Huawei USG 6320. First View of Zisovod

All tsiska, yes tsiska with its firewall. But here we have taken on the test of the ITU from Huawei. And fashionable ITU, a new generation. We looked, felt, decided to share first impressions. I’ll say right away that we didn’t carry out any load testing, we only got acquainted with the functionality.
The model Huawei USG6320 came into our hands. (Not to be confused with Zywall USG by the way from Zyxel).
This is the second after the youngest model (USG6310) in the USG6000 lineup for small and medium businesses. A little confused by the success stories of this solution on the manufacturer's website:
Anyway.
')
Appearance photo:
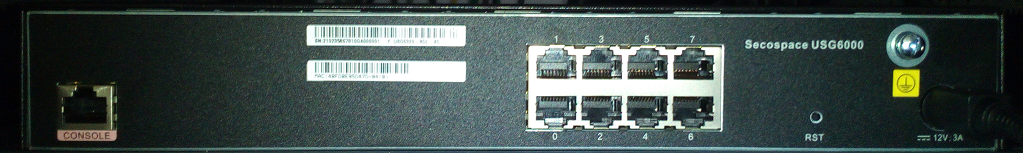
Outside 8 gigabit ports and console port. It would seem, everything is simple. But the fun site e.huawei.com again warns:
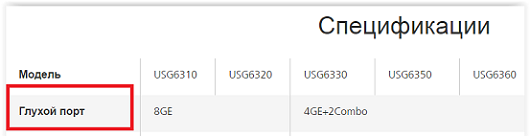
So. Ports are deaf? Seriously? How does this affect packet transfer? May not hear collisions in the environment? Or will there be problems with Spanning Tree, Listening State - “A? What? BPDU come or not? Repeat, can not hear! ". Well, okay, if something goes wrong, I lend a hearing aid from my grandmother.
Turn on the device, connect to the console. After loading we have the command line. Instead of conf t - system-view, instead of show - display. Ok, you can live. Of course, it’s not a good idea to mess around with an unfamiliar command line, I want to quickly see the GUI. Therefore, we configure the IP address on the interface, check that the interface can be connected and that the web services are running, and open the browser.
Commands for verification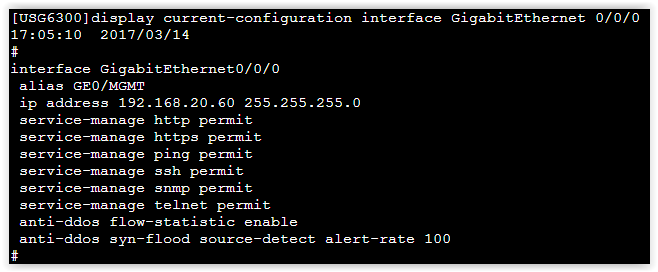


The Web interface immediately kindly offers to go through a simple Wizard to set the initial screen parameters: IP addresses of the external and internal interfaces, connection to the provider, DHCP for the local network, etc.
Startup wizard

Do not forget to check the box “Do not display this page upon the next login”, otherwise Huawei will kindly offer Startup Wizard after each connection to the Web interface.

By the way, as it turned out, if you enter the login / password several times when connecting to the device (web, ssh, telnet), Huawei takes offense for 10 minutes and stops communicating with you (picture of a shy Chinese). Honestly, I immediately find out how this behavior is turned off, I did not succeed. Well, okay, maybe the ports are deaf.
Overview of the graphical interface and device capabilities
Joking aside, more to the point. Immediately, I note: Web-interface is logical and intuitive. Everything works very quickly, especially when compared with the heavyweight Cisco FMC.
At the top there are six tabs: Dashboard , Monitor , Policy , Object , Network , System :
Dashboard tab . It's all clear. Some infographics, device information, licenses, syslog messages, etc.
Dashboard screenshots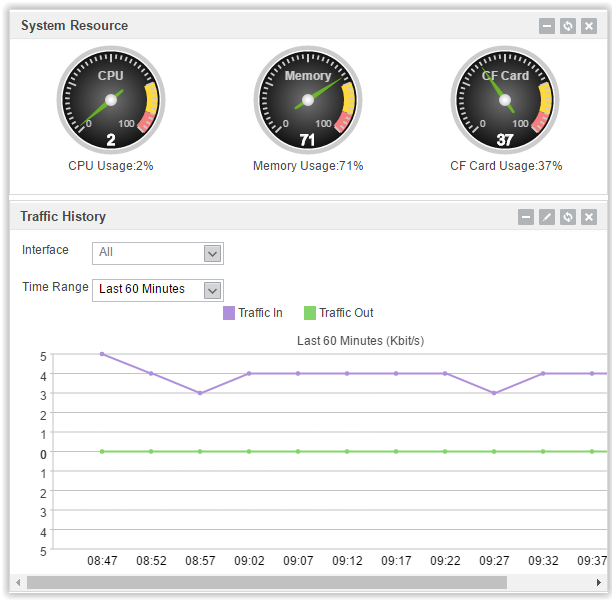



Monitor tab . Here you can see information about current connections, some statistics.
Screenshots Monitor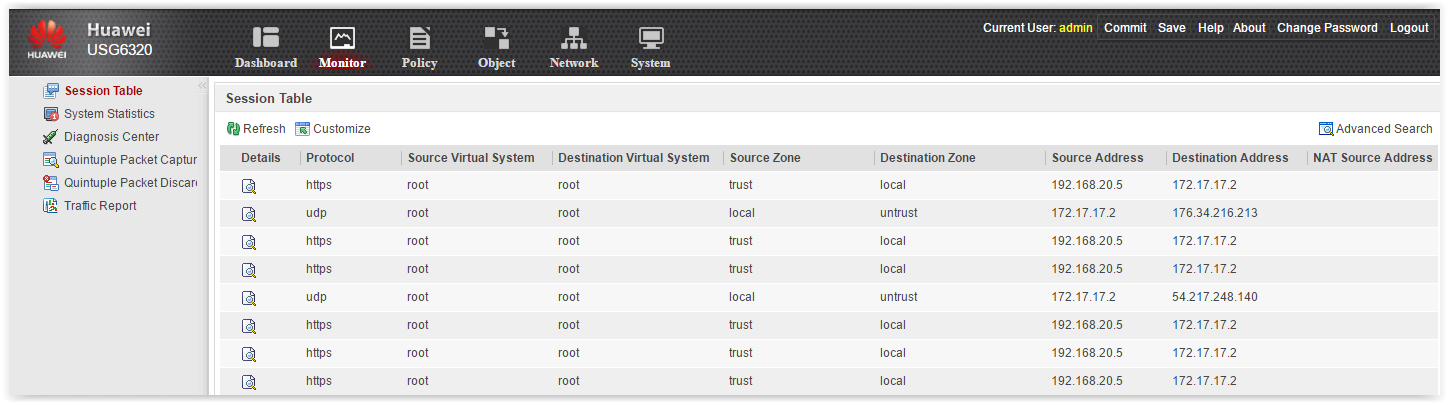


Here are some diagnostic tools. Nice that there is
Packet tracing
and
Packet capture

