Secure access from anywhere in the world using Microsoft DirectAccess and Windows To Go. Part One - Theory
The most common method used for remote access to the internal resources of organizations is to configure a VPN connection. This technology has a number of disadvantages such as:
I propose to consider replacing the VPN technology developed by Microsoft - DirectAccess. This will allow the remote computer to be regarded as a component of the organization’s computer network, due to which it will be possible to perform the following operations to ensure information security:
I will consider DirectAccess in conjunction with Windows To Go. Windows To Go is an operating system of Windows 8 and higher, installed on an external USB-drive with all the necessary software. The OS installed in this way can be downloaded on any equipment that meets the minimum requirements. However, the software and data on the computer being used are not affected.
The description of the key technologies used will start with Microsoft DirectAccess, since it will be the main component of the created mobile remote access system for the corporate environment. It makes sense to consider the most current version based on Microsoft Windows Server 2012 R2 and the Windows 8.1 client operating system.
')
DirectAccess technology was first introduced as a component of Micrisoft Windows Server 2008 R2 and was designed to provide transparent access of remote computers to internal company network resources. DirectAccess allows remote users to fully utilize corporate network resources and use domain services.
Also, DirectAccess technology allows employees of various technical departments (Help Desk, IT and IB administrators) to manage remote user accounts, anti-virus protection components, local security policies, and monitor the timely installation of operating system updates and application programs. This allows the remote system to be kept up-to-date from the point of view of information security.
At its core, DirectAccess is a lot like a traditional VPN connection to a corporate network, but there is a difference, and quite substantial. Windows Server 2012-based DirectAccess makes the difference between computers on the internal corporate network and computers of remote clients less noticeable.
Below is a comparison of the new DirectAccess with VPN technology.
DirectAccess is built on top of IPv6 and requires all endpoint devices to support IPv6. Currently, the Internet protocol is dominated by IPv4, therefore the following technologies are used for communication between IPv6 devices via IPv4 networks: IPv6 tunneling over IPv4:
The Windows Server 2012, Windows 7 and Windows 8 operating systems support the transition protocols ISATAP, 6to-4 and Teredo. The end result is that clients connect to hosts using IPv6.

The DirectAccess client establishes two tunnels, which are the key to the versatility of this remote access method. These are IPsec ESP tunnels — payload with integrated security that is authenticated and encrypted to ensure confidentiality.
The computer tunnel is installed first when the DirectAccess client starts. This tunnel is authenticated only by a computer certificate and provides access to intranet DNS and domain controllers. This tunnel is also used to load the computer group policy and user authentication request.
The user’s tunnel is authenticated by a computer certificate and user credentials and provides access to intranet resources. This tunnel is also used to load user group policy.
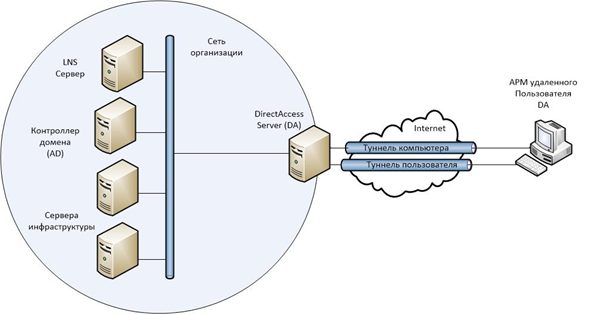
Both of these tunnels are installed transparently to the user. To set up remote access, the user does not need to enter registration information other than what he enters when logging into Windows.
There are three models of DirectAccess operation:
One of the advantages of DirectAccess is the ability to separate intranet traffic from Internet traffic, which has a positive effect on the throughput of the corporate network. However, in some cases, administrators can send all traffic through a DirectAccess connection. For example, to fully control the Internet traffic of a remote user.
