audit
This mode is intended only for monitoring unknown threats. In this mode of operation, the solution does not block anything, but only tracks all running processes and the relationships between them and provides monitoring results in the form of expert information. By the way, this mode is recommended to be used in the first 2-3 weeks since the introduction of Adaptive Defense, so that the solution could “get to know” the software used in the company and adapt to its specificity.
Hardening
In this mode, the solution allows the launch of unclassified programs that are already installed on users' computers. At the same time, the solution will monitor all processes generated by such programs in order to prevent malicious and suspicious ones, and each of these programs will be analyzed for about 24 hours in the PandaLabs anti-virus laboratory for classification.
Also in this mode, the solution will block all unknown programs that come to the computer from external sources (Internet, e-mail, flash drives, etc.) until it is classified. In turn, programs classified as malicious will be moved to central quarantine.
Lock
This mode allows you to block the launch of all unknown (unclassified in PandaLabs) programs until they are classified. This mode has quite serious restrictions on the use of unknown software, but in the overwhelming majority of cases each such unknown program will be classified within 24 hours. In addition, the administrator always has the ability to make an exception to the block for each specific unknown program.
When selecting this mode, you can configure the following options:
• Do not inform the computer user about blocking - the local agent will not show any notifications when blocking an unknown program;
• Notify the computer user about the blocking - in this case, each time when blocking an unknown program, end users will see a message explaining the reason for blocking;
• Notify the computer user about the blocking and provide him with the option to launch the object - in this case, the end user is shown a message within 1 minute where he can choose the option to launch the blocked program under his responsibility. Such exceptions are permanent until the administrator changes the configuration in the management console.
Exceptions
On this tab, you can configure objects on computers that will not be checked by Adaptive Defense. Please note that these settings will be relevant for both extended protection and anti-virus protection too.
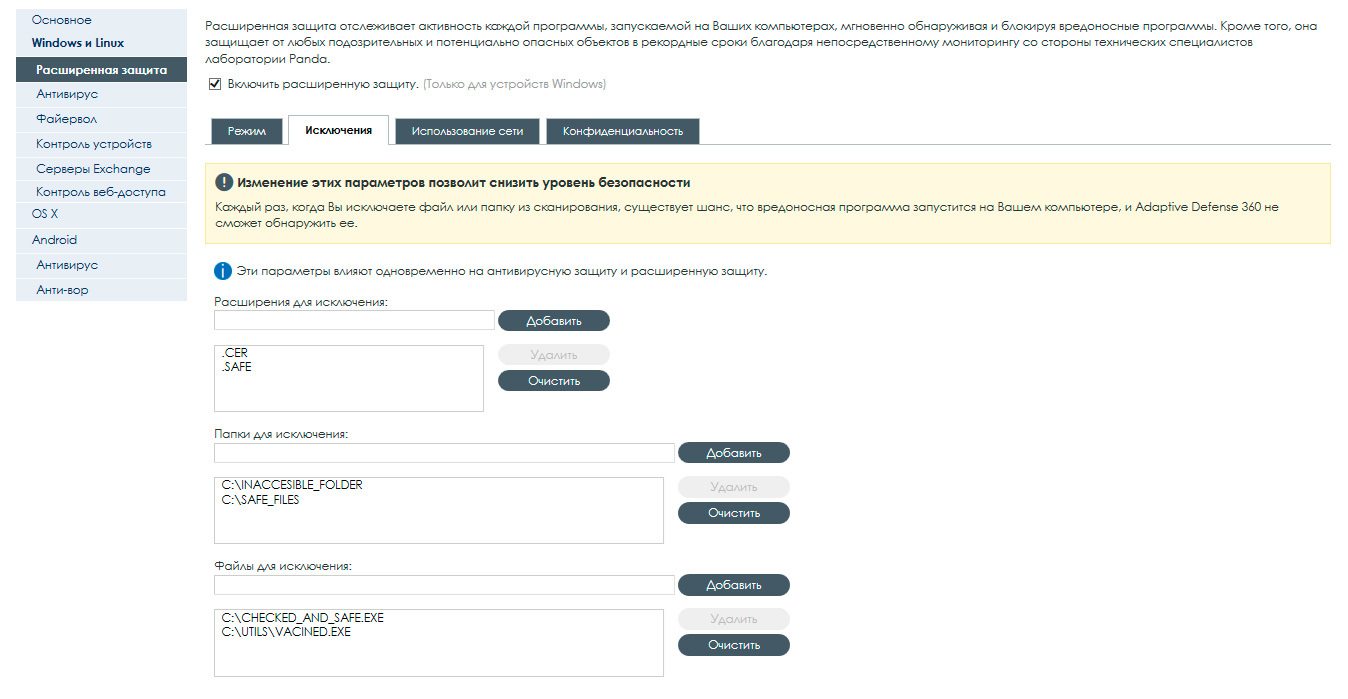
On this tab you can specify extensions, folders or files that should be excluded from control.
