How to let cryptographers sink a company

So far, not all system administrators have enjoyed their full acquaintance with crypto-fiber, although many are trying. In this article, I will explain what needs to be done to facilitate the entry of the cryptographer into the infrastructure and to ensure the most devastating consequences.
Depending on the worldview and mood, what is written can be perceived both literally and creatively.
Attack Vector and Perimeter Defense
Most often, cryptographers get into the infrastructure in two ways - via email, or outside, through RDP. With the mail, everything is clear: the letters "from the tax" and "from the bank" reach their recipients even through spam filters (it is better, of course, to disable them altogether). But on the second method, I will focus in more detail.
First you need to open RDP outside - it will be easier for employees to work, without any uncomfortable VPNs there. If the boss wants to increase information security, just hang the external RDP port on another. This does not interfere with scanners, and the boss may calm down.
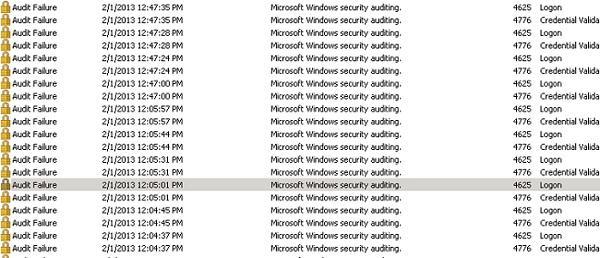
Brutfors when auditing failed login attempts is enabled
The virus will try to get to your server using brute force. In order to maximally entreat this task to him, perform the following "tuning":
On the terminal server, disable account lockout, which works after several failed login attempts;
If the terminal server has a fail2ban equivalent, for example, Ts_block , EvlWatcher or RdpGuard , then remove it immediately. This service will provide you with blocking on the firewall IP-address after unsuccessful attempts to connect. You do not want to interfere with hacking, right?
- Passwords of users and administrators should be as short and simple as possible - ideally, consist only of numbers. If management suddenly orders action, turn on password complexity requirements. This does not interfere with the cryptographer if you do not put a length limit. Without length restrictions, users will use dictionary passwords, because they are more convenient than complex combinations and easier to select.
When the RDP is open outside, all users have simple passwords, and letters with links to archives regularly come to the post office, the virus will not keep itself waiting. The administrator’s next task is to facilitate the new arrival of decent feeding in the infrastructure.
We optimize infrastructure
When the cryptographer "knocks" to you in the form of a letter from the "prosecutor's office", the system can be alerted. Here the user downloaded the archive, launched the executable file, but when starting up a message appears:
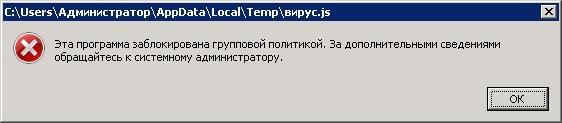
This means that the Software Restriction Policies (SRP) policy is enabled on the system. This technology appeared at the time of Windows XP and its principle of operation is very simple: with a configured policy, none of the executable files, except the ones allowed, will be launched. And only exploits will remain really dangerous for the system.
Fortunately for coders, rare administrators include this policy. If your system is “unlucky” and protection is working, then you need to change the domain or local group policy, setting the default security level to “unlimited”:
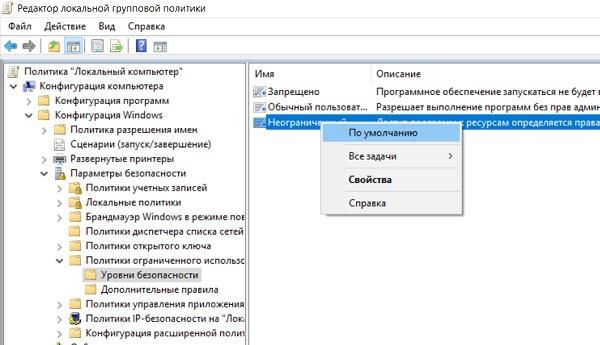
But management can pay attention to disabling the policy. In this case, you can open another loophole for the virus. Usually, when configuring SRP, executable files from system folders are allowed to run, but one thing is left out: the system folders have subfolders in which the user has rights to create files. For example, the path C: \ Windows \ Temp:
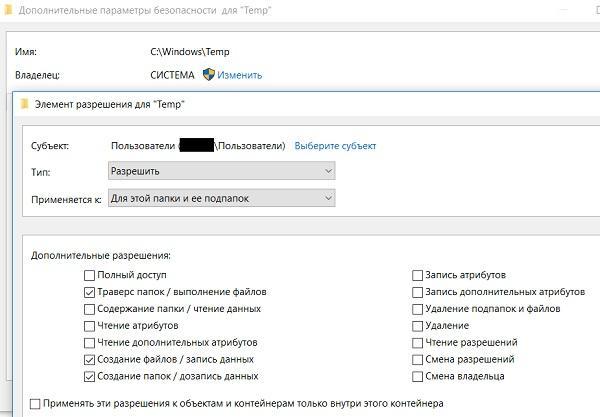
In the security settings, allow the creation of files and their execution
A complete list of interesting subfolders in the system directories can be obtained using Powershell or through utilities like DumpSec .
