Necurs, one of the largest botnets in the world, received a DDoS module
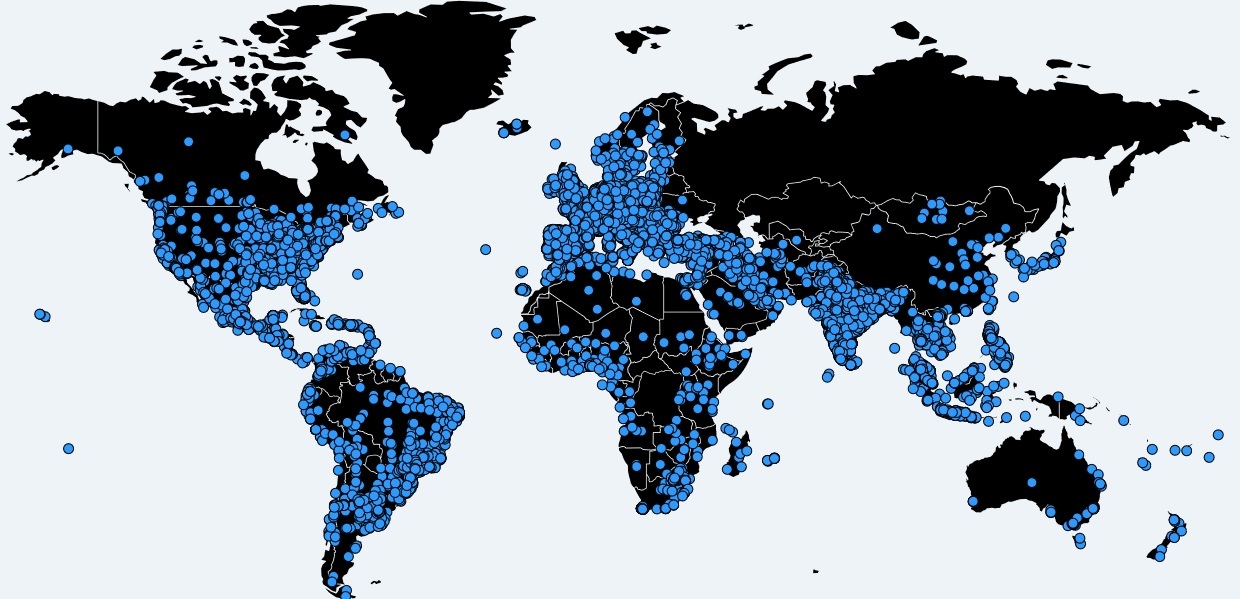
Necurs botnet is known as one of the largest bots in the world. Its owners use the power of their offspring to send a huge number of spam messages. Their volume is so large that the work of Necurs noticeably affects the total size of e-mail traffic worldwide. Generally speaking, Necurs is not just a spamboot, it is a dangerous enough malware that infects vulnerable systems, pulling up the main module of the botnet and the corresponding modules.
Necurs has been around for several years. During this time, he has become the object of research for many information security specialists. The experts were able to find out what vulnerabilities the attacking part of the botnet uses and what protocol is used by the spam module. But the platform itself is not static, it is changing and improving.
About six months ago, Anubisnetworks specialists noticed that Necurs now works not only with port 80, but also with other ports that belong to a completely different data transfer protocol. Here is an example of analyzing Necurs traffic.
')
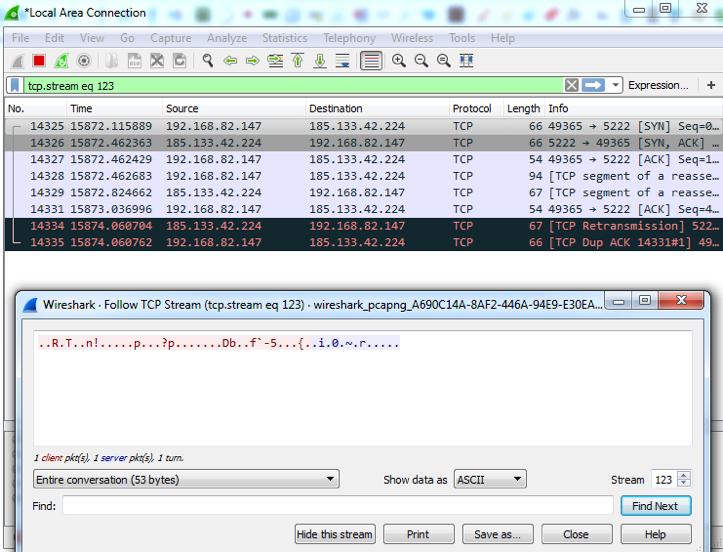
Studying this aspect, the company's specialists were able to understand that, in fact, the botnet was activated in order to install a module in the affected systems that provides Necurs with the ability to conduct DDoS attacks.
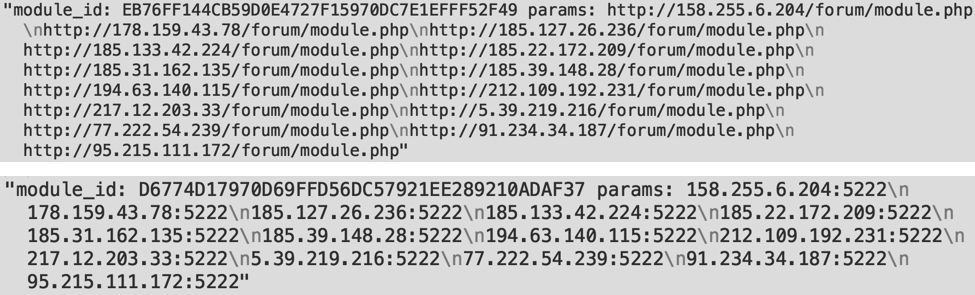
