OpenSSL, ssl_ciphers and nginx: we pump 100%
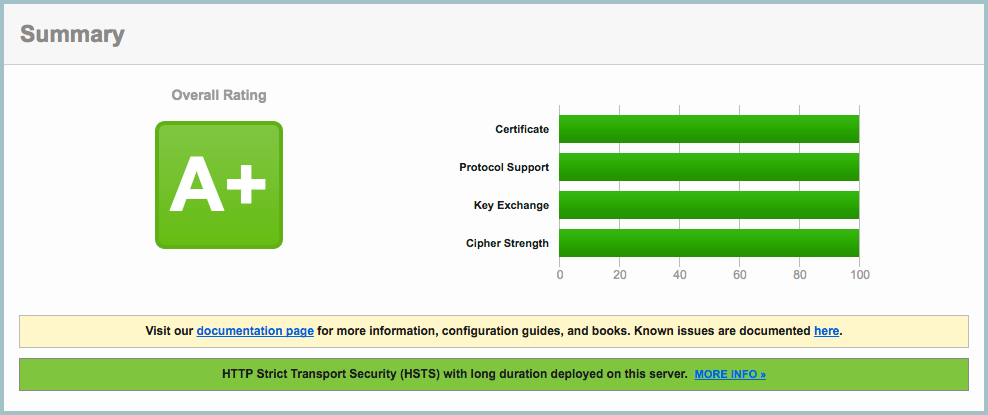
A lot of where it is written about how to get 100% and A + on the test from Qualys . At the same time, almost everywhere the directives ssl_ciphers and the like are given as such magic lines that you just need to insert, and hope that the author does not let you under the monastery. This article is intended to correct this misunderstanding. After reading this article, the ssl_ciphers directive will lose all magic for you, and ECDHE and AES will be like friends and brothers.
Training
We will work with Debian 8.7. If you have a different distribution, the versions should be the same or newer.
# lsb_release -d Description: Debian GNU/Linux 8.7 (jessie) # openssl version OpenSSL 1.0.1t 3 May 2016 # nginx -V nginx version: nginx/1.6.2 We will configure nginx to receive certificates from Let's Encrypt according to the instructions , but only before obtaining a certificate for our domain.
certbot certonly -d example.com -d www.example.com Config use the minimum. Nothing extra. Everything is by default.
server { server_name www.example.com example.com; listen 443 ssl default_server; ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem; } Now let's run a test for this server .

With the default settings, the result is so-so. On the four, if in our opinion. They swear at weak parameters for key exchange using the Diffie – Hellman algorithm (hereinafter referred to as DH).
It would be possible to make enhanced parameters , but such parameters and speeds are not added, and are supported by some old clients. The same old clients support the DH protocol on elliptic curves (ECDHE), which means we do not lose anything and even gain speed if, following Google , Facebook , Mozilla and CloudFlare, we completely abandon the slow EDH ciphers in favor of ECDHE.
Easy further. Need a list of recommended ciphers .
For a certificate with an RSA key from that list, only authenticated RSA ciphers are needed.
ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES256-SHA384 DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA DHE-RSA-AES128-SHA256 DHE-RSA-AES256-SHA256 From them we exclude ciphers weaker than 256 bits, and ciphers DHE. We list the remaining in the configuration directive.
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES256-SHA384; But this alone will not be enough . Need a key of at least 4096 bits.
certbot certonly --renew-by-default --rsa-key-size 4096 -d example.com -d www.example.com And another curve. In the version of OpenSSL you are using, you can only select one . Choose the most reliable of the popular.
ssl_ecdh_curve secp384r1; For evaluation with a plus, add HSTS.
add_header Strict-Transport-Security "max-age=31536000"; Finally, disable the old protocols for a 100% score on the Protocol Support column .
ssl_protocols TLSv1.2; The complete config is obtained as follows.
server { server_name www.example.com example.com; listen 443 ssl default_server; ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem; ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES256-SHA384; ssl_ecdh_curve secp384r1; add_header Strict-Transport-Security "max-age=31536000"; ssl_protocols TLSv1.2; } We will verify that there is no error in the configuration of ciphers and protocols.
$ nmap --script ssl-enum-ciphers -p 443 example.com Starting Nmap 7.40 ( https://nmap.org ) at 2017-03-01 00:00 UTC Nmap scan report for example.com (1.2.3.5) Host is up (0.030s latency). PORT STATE SERVICE 443/tcp open https | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp384r1) - A | compressors: | NULL | cipher preference: server |_ least strength: A Nmap done: 1 IP address (1 host up) scanned in 3.22 seconds The ciphers are in place, though not in that order. But it is expected. You can run the test.