Policy tab . The most important tab. All traffic management policies are consolidated here:
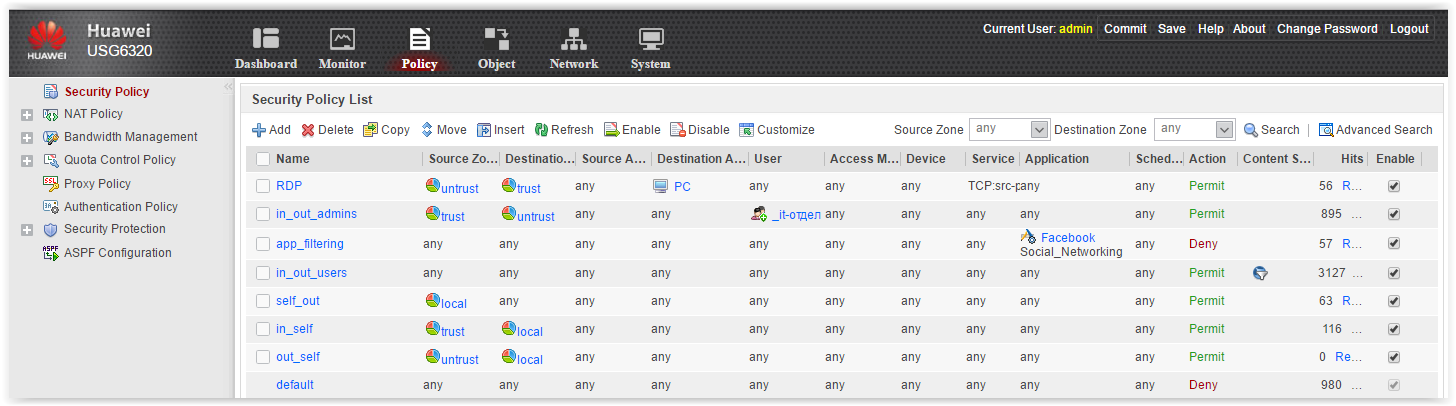
- Security Policy - large access list.Classic tabular display
- NAT Policy — all necessary IP address translation options: dynamic NAT, server publishing, NAT exceptions, etc.NAT
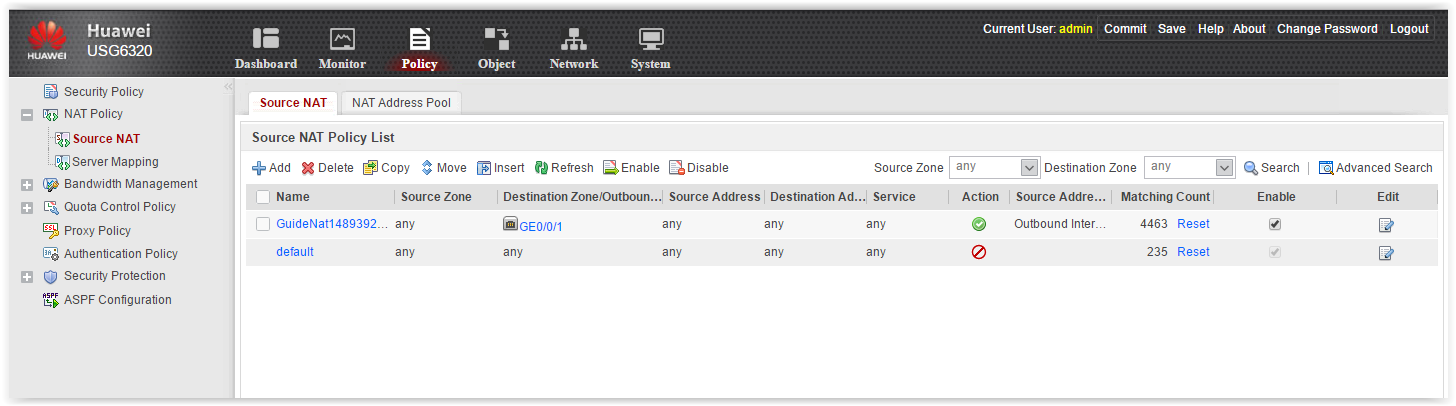
Nuance. There is no possibility to configure Destination NAT. And this is sometimes useful. For example, when, for some reason, the address of an external resource is firmly “sewn up” on the service, and this same external resource moves to a different IP address. Faced, it happens. Well, it's the little things ... - Bandwidth Management and Quota Control . Cool, that is. Highly demanded.
- Proxy Policy . You can enable non-caching proxying. The device can proxy user requests, that is, Huawei gets into a TCP session gap between the client and the server:
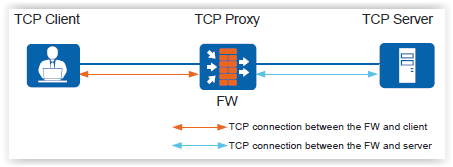
There are two proxying options: TCP Proxy and SSL Decrypt. The last option is to decrypt SSL traffic. Decryption works as standard, with certificate substitution. Test failed: SSL Decrypt requires an additional non-realistic license. Moreover, the policy can be configured, they just do not work. - Authentication Policy . Oooh, this is one of my favorite topics - user authentication, AD integration and all that. In the policy settings, everything is simple: choose a traffic pattern and say whether to authenticate or not.Auth policy
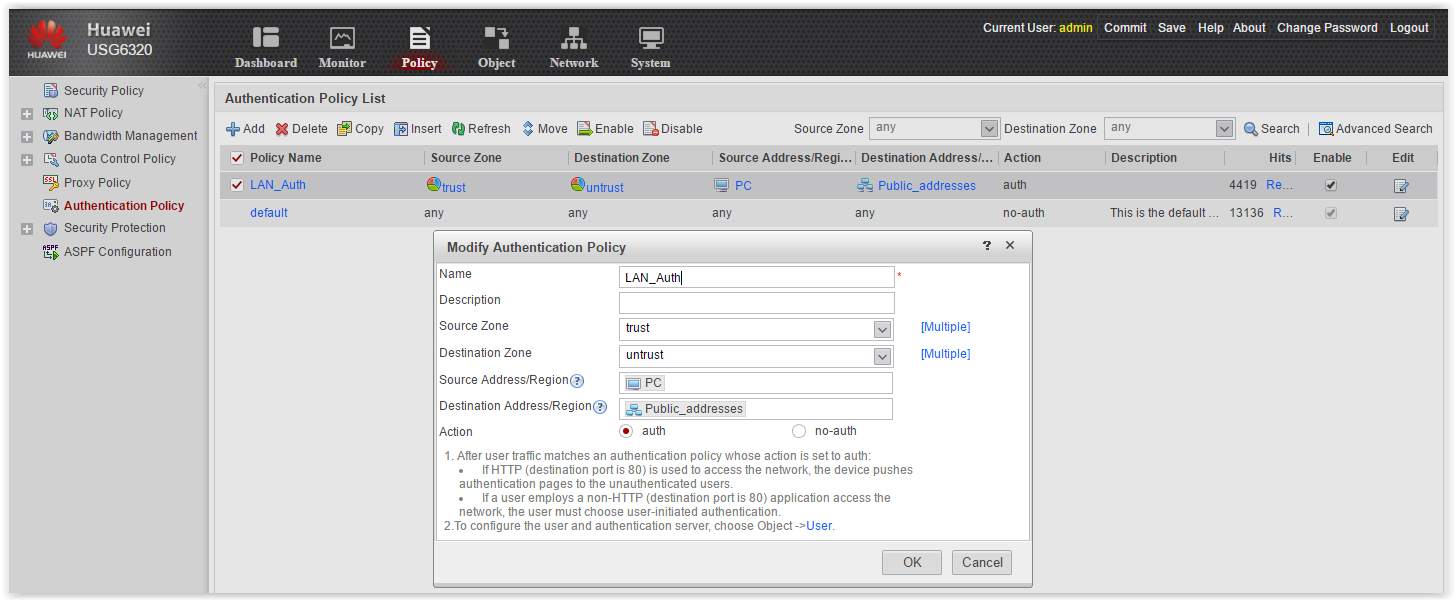
How exactly to authenticate users is configured in another tab - Objects - in the settings of the authentication domain. But once in another tab, then we will return to this issue later. - Remain Security Protection and ASPF . I will not stop in detail. In short, Security Protection includes various protection against DDoS attacks, flooding, IP Sweep, Port Scanning, defragmentation, blacklists, and so on and so forth.
ASPF (application specific packet filter) is an inspection of packets for opening additional sessions through a firewall. For FTP, SIP, H323, etc.
Objects tab . Here everything that is subsequently applied in policies is configured (on the Policy tab). In particular, everything related to Content Security. For example:
- Antivirus settingsScreen
- IPS settingsScreen
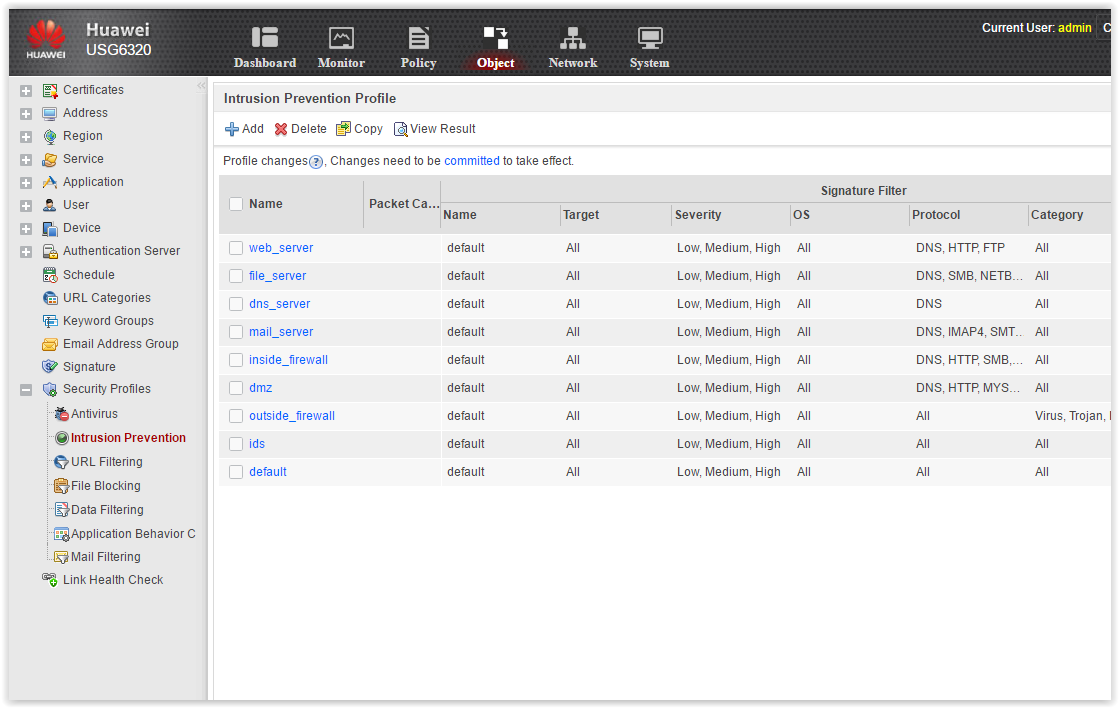
- URL filtering profileScreen
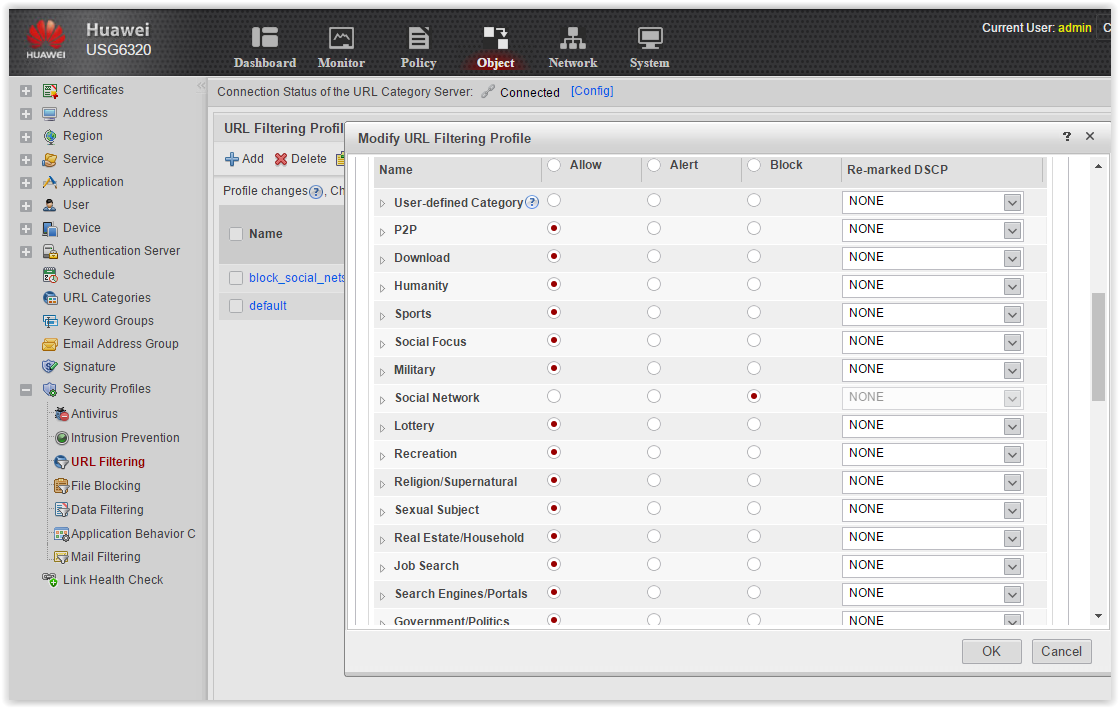
- Email ProtectionScreen
- Etc.
Network tab . Here we set up our interfaces, routing and VPN.
Network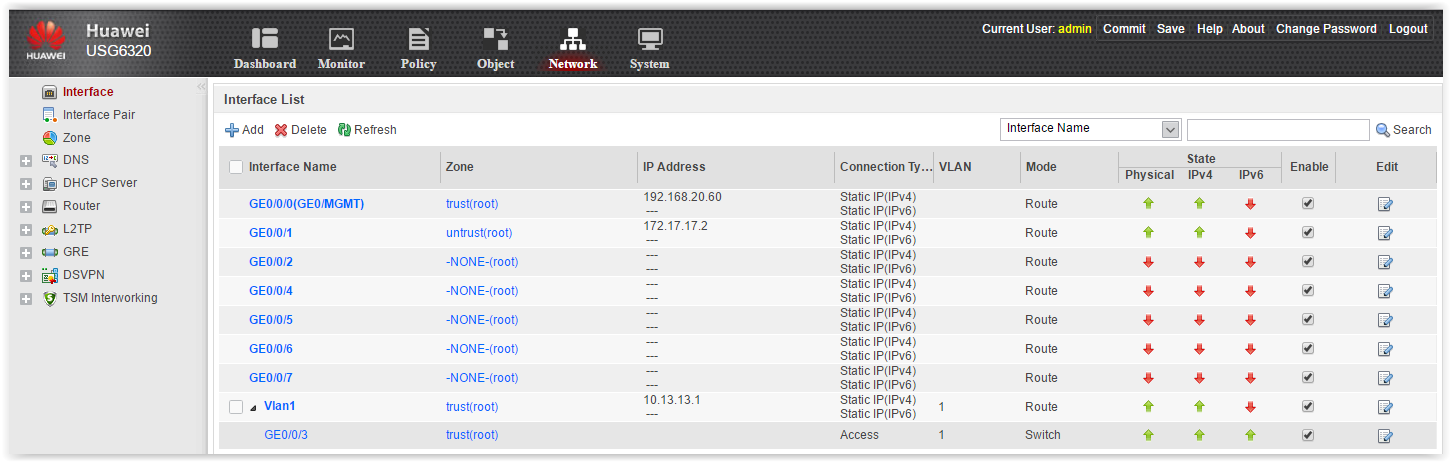
I will not dwell here in detail, I will mention only a few points:
- Interfaces By default, all interfaces are routed. But any interface can be made switched, configured as access or as trunk. You can add interface vlan, subinterface, aggregate ports. In general, in terms of interfaces, everything is very, very flexible. This is a plus.
- Routing There is a PBR, there are options for balancing on WAN ports. You can add tracking to static routes. From dynamic protocols are present RIP, OSPF and BGP.
- VPN . There are L2TP, GRE, DSVPN. The latter is an analogue of DMVPN in tsiska. Stop. But where is IPsec? Where is SSL VPN? I remember exactly what I saw in the bulletin data on IPsec and SSL VPN. Ok, we study the user manual. We find the following phrase:
The IPSec VPN and SSL functions are in accordance with Russian laws.
Gee. Are there no options to use these services in Russia? - Of course there is. As it turned out, we got a piece of hardware from the PWE (payload without encryption) software. That is, as NPE (no payload encryption) at tsiska. In order not to receive permission from the FSB, such devices are imported. To start encryption, full-fledged software is simply downloaded and installed. By the way, without problems, you can enter a piece of hardware with encryption officially - with obtaining permission from the FSB to import. In this case, the delivery time will simply increase.
System tab . There is nothing interesting here - standard system settings: time, SNMP, administrator accounts, logging, licenses, updates, upgrades, etc. In general, the narrative is limited to a screenshot.
Screen

