How hackers attack corporate WiFi: parsing attacks

Image: Manuel Iglesias , Flickr
Wireless networks are an integral part of the corporate infrastructure of most modern companies. Using WiFi allows you to deploy networks without cabling, and also provides mobility for employees - you can connect from anywhere in the office from a variety of devices. Of particular importance is the convenience of the company's customers, who, for example, need to use high-speed Internet access. A deployed wireless network allows you to do this quickly and comfortably.
')
However, the insecure use or administration of wireless networks within an organization entails serious threats. In case of successful implementation of such attacks on corporate Wi-Fi, attackers have the ability to intercept sensitive data, attack wireless users, and also gain access to the company's internal resources.
Attack Parsing: From Guest Network to Corporate
Get key access to the guest WiFi in most organizations is quite simple. This is a common practice, the convenience of customers or visitors is an important aspect of business, but this convenience is often created at the expense of security. As experience in security analysis shows, in many cases, after connecting to the guest network, access to other network segments, including LAN resources, can be obtained. Some systems that were accessed from the organizations' guest wireless network are shown in Figure 1.
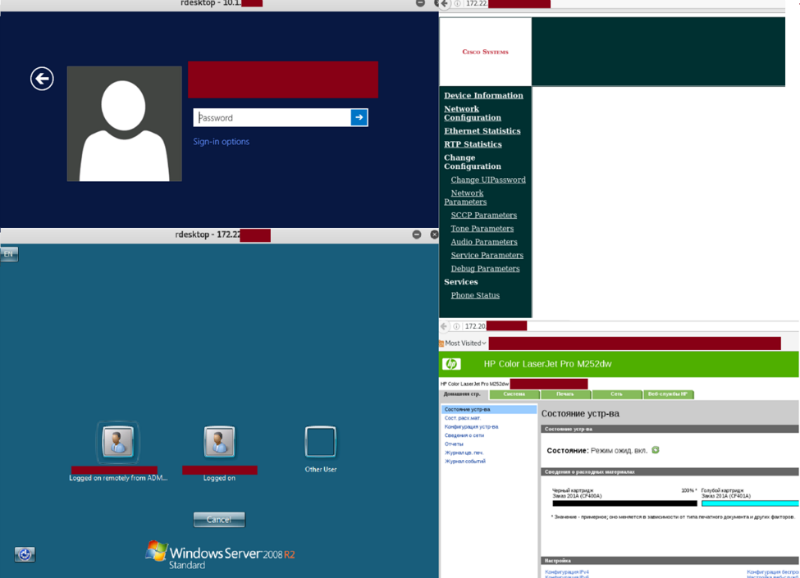
Figure 1. Access to a variety of LAN resources from a guest wireless network
An interesting fact is that employees of companies themselves regularly use the guest network, not suspecting that it is unsafe. For a guest network, encryption mechanisms are not always used. And if, at the same time, the access point does not isolate users among themselves, then an attacker who gains access to the guest network can attack company employees, listen to their traffic and intercept sensitive information, including credentials for access to various systems. The intruder can also combine this flaw with the use of a fake access point.
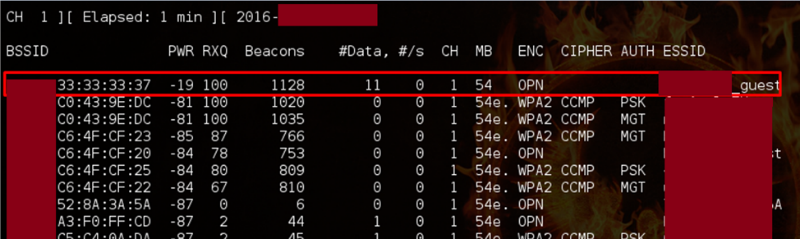
Figure 2. Lack of encryption mechanisms for the guest network
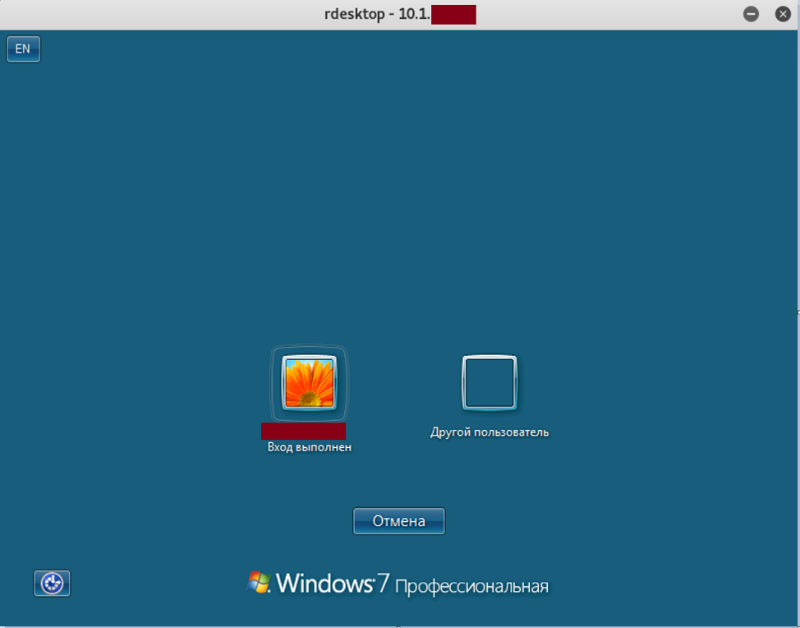
Figure 3. Access to employee workstation
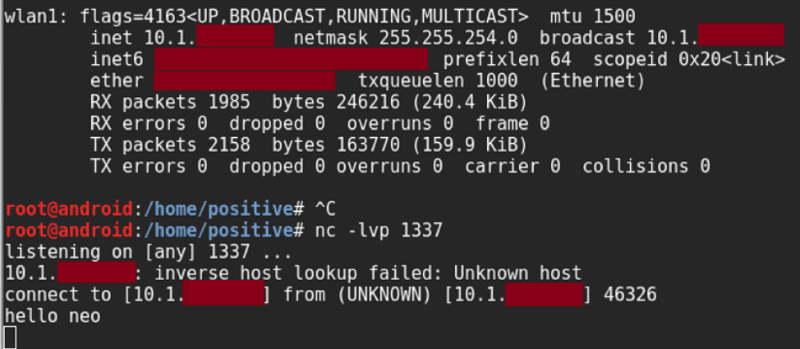
Figure 4. Demonstration of the possibility of direct exchange of information between clients of the guest corporate network
To increase the security of the guest network, you should use the access point user isolation mode, prohibit the use of the guest network by company employees, and strong encryption mechanisms (WPA2).
Where to learn about other attacks
Successful hacking of Wi-Fi allows not only to intercept sensitive information, attack other users of the wireless network, but also develop an attack to gain access to the company's internal resources.
Above, we looked at just one example of a possible attack on corporate WiFi, but there are many more: Organization of fake access points, exit from a guest Wi-Fi network to a corporate one, or exploitation of vulnerabilities of unsafe authentication protocols, etc.
On Thursday, March 30, at 14:00 , during a free webinar, Dmitry Katalkov, analyst of information security analytics at Positive Technologies, will review several illustrative scenarios of attacks on corporate WiFi that occurred in 2016.
Participation in the webinar is free. Registration link www.ptsecurity.com/ru-ru/research/webinar/194213/
Source: https://habr.com/ru/post/325226/
All Articles