Score five plus. Happiness joy. It would seem that.
disadvantages
But there is one problem. If the test results are scrolled to the Handshake Simulation section, then we will see that IE users of any version younger than 11, Java up to SE 8, Android up to version 4.3 and even some versions of Safari will not get to our site. I don’t even speak about software compiled with OpenSSL version less than 0.9.8.
There is another problem: performance . Our key for 4096 bits directly affects the speed of the connection , while not too enhances protection . Ciphers for 256 bits also do not help speed up the connection, as for mobile devices with low-power processors and other clients without AES-NI (hardware acceleration).
In the case of RSA, it is easy to verify the negative impact on speed using the built-in test in OpenSSL.
openssl speed rsa2048 rsa4096 On low-power Celeron 1007U, the difference is obvious.
sign verify sign/s verify/s rsa 2048 bits 0.002381s 0.000071s 420.0 14051.0 rsa 4096 bits 0.016790s 0.000260s 59.6 3852.8 Signing on the server side is seven times slower. Verification of the signature on the client is 3.6 times slower. On the other gland, the trend remains the same. This loss in speed is a fee for strengthening the cipher strength by some 16% .
ChaCha20 / Poly1305 vs. AES-128
Similarly, let's check the speed of the recommended ciphers on OpenSSL 1.1.0e.
for cipher in aes-128-gcm aes-256-gcm chacha20-poly1305 do openssl speed -decrypt -evp $cipher 2>/dev/null | grep ^$cipher done | column -t 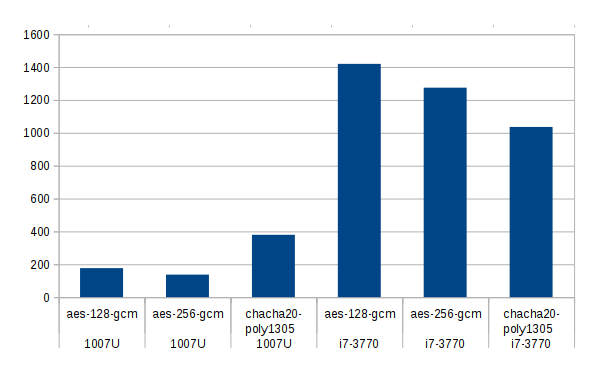
On the Celeron 1007U, the ChaCha20 / Poly1305 cipher is twice as fast as AES-128, and the last one-third faster than AES-256. On the Core i7 with AES-NI, the picture is different: the ChaCha20 / Poly1305 will be a third slower than the AES-128, and the AES-256 is only slightly slower than the AES-128. When encrypting the picture is about the same.
Key exchange with the default prime256v1 curve (also secp256r1 or NIST P-256) will be significantly faster than with the enhanced curve secp384r1 (NIST P-384).
$ openssl speed ecdsap256 ecdsap384 ecdhp256 ecdhp384 sign verify sign/s verify/s 256 bit ecdsa (nistp256) 0.0001s 0.0003s 7923.8 3214.4 384 bit ecdsa (nistp384) 0.0006s 0.0023s 1756.6 430.1 op op/s 256 bit ecdh (nistp256) 0.0002s 4893.5 384 bit ecdh (nistp384) 0.0019s 525.9 Working with the P-384 takes 7–9 times longer depending on the operation.
If we compare ECDSA and RSA, then it can be seen that in the case of ECDSA the computational load falls more on the client than on the server.
If you want to repeat the tests at home, then before the tests should raise the priority of the current process.
sudo renice -1 $$ One thing is clear: the choice of ciphers and parameters must be approached more carefully.
Cipher Search Principle
Listing ciphers by the list is not the best idea because it will soon be possible to use ChaCha20 / Poly1305 in nginx, without recompiling and third-party sources. With an explicit cipher job, the server will not use any new types of encryption without reconfiguration. This is not something you want to think about every day.
It will be better to choose ciphers by keywords or tags , each of which correspond to a certain group of ciphers. Keywords in different versions of OpenSSL are different, but we can always check them.
For example, the EECDH tag matches all ciphers with the exchange of one-time (ephemeral) keys using the DH algorithm with elliptic curves.
$ openssl ciphers -v 'EECDH' | column -t ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-RC4-SHA SSLv3 Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1 ECDHE-ECDSA-RC4-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=RC4(128) Mac=SHA1 ECDHE-RSA-DES-CBC3-SHA SSLv3 Kx=ECDH Au=RSA Enc=3DES(168) Mac=SHA1 ECDHE-ECDSA-DES-CBC3-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=3DES(168) Mac=SHA1 ECDHE-RSA-NULL-SHA SSLv3 Kx=ECDH Au=RSA Enc=None Mac=SHA1 ECDHE-ECDSA-NULL-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=None Mac=SHA1 The ciphers are shown in the list according to priority: the client will select the first suitable cipher, viewing the list in the specified order.