In DA 2012, in contrast to the previous version implemented in Windows Server 2008, the presence of a PKI infrastructure is not a requirement. A PKI infrastructure is required when using clients on Windows 7 Enterprise or Ultimate, or when advanced options are required. When you plan to use Windows 8 Enterprise as a client OS, you can do without PKI. In this case, client computers will be authenticated using the Kerberos protocol. The DA server will be used as a Kerberos proxy, that is, authentication requests from clients are sent to the Kerberos proxy service, which runs on the DirectAccess server. Then the Kerberos proxy, on behalf of the client, sends Kerberos requests to the domain controllers.
Consider the process of connecting a client to a DirectAccess server.
The computer becomes a DirectAccess client after applying group policies to it, passing on the settings for connecting through the DA. Group policies are created during the configuration of the DirectAccess server and are distributed to security groups in Active Directory.
After applying group policies, the client determines its location relative to the corporate network. To do this, check the availability of the NLS server (Network Location Server). NLS server is a normal web server that uses the HTTPS protocol in its work. An NLS server can be any web server (IIS, Apache, etc.). In Windows Server 2012, the DirectAccess server can perform NLS functions. To decide on further actions of the client, depending on the availability of the NLS server, the name resolution policies are used - NRPT . If the NLS server is called by a name whose suffix matches the domain suffix of the local network, the client will use the corporate network’s DNS servers, if not, then use the DNS servers specified in the client’s network adapter settings. To properly check the NLS, its DNS name is entered into NRPT exceptions so that name resolution occurs through the DNS servers specified on the network adapter. When the client is located inside the corporate network, the internal DNS servers know the corresponding NLS address of the server.
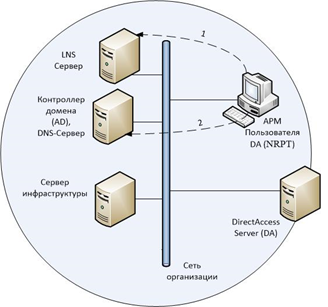
Being outside the corporate network, the client uses external DNS servers (local Internet service provider), which does not indicate how to convert the name of the NLS server. If the NLS server is detected, the client operates on the network as a normal workstation, that is, IPsec does not apply.
In the case when the client is outside the corporate network, when trying to connect to the NLS server using a DNS name that is added to the NRPT exceptions, the client contacts the DNS servers specified in the network adapter settings. Since this uses the ISP's DNS server, on which the NLS server’s DNS name resolution rule is not specified, the client is denied name resolution. When the client computer rejects the DNS server, the client computer applies IPsec policies and contacts the DirectAccess server using its DNS name, which must be spelled out in the outer zone of the corporate domain.
The DirectAccess client establishes a tunnel on the DirectAccess server using IPv6. If there is an IPv4 network between them, the client uses the Teredo or 6to4 protocol to encapsulate IPv6 to IPv4, or it will try to connect using IP-HTTPS. Once established, the client and the DirectAccess server perform mutual authentication during the IPsec tunnel setup process. The DirectAccess client then connects to the domain controller to get group policies.
Next, the DirectAccess user logs in or uses the credentials of an already logged in user in conjunction with certificates to establish an IPsec user tunnel. User Group Policy applies to the DirectAccess client. The DirectAccess server begins to forward traffic from the DirectAccess client to authorized intranet resources.
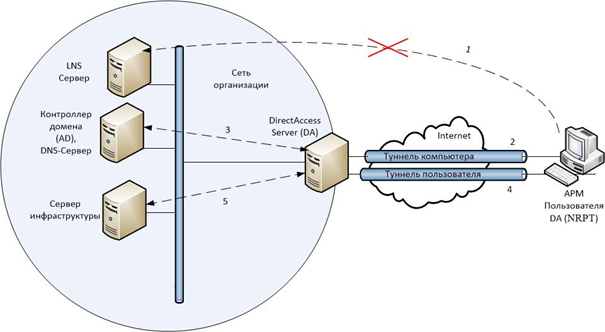
Due to the fact that DirectAccess requires the client’s computer to be included in the corporate domain, this option is not suitable for users using personal computers. But there is a technology, the use of which will allow Windows To Go to use DirectAccess on any computer that meets the minimum requirements for running Windows 8 and is connected to the Internet.
