Password Requirements - Complete Nonsense
Do you know what the worst is in passwords ( and there are plenty to choose from )? Requirements for their complexity.
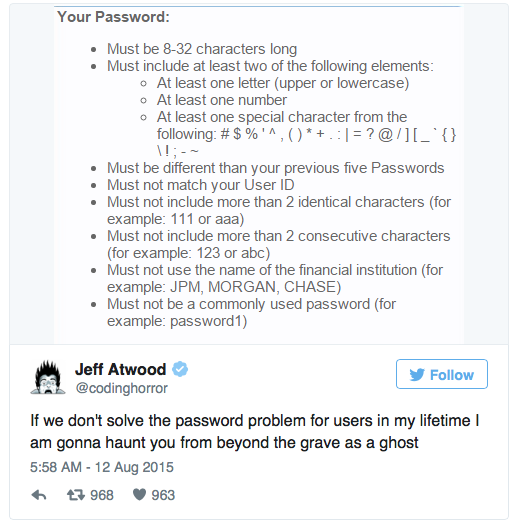
"If we do not solve the problem with passwords during my lifetime, I will rise from the grave with a ghost and will haunt you all."
Let this oath be written on the tablets of the Internet. I do not know whether there is life after death, but sooner or later I will find out, and then hold on - I have ambitious plans.
')
The world is literally mired in the terrible rules for creating passwords:
→ Stupid requirements
→ Examples of bad politics
→ Board of shame
But you do not need to explain all this. Those who use random password generators, as befits us, the geeks in the last stage, in their own skin, experience unbearable suffering under the yoke of this regime from day to day.
Have you seen this classic comic about XKCD passwords?
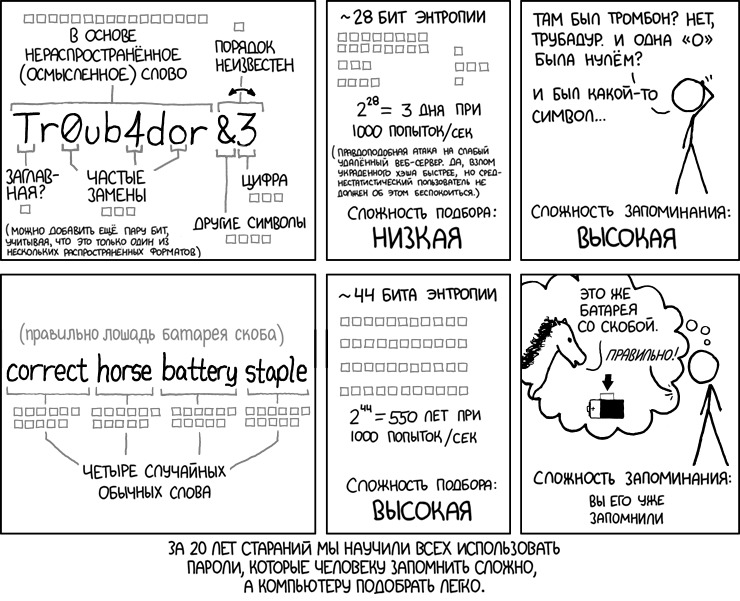
Of course, one can argue whether the “correct horse battery staple” should be considered an example of a good password generation strategy, but the point of the argument is that the length decides.

No, seriously, decides. I will say even more: I give a tooth that your password is too short . Nowadays, considering how well developed cloud computing and password cracking are with the help of the GPU, putting a password in 8 characters or shorter is just the same as not putting it at all.
Then, it turns out, we already have one rule: the password should not be short . A long password is more likely to be secure than a short one ... is it true?
And what about this password in 4 characters?

Or about this, in 8 characters?

Or about such a hypothetical, but quite realistic, 7 characters?
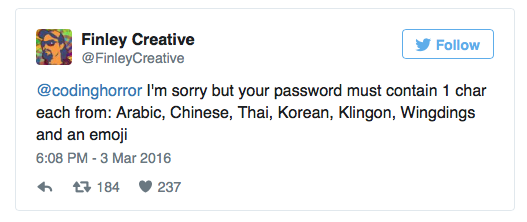
“Sorry, but your password must contain at least one character from Arabic, Chinese, Thai, Korean and Klingon, an icon from Wingdings and a smiley.”
In addition, you are probably surprised, but if you insert the above 4 smileys in the password field from your favorite authorization window (let's try), it turns out that there really are ... not four characters at all.
Lord

Our old friend Unicode again for his .
As it turns out, even the simple rule “your password must be of a reasonable length” works with reservations. Especially if you stop thinking like Americans moved to ASCII .
And if you look at all these nice long passwords ... are they always reliable?
aaaaaaaaaaaaaaaaaaa
0123456789012345689
passwordpassword
usernamepassword
Of course not. Have you seen live users lately?