Let's go back to the Security Policy and see them in more detail. This is the place where all the functions of the device are combined. Click Add and see what can be configured in terms of filtering traffic.
Add Security Policy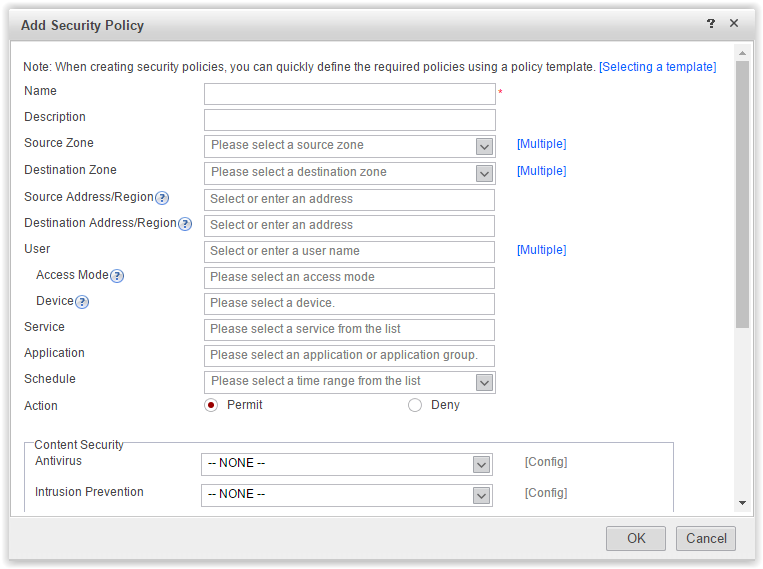