The Windows To Go technology is one of the new features of Windows 8 that allows you to create a properly configured OS image with the necessary software installed, which will be downloaded directly from the USB media, regardless of which OS is installed on the computer.
Differences between Windows To Go and a typical Windows installation:
To install and download Windows To Go, you must meet the following requirements:
There is a list of certified for use with WTG USB media:
If for the installation of Windows To Go will be used media that is not included in this list, then this may impose additional requirements for the computer on which WTG will run, for example, USB 3.0 support. Also because of this, Microsoft tech support is not worth counting on.
When choosing a computer to use as a Windows To Go workspace node, you must consider the following criteria:
When you first start Windows To Go on your computer, it detects all the hardware on your computer and installs the necessary drivers. Subsequently, the Windows To Go workspace loads on this computer more quickly, since the required set of drivers is already installed.
There are three ways to deploy WTG:
If the Windows To Go Creator Wizard is selected for the WTG deployment, then on the computer on which you plan to create the WTG, you will need to use the Windows 8 Enterprise
Each of the methods described above presupposes the preparation of a wim file (Windows Imaging Format is an oriented disk image format). WIM-file can contain not only the files of the operating system, but also a pre-configured OS with installed standard software.
This file can be obtained in several ways:
WIN file must contain Windows 8 Enterprise. Other OS editions are not supported by Windows To Go.
In the case of Windows To Go, encrypting the alienable media using BitLocker Drive Encryption technology is a mandatory requirement, since the disk can contain confidential information containing data that can be attributed to trade secrets or to personal data of partners, employees or customers of the company. BitLocker (full name BitLocker Drive Encryption) - data protection technology by full disk encryption, which is part of the operating systems Microsoft Windows Vista Ultimate / Enterprise, Windows 7 Ultimate / Enterprise, Windows Server 2008 R2, Windows 8, Windows 8.1 and Windows 10 With BitLocker, you can encrypt a logical drive, SD card or USB drive. At the same time, AES 128 and AES 256 encryption algorithms are supported.
The key itself can be stored on a USB drive, in a hardware TPM module or on a hard disk.
To obtain a key from the TPM, an additional method of user authentication using a USB key and / or password can be configured.
If a trusted platform module is absent on the motherboard used, or if a USB-drive with Windows To Go is used as the download and encryption object, the encryption key must be stored on an external USB-drive or a password can be used instead of the encryption key. In order to configure access to the encrypted media via USB-drive or password, you need to make changes to local group policies.
As a result of the considered combination of DirectAccess, Windows To Go and BitLocker technologies, we get a solution that will allow:
From the above, we can conclude that the sharing of the described technologies allows for the implementation of a remote connection to the corporate environment controlled by the organization’s services, not tied to specific client equipment and having a high degree of security.
In the next chapter, I will describe the practical implementation of the above described remote access system.
- the need to install additional software on the client computer, which is not always convenient, in some cases impossible;
- the need for the user to undergo additional authentication procedures;
- the inability to control the client computer by services responsible for the technical support and information security of the organization;
- the inability to control the timely update of the system and application software, the presence of antivirus software on it and the relevance of the antivirus databases;
- when moving a remote user must not always carry a lightweight laptop.
I propose to consider replacing the VPN technology developed by Microsoft - DirectAccess. This will allow the remote computer to be regarded as a component of the organization’s computer network, due to which it will be possible to perform the following operations to ensure information security:
- apply group policies to a remote computer;
- connect to a computer using standard tools - RDP, mmc, Remote Assistance;
- control Internet traffic;
- apply DLP systems;
- use centralized management of anti-virus protection;
- and other tools available within the domain.
I will consider DirectAccess in conjunction with Windows To Go. Windows To Go is an operating system of Windows 8 and higher, installed on an external USB-drive with all the necessary software. The OS installed in this way can be downloaded on any equipment that meets the minimum requirements. However, the software and data on the computer being used are not affected.