Get–ChildItem C:\Windows\ –recurse | Get–Acl | export–csv filename.csv To cipher operators who get into the system via mail, this, of course, will not help. But if the author of the virus has received unprivileged access to the server, then he will be able to upload executable files to these folders and encrypt anything. An experienced encryption master can also get password hashes (especially if the system uses NTLM), and through them open the hash through brute force and discover already privileged access. For NTLM to work instead of secure Kerberos, it’s enough to access network resources not by name, but by IP address.
Administrator rights on computers also help in obtaining hashes. Therefore, if the user needs access to specific applications, then you should not allocate his computer in a separate VLAN. Optimally, with the rights of the local administrator, immediately issue and domain.
If the policy of limited use of programs is disabled, then the antivirus can be left: all the same, the encryptor who uses the installed archiver, the antivirus can be caught only by signatures. At the same time, UAC must be disabled.
Now the virus is guaranteed to be able to penetrate the infrastructure and encrypt useful data. However, for the final triumph, this is not enough: after all, you will have backup copies that will quickly restore their functionality. So what? That's right, adjust the backup settings - so as not to interfere ...
Configuring backup
Do not turn off the backup completely - it will cause a lot of questions, even for not very savvy employees, when you suddenly can not restore the deleted file at their request.
There are more elegant ways to make system recovery after a coder’s attack impossible:
The backups must be on the same server: the encryption cipher encrypts them, and the existing shadow copies will delete them;
Files must be archived with the extension .zip or .bak. God forbid billgates, there will be files .exe or even without an extension - our "animal" can skip them!
It is undesirable to make backups to the cloud or to a network share connected by a separate username - so it will be difficult for the virus to reach them;
Another good option is to set up a backup in a shared folder with “All - full access” rights.You should not keep backups for a certain period: it is better to create backup copies on a daily basis, erasing previous ones. And you do not need to enable for backup copying settings for your own protocol in your repository;
- Another thing you should not forget about is that the built-in backup tool for Windows can make backups to a hard disk that is invisible in the system. This is inconvenient for both you and the cryptographer.
Now, after the cipher attacker can be sad, but confidently say that there are no backups. This is victory!
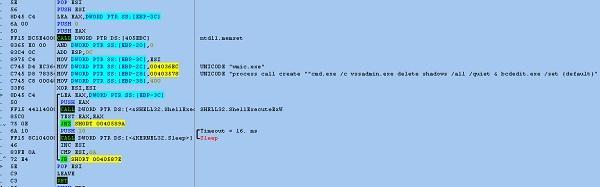
Spora ransomware removes shadow copies using the vssadmin.exe command and disables recovery in the boot loader. UAC could stop this action.
Although not - you can make the final chord and become an intermediary between the organization and the authors of cryptographers. To do this, tell the boss that the extortioners do not have to pay, but there are companies involved in decoding. After that, take from him an amount equal to that which the extortioners are asking plus throw a percentage - and voila, a quiet monetary joy was added to the moral pleasure. You can safely consider yourself a god of systemic intrigue and ... it is better to quit.
Now seriously
On writing this article, the eleventh in the past six months was inspired by an appeal from organizations affected by the coder's actions. When investigating the attack vector, there were wonderful things like the open RDP for user “1” with password “1”, open attachments from letters “from the bank”, and the researcher who mixed up the isolated sandbox computer with the blast machine.
It's a shame that the simplest setting of the SRP and the perimeter closed a little more seriously would help avoid the sad consequences. I hope the material will help someone to organize the protection of the enterprise more rationally, or at least think about it.
')
Source: https://habr.com/ru/post/325080/
All Articles