File storage in the social network and other projects of the students of Innopolis University

Students of the master program “Development of secure systems and networks” found weak spots in cryptosystems, suggested ways to improve the protection of large graphs, and found out that in VKontakte you can store files of any type and size under the guise of audio recordings.
Students at an IT university have completed cybersecurity research in preparation for summer industrial projects. “A research project is one of the conditions that a student must fulfill in order to complete a training program. To this end, we advise you to take topical research problems and work on them. But in the future we plan to take on the problems that really exist in the industry, and allow students to work on solving them. In this way, students will become familiar with the real working conditions in the industry, ”explains Rashid Hussein, head of the graduate program“ Development of secure systems and networks ”.
Storing files in the social network under the guise of audio recordings
')
Artyom Bakhtin, Anatoly Tykushin and Timur Samigullin worked on an application that, under the guise of audio recordings, saves files of any type and size in social networks. Students encountered similar capabilities on other resources: file systems were implemented on the basis of the Imgur image hosting service, the Git version control system, and the Bittorrent network.
“We found out that the storage functionality of MP3-files and in VKontakte can be used for other purposes. This allows you to make your personal page a file repository, ”explains Artyom Bakhtin.
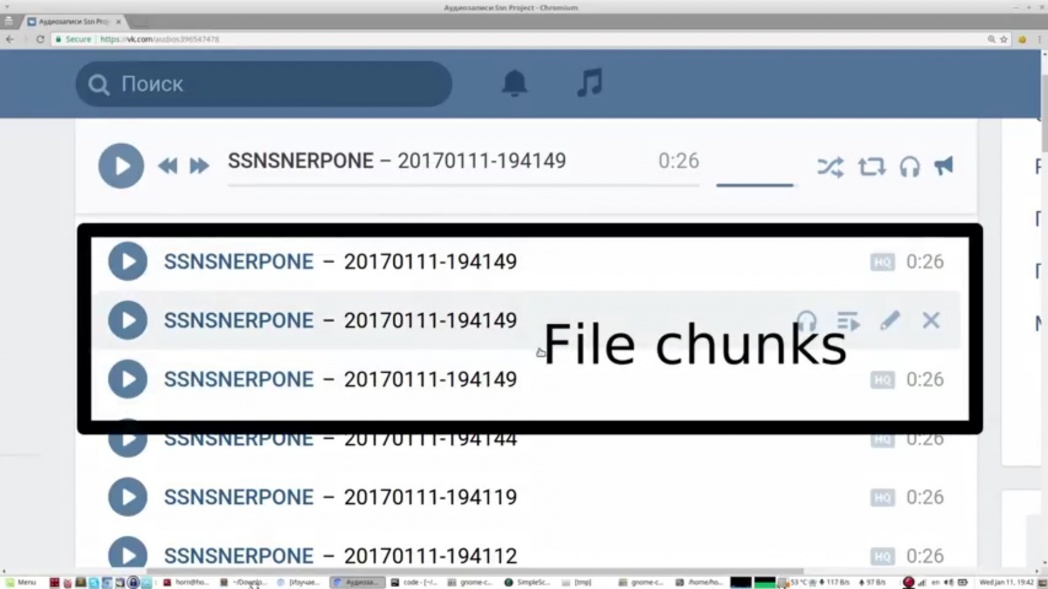
Students have developed an application that integrates into the standard file viewer of the operating system, and working with such files looks as if they were stored locally. Using the application, you can synchronize files between multiple devices at no additional cost for increasing the amount of stored data, which happens with other service providers.
To use the system, you need to install on the devices where file synchronization is required, a special application on the GitHub. Now it works only on computers with the Linux operating system. The application converts MP3-files, that is, deals with their pre-and post-processing. The downloaded data looks like simple audio recordings with noise and does not represent value for third parties without an algorithm for extracting information from this format. But, according to students, the recovery algorithm is not too complicated, and interested parties can recover it, so it’s better to hide such files with privacy settings on the social network.