Microsoft DirectAccess 2012
The description of the key technologies used will start with Microsoft DirectAccess, since it will be the main component of the created mobile remote access system for the corporate environment. It makes sense to consider the most current version based on Microsoft Windows Server 2012 R2 and the Windows 8.1 client operating system.
')
DirectAccess technology was first introduced as a component of Micrisoft Windows Server 2008 R2 and was designed to provide transparent access of remote computers to internal company network resources. DirectAccess allows remote users to fully utilize corporate network resources and use domain services.
Also, DirectAccess technology allows employees of various technical departments (Help Desk, IT and IB administrators) to manage remote user accounts, anti-virus protection components, local security policies, and monitor the timely installation of operating system updates and application programs. This allows the remote system to be kept up-to-date from the point of view of information security.
At its core, DirectAccess is a lot like a traditional VPN connection to a corporate network, but there is a difference, and quite substantial. Windows Server 2012-based DirectAccess makes the difference between computers on the internal corporate network and computers of remote clients less noticeable.
Below is a comparison of the new DirectAccess with VPN technology.
- DirectAccess 2012 can be configured only for remote control, without the ability for remote clients to access the organization’s internal network.
- The user does not need to launch the client application and separately enter credentials for the organization of the VPN connection and authorization in the domain. DirectAccess connects to the corporate network automatically when the operating system is loaded, the user only needs to enter credentials to authenticate and authorize the corporate domain.
- Since the computer is already in the corporate network at the boot stage, it receives updates of domain group policies and other changes that are possible only at the computer boot stage.
- The computer simply loads in order to be able to connect to it, for example via RDP. It does not require identification and authentication procedures to download a remote user account.
- The communication channel between the computer and the corporate network is encrypted with robust algorithms using IPsec. To implement IPsec in VPN technology, additional hardware is required.
- It is possible to add native support for two-factor authentication using one-time passwords ( OTP ). For VPN, there is no such built-in support; you need to use additional third-party software.
- A single port, 443, is used to connect the remote client and the DirectAccess server. Since this port is usually open on firewalls, the client will not have a connection problem, no matter where it is. In VPN, this can be achieved using only SSTP.
- It is possible to add a remote machine to the domain using the Offline Domain Join technology, that is, to enter the computer into the domain without connecting to the domain controller. The next time the workstation is loaded, it will be part of the corporate network using DirectAccess connections.
- The advantages of a VPN include the fact that remote clients do not have to be members of a domain, DirectAccess is a mandatory requirement, therefore DirectAccess does not replace VPN. That is, a remote user must either issue a corporate laptop or enter his personal computer into the domain.
DirectAccess is built on top of IPv6 and requires all endpoint devices to support IPv6. Currently, the Internet protocol is dominated by IPv4, therefore the following technologies are used for communication between IPv6 devices via IPv4 networks: IPv6 tunneling over IPv4:
- ISATAP is a protocol that is used to automatically assign IPv6 addresses within an organization's IPv4 intranet.
- 6t4 — This protocol is used to automatically assign IPv6 addresses and route through an IPv4-based public Internet.
- Teredo is a protocol that applies to devices behind NAT to automatically assign IPv6 addresses and route through the public IPv4 Internet. This protocol requires two consecutive public IPv4 addresses.
The Windows Server 2012, Windows 7 and Windows 8 operating systems support the transition protocols ISATAP, 6to-4 and Teredo. The end result is that clients connect to hosts using IPv6.

The DirectAccess client establishes two tunnels, which are the key to the versatility of this remote access method. These are IPsec ESP tunnels — payload with integrated security that is authenticated and encrypted to ensure confidentiality.
The computer tunnel is installed first when the DirectAccess client starts. This tunnel is authenticated only by a computer certificate and provides access to intranet DNS and domain controllers. This tunnel is also used to load the computer group policy and user authentication request.
