Fake promises, aggressive ads, trojan downloaders and other Google Play surprises
ESET specialists have discovered another batch of malicious and unwanted applications on Google Play. They disguise themselves as legitimate programs and / or use social engineering methods to increase the rating. The total number of downloads of the “heroes” of this review exceeds one and a half million, and in most situations, the study of user feedback on Google Play would avoid installing potentially dangerous software.
Fake promises as a business model
')
An extensive category of these advertisements on Google Play has used social engineering techniques, begging users for high marks - this increased the number of subsequent downloads.
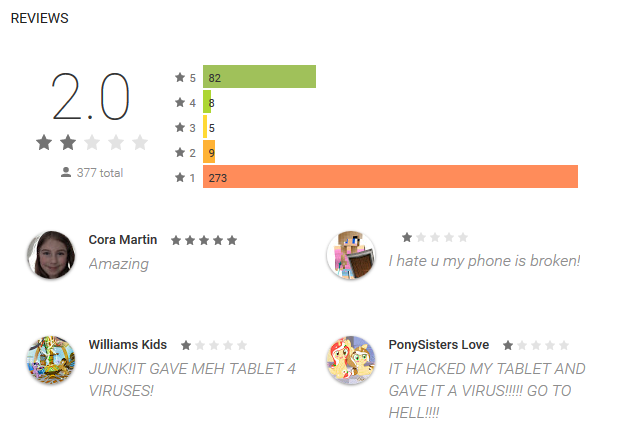
As a rule, non-existent functions were listed in the application description. After installing the device, a pop-up message was displayed promising to continue the installation or unlock the full version for a high rating on Google Play. As a result, the applications had an incredibly high rating; they were only given out by reviews of disappointed users.
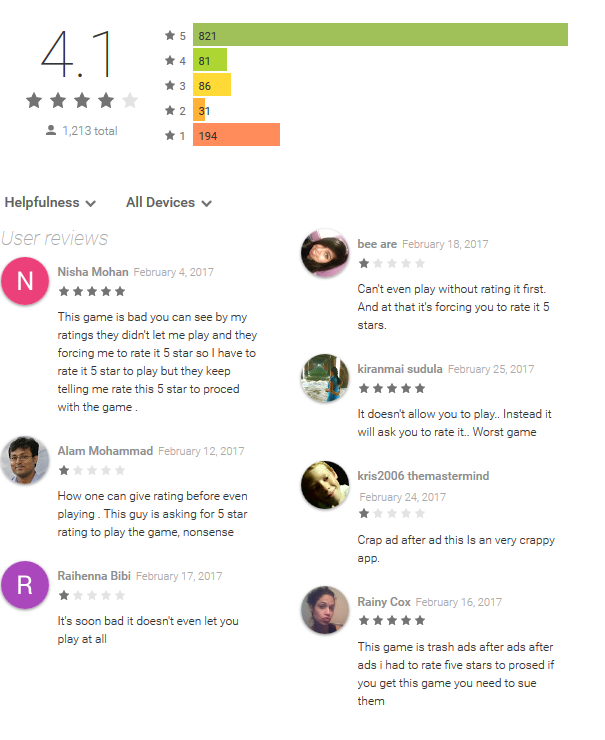
A classic example is the fake Subway Sonic Surf Jump game, which begged for a 5 * rating, promising to open full access to the functions, and in fact showed one ad banner after another. The application was installed by more than 500 thousand users, the average rating was 4.1 points, high marks were accompanied by outraged comments.