They consistently spoil every program I create. Yes, yes, I know, you are the geeks in the last stage and you know everything about the concept of entropy. But expressing your love for entropy through terrible sophisticated password requirements like:
in a world where there are Unicode and emoticons, it means not to have imagination.
When we were working on Discourse , I learned that the authorization window turns out to be a very complex software component , despite its apparent simplicity. The main requirement for passwords that we adopted - the length - was also quite simple. While I was writing this article, we have already increased the minimum possible password length from 8 to 10 characters. And for moderators and administrators, they decided to put the lower limit even higher, on 15 characters.
In addition, I insisted on checking that the password does not match any of the 100,000 most common ones. If we analyze the 10 million passwords that were shared due to data leaks , it turns out that the following 25 are most commonly used:
123456
123456789
qwerty
12345678
111111
1234567890
1234567
password
123123
987654321
qwertyuiop
mynoob
123321
666666
18atcskd2w
7777777
1q2w3e4r
654321
555555
3rjs1la7qe
google
1q2w3e4r5t
123qwe
zxcvbnm
1q2w3e
Even these data indicate excessive obsession with the ASCII system. That is, the numbers, of course, are the same everywhere, but somehow I can’t believe that the average Chinese would have thought to put “password”, “quertyuiop” or “mynoob” as a password. So such lists need to be made taking into account localization and other parameters.
(There is another interesting idea: look for popular short passwords as part of long ones, but, as it seems to me, there will be too many errors of the first kind)
The presented statistics also testify in favor of making passwords longer. Please note: of the 25 most popular passwords, only 5 have a length of 10 characters or more. Accordingly, if we set at least 10 characters, then this one will cut off 80% of the list. I found this out for the first time when I collected several million passwords from data breaches in a study for Discourse and filtered out those that meet our new requirement that the password be at least 10 characters long.

And suddenly from the huge list there were horns and legs. (If you also conducted similar studies, please share the results in the comments)
I would like to offer fellow developers the following recommendations dictated solely by common sense:
One rule, at least, is easy to remember, understand, and implement. This is the same notorious rule to rule everyone, it is more important than all, it will put everyone together and put it in darkness.

As I said, which ones are considered “common” depends on your audience and language, but in any case, by allowing users to set passwords from a list of 10,000, 100,000, or a million of the most popular passwords from data leaks, you do them a disservice . There is not the slightest doubt that the hacker will try these passwords when trying to break, and even if you put tight restrictions on the number of attempts to enter, it is enough to drive away the first thousand to achieve shockingly good results.
But you are lucky: you can find millions of lists of "published" passwords on the web. Making an investigation based on this data is even fun - after all, these are not some abstract, artificial rules for you that some programmer made out of boredom. No, these are the real passwords that the real users used.
Do research. Collect data. Save users from themselves.
There is nothing particularly abstruse, just choose the value that instinctively seems to be suitable for you deep down. But do not forget: you will have to explain your logic to users who do not pass the test.

With some sadness, I realized that we were completely satisfied with the user setting a password of 10 completely identical characters ("aaaaaaaaa"). In my opinion, the easiest way to avoid such a situation is to set a minimum of x unique characters to the total number y. So we do in the latest beta version of Discourse. But if you have any other ideas, we will be glad to hear them in the comments. The simpler and clearer the better!
I am ashamed to admit, but, realizing the authorization window for Discourse, we completely forgot about two common cases that need to be monitored and suppressed ( I mentioned this in another article ):
If you have Discourse version 1.3 and below - I'm sorry, please update it as soon as possible.
You may also want to block some more varieties:
In short, try to think, going beyond the input field - just like your users.
Some readers took my words as "all the rules, except for these four, which I am now writing out, are complete nonsense." I meant something else.
The idea is this: focus on one clear, simple and practical rule that really works in any situation - length. Users can enter anything (within reason) on Unicode with one condition - that there are enough characters. The password must be long - this is the only collective rule that we must teach users.
Points three through five are just reservations for special occasions (such as a genie you cannot make a wish to get an unlimited number of desires ). It does not need any preliminary discussions, because such things should be rare exceptions. Users need to be stopped if they try to enter a password that matches the name, or 0123456789, or simply “aaaaaaaaaaaa”, but this should occur as part of data verification after entry, and not in accordance with a previously clarified rule.
So, if in two words: one rule - length. Enter what your soul desires, if only the number of characters is drawn to a normal password.