The first options are classic firewall: zones and IP addresses. Just below - Services. These are port numbers. Everything is standard.
More interesting options.
- User . If an authentication domain is configured, you can select existing users and user groups in this tab. In my example on the device the basis from corporate AD is tightened.User
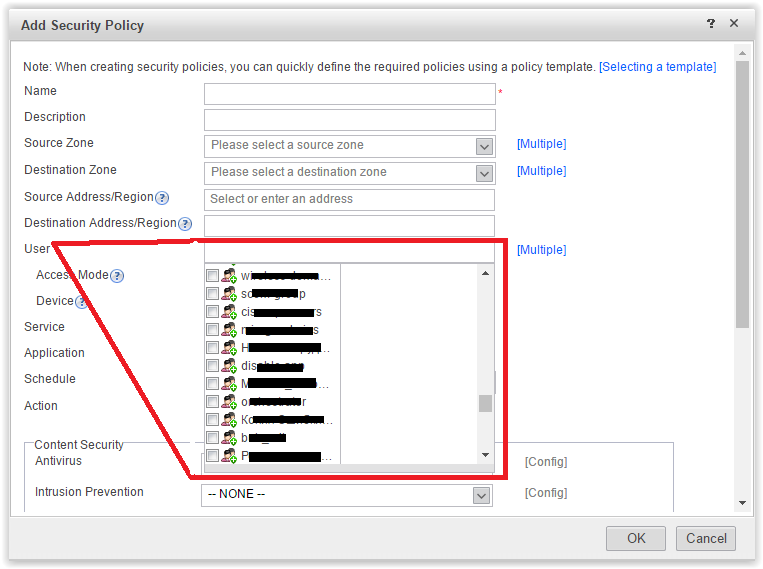
Additional options User -> Access Mode . If authentication is performed using a third-party access server - Terminal Security Management (TSM), you can monitor users depending on how they connect to the network.User → Access Mode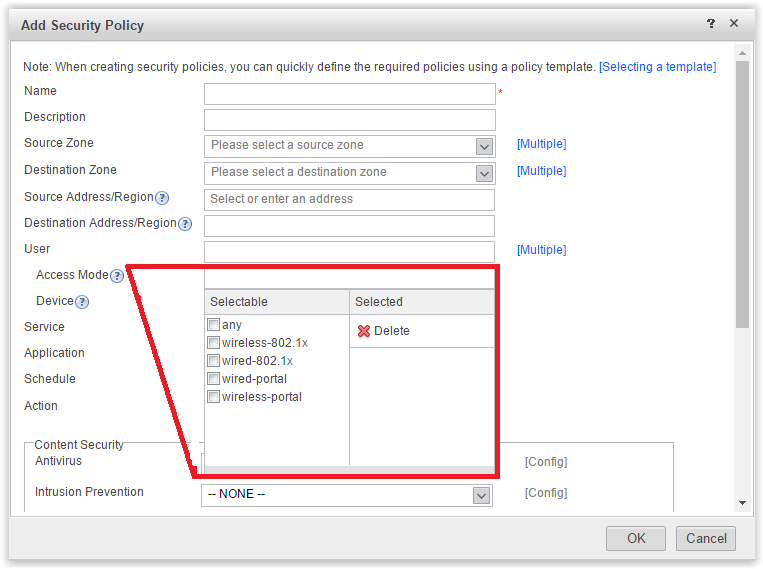
Additional options User → Device - an indication of the TSM server. As I understand it, TSM is an analogue of Cisco ISE. Allows you to implement 802.1x, provides control of connection to the network of end equipment. Cool. - Application . Required for ITU new generation. Allows you to select various Internet applications.Application
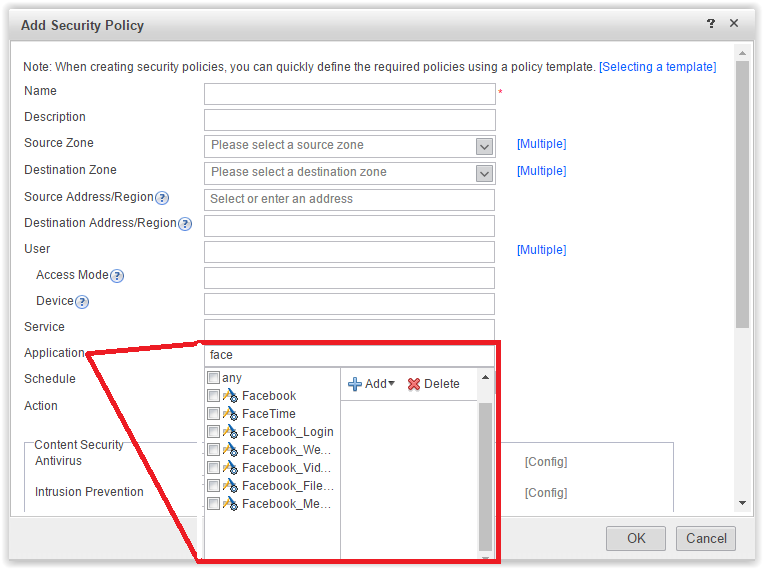
Existing application signatures can be found in more detail in the Objects tab.Application list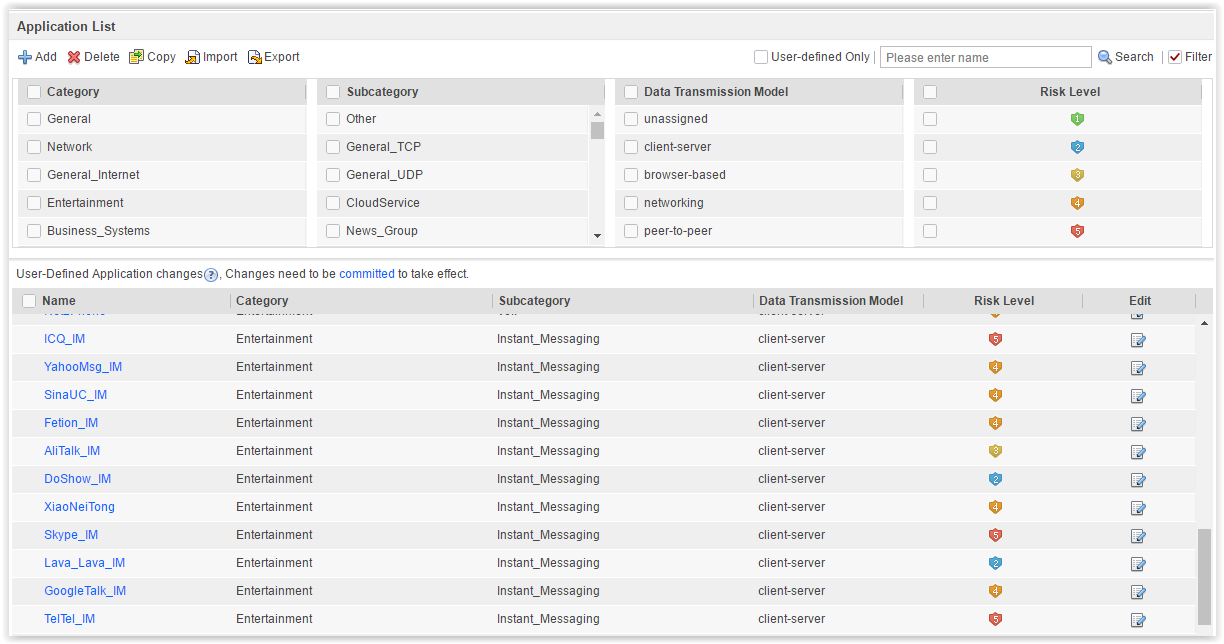
It is seen that the applications are categorized and ranked by risk. It is possible to create signatures of your own applications.
The abundance of specific Chinese applications catches the eye. Here are some funny names: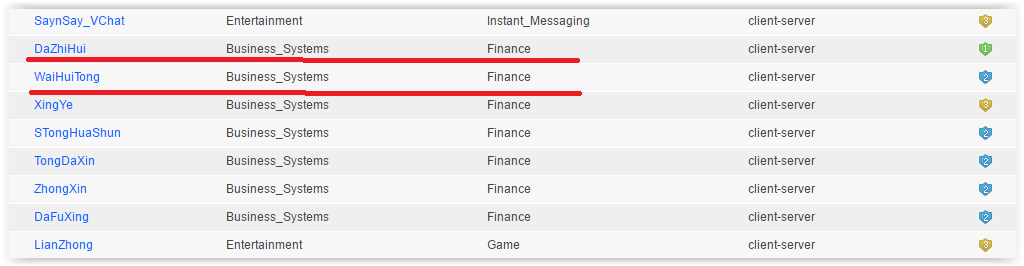
And indeed, how often in Russia we hear “WaiHuiTong does not work for me”, or we suggest that the authorities visit DaZhiHui. In general, an exclusive and irreplaceable functionality for our realities. - Scheduling is another nice option.Scheduling
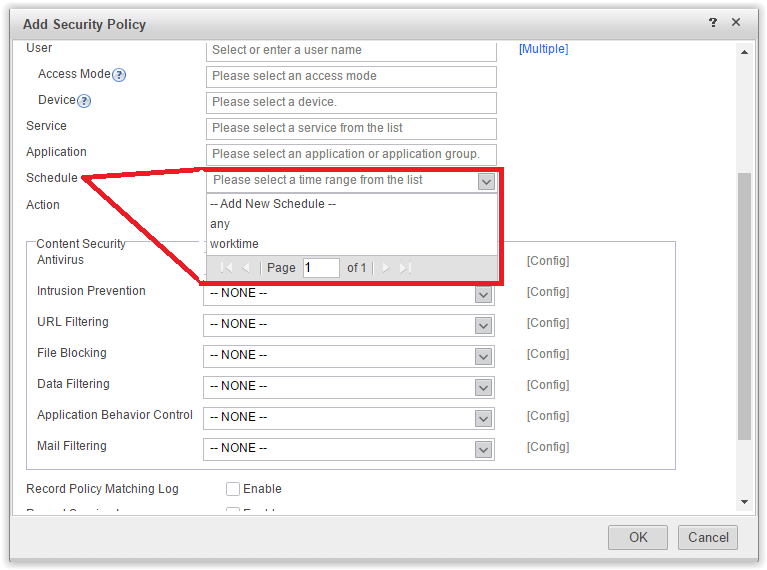
- The remaining options are for content security.Content security
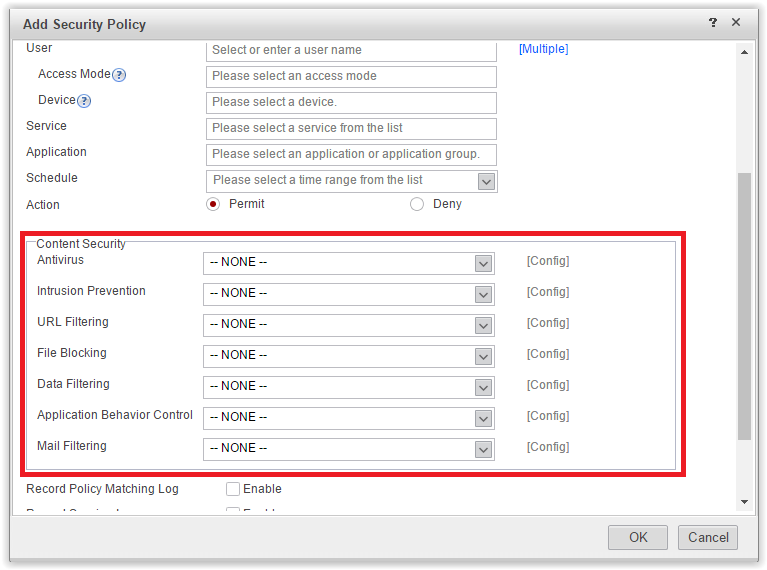
As you can see, the device has a powerful set of content security tools:
- file antivirus;
- IPS;
- URL filtering;
- File transfer control;
- Protection against information leakage;
- Additional application control. This again refers to the transfer of files and information within specific applications.
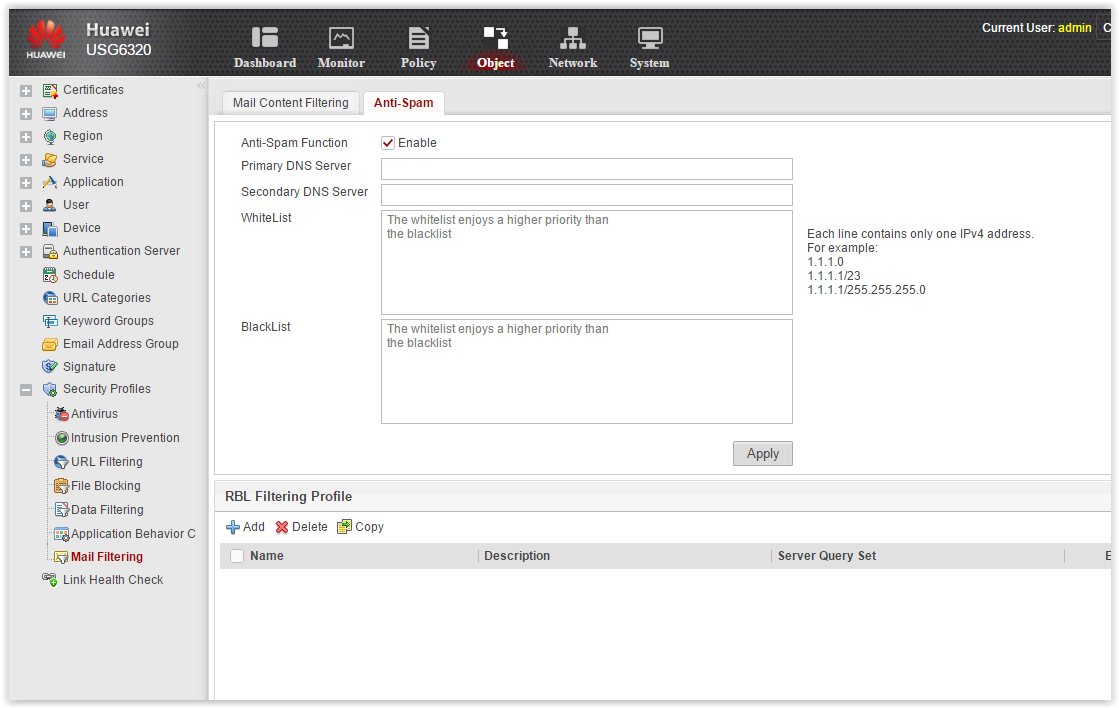
- Email filtering, including integrated anti-spam.
In general, the functionality of the device is very wide. The device not only fits perfectly with the definition of a new generation of ITU, but can also compete in the UTM segment. At first glance, everything is cool. But how effective the presented functionality is and how efficiently each module works out is the topic of deeper research. I do not want to go into boring arguments here, because now it’s just about first impressions about the device.
Some settings
So, with the capabilities of Huawei more or less familiar. Let's go to the settings and tests.
Consider authentication . As promised, I’ll deal with integration with AD in a little more detail. Who cares, I ask under the cat.
AD integration
First you need to configure the Authentication Server. Select the type of LDAP server.
Set the parameters of the LDAP server.
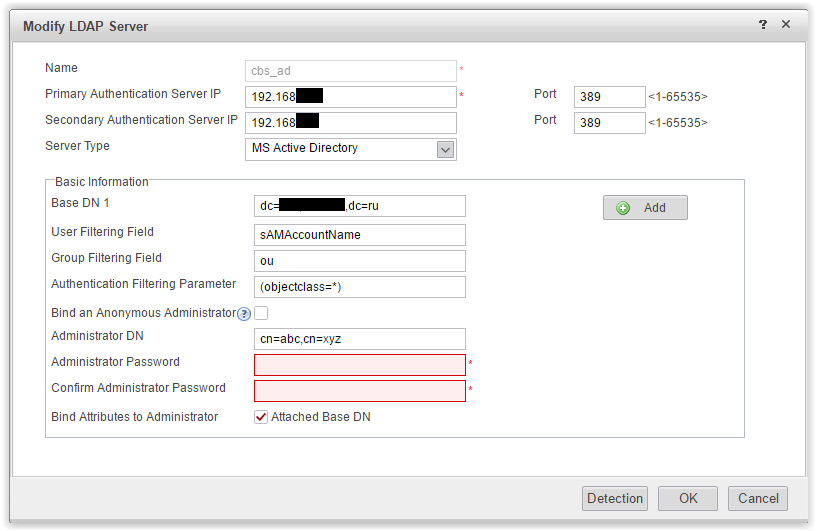
By the way, by default, in the “User Filtering Field” field, Huawei suggests using cn. For my account in CN = Boris Uskov. And I was pleasantly surprised that Huawei is not experiencing any problems with Cyrillic. Cyrillic is perfectly displayed in the policy settings. Moreover, during testing, when in the authentication process you enter into the login window "Boris Uskov" - authentication is successful. However, for convenience, I replaced the User Filtering Field with sAMAccountName and began to use my usual AD login.
After filling in the parameters, we acquire Detection and check that the connection with the LDAP server is established successfully.
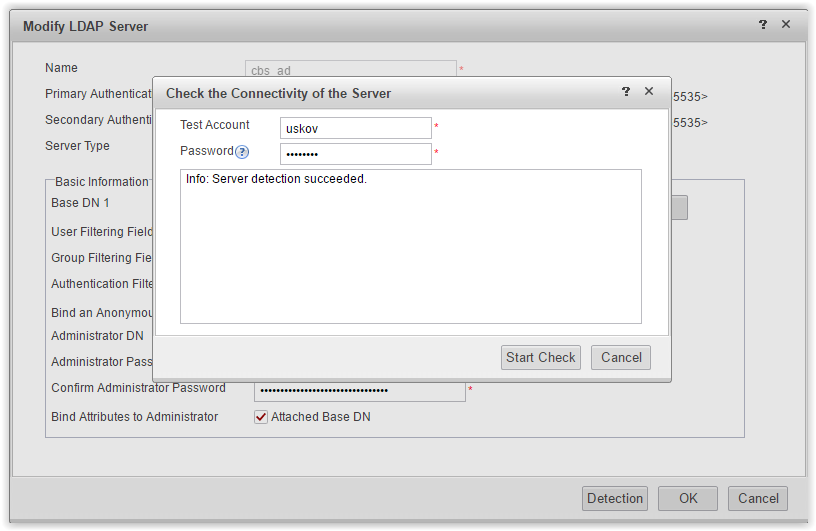
Now that we have established a connection with the LDAP server, we can pull up the user and group directory on Huawei so that we can use the names in the policy settings. This is done in the User Import menu on the Server Import tab.