Other popular (by rating) apps - Anime Wallpapers HD and Latest online movies acted in the same way. They "sold" the missing features for 5 *, attracting users who do not read reviews.
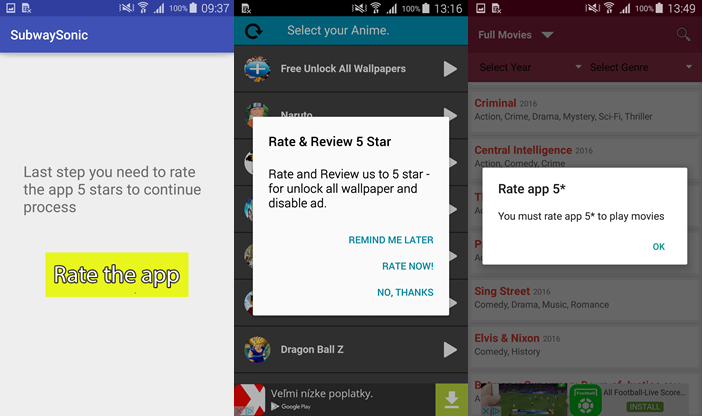
Another way to get high praise is annoying ads. Some applications showed advertisements in pop-up windows and promised to remove them in exchange for a five-point rating.
It is clear that these are empty promises, but the authors have no other way to improve the rating. They are not stopped even by a direct ban on cheating, as provided for by the rules of the Google Play Developer Policy .
Android / Hiddad.BZ: advertising trojan, winding rating
Among the applications that wind up the rating, a mobile Trojan is highlighted for displaying Android / Hiddad.BZ advertising.
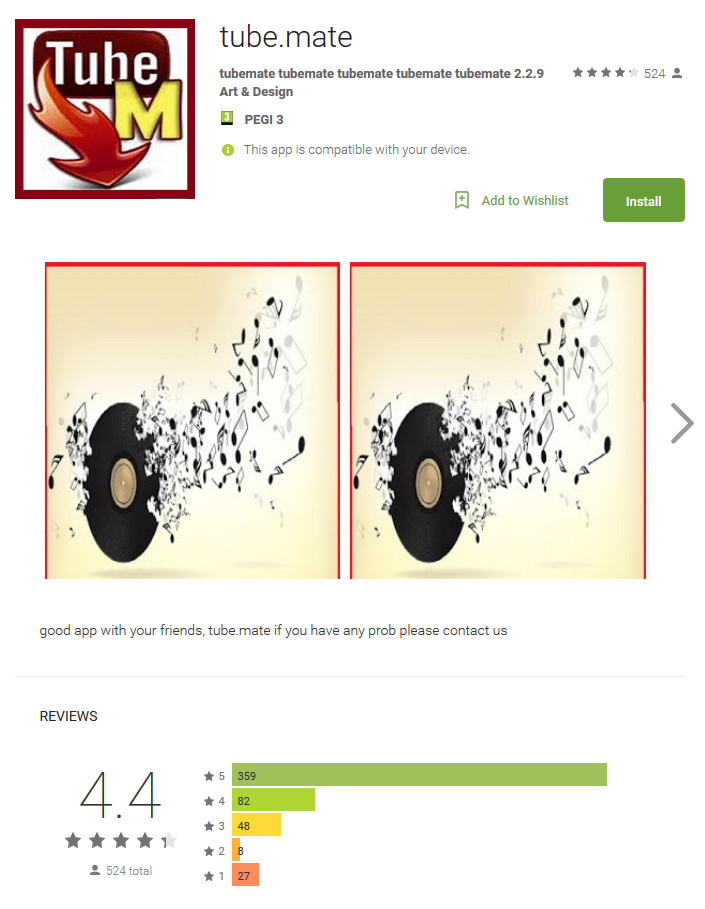
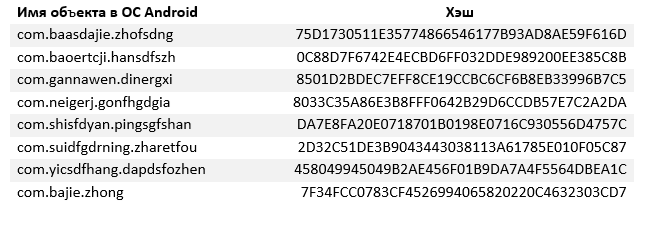
The program was disguised as a tool for downloading content from YouTube - seven applications with names like Tube.Mate and Snaptube. They were installed by up to 5,000 users.
Malicious software uses a number of methods to convince users to install an additional component that shows ads, and at the same time to put the application to a high rating on Google Play.