The user’s tunnel is authenticated by a computer certificate and user credentials and provides access to intranet resources. This tunnel is also used to load user group policy.

Both of these tunnels are installed transparently to the user. To set up remote access, the user does not need to enter registration information other than what he enters when logging into Windows.
There are three models of DirectAccess operation:
- End-to-edge model — The DirectAccess client will establish an IPsec tunnel to the DirectAccess server. The DirectAccess server then redirects unprotected traffic to intranet resources.
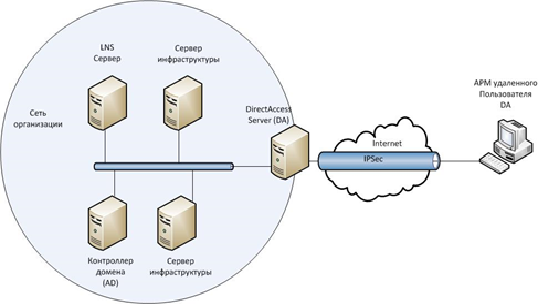
- The end-to-end model is a DirectAccess client that establishes an IPsec tunnel with each application server to which it connects. This guarantees the protection of traffic, including that transmitted over the intranet.
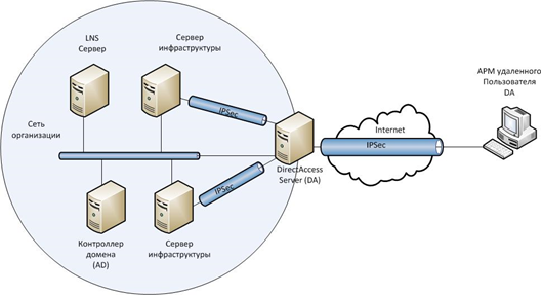
- The remote control support model is used to control devices without providing user access. This deployment model provides DirectAccess clients only access to dedicated management servers, which in turn have access to DirectAccess clients.
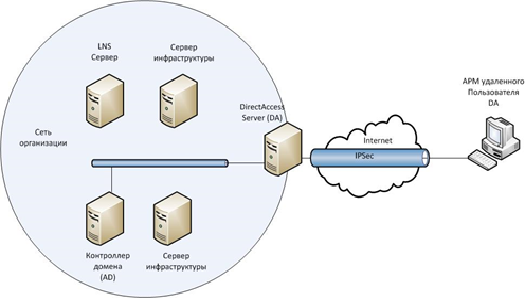
One of the advantages of DirectAccess is the ability to separate intranet traffic from Internet traffic, which has a positive effect on the throughput of the corporate network. However, in some cases, administrators can send all traffic through a DirectAccess connection. For example, to fully control the Internet traffic of a remote user.
In DA 2012, in contrast to the previous version implemented in Windows Server 2008, the presence of a PKI infrastructure is not a requirement. A PKI infrastructure is required when using clients on Windows 7 Enterprise or Ultimate, or when advanced options are required. When you plan to use Windows 8 Enterprise as a client OS, you can do without PKI. In this case, client computers will be authenticated using the Kerberos protocol. The DA server will be used as a Kerberos proxy, that is, authentication requests from clients are sent to the Kerberos proxy service, which runs on the DirectAccess server. Then the Kerberos proxy, on behalf of the client, sends Kerberos requests to the domain controllers.
Consider the process of connecting a client to a DirectAccess server.
The computer becomes a DirectAccess client after applying group policies to it, passing on the settings for connecting through the DA. Group policies are created during the configuration of the DirectAccess server and are distributed to security groups in Active Directory.
After applying group policies, the client determines its location relative to the corporate network. To do this, check the availability of the NLS server (Network Location Server). NLS server is a normal web server that uses the HTTPS protocol in its work. An NLS server can be any web server (IIS, Apache, etc.). In Windows Server 2012, the DirectAccess server can perform NLS functions. To decide on further actions of the client, depending on the availability of the NLS server, the name resolution policies are used - NRPT . If the NLS server is called by a name whose suffix matches the domain suffix of the local network, the client will use the corporate network’s DNS servers, if not, then use the DNS servers specified in the client’s network adapter settings. To properly check the NLS, its DNS name is entered into NRPT exceptions so that name resolution occurs through the DNS servers specified on the network adapter. When the client is located inside the corporate network, the internal DNS servers know the corresponding NLS address of the server.