Here you need to create a profile to import users from the directory.
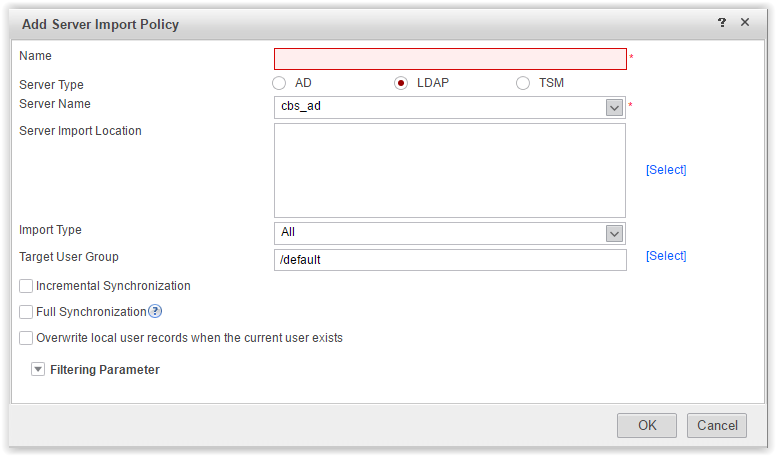
It remains to configure the Authentication domain.
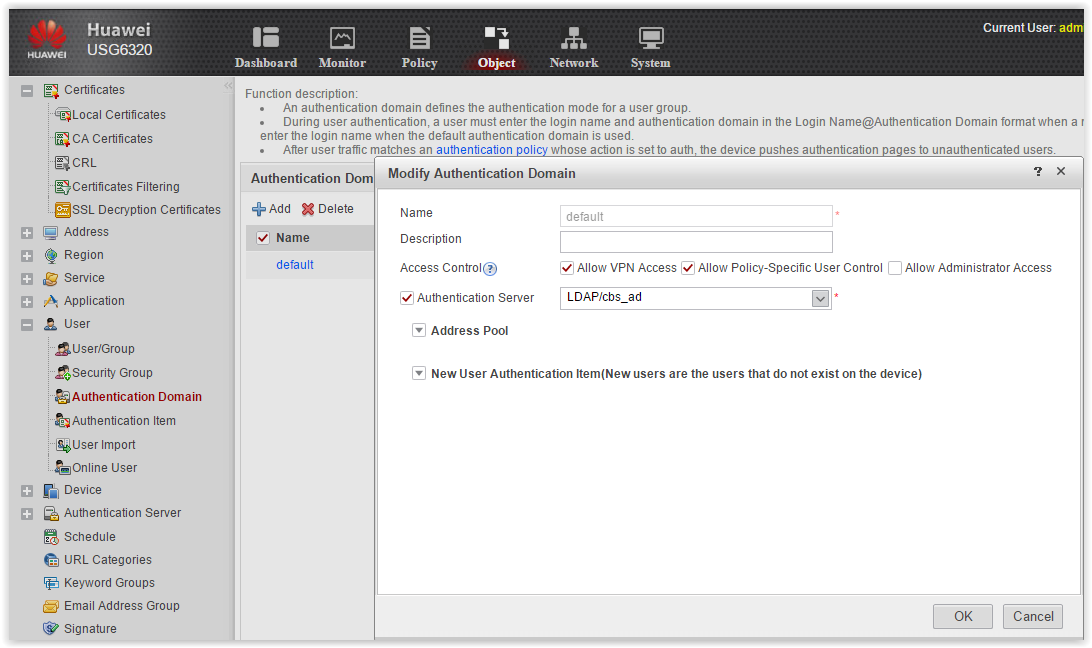
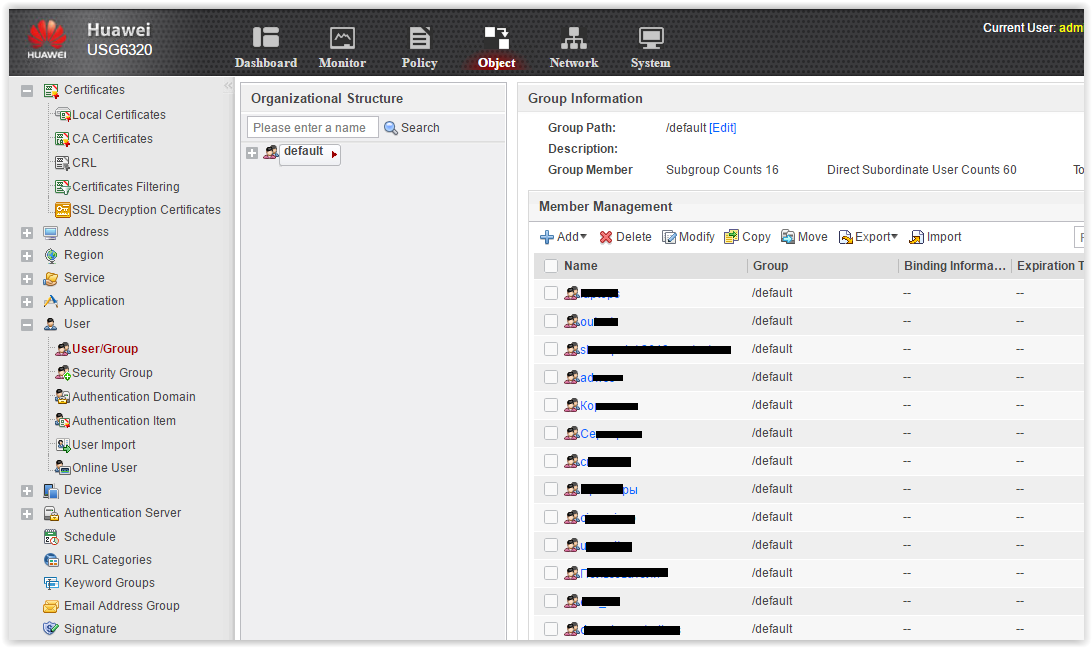
Now in the User / Group and Security Group menu there are users from the directory.
All is ready. Now in the Security Policy settings you can use the names of users and groups in your directory, and in the Authentication Policy settings you can enable authentication.

Set the parameters of the LDAP server.

By the way, by default, in the “User Filtering Field” field, Huawei suggests using cn. For my account in CN = Boris Uskov. And I was pleasantly surprised that Huawei is not experiencing any problems with Cyrillic. Cyrillic is perfectly displayed in the policy settings. Moreover, during testing, when in the authentication process you enter into the login window "Boris Uskov" - authentication is successful. However, for convenience, I replaced the User Filtering Field with sAMAccountName and began to use my usual AD login.
After filling in the parameters, we acquire Detection and check that the connection with the LDAP server is established successfully.

Now that we have established a connection with the LDAP server, we can pull up the user and group directory on Huawei so that we can use the names in the policy settings. This is done in the User Import menu on the Server Import tab.

Here you need to create a profile to import users from the directory.

It remains to configure the Authentication domain.

Now in the User / Group and Security Group menu there are users from the directory.