After installation, all seven applications were displayed on the device as Music Mania. Clicking on the corresponding icon, the user launched the download component to display ads. To do this, the program displayed a message suggesting the installation of a “plug-in for Android” and blocked the screen before pressing INSTALL. Further, the program requested the device administrator rights in the same way - displaying another message.
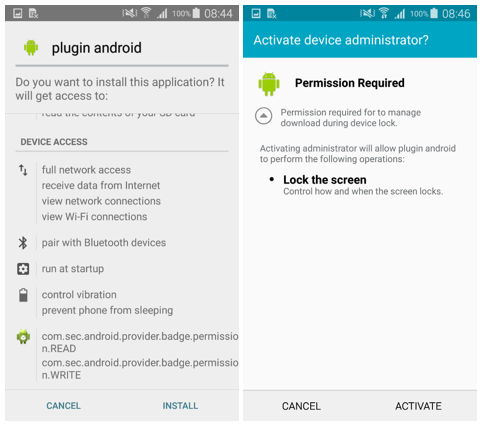
Having received administrator rights, the program showed the user advertising banners and offered to rate the application in 5 * to get rid of annoying content. Delete messages is useless - advertising banners will be even more, which in the future forces the user to evaluate the program when the offer appears again.
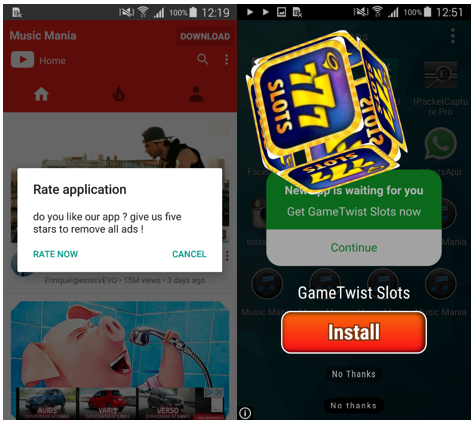
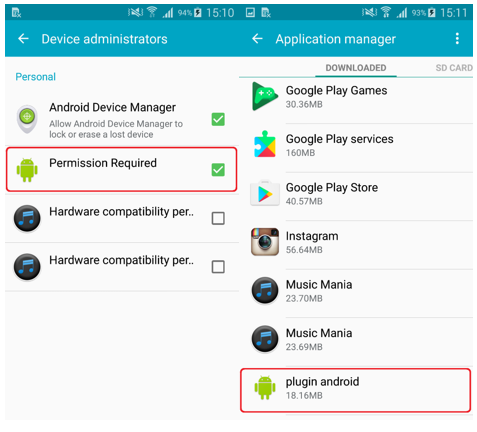
To clear the device from Android / Hiddad.BZ, you need to disable its administrator rights, manually remove the additional plug-in, and then the application itself (Music Mania) through the Application Manager. If you have a mobile antivirus installed, it also detects and removes this threat.
Android / TrojanDownloader.Agent.JL: Trojan Downloader with Adware
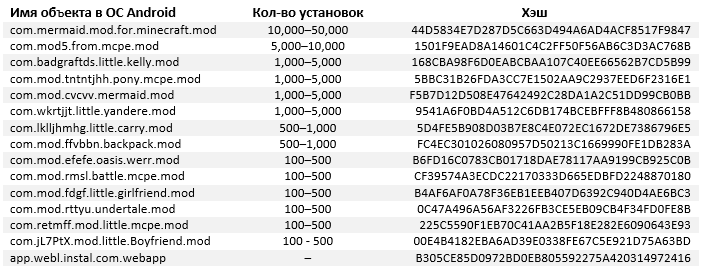