Network use
Each executable file unclassified in PandaLabs that tries to run on the user's computer is sent by the agent to our server for a thorough analysis. This function is configured in such a way as not to affect the performance of the computer network. For this reason, the default option, Maximum MB, which can be transferred per hour, is 50 MB.
You can specify the required value in MB for this option or set the value to 0 if you do not want to limit the amount of transferred files.
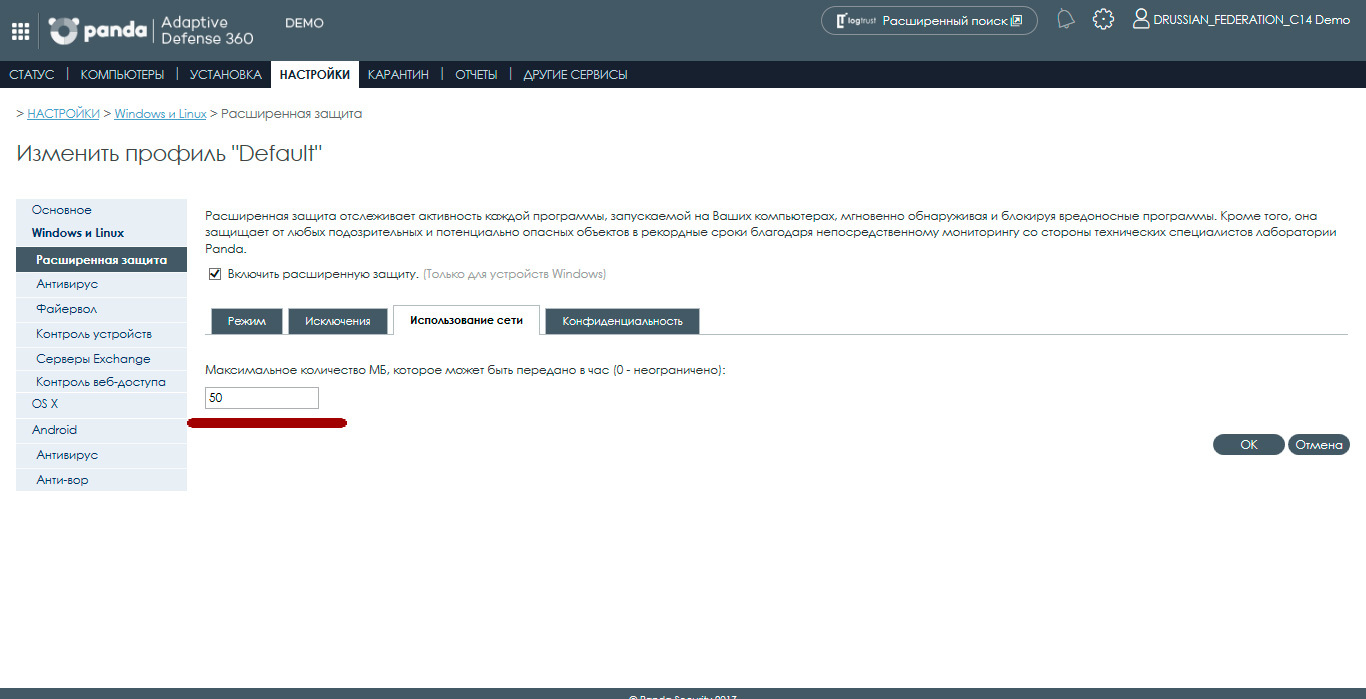
Unknown files are sent only once among all users in the world using Adaptive Defense, therefore if this unknown file has already been sent by an agent of a user, it will not be sent from another user's computer. In addition, the solution uses special mechanisms that allow you to optimize the use of network resources and minimize the load on the corporate network.