“We made a prototype and it’s hard to rely on reliable file storage, because this is not the use of social networks. Before use, you need to check if this is not a violation of the site’s user agreement. Otherwise, files will be deleted without warning. The project was not developed for use by other users, for this it is necessary to bring the code into the proper form, ”adds Artyom.
“The project is interesting - the students showed that the existing service has a different side of the coin. They proved their theory of free storage, and the social network can consider it as an additional service, ”commented Professor Rashid Hussain on the project.
Complex watermarks to protect against intruders
Mikhail Boldyrev and Emil Melnikov complicated the watermarks protecting large columns in the Graph Watermarking project. A graph (or network) is a data structure, where vertices are members of a network, and edges are interactions between participants. In the social network, the peaks will be people, and the ribs will be the subscriptions of one person to another.
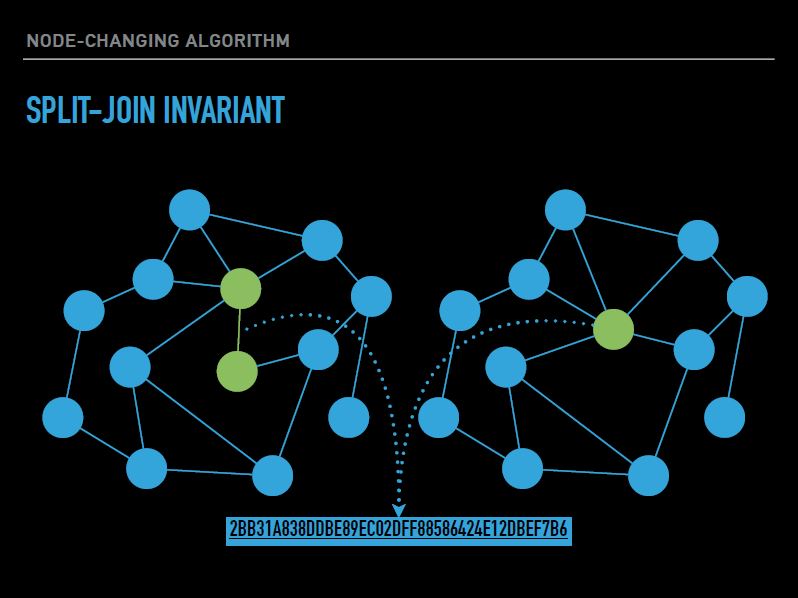
In digital space, it is easy to cover footprints and it is difficult to find the culprit of information leakage, so graphs are marked with watermarks. They act as individual identifiers for everyone who received this information. Students came up with a new method of embedding a watermark that is more resistant to attacks. The study of watermark overlays on graphs began recently; two scientific articles were published on this topic in 2015 and in 2016. But previous researchers have not provided for the protection of a watermark on individual large clusters of the graph. The method of students of the University of Innopolis does not allow attackers to attack a separate fragments of graphs to destroy the watermark so that the culprit does not declassify himself.
“With such a watermark, you can safely give the graph to other people for work and not worry that it will publish on the Internet. If someone tries to do this, it will be immediately detected, ”adds Emil Melnikov.
Research cryptosystem weaknesses to protect secret files from scammers
In the framework of the Backdooring asymmetric crypto-algorithms project, Bogdan Vaneev, Nadezhda Troflyanina and Aydar Sabirov investigated how attackers hacked cryptosystems by embedding special bookmarks. “It puts at risk all distributed systems whose security is based on cryptography, for example, banks,” comments Bogdan Vaneev.
