HPE Aruba and Cisco Controller Interfaces

HPE Aruba equipment is not very common in Russia, but in the US market the vendor competes quite closely with Cisco. Wireless solutions from these manufacturers have a similar set of functions and additional services. Equipment is comparable in cost.
There are many marketing tests, comparisons of technical characteristics, performance and technologies of each solution. After reviewing the documentation, you are convinced that the functions of the solution are very similar. However, in addition to the functional similarity, there is a slightly different manufacturer's approach to customization, operating principles, and architectural differences. That is what I would like to draw attention to. This is a note on how cisnovodki configured HPE Aruba and what came of it.
Functionality. Network architecture
Both vendors offer various options for building a network. In addition to autonomous access points, this can be:
- centralized solution with a controller (or cluster of controllers) for management and monitoring;
- solution for a small office with a controller based on the access point (s);
- distributed solution with multiple remote points (controller in the center; VPN connection);
- controller in the cloud.
In addition to basic Wi-Fi for enterprises, there are many more products that allow you to implement various services in the company's wireless network. For example, it can be a device positioning service in a room, a policy-based network identification / access service for BYOD devices, analytics of connecting devices, etc.
')
As equipment, I considered classic controllers (a centralized solution; the controller controls all access points) for an entry-level wireless network and typical office access points with integrated antennas.
Equipment
Cisco - controller 2504, access point 2600i.
Aruba - controller 7010, access point 205.
Aruba - controller 7010, access point 205.
Let's compare the presence of the main functions in the solution based on Cisco and HPE controllers:
| Function | Cisco | Aruba |
| Automatic Radio Control | Rrm | ARM |
| Interference monitoring | Cleanair | Spectrum Analysis |
| Detection of neighboring TDs | Rogue detection | Rogue detection |
| Application Monitoring and Control | AVC | AppRF + URL Filtering |
| Roaming optimization | Optimized roaming | Client match |
| Data Encryption (Point-to-Controller) | DTLS | Ipsec |
| Reservation | SSO, N + 1 | Active / Active, Active / Standby |
| Intrusion Prevention | wIPS | wIPS |
| Positioning | Hyperlocation | - (BLE only) |
| Signal optimization | ClientLink | - |
| Firewall | - | Stateful firewall |
| Routing | - | Static, OSPF |
| Remote access IPsec / SSL VPN | - | Virtual Intranet Access (VIA) |
Licensing
Typically, Cisco has a rather complex licensing schemes, the licensing of certain functions. But not the case with the wireless network. Everything is exactly the opposite, HPE goes to the “first” place.
HPE Aruba
On the controller there are about ten various licenses. Any important feature is licensed separately (same firewall, spectrum analysis or application analysis (DPI)). If you want to test the controller from Aruba, you will need to manually request a temporary license (certificate), as already mentioned, for each feature separately.
Cisco
All features are available in the base license. There is a temporary for 12 weeks.
GUI setting
HPE Aruba
On the HPE Aruba controller, configuration is done through profiles. The branched structure of profiles for configuring wireless parameters on a point / group of points is presented below. Logical and understandable.
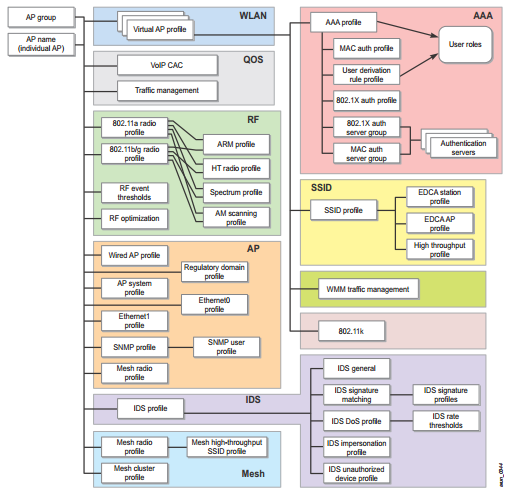
For example, to create a wireless network, you need to create a Virtual AP profile, then attach the AAA profile and SSID profile to it. There is a simplified configuration menu with indication of the main profiles (radio environment management, QoS, AAA, etc.).
In the Configuration section menu there are tabs for setting various functions.
Due to the abundance of detailed settings, pre-configured policies and profiles, you can get confused when setting up for the first time. Here the Show reference button can help, showing the links of various entities (profile, policy) with each other.