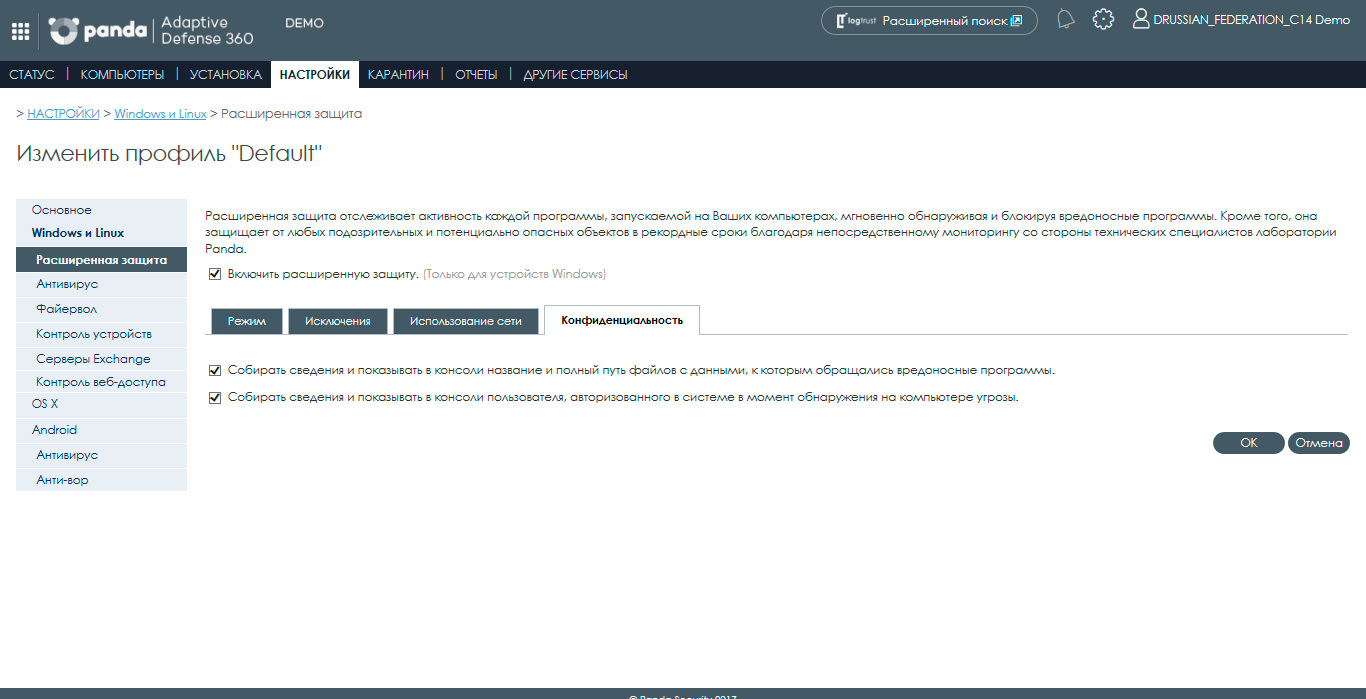
Confidentiality
On this tab, you can configure several privacy options:
• If you select the first option, the solution will collect and display to the administrator in the management console (and reports) the name and full path of the data files that the malware / processes accessed
• If you select the second option, the administrator will be able to see in the management console (and reports) data on the user who was authorized in the system at the time the threat was detected on the computer.
After you have configured all the required advanced protection settings, click OK .
This completes the extended protection setting in this profile. After about 15 minutes, all settings will be synchronized and take effect. From this moment on those computers that belong to this profile, the extended protection will work in accordance with your settings.
Extended Protection Behavior Against Malicious and Unknown Objects
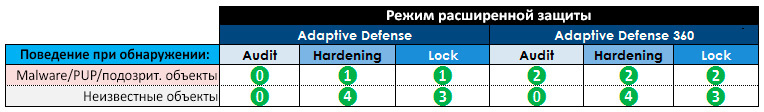
After you have configured the advanced protection options, let's see how the solution will behave depending on the scenario. The table below shows the scenario number for Adaptive Defense and Adaptive Defense 360 depending on the mode of operation and the characteristics of the detected object, and below the table below are detailed descriptions of each scenario.