The next category of malware on Google Play, discovered by ESET experts, is a trojan downloader that displays ads on an infected device. This content was found in 14 applications masquerading as Minecraft mods. Malicious software downloaded a total of up to 80 thousand times.
Like Android / Hiddad.BZ, the trojan uses additional components to display ads. The ad module is not part of the original application - it must be downloaded from the network and installed manually by the user after launch.
The application has no real functions and shows annoying ads. As a result, it gives a low rating and negative reviews.
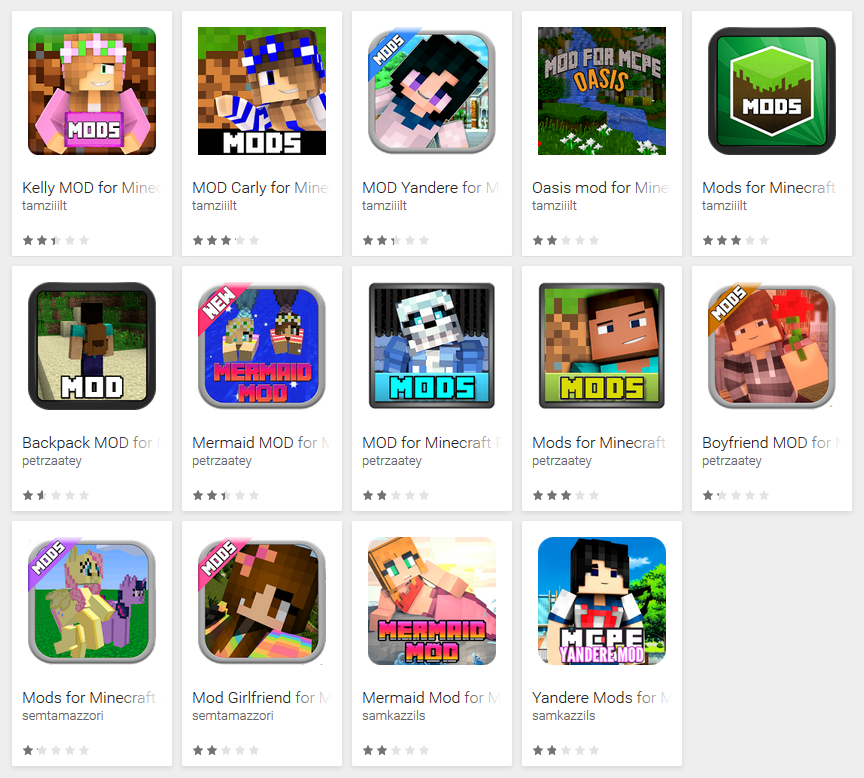
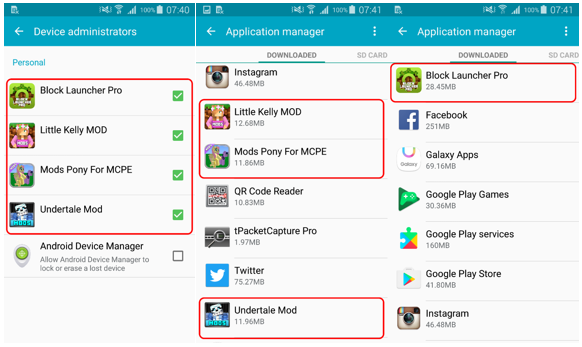
After starting the application requests the device administrator rights. When administrator mode is activated, a message is displayed on the screen with the INSTALL MOD button. At the same time, a push notification informs the user that an additional Block Launcher Pro module is required to continue the installation.
During the module installation process, the user is asked to grant him a number of permissions (including administrator rights). Additional components that are installed in the process are detected by ESET NOD32 products like Android / Hiddad.DA. The only function of such an application and an additional module is to display ads.

