Download trusted environment or easy way to paranoia in IT

Despite the somewhat academic name, the topic is quite a practical one.
When we see news headlines about another successful hacking of Telegram or WhatsApp chats (CIA, Iranian intelligence services, Zimperium - underline), people often have to explain that compromising the operating system or user account is not synonymous with the weakness of the application’s protection, and this is not reason to refuse to use your favorite messenger, because in its place it can be without any other difference in principle.
And if, for example, booting from the flash drive you “reset” the administrator's passwords of any of your Windows machines, this does not mean monstrous holes in the “Mastdaye”, and about you - as a super hacker who hacked the brainchild of Microsoft.
I would like to slightly clarify the issues of the environment, components of trust and threats, to create a holistic picture and to understand what we expect in terms of security from the operating system, BIOS and favorite chat application, so as not to shift responsibility from slander to healthy.
So, let's start with the practice, there is the following case:
You, after successfully celebrating the day of the system administrator, have forgotten all your logins and passwords for logging into the system and cannot work with your computers. How to return access? Consider the example of two popular operating systems: Ubuntu and Windows (MacOS consider later).
Reset a forgotten password in Ubuntu OS
Scenario 1. There is access to the menu for choosing the GRUB operating systems.
If you have when you boot your computer, the operating system selection menu appears, then most likely you have an item labeled recovery mode.

Boot into it, in the Recovery menu, select root to go to the shell superuser.
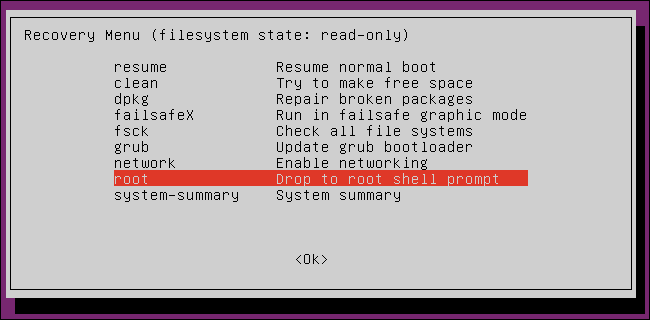
You will run the console as root.
If you have one operating system, then in order to display the GRUB boot loader menu, you must hold down the Shift button (or ESC on some computers) during the boot process. If this does not work, then try booting the computer (when you see the Ubuntu screensaver) and pressing the Reset button on the computer’s system unit; the next time the GRUB menu is displayed, it will be displayed without any manipulations.
- First you need to put the root filesystem into write mode.
mount -no remount,rw / - Now, to set a new password, just run the command
passwd _
where instead of_substitute the name of the desired user, and then executereboot
to restart the computer.
If there is no recovery mode item, then:
- choose a line with your system;
- press the E key;
- add the word single to the end of the kernel options;
- press the B key.
The same terminal will be loaded with superuser rights.
Scenario 2. The GRUB operating system selection menu is not available.
If you have for some reason turned off the choice of operating systems at startup, then the password can be reset using any Live CD with Linux. To do this, you need to boot from the Live CD, mount your root partition, and then reset the password to the user by editing the etc / shadow file on this section.
Note: Generally speaking, no Ubuntu tools can set an empty password to a user. All graphical utilities require a password of at least 6 characters, and the passwd program can set any password other than empty. However, you can reset the user's password, then it will be possible to log in without a password.
Note: The ability to enter a blank password is not in vain. A blank password is a huge potential security hole.
We will need to change the system file / etc / shadow, so it is highly recommended to make a backup before performing further actions:
sudo cp /etc/shadow /etc/shadow.bak Now, in any text editor as root, open the / etc / shadow file, find the line starting with the username of the desired user, and delete everything between the first and second colon in this line. For example, there was this line:
admin:$6$eZ1pQKRK$tGvrlJnV7NU/anEFoxRCluIbe5kSNE2x2uqRrw62xHVrQPWKKbfYZ0cvdmgxXAcrGxBngPM7HnrrKxdmNwp0:14371:0:99999:7::: To remove a password, the admin user needs to bring it in both files to the form:
admin::14371:0:99999:7::: After that, the admin user password will be reset.
Now you can reboot into our system and log in without a password. Do not forget to set a normal password for the administrator after resetting.
How to reset the password of Windows 10
Consider two scenarios for resetting a local user password in Windows 10.
Scenario 1. Executable file spoofing.
To use this method, you need one of the following: Live CD with the ability to download and access the computer's file system, recovery disk (USB flash drive) or Windows 10, 8.1 or Windows 7 distribution kit. Next, resetting the password using Windows recovery tools on the installation flash drive will be discussed.
The first step is to boot from one of the specified drives. After the installation language has been loaded and appears, press Shift + F10. This will bring up the command line. If nothing of the kind appears, you can on the installation screen, after choosing a language, select System Recovery at the bottom left, then go to Troubleshooting - Advanced Options - Command Line.