Adaptive Defense is a simplified version of the product without permanent protection. It contains only the extended protection module. This version can work in parallel with any current corporate antivirus, providing an additional level of protection against unknown threats.
Adaptive Defense 360 is a full version of the product, which, in addition to enhanced protection, also contains all permanent protection modules (antivirus, firewall, device control, URL filtering, Exchange protection, etc.).
Scenario 0
Action:
• No action is taken (disinfection, deletion, blocking, ...)
Notifications:
• No pop-up windows are displayed on the end user's computer
• Malware and ANP activity is recorded and displayed in the management console ( Malicious programs and Potentially unwanted programs )
• The activity of suspicious and unknown objects is not registered and is not displayed in the control console (Blocked unclassified objects )
• If email notifications are enabled and configured in the Settings section , they will be sent if malware is detected.
Scenario 1
Action:
• Block
Notifications:
• A message pop-up window is displayed on the end user's computer
• Malware and PUP activity is recorded and is displayed in the management console (panel Malware and Potentially unwanted programs )
• suspicious activity and registers of unknown objects iruetsya and displayed in the management console (panel Blocked unclassified objects).
After these objects are classified, they will be registered and displayed in the corresponding panel ( Malicious programs or Potentially unwanted programs ), except when these objects are ultimately classified as non-malicious programs (goodware). After that, these objects will no longer be registered in the Blocked unclassified objects panel.
• If, in the Parameters section, email notifications are enabled and configured, they will be sent if malware and suspicious objects are detected. But they will not be sent in the case of the PNP.
Scenario 2
Action:
• Block and send to quarantine, disinfect or delete
Notifications:
• A pop-up window is displayed on the end user's computer with the message
• Malicious and anti-malware activity is logged and displayed in the management console ( Malicious programs and Potentially unwanted programs )
• Suspicious and unknown objects are logged and is displayed in the management console ( Blocked unclassified objects panel ).
After these objects are classified, they will be registered and displayed in the corresponding panel ( Malicious programs or Potentially unwanted programs), except for cases when these objects will be ultimately classified as non-malicious software (goodware). After that, these objects will no longer be registered in the Blocked unclassified objects panel.
• If, in the Parameters section, email notifications are enabled and configured, they will be sent if malware and suspicious objects are detected. But they will not be sent in the case of the PNP.
Scenario 3
Action:
• Blocking all unknown objects
Notifications:
• A pop-up window is displayed on the end-user's computer with a message
• Blocked unknown objects are registered and displayed in the control console (panelBlocked unclassified objects ). After these objects are classified, they will be registered and displayed in the corresponding panel ( Malicious programs or Potentially unwanted programs ), except when these objects are ultimately classified as non-malicious programs (goodware). After that, these objects will no longer register in the Blocked unclassified objects panel
• No email notifications are sent in case of detection of unknown objects.
Scenario 4
Action:
• Block all unknown objects that comply with the logic of the rules set for the advanced protection modeHardening
Notifications:
• A message pop-up window is displayed on the end-user's computer
• Blocked unknown objects are registered and displayed in the management console (the Blocked unclassified objects panel ). After these objects are classified, they will be registered and displayed in the corresponding panel ( Malicious programs or Potentially unwanted programs ), except when these objects are ultimately classified as non-malicious programs (goodware). After that, these objects will no longer register in the Blocked unclassified objects panel.
• No email notifications are sent when unknown objects are detected.
Conclusion
Adaptive Defense 360 offers automated advanced protection against unknown threats, APT, targeted attacks, cryptographers and other zero-day threats. This protection, using the full power of cloud big data and artificial intelligence, allows you to analyze each process directly in the context of the whole "big process", which allows you to more accurately understand its nature and end goals. And this, in turn, allows us to more accurately classify each application and process, providing a high level of protection against unknown threats.
As you can see, extended protection is configured very quickly and easily, which does not require any specialized knowledge.
Demo Console Adaptive Defense 360
To familiarize yourself with the management console, just a regular browser (Chrome or Firefox is recommended) and some free time are sufficient.
Console: demologin.pandasecurity.com
Login: DRUSSIAN_FEDERATION_C14@panda.com
Password: DRUSSIAN # 123
Trial licenses Adaptive Defense 360
You can register free full-featured licenses for 1 month
Source: https://habr.com/ru/post/325710/
All Articles