Interestingly, this Trojan downloader is an improved version of the application that first appeared on Google Play in February. In that version, a similar interface was used, she also requested administrator rights, but did not have the functionality to load and, unlike the current one, did contain Minecraft mods.
The updated version of the bootloader can theoretically download any software to the victim’s device. There is no reason to believe that the authors of the Trojan will limit the display of advertising. After working through the security crawl scheme of the Google Play service and deception of users, sooner or later they will take the next step - the distribution of more dangerous malware.
The chance to see and install one of the malicious applications when downloading Minecraft mods is quite large. To get rid of the bootloader, you can use a reliable mobile antivirus or manually eliminate the threat in the Application Manager by first disabling administrator rights for the application and the downloader module.
Android / FakeApp.FG: app to redirect to scam sites
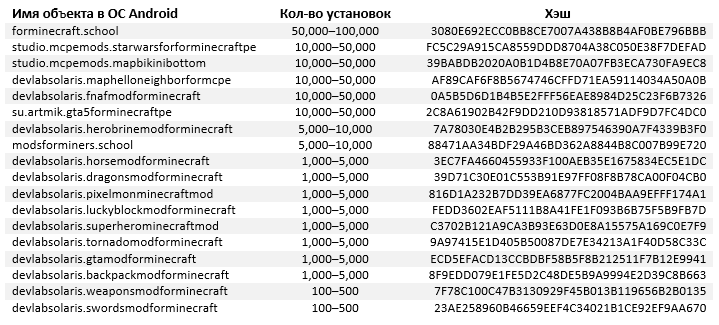
Another 73 fake Minecraft mods use the classic scheme, redirecting the user to the scam sites. These applications show up as Android / FakeApp.FG, they were installed up to 910 thousand times.
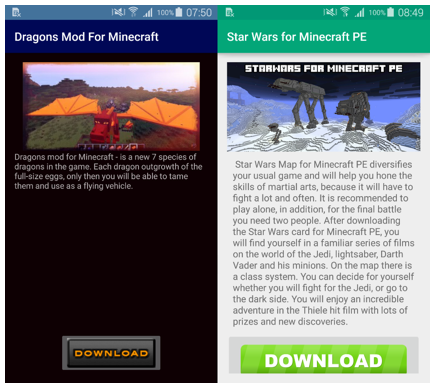
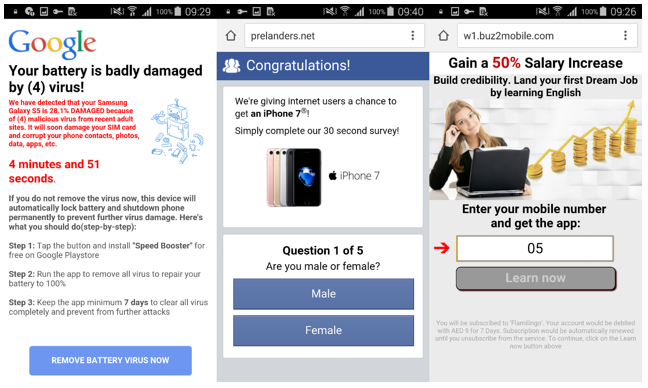
After launching, the application displays a message with the DOWNLOAD button. Clicking the button will not load any mods, but instead redirect the user to the site that opens in the default browser. The sites feature all sorts of intrusive content - advertisements, polls, "pranks", coupons, fake software updates and virus messages. Messages are localized - depending on the user's IP address.
Android / FakeApp.FG can be removed manually in the Application Manager or use the mobile antivirus.
Prevention
Even finding malware that has a rating on Google Play, we don’t refuse the main advice - check the application before downloading. In addition to the average rating, it is important to check user feedback. As the listed episodes have proved, users write honest reviews, even (especially) if they have already been persuaded to put an overestimation.
Samples
Android / Hiddad.BZ:
Android / FakeApp.FG:
For reviews of malicious applications, special thanks to virus expert Lukasz Stefanko .
Just in case, we remind you that ESET NOD32 mobile antivirus protects against such threats.