Being outside the corporate network, the client uses external DNS servers (local Internet service provider), which does not indicate how to convert the name of the NLS server. If the NLS server is detected, the client operates on the network as a normal workstation, that is, IPsec does not apply.
In the case when the client is outside the corporate network, when trying to connect to the NLS server using a DNS name that is added to the NRPT exceptions, the client contacts the DNS servers specified in the network adapter settings. Since this uses the ISP's DNS server, on which the NLS server’s DNS name resolution rule is not specified, the client is denied name resolution. When the client computer rejects the DNS server, the client computer applies IPsec policies and contacts the DirectAccess server using its DNS name, which must be spelled out in the outer zone of the corporate domain.
The DirectAccess client establishes a tunnel on the DirectAccess server using IPv6. If there is an IPv4 network between them, the client uses the Teredo or 6to4 protocol to encapsulate IPv6 to IPv4, or it will try to connect using IP-HTTPS. Once established, the client and the DirectAccess server perform mutual authentication during the IPsec tunnel setup process. The DirectAccess client then connects to the domain controller to get group policies.
Next, the DirectAccess user logs in or uses the credentials of an already logged in user in conjunction with certificates to establish an IPsec user tunnel. User Group Policy applies to the DirectAccess client. The DirectAccess server begins to forward traffic from the DirectAccess client to authorized intranet resources.

Windows To Go
Due to the fact that DirectAccess requires the client’s computer to be included in the corporate domain, this option is not suitable for users using personal computers. But there is a technology, the use of which will allow Windows To Go to use DirectAccess on any computer that meets the minimum requirements for running Windows 8 and is connected to the Internet.
The Windows To Go technology is one of the new features of Windows 8 that allows you to create a properly configured OS image with the necessary software installed, which will be downloaded directly from the USB media, regardless of which OS is installed on the computer.
Differences between Windows To Go and a typical Windows installation:
- In order to avoid accidental breach of data privacy, the internal hard drives of the host computer, when booted into the WTG workspace, work autonomously by default. Similarly, if the disk is connected to a computer with the OS loaded, the WTG disk is not displayed in the explorer.
- To ensure security when encrypting a WTG drive using BitLocker, the boot system boot password is used instead of the TPM because the TPM is tied to a specific computer, while Windows To Go drives are moved between computers.
- To ensure that the Windows To Go workspace can easily move between computers, hibernation is disabled by default. However, hibernation can be enabled in Group Policy settings.
- Windows Recovery Environment is not available. In those rare cases when you need to repair a WTG disk, you should reinstall it from the image, creating a new Windows image.
- Updating and resetting the Windows To Go workspace is not supported. Reset to the manufacturer standard does not apply to the computer when executing the WTG workspace, so the feature has been disabled.
- Shop is disabled by default. Applications licensed through the Store are tied to licensing equipment. Since WTG is designed to navigate different computers, access to the Store has been canceled. You can enable the use of the Store if your Windows To Go workspaces do not move across multiple computers.
To install and download Windows To Go, you must meet the following requirements:
There is a list of certified for use with WTG USB media:
- IronKey Workspace W300
- Kingston DataTraveler Workspace for WTG
- Spyrus Portable Workplace
- Spyrus Secure Portable Workplace
- Super Talent Express RC4 for WTG and Super Talent Express RC8 for WTG
- Western Digital My Passport Enterprise
If for the installation of Windows To Go will be used media that is not included in this list, then this may impose additional requirements for the computer on which WTG will run, for example, USB 3.0 support. Also because of this, Microsoft tech support is not worth counting on.