When you go to the All Profiles tab, you can see how many different thin details can be configured on the Aruba controller. Customization is more detailed here than in Cisco.
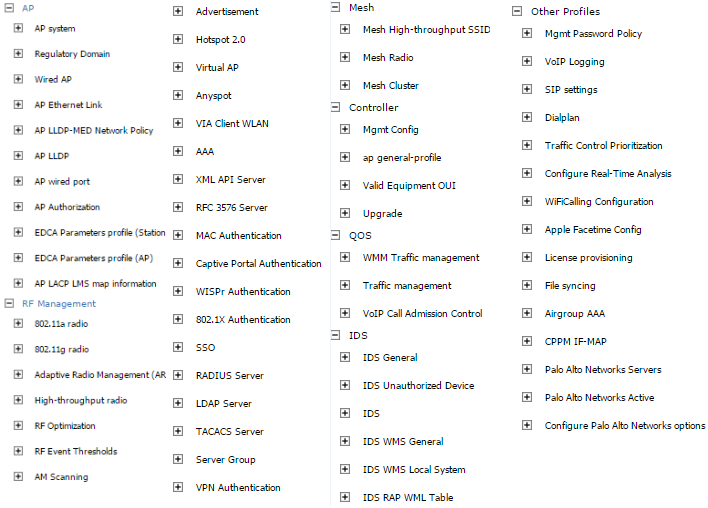
Cisco
The interface is divided into sections (WLANs, SECURITY, MANAGEMENT, etc.). Each has a tabbed menu. No profiles and references. The interface looks more convenient and intuitive. However, there are no such number of detailed settings and additional functions as in Aruba.
For example, the WLAN configuration menu.

HPE Aruba
Each connected client is assigned a specific role with its access policies (User-centric network, Stateful Firewall). The controller has preset profiles and firewall rules. On the one hand, it is very convenient: for example, you do not need to configure guest access policies from scratch, you can only add specific rules for this role.

On the other hand, if you do not have a firewall license (PEFNG), then the roles lose their meaning. At the same time, in the settings (AAA profiles, for example), they still remain, since this is one of the key entities used during configuration.

Since we have touched the firewall settings, below is a menu of general options. Very extensive. There are sections with access lists (ACLs), services, bandwidth limitations, etc.

Cisco
The controller does not have a firewall function. A full-fledged ME can be implemented on a separate device. However, to analyze traffic in a wireless network, one of the key functions is the analysis of traffic by application (DPI), the possibility of its prioritization or blocking. Both vendors have this option. In Cisco, it is called AVC (Application Visibility and Control), in HPE Aruba - AppRF. Also on the Cisco controller, you can configure (except standard ACLs) access restriction policies for a specific type of device.
Cisco, like Aruba, is able to determine the type of client (profiling) using HTTP, DHCP headers. For a certain type of clients (for example, iPad or Android-Samsung) on the controller, you can create an access policy (local policy) with the necessary parameters and restrictions - ACL, VLAN, QoS, hours of operation, etc.

CLI configuration
Configuring a wireless network controller is more comfortable through a graphical interface. In the command line, it is more convenient to do a selection by parameters or to debug a problem. For comparison, I will give an example of the WLAN configuration on the controllers. Many people know that the CLI on Cisco controllers is a little like the regular Cisco IOS command line (hi Aironet), familiar to many. So, when you look at the example below, the thought creeps in that Aruba is more like Cisco IOS.
HPE Aruba
aaa profile "tst-dot1x-peap" mac-default-role "employee" authentication-dot1x "ad-users-radius" dot1x-default-role "employee" dot1x-server-group "default" ! wlan ssid-profile "test123" essid "test123" opmode wpa2-aes ! wlan virtual-ap "virt-ap" aaa-profile "tst-dot1x-peap" ssid-profile "test123" vlan 21 Cisco
config radius auth add 1 1.1.1 1645 ascii secret123 config wlan create 3 test123 test123 config wlan interface 3 users_vlan21 config wlan security wpa akm 802.1x enable 3 config wlan radius_server auth add 3 1 config wlan broadcast-ssid enable 3 config wlan enable 3 Monitoring
In terms of monitoring, both solutions look good. If you use only the controller (without additional servers), Aruba provides more detailed information. Cisco has less network monitoring data. This is due both to the lack of certain functions in principle (for example, a firewall), and to the general Cisco approach, when we are asked to install a separate system for monitoring the wireless network and storing statistics (of course, from Cisco).
HPE Aruba also has a management and monitoring system, of course. But at the same time there are a lot of things in the database that Cisco can get only with an additional server. For example, guest access with printout of information on connection, mailing, traffic statistics (addresses, url, categories). In the latest software version, Aruba also has proactive traffic monitoring and wireless network monitoring tools.
Monitoring Radio Parameters
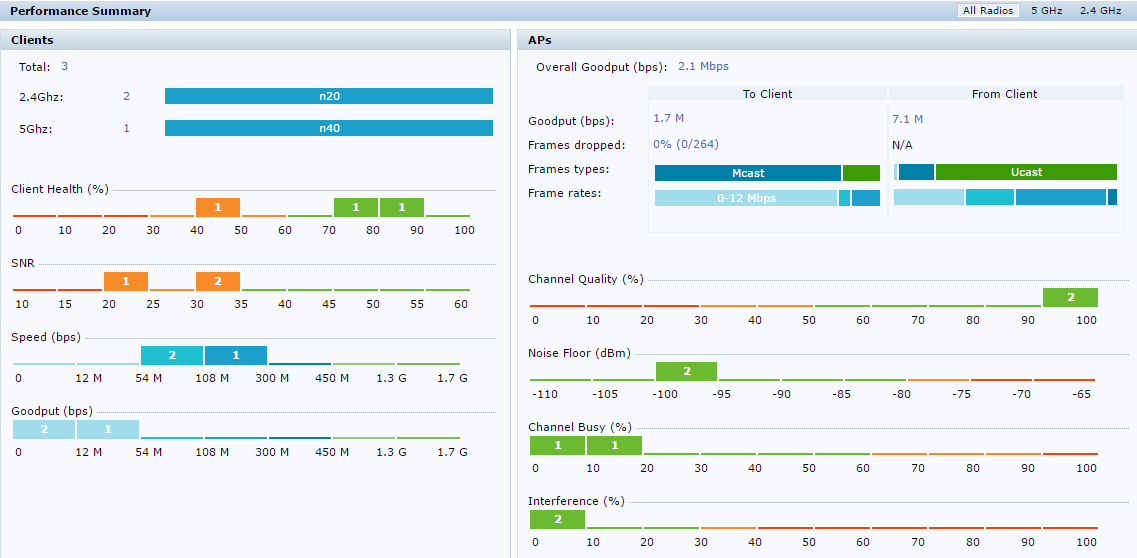
HPE Aruba
Aruba provides an overview of all wireless network users. Here we see the distribution by range, connection speed, signal level, etc.
Cisco
At Cisco, we also see overall connection statistics for the moment.