In the command line, enter the following command in sequence (press Enter after input):
diskpart list volume 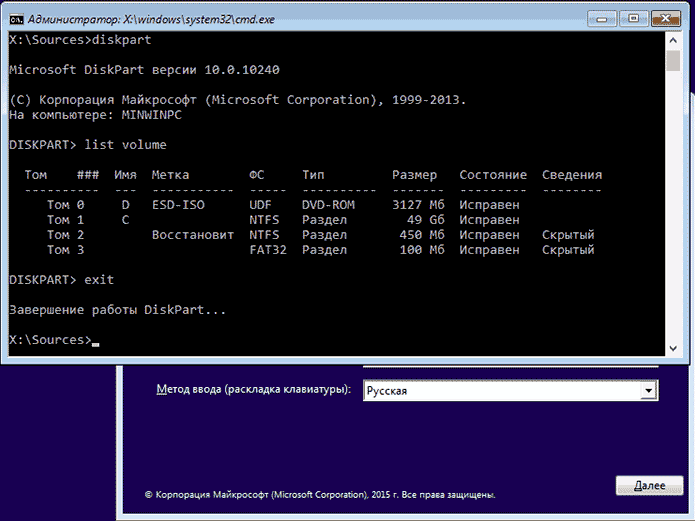
You will see a list of partitions on your hard disk. Find the letter of the partition on which Windows 10 is installed. Type Exit and press Enter to exit DiskPart. Using the letter of the section (C) in the commands, you should enter further:
move c:\windows\system32\utilman.exe c:\windows\system32\utilman2.execopy c:\windows\system32\cmd.exe c:\windows\system32\utilman.exe
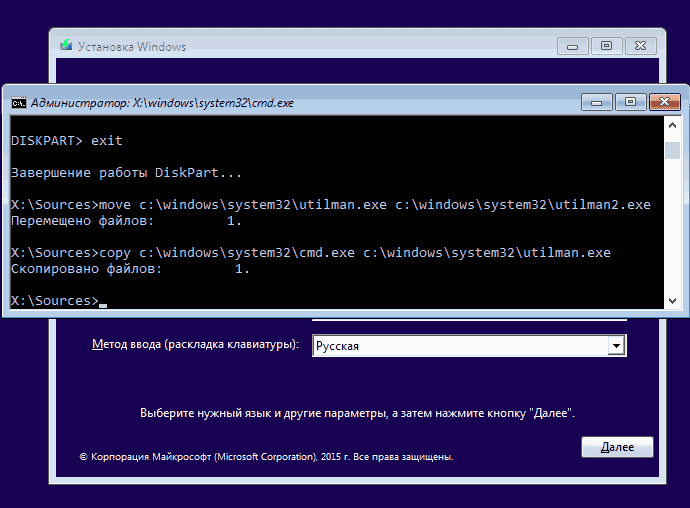
If everything went well, enter the wpeutil reboot command to restart the computer (you can reboot in a different way). This time, boot from your system disk, not from a bootable flash drive or disk.
Note: if you did not use the installation disk, but something else, then your task using the command line, as described above, or by other means, make a copy of cmd.exe in the System32 folder and rename this copy to utilman.exe.
After loading, in the password entry window, click on the “Special features” icon at the bottom right. The Windows 10 command prompt opens.
At the command prompt, type net user username new_password and press Enter. If the username consists of several words, use quotes. If you do not know the username, use the net user command to view a list of Windows 10 usernames. After changing the password, you can immediately log in to the account with a new password.
Scenario 2. Editing the registry.
There is another interesting, simple and working way to reset your password. It also requires either a bootable distribution with the OS, or a recovery disk, or a third-party Live CD with registry editing tools.
The essence of the method is as follows:
- Boot from the drive, in the installation program, press Shift + F10 to open the command line.
- Enter regedit and press Enter to start the registry editor.
- In the Registry Editor, select the HKEY_LOCAL_MACHINE key and then select “File” - “Load hive” in the menu and open the file C: \ Windows \ System32 \ config \ system
- When requesting a section name, specify any.
- Inside the HKEY_LOCAL_MACHINE of the loaded hive (registry key) with the name you specified, select the setup key and in the right part, change the following values (by double clicking on them).
- CmdLine - set the value of cmd.exe
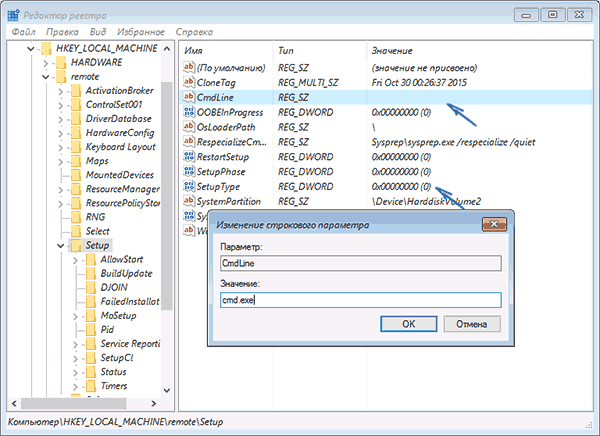
- SetupType - set the value to 2.
- In the Registry Editor, select "File" - "Unload Hive" and confirm the unloading.