When choosing a computer to use as a Windows To Go workspace node, you must consider the following criteria:
- The computer must meet the minimum requirements for use with Windows 7 or Windows 8 operating systems.
- The computer selected as the host for the WTG must support booting from USB.
- Using WTG on a computer running Windows RT (Windows 8 ARM) is not supported.
- Running Windows To Go workspace from a Mac is not supported.
When you first start Windows To Go on your computer, it detects all the hardware on your computer and installs the necessary drivers. Subsequently, the Windows To Go workspace loads on this computer more quickly, since the required set of drivers is already installed.
There are three ways to deploy WTG:
- using the Windows To Go Creator Wizard;
- using a script (PowerShell + utilities for working with DISM or ImageX images);
- using the User Self-Provisioning tool in System Center 2012 Configuration Manager SP1.
If the Windows To Go Creator Wizard is selected for the WTG deployment, then on the computer on which you plan to create the WTG, you will need to use the Windows 8 Enterprise
Each of the methods described above presupposes the preparation of a wim file (Windows Imaging Format is an oriented disk image format). WIM-file can contain not only the files of the operating system, but also a pre-configured OS with installed standard software.
This file can be obtained in several ways:
- Use the install.wim file located on the disk with the OS distribution in the / sources folder. In this case, we get a "clean" OS. However, in the latest versions of Windows, the OS image file is in ESD format, so it may be necessary to convert ESD to WIM format.
- Create a wim image of a pre-prepared OS using Microsoft's WAIK automated installation tools. Of course, the advantage of this method is the fact that when preparing the OS you can make the necessary settings and install a standard set of software.
- Also, using third-party software, you can create a wim file by converting a virtual hard disk vhd file.
WIN file must contain Windows 8 Enterprise. Other OS editions are not supported by Windows To Go.
Bitlocker
In the case of Windows To Go, encrypting the alienable media using BitLocker Drive Encryption technology is a mandatory requirement, since the disk can contain confidential information containing data that can be attributed to trade secrets or to personal data of partners, employees or customers of the company. BitLocker (full name BitLocker Drive Encryption) - data protection technology by full disk encryption, which is part of the operating systems Microsoft Windows Vista Ultimate / Enterprise, Windows 7 Ultimate / Enterprise, Windows Server 2008 R2, Windows 8, Windows 8.1 and Windows 10 With BitLocker, you can encrypt a logical drive, SD card or USB drive. At the same time, AES 128 and AES 256 encryption algorithms are supported.
The key itself can be stored on a USB drive, in a hardware TPM module or on a hard disk.
To obtain a key from the TPM, an additional method of user authentication using a USB key and / or password can be configured.
If a trusted platform module is absent on the motherboard used, or if a USB-drive with Windows To Go is used as the download and encryption object, the encryption key must be stored on an external USB-drive or a password can be used instead of the encryption key. In order to configure access to the encrypted media via USB-drive or password, you need to make changes to local group policies.
Conclusion
As a result of the considered combination of DirectAccess, Windows To Go and BitLocker technologies, we get a solution that will allow:
- remote employees to feel “as in the workplace”, while being anywhere in the world where there is a computer connected to the Internet;
- not to modify or supplement the software of the computer used;
- employees to work in any division of the company, on any free computer, using pre-configured software and the necessary files;
- ensure the confidentiality of data stored on a portable device in case of loss of the carrier or contact with persons who do not have authorized access to the specified data and resources of the corporate network;
- use the built-in two-factor authentication with OTP;
- organizational units responsible for technical user support, administration of system and application software, as well as providing information security systems, do not lose contact with remote systems and keep them up to date;
- Manage Internet traffic from remote clients by sending it through a corporate proxy server.
From the above, we can conclude that the sharing of the described technologies allows for the implementation of a remote connection to the corporate environment controlled by the organization’s services, not tied to specific client equipment and having a high degree of security.
In the next chapter, I will describe the practical implementation of the above described remote access system.
Source: https://habr.com/ru/post/325458/
All Articles