Fake promises as a business model
')
An extensive category of these advertisements on Google Play has used social engineering techniques, begging users for high marks - this increased the number of subsequent downloads.
As a rule, non-existent functions were listed in the application description. After installing the device, a pop-up message was displayed promising to continue the installation or unlock the full version for a high rating on Google Play. As a result, the applications had an incredibly high rating; they were only given out by reviews of disappointed users.
A classic example is the fake Subway Sonic Surf Jump game, which begged for a 5 * rating, promising to open full access to the functions, and in fact showed one ad banner after another. The application was installed by more than 500 thousand users, the average rating was 4.1 points, high marks were accompanied by outraged comments.

Other popular (by rating) apps - Anime Wallpapers HD and Latest online movies acted in the same way. They "sold" the missing features for 5 *, attracting users who do not read reviews.

Another way to get high praise is annoying ads. Some applications showed advertisements in pop-up windows and promised to remove them in exchange for a five-point rating.
It is clear that these are empty promises, but the authors have no other way to improve the rating. They are not stopped even by a direct ban on cheating, as provided for by the rules of the Google Play Developer Policy .
Android / Hiddad.BZ: advertising trojan, winding rating
Among the applications that wind up the rating, a mobile Trojan is highlighted for displaying Android / Hiddad.BZ advertising.
The program was disguised as a tool for downloading content from YouTube - seven applications with names like Tube.Mate and Snaptube. They were installed by up to 5,000 users.
Malicious software uses a number of methods to convince users to install an additional component that shows ads, and at the same time to put the application to a high rating on Google Play.


After installation, all seven applications were displayed on the device as Music Mania. Clicking on the corresponding icon, the user launched the download component to display ads. To do this, the program displayed a message suggesting the installation of a “plug-in for Android” and blocked the screen before pressing INSTALL. Further, the program requested the device administrator rights in the same way - displaying another message.

Having received administrator rights, the program showed the user advertising banners and offered to rate the application in 5 * to get rid of annoying content. Delete messages is useless - advertising banners will be even more, which in the future forces the user to evaluate the program when the offer appears again.

To clear the device from Android / Hiddad.BZ, you need to disable its administrator rights, manually remove the additional plug-in, and then the application itself (Music Mania) through the Application Manager. If you have a mobile antivirus installed, it also detects and removes this threat.

Android / TrojanDownloader.Agent.JL: Trojan Downloader with Adware
The next category of malware on Google Play, discovered by ESET experts, is a trojan downloader that displays ads on an infected device. This content was found in 14 applications masquerading as Minecraft mods. Malicious software downloaded a total of up to 80 thousand times.
Like Android / Hiddad.BZ, the trojan uses additional components to display ads. The ad module is not part of the original application - it must be downloaded from the network and installed manually by the user after launch.
The application has no real functions and shows annoying ads. As a result, it gives a low rating and negative reviews.

After starting the application requests the device administrator rights. When administrator mode is activated, a message is displayed on the screen with the INSTALL MOD button. At the same time, a push notification informs the user that an additional Block Launcher Pro module is required to continue the installation.
During the module installation process, the user is asked to grant him a number of permissions (including administrator rights). Additional components that are installed in the process are detected by ESET NOD32 products like Android / Hiddad.DA. The only function of such an application and an additional module is to display ads.

Interestingly, this Trojan downloader is an improved version of the application that first appeared on Google Play in February. In that version, a similar interface was used, she also requested administrator rights, but did not have the functionality to load and, unlike the current one, did contain Minecraft mods.
The updated version of the bootloader can theoretically download any software to the victim’s device. There is no reason to believe that the authors of the Trojan will limit the display of advertising. After working through the security crawl scheme of the Google Play service and deception of users, sooner or later they will take the next step - the distribution of more dangerous malware.
The chance to see and install one of the malicious applications when downloading Minecraft mods is quite large. To get rid of the bootloader, you can use a reliable mobile antivirus or manually eliminate the threat in the Application Manager by first disabling administrator rights for the application and the downloader module.

Android / FakeApp.FG: app to redirect to scam sites
Another 73 fake Minecraft mods use the classic scheme, redirecting the user to the scam sites. These applications show up as Android / FakeApp.FG, they were installed up to 910 thousand times.

After launching, the application displays a message with the DOWNLOAD button. Clicking the button will not load any mods, but instead redirect the user to the site that opens in the default browser. The sites feature all sorts of intrusive content - advertisements, polls, "pranks", coupons, fake software updates and virus messages. Messages are localized - depending on the user's IP address.


Android / FakeApp.FG can be removed manually in the Application Manager or use the mobile antivirus.
Prevention
Even finding malware that has a rating on Google Play, we don’t refuse the main advice - check the application before downloading. In addition to the average rating, it is important to check user feedback. As the listed episodes have proved, users write honest reviews, even (especially) if they have already been persuaded to put an overestimation.
Samples
Android / Hiddad.BZ:


Android / FakeApp.FG:

For reviews of malicious applications, special thanks to virus expert Lukasz Stefanko .
Just in case, we remind you that ESET NOD32 mobile antivirus protects against such threats.
Source: https://habr.com/ru/post/325188/
All Articles