Traffic monitoring (applications, users, sessions)
Here, comparing solutions is not entirely correct, since Aruba has a Stateful Firewall, which means more detailed information about the session.
HPE Aruba
Aruba provides information on the applications used. There are signatures for our resources like vkontakte and yandex. Present data by session, the distribution of user roles, information on the URL.


Cisco
Everything is more modest here - only applications and device type. You can see the statistics for a specific user. Signatures for Russian applications, too.

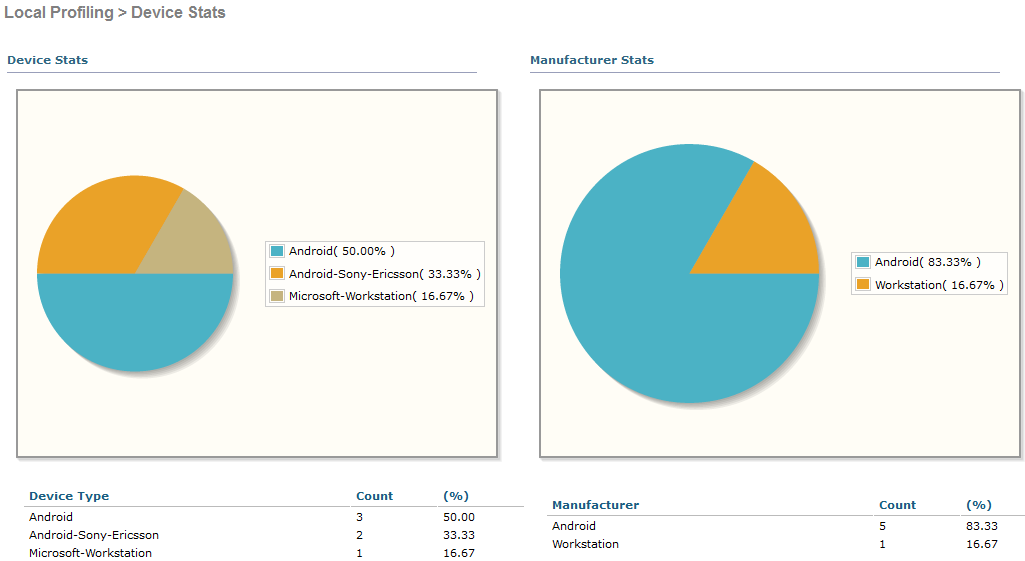
General Application Usage Statistics for Cisco
Logging
HPE Aruba
The main protocol for keeping system messages is syslog. The system uses the distribution of logs by category (system, AAA, firewall, etc.). For each set the required level of logging. They are stored in separate files.

Cisco
System logs are collected in a single syslog console. An important tool for tracking wireless events are snmp notifications. Collecting messages can be configured by type (auth \ deauth, etc.) and categories (ap, security, etc.).

Conclusion
The material is a subjective view on the difference of approaches, control interfaces of two solutions. Described only a small part of the functions that provide the device. On the wireless functions of the solution are similar. Cisco seemed more intuitive and logical to set up (although it may be a matter of habit). Aruba is more complicated, but you should not forget that there are more various additional services (VPN, FW, Routing). Of course, when choosing a solution, it is worthwhile to focus on other aspects: solution reliability; the stability of its work, customer service; vendor technical support, etc.
Source: https://habr.com/ru/post/324112/
All Articles