If we had the latest version of OpenSSL, then to get the same list, we would use a clear ECDHE tag, giving the same list and corresponding to the cipher prefix. In the current version there is no such tag , so we use one.
In the resulting list, ciphers are striking without, in fact, encryption, which come with the mark Enc=None . Exclude such ciphers, giving only authentication. At the same time exclude ciphers without authentication.
openssl ciphers -v 'EECDH:!aNULL:!eNULL' For a complete and irrevocable exclusion, the tags of the groups aNULL and eNULL with unsuitable ciphers are mentioned with negation. There will be no cipher with Au=None or Enc=None in the list.
Tags can be combined by getting intersections of cipher suites. Get ciphers that combine ECDHE, AES-256 and GCM .
$ openssl ciphers -v 'EECDH+AES256+AESGCM' | column -t ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD Cipher groups can be moved lower in priority, with a plus at the beginning. Lower the priority of ciphers with AES-256 without deleting them.
$ openssl ciphers -v 'EECDH+aRSA+AES:+AES256' | column -t ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 You can temporarily remove some cipher group, then add it in another form. Exclude ciphers from 3DES from all ECDHE ciphers, and then return them back, but only in combination with RSA key exchange. Such weak ciphers should be at the very bottom of the list.
$ openssl ciphers -v 'EECDH:-3DES:RSA+3DES' | tail -1 | column -t DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1 Choosing ciphers
Now we have everything to make a list of ciphers for nginx, which will not require additions when new versions of OpenSSL are released, losing old ciphers and acquiring new ones without any participation on our part. We consider the need to support older browsers and speed requirements.
Let's start by getting the list of ciphers we already use, but we will not exclude ciphers for certificates with EC in case we ever want to use this type of certificate.
$ openssl ciphers -v 'EECDH+AES256' | column -t ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 In fact, we need not so much AES specifically, but how many weak 3DES and RC4 ciphers are not needed. Last exclude completely and forever.
$ openssl ciphers -v 'EECDH:-3DES:!NULL:!RC4' | column -t ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 Give priority to faster ciphers , lowering it for AES-256. We will not completely remove AES-256 in case someone really needs AES-256. (The extra bits from him are imaginary .)
$ openssl ciphers -v 'EECDH:+AES256:-3DES:!NULL:!RC4' | column -t ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 Such a cipher string will not exclude ChaCha20 / Poly1305 in the next version of OpenSSL.
$ openssl version; openssl ciphers -v 'EECDH:+AES256:-3DES:!NULL:!RC4' | column -t | head -n 6 OpenSSL 1.1.0e 16 Feb 2017 ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-CCM8 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESCCM8(128) Mac=AEAD ECDHE-ECDSA-AES128-CCM TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESCCM(128) Mac=AEAD For some legacy clients, we will return AES without ephemeral keys.
$ openssl ciphers -v 'EECDH:+AES256:-3DES:RSA+AES:!NULL:!RC4' | column -t ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256 AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1 AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256 AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1 Finally, let's get back 3DES without ephemeral keys purely for IE8 / XP. There is no way to help IE6 / XP - by default it does not support TLS.
$ openssl ciphers -v 'EECDH:+AES256:-3DES:RSA+AES:RSA+3DES:!NULL:!RC4' | column -t ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 ECDHE-RSA-AES128-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 ECDHE-ECDSA-AES128-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 ECDHE-RSA-AES256-SHA SSLv3 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 ECDHE-ECDSA-AES256-SHA SSLv3 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256 AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1 AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256 AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1 DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1 Total
With ciphers finished. To support old clients, we need to return lower versions of TLS and, for speed, use a regular curve and a 2048-bit certificate.
server { server_name www.example.com example.com; listen 443 ssl default_server; ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem; add_header Strict-Transport-Security "max-age=31536000"; ssl_ciphers EECDH:+AES256:-3DES:RSA+AES:RSA+3DES:!NULL:!RC4; } With this config, we get exactly the same result as that of Google at the beginning of 2017.

At the same time, we know for sure that all clients open the site as quickly as possible without using weak ciphers: all modern browsers use ECDHE.
Also, you definitely need to configure OCSP stapling and, optionally, TLS cache sessions .
')
Source: https://habr.com/ru/post/325230/
All Articles