After that, close the registry editor, the command line, exit the installation program and boot from the hard disk of the computer. When you boot into Windows 10, a command prompt opens in which you can reset the password by typing:net user _ _
To continue booting the OS, type exit in the command line and press Enter. There is no need to reset the parameters in any way: the SetupType parameter in the registry will return to the value 0.
What was it?
This is where issues of the environment and confidence in it emerge.
So what happened above?
In fact, we removed the operating system from the management and loaded another medium (from the live media or bootloader), which provided us with access to the system media in order to overwrite (reset) the hashes of forgotten passwords.
Conceptually, this means that a computer system, like a building, is built on a foundation (and not just one), and if security is not ensured at the lowest level, everything will collapse regardless of wall thickness and signaling reliability on the 110th floor.
In IT, we are actually talking about nested environments; each component is executed inside (in the environment) of a component of a lower level, using its services. For example, the browser uses operating system calls to allocate memory for a web page, opening / closing ports for network connections.
Below is the nesting hierarchy of system environments, the task of completely systematizing them was not:
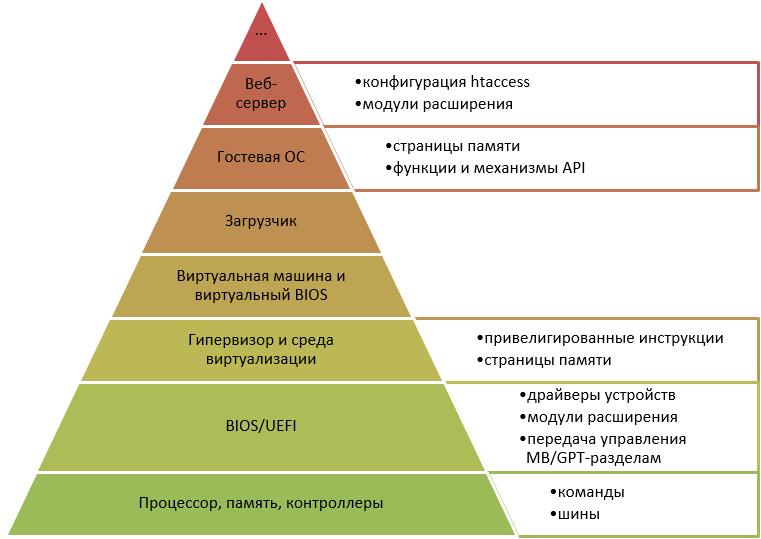
Accordingly, if there is an incorrect configuration or vulnerability of a component of the lower level, such as an error in the BIOS microcode, then closing it at a higher level (for example, at the “host” OS ”level) is either difficult or almost impossible. In general, it is as unpromising as it is to hope to seal cracks in the walls of a building with a leaning foundation.
How do we get a reliable building? In IT, this is called trusted systems or a trusted platform / platform.
The concept of “trusted environment” does not currently have an established definition, specialists cannot agree on opinions, and strictly speaking, the term “trusted” is not defined in the regulatory framework. The concept of "trusted environment" appeared after the "trusted system", introduced back in 1983. in the so-called Orange Book ( TSSEC - Trusted Computer System Evaluation Criteria ), which was the source material for a number of governing documents of the State Technical Commission of the Russian Federation, for example, the RD AS .
A trusted system in the standard is a system that uses hardware and software to ensure that a group of users simultaneously process information of different categories of secrecy without violating access rights.
One of the technical means to ensure a trusted system is a trusted boot tool. The main function of trusted boot is to boot the system only from predefined media, after successfully completing the integrity check and confirming its credentials, by identifying and authenticating the user.
Conclusion
In the next articles we will look at ways to protect against the attacks described above using the trusted boot mechanism. To do this, we will study the classic scenario of computer loading and, in general, understand how conceptually the protected systems are built. Consider the loading of a computer using the means of trusted boot (SDZ) and compare SDZ with the Secure Boot protocol (UEFI).
Literature
- GOST R 54583-2011 / ISO / IEC / TR 154443-3: 2007. Information technology. Security measures and means. M .: Standardinform. 2013 .;
- GOST R ISO / IEC 15408-3-2002. Information technology. Methods and means of security. Criteria for assessing the security of information technology. Part 3. Security trust requirements;
- Tsirlov V.L. Basics of information security of automated systems, a short course. - Rostov-on-Don: Phoenix, 2008. - 253 p .;
- Avezova Ya.E., Fadin A.A. Issues of ensuring trusted boot in physical and virtual environments // Cyber Security Issues. 2016. № 1 (14). Pp. 24-30;
- Windows registry information for advanced users, https://support.microsoft.com/ru-ru/help/256986/windows-registry-information-for-advanced-users ;
- User documentation on Ubuntu, http://help.ubuntu.ru/wiki/power_password ;
- Trusted Computer System Evaluation Criteria, http://csrc.nist.gov/publications/history/dod85.pdf ;
- Guidance document. Automated systems. Protection against unauthorized access to information. Classification of automated systems and information security requirements. M .: State Technical Commission of Russia, 1992.
')
Source: https://habr.com/ru/post/324178/
All Articles