All is ready. Now in the Security Policy settings you can use the names of users and groups in your directory, and in the Authentication Policy settings you can enable authentication.
So, we are connected to AD via LDAP, users from the directory are pulled to the device. Now let's see what authentication options are available. This can be done in the menu Authentication Item.
Authentication Item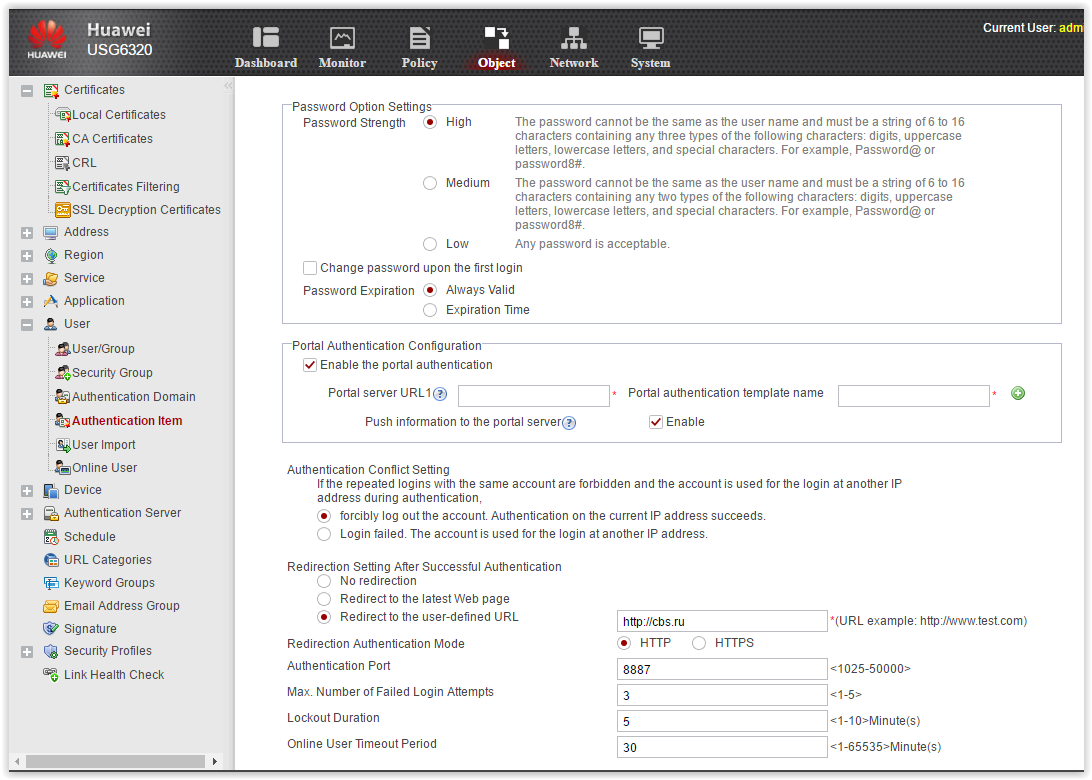

By default, active user authentication through the built-in portal works. It can be customized. You can use a third-party portal for authentication.
Active authentication is not very convenient, since the user will have to manually enter a username / password to access the Internet. Huawei offers some options for Single Sign On (SSO).
SSO Configuration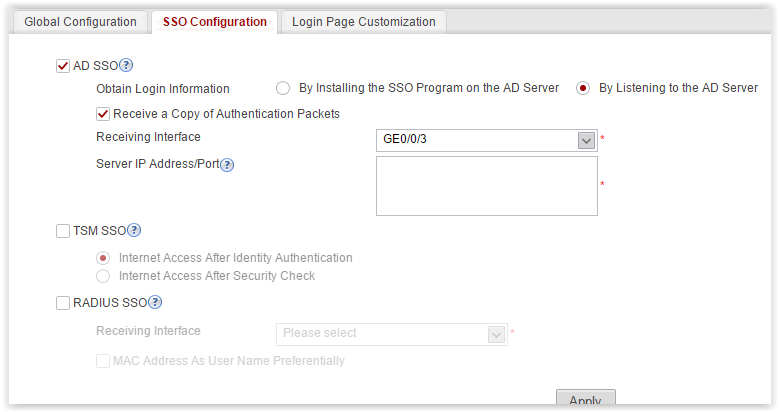

For AD SSO, there are two options for passive authentication - to install an agent on a computer in a domain or on a domain controller (well, this is a classic), or to listen to the exchange of authentication messages between a client machine and AD. Moreover, if the authentication packets do not pass through Huawei, we can mirror this traffic to the selected port (see the Receive a Copy of Authentication Packets setting, Receiving Interface setting in the screenshot above). I'll tell you right away how this kitchen works - I didn’t have time to check it. Hope that works.
Note that active authentication using Kerberos / NTLMSSP is not supported. Terminal server authentication is also not provided.
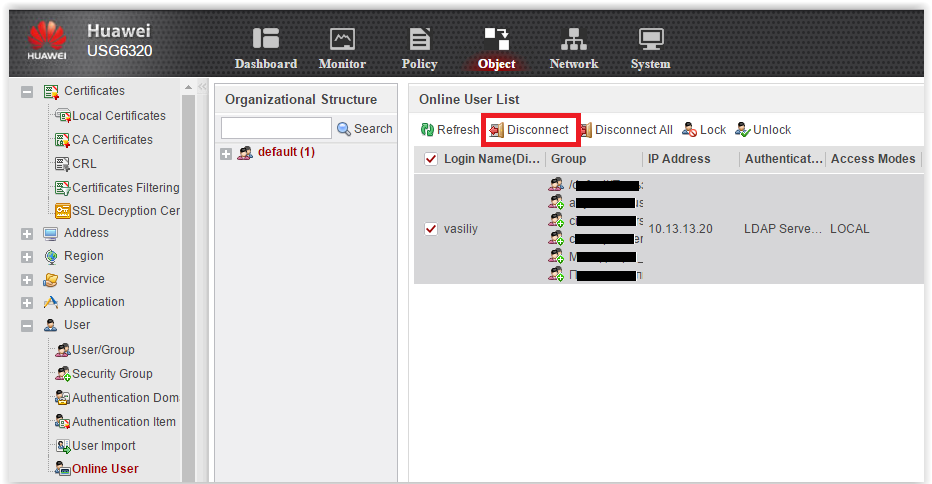
The last thing I would like to mention in terms of authentication is convenient to view active users. This is the Online User menu.
Online user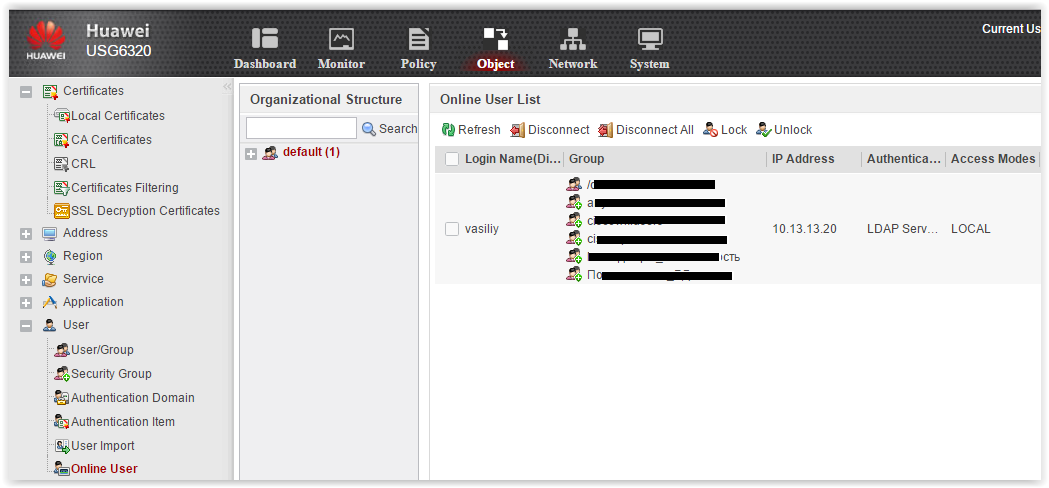