In the first case, the installation of a spam module, which is well known to specialists. There is a mention of C2 addresses that are associated with new spam campaigns. But in the second case, the parameters of the hitherto unknown module that communicates with the server through port 5222 are specified.
The approximate “release date” of this module is August 23, 2016. True, there is a possibility that this was a preliminary version, replaced by a final one.
Campaign staff downloaded the module and conducted reverse engineering in order to understand what it is. At first glance, this is a simple SOCKS / HTTP module. But if you look better, it becomes clear that this module has the ability to work with HTTP and UDP requests, which are put in an infinite loop. Accordingly, it becomes clear that this module is designed to implement DDoS attacks.
By the way, the botnet is really big - there are more than a million infected active elements in this network. With this size it is a very convenient option for conducting DDoS attacks. Some infected network elements have been part of it for more than two years. So long the botnet lasted thanks to the caution of its owners, who carefully dispose of the received features.
As soon as the module is loaded into the victim system. The following actions are performed:
* There is a parsing of parameters and settings;
* A database of internal IP addresses of the system is being collected, as well as an external database;
* Network bandwidth is determined;
* Determined random port;
* A botnet tries to find out if the main system is hidden behind a NAT or not;
* If not, the bot starts the SOCKS / HTTP service for an arbitrary port greater than 1024.