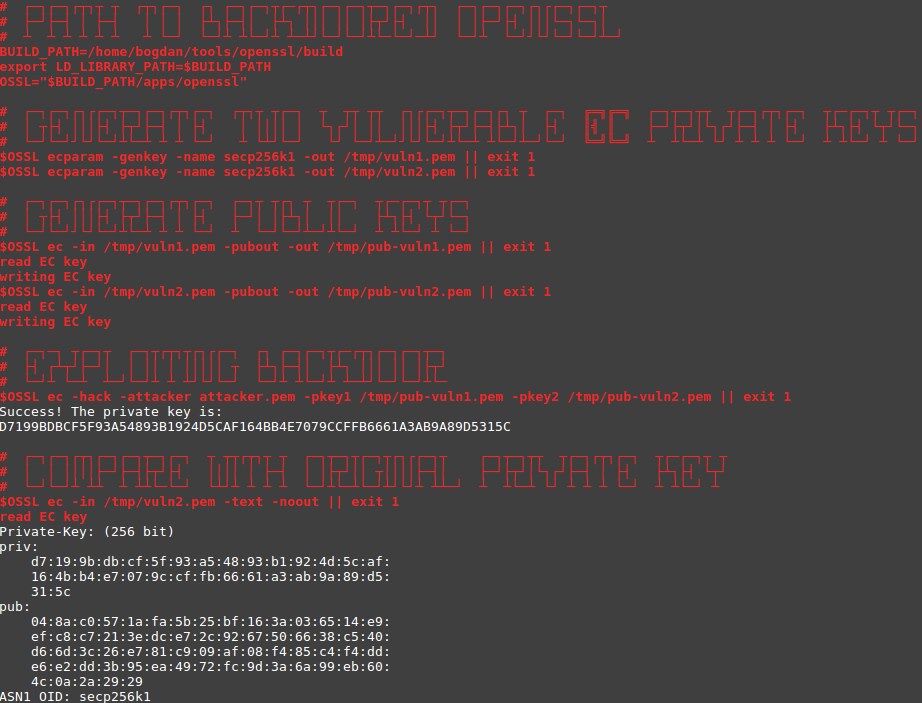
Students reviewed public sources with a description of the embedding algorithms for bookmarks, evaluated them for the complexity of implementation and detection, and suggested methods for improving the algorithms.
“Usually, for managers of cryptosystem companies, there is a black box in which it is not known what is happening. The attacker changes the structure of the encryption algorithms, receives data about the company's customers, and it is almost impossible to notice. Bookmark algorithms are designed to be undetectable, but we found out that this is possible through source code analysis. Therefore, our research will be useful for companies to protect sensitive data, ”said Bogdan.
Students Bulat Saifullin and Oleg Ilin investigated neuro-cryptography, where instead of complex mathematical functions, neural networks resistant to the attacks of quantum computers are used.
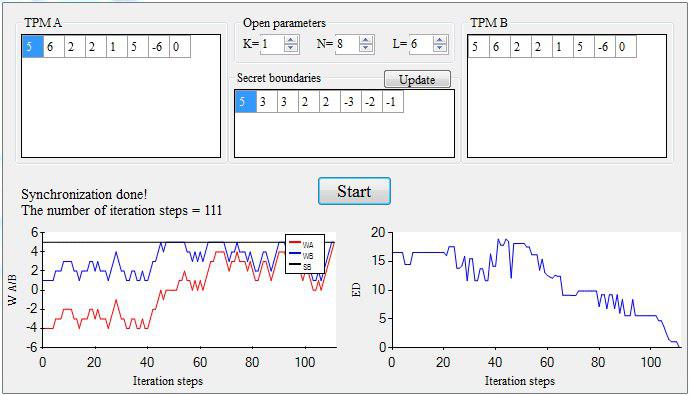
Students studied how attackers could get encryption keys in neuro-cryptography and found out that if the learning speed of the neural network components was made random and the information on the neural network status in the received keys was hidden, the fraudsters had no chance to intercept the encryption keys.
“Now I am working on two articles, which reflect the results of two scientific projects of our students - Backdooring asymmetric crypto-algorithms and Graph Watermarking. Writing an article on the basis of student projects takes a lot of time, since the text should be written in a scientific and technical way. I hope we can submit these articles for publication in a scientific journal, ”added Rashid Hussein.
Source: https://habr.com/ru/post/324010/
All Articles