From here you can see who and when successfully passed the authentication, to which groups the user belongs. Here you can disconnect and lock users.
Let's do a test . Tiny test of NGFW functions. And we will round out.
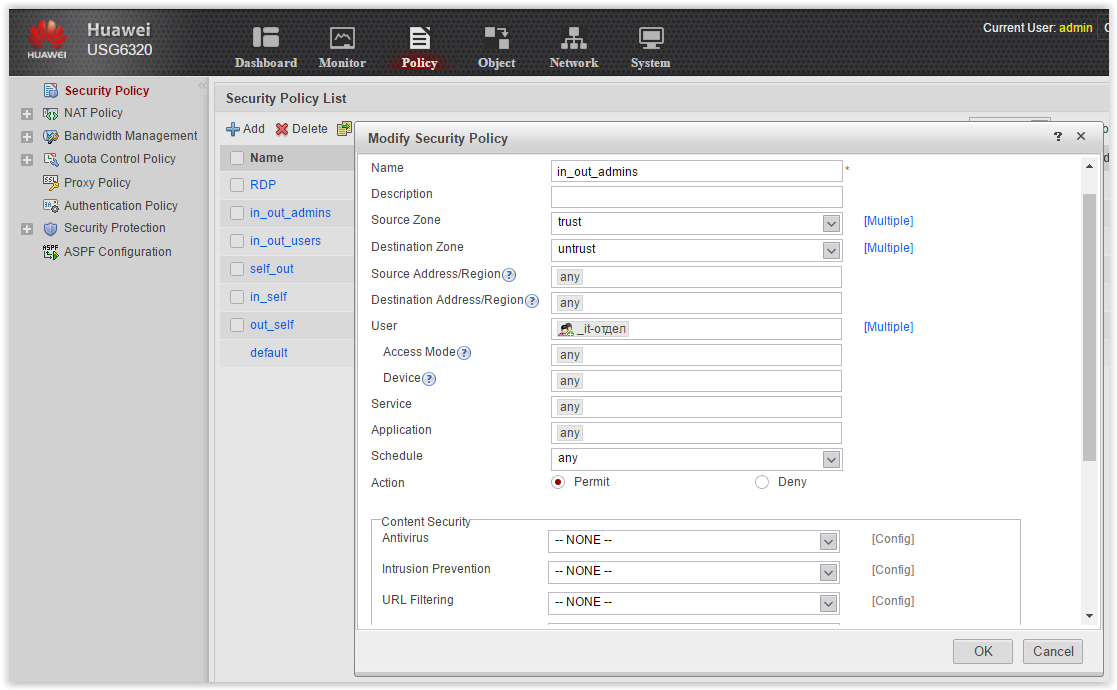
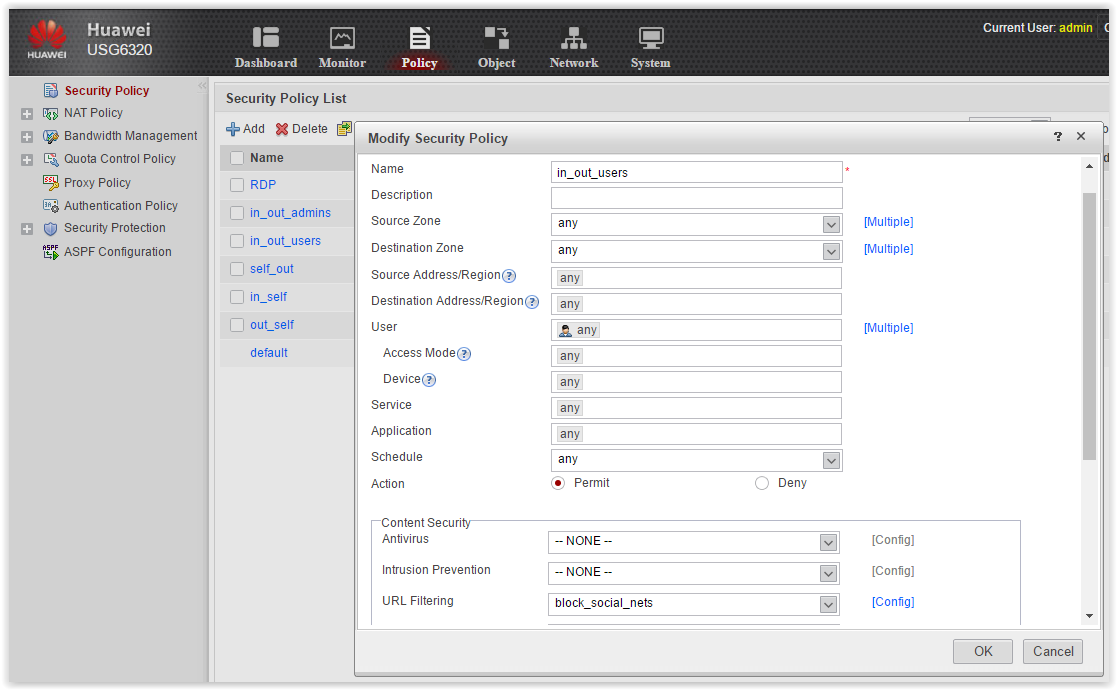
Traditionally, we check the possibility of blocking soc. networks for different user groups from AD. Create two rules in the Security Policy: in_out_admins and in_out_users. According to the first rule, members of the AD group IT department will have unlimited access to the Internet. According to the second rule, all remaining users will be banned from the URL category social. network.
Policy setting
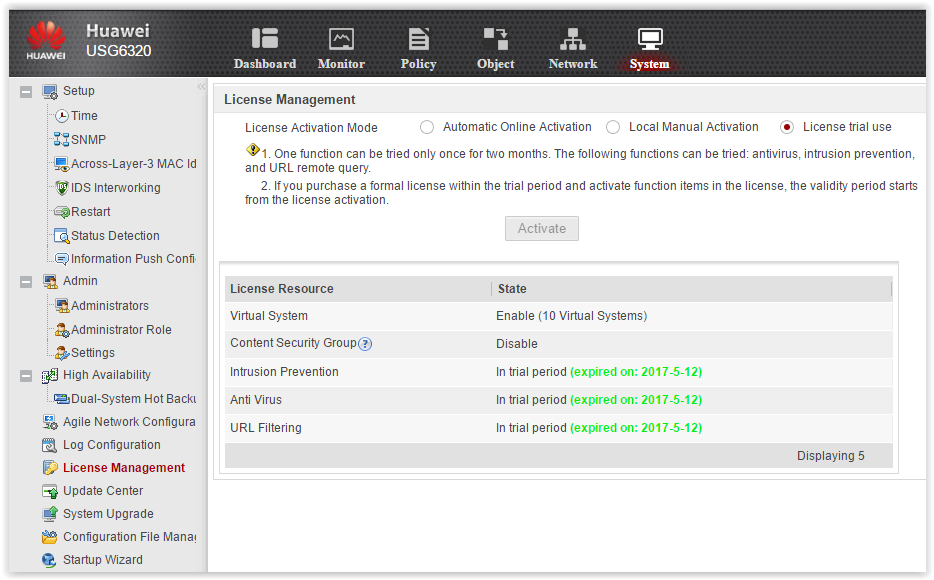
First, we activate all possible trial licenses. Term - for 2 months.
Next, connect the device to the database URL.
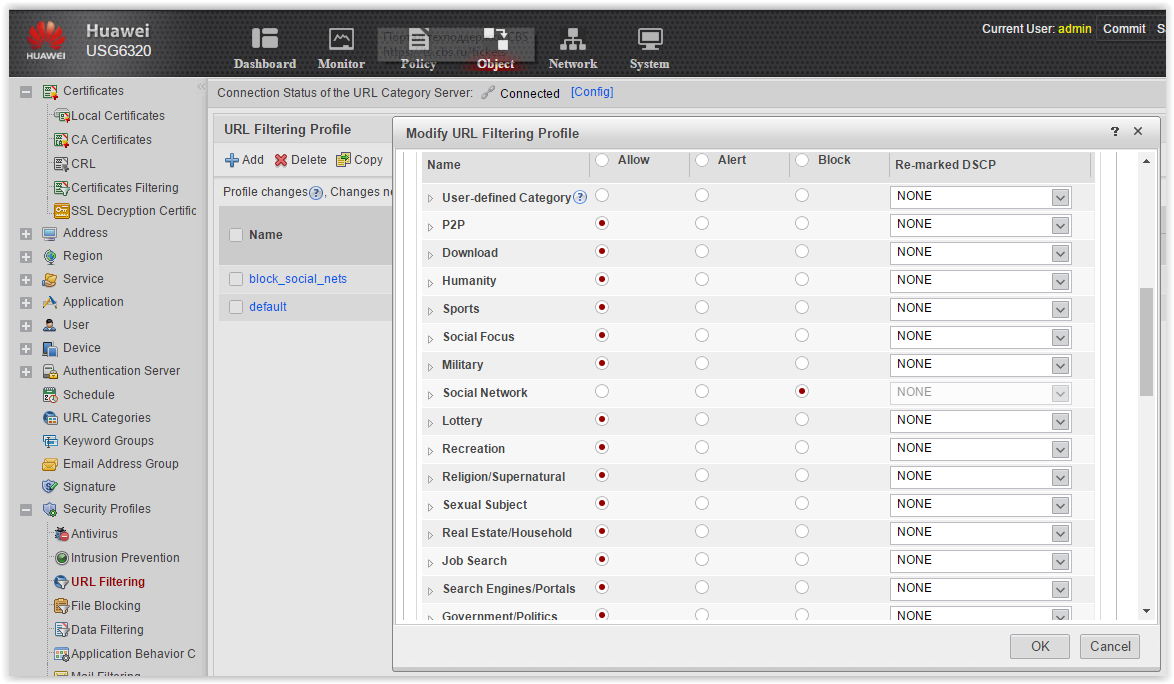
Now we set up the filtering URL profile, which we will call block_social_nets.
Now everything is ready for setting up two Security Policy.
All is ready.

Next, connect the device to the database URL.

Now we set up the filtering URL profile, which we will call block_social_nets.

Now everything is ready for setting up two Security Policy.


All is ready.
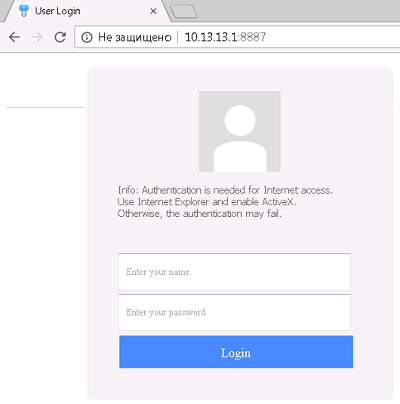
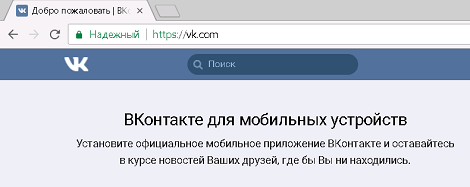
Checking what happened. Open the browser on the laptop for Huawei and go to ya.ru. We are redirected to the authentication portal:
We enter first under the account of a regular user (not an IT department) and check the availability of social services. networks (must be blocked).
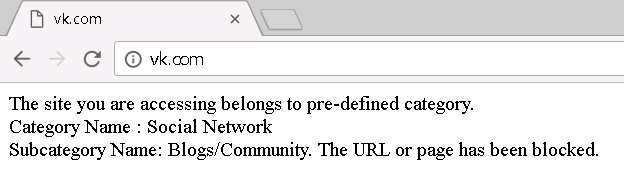
Hurray, vk.com is blocked. Of course, the End-User-Notification is as austere as possible, but still.

Everything is OK, normal flight. So, now facebook.com:

Oh, what are you, dear ...
Same with hi5.com.
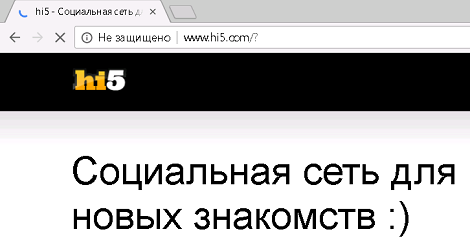
Well, there are obvious blunders. Well, we do not despair. And what if you add a social lock. networks not only as URL categories, but also as Internet applications. We try. Add a policy to the Security Policy.
Add policy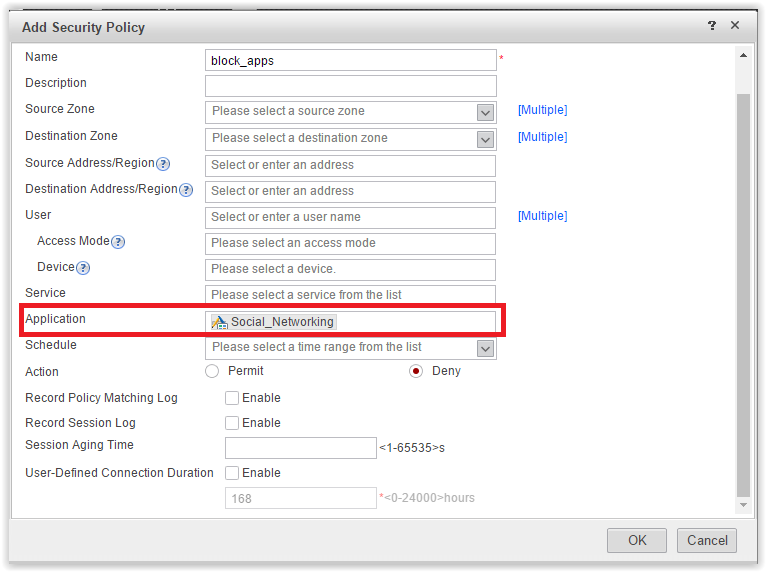