After initialization, the bot tries to connect to the current C2 every 10 minutes. He does this until the operators give the command to stop.
In addition, the botnet is equipped with a SOCKS / HTTP module, which allows platform operators to use the compromised elements of the botnet as a proxy (HTTP, SOCKSv4 and SOCKSv5 protocols). Work with a proxy is conducted in two modes: direct proxy and proxy backconnect.
As for the first mode, here the principle of operation is simple:

But working in this mode is possible only if the infected system is not hidden behind NAT or is not protected by a firewall. And such systems are literally units.
As for the proxy backconnect mode, everything is more complicated.
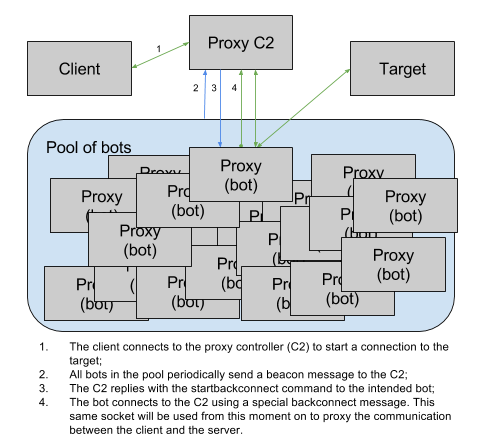
But working in this mode is possible even if the infected system is behind NAT or a firewall. In this case, you can connect to the internal resources of the network, of which the infected system is a part. Moreover, the connection is from the system itself. Another way to work with such proxies is to constantly change IP addresses.

DDoS module
But the most interesting thing is not a proxy, but a new DDoS module. It provides for the possibility of conducting basic attacks of two types. Despite the fact that there are no tricks like methods of enhancing the attack, the scale of the bot allows its operators to do without tricks.
When receiving a command from a botnet operator, it attacks a specific target using HTTP or UDP flood, as indicated above.
HTTP works in 16 parallel request streams.

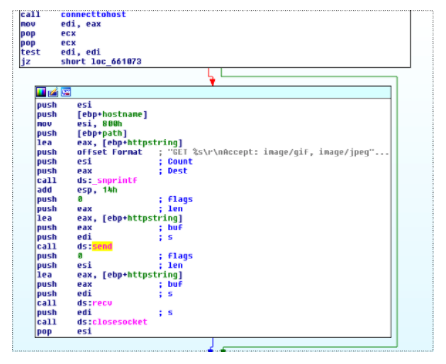
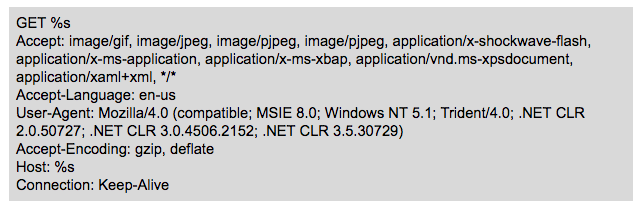
The request is formed as follows.
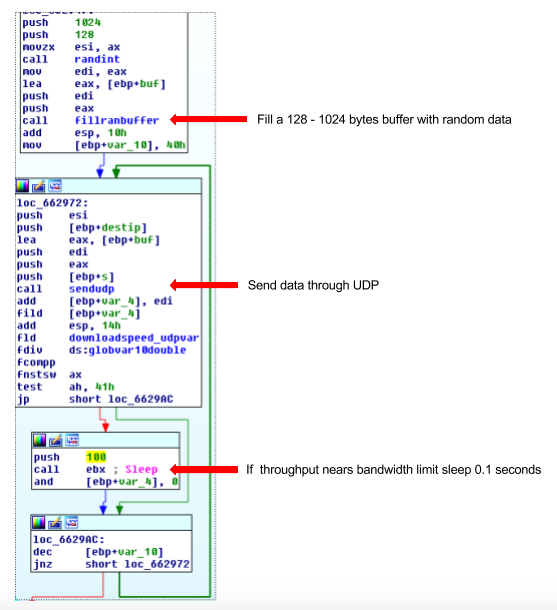
As for UDP, here everything is somewhat different - a botnet sends packets with a radome size from 128 to 1024 bytes.
So far, no DDoS attacks using Necurs have been fixed. But such attacks are possible at any time. But Necurs is even more than Mirai, with which the attackers attacked several large telecommunications organizations in different countries of the world. True, some experts believe that the DDoS module in Necurs is not intended for carrying out custom attacks, but for the own needs of botnet operators, for example, to attack competitors' resources.

Source: https://habr.com/ru/post/325302/
All Articles