We try again. Uuuvala, access to facebook.com and hi5.com disappears:
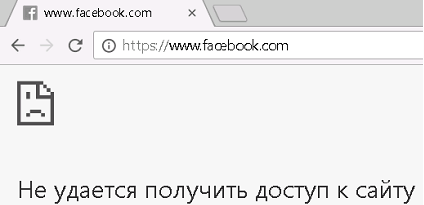
True, the End-User-Notification is also not displayed ... Well, nothing, well, let's survive.
Now we try to go under another uchetkoy. This time from the IT department. Script access to social. networks should appear if Huawei does not mess up group membership. First disconnect the current user.
We are authenticating again on the portal. We try vk.com, facebook.com, etc .:
Well, everything is cool, access works!
What did not like
It would be great to see user sessions on Huawei: who goes where, what URLs are visiting, why the session is blocked, etc. But the only thing I saw was the Session Table on the Monitoring tab:
Session table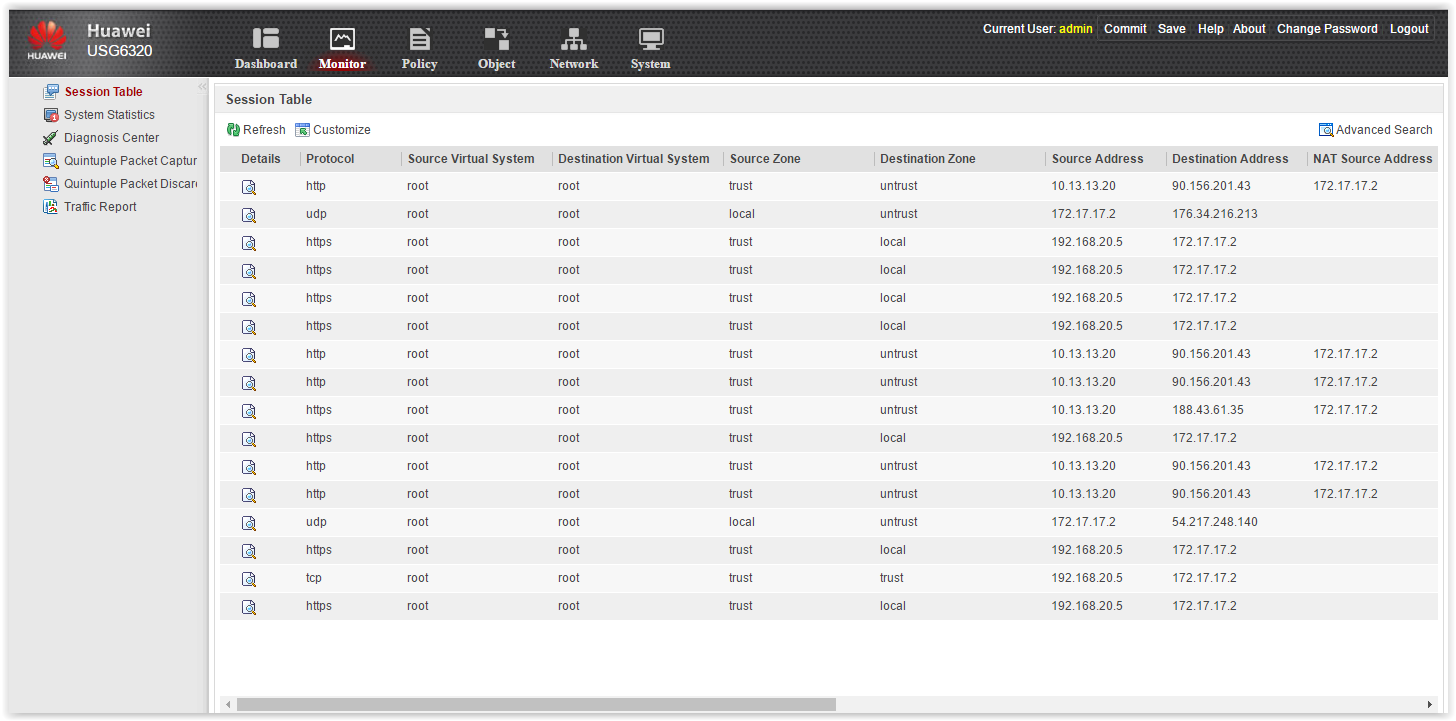

This table is not informative. There are only IP addresses, ports, zones, the work of NAT and the name of the policy under which the transaction falls. No usernames, no URL, no categories, no applications. There is not even an Action column! That is, it is not clear whether the transaction was allowed or dropped. Searching the table is, of course, just as worthless.
No, no, I understand perfectly, all this information can be collected from user tables, from syslog messages, etc. But still, NGFW without the built-in event analysis and at least some reports are built - it seems to me that it is not serious.
We began to find out. They explained to us that the two low-end models of the line (USG6310 and USG6320) do not really have an integrated monitoring tool. These models are positioned for branches. And monitoring should be in the center. As a separate monitoring and management system LogCenter, eSight module. You can send all the logs there and from there make centralized traffic reports, users, URLs, etc.
Older models, starting with USG6330, have full built-in monitoring. Only the device must be equipped with HDD for storing logs. As an example, we were sent a screenshot of the Monitoring tab:
Screen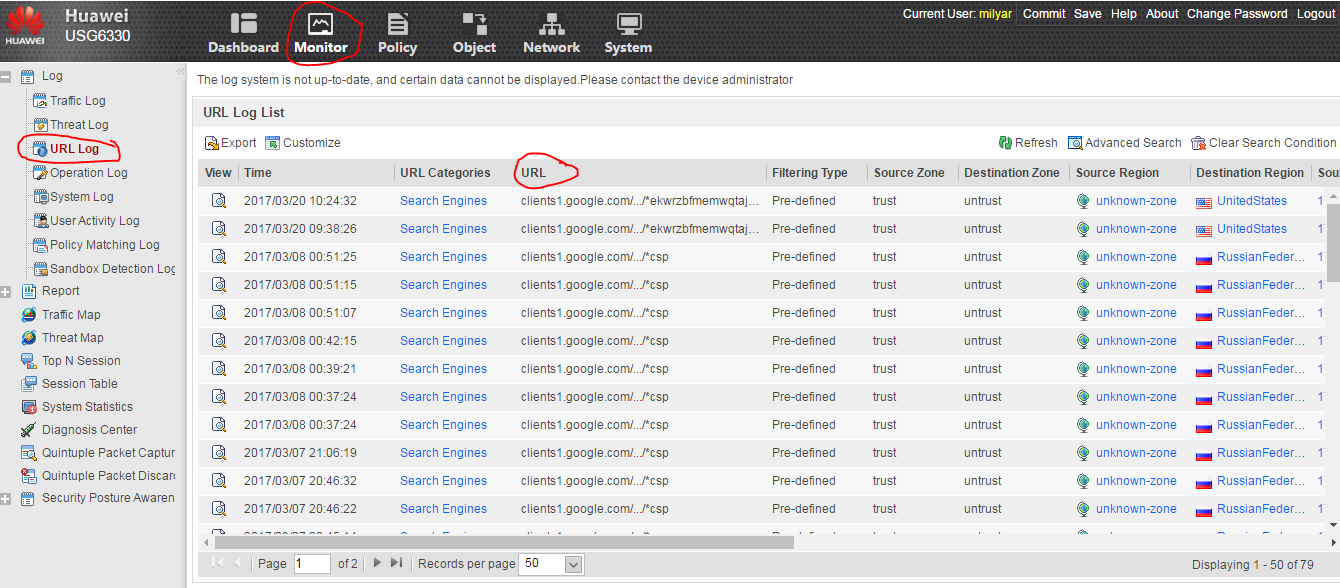

How much is cho?
The piece of iron we tormented costs $ 1,202 .
A bundle that includes the device and 1-year license-subscription IPS-AV-URL will cost $ 1,586 .
An interesting point licensing scheme. To open the remaining options, namely, content security (file control, DLP, antispam, SSL decryption), you need a LIC-CONTENT license, which costs 1 cent. As explained to us, this is also due to export restrictions in various countries. For example, in Korea, the use of SSL decryption is limited.
Of course, the license-subscription IPS, AV, URL is a separate position, for 1 or 3 years. Line items on SSL VPN.
The youngest piece of hardware USG 6310 will cost $ 809 .
Bundle IPS-AV-URL - $ 1,193 .
Older piece of iron - USG6330 - $ 2,268.
Bundle IPS-AV-URL - $ 2,997 .
Plus, for full monitoring will require HDD. At 300 GB - $ 494 , At 600 GB - $ 555 .
All prices are RPL, no discounts.
Conclusion
So, Huawei USG6320. Pros:
- Convenient intuitive and fast Web-based interface;
- Functionality:
- Flexible configuration of interfaces, routing;
- Wide range of content security functionality;
- Different user authentication options.
Minuses:
- Lack of built-in monitoring tools and reports. Only relevant for low-end models USG6310 and USG6320.
Nuances As usual, the devil is in the details. Yes, the functionality is very wide. But, if we start digging deeper into each module, nuances will come out. Here are some examples:
- URL filtering. On the simplest test, the flaws got out: facebook.com and hi5.com are blocked only by filtering applications. At the same time, we lose End-User-Notification.
- Authentication. No Kerberos, NTLMSSP, terminal server authentication is not supported.
- Ips. Yes, there are signatures. There are preconfigured policies - some generalized recommendations for the network. But Huawei does not collect information about your network. Accordingly, it cannot adjust policies for specific tasks, ensure the reduction of False Negative, False Positive. I'm not talking about the correlation of events.
- Email filtering. Antispam. In fact, it's about black-and-white lists, and anti-spam engine, which works on the principle of on / off. Reputation senders? Custom quarantine? Application Verification? No no no. I think, not one sane administrator would not put Huawei USG as the only means of protecting a corporate mailer.
- etc.
But all this is not so bad. The competitors are all the same. Some functions work out very clearly, some added to the device purely nominally.
As a result, the first impression is positive. The solution can compete, moreover, both in the NGFW segment and in the UTM.
Source: https://habr.com/ru/post/324558/
All Articles