"If we do not solve the problem with passwords during my lifetime, I will rise from the grave with a ghost and will haunt you all."
Let this oath be written on the tablets of the Internet. I do not know whether there is life after death, but sooner or later I will find out, and then hold on - I have ambitious plans.
')
The world is literally mired in the terrible rules for creating passwords:
→ Stupid requirements
→ Examples of bad politics
→ Board of shame
But you do not need to explain all this. Those who use random password generators, as befits us, the geeks in the last stage, in their own skin, experience unbearable suffering under the yoke of this regime from day to day.
Have you seen this classic comic about XKCD passwords?

Of course, one can argue whether the “correct horse battery staple” should be considered an example of a good password generation strategy, but the point of the argument is that the length decides.

No, seriously, decides. I will say even more: I give a tooth that your password is too short . Nowadays, considering how well developed cloud computing and password cracking are with the help of the GPU, putting a password in 8 characters or shorter is just the same as not putting it at all.
Then, it turns out, we already have one rule: the password should not be short . A long password is more likely to be secure than a short one ... is it true?
And what about this password in 4 characters?

Or about this, in 8 characters?

Or about such a hypothetical, but quite realistic, 7 characters?

“Sorry, but your password must contain at least one character from Arabic, Chinese, Thai, Korean and Klingon, an icon from Wingdings and a smiley.”
In addition, you are probably surprised, but if you insert the above 4 smileys in the password field from your favorite authorization window (let's try), it turns out that there really are ... not four characters at all.

Lord

Our old friend Unicode again for his .
As it turns out, even the simple rule “your password must be of a reasonable length” works with reservations. Especially if you stop thinking like Americans moved to ASCII .
And if you look at all these nice long passwords ... are they always reliable?
aaaaaaaaaaaaaaaaaaa
0123456789012345689
passwordpassword
usernamepassword
Of course not. Have you seen live users lately?

They consistently spoil every program I create. Yes, yes, I know, you are the geeks in the last stage and you know everything about the concept of entropy. But expressing your love for entropy through terrible sophisticated password requirements like:
- must contain uppercase letters;
- must contain lowercase letters;
- must contain numbers;
- must contain special characters.
in a world where there are Unicode and emoticons, it means not to have imagination.
When we were working on Discourse , I learned that the authorization window turns out to be a very complex software component , despite its apparent simplicity. The main requirement for passwords that we adopted - the length - was also quite simple. While I was writing this article, we have already increased the minimum possible password length from 8 to 10 characters. And for moderators and administrators, they decided to put the lower limit even higher, on 15 characters.
In addition, I insisted on checking that the password does not match any of the 100,000 most common ones. If we analyze the 10 million passwords that were shared due to data leaks , it turns out that the following 25 are most commonly used:
123456
123456789
qwerty
12345678
111111
1234567890
1234567
password
123123
987654321
qwertyuiop
mynoob
123321
666666
18atcskd2w
7777777
1q2w3e4r
654321
555555
3rjs1la7qe
1q2w3e4r5t
123qwe
zxcvbnm
1q2w3e
Even these data indicate excessive obsession with the ASCII system. That is, the numbers, of course, are the same everywhere, but somehow I can’t believe that the average Chinese would have thought to put “password”, “quertyuiop” or “mynoob” as a password. So such lists need to be made taking into account localization and other parameters.
(There is another interesting idea: look for popular short passwords as part of long ones, but, as it seems to me, there will be too many errors of the first kind)
The presented statistics also testify in favor of making passwords longer. Please note: of the 25 most popular passwords, only 5 have a length of 10 characters or more. Accordingly, if we set at least 10 characters, then this one will cut off 80% of the list. I found this out for the first time when I collected several million passwords from data breaches in a study for Discourse and filtered out those that meet our new requirement that the password be at least 10 characters long.

And suddenly from the huge list there were horns and legs. (If you also conducted similar studies, please share the results in the comments)
I would like to offer fellow developers the following recommendations dictated solely by common sense:
1. Password Requirements - Complete Nonsense
- They do not work.
- They punish the audience that you need to attract in the first place - those who use random password generators. Estimate, the random password may not contain numbers or symbols. I checked the math textbook twice, and yes, it seems to be quite possible.
- They annoy the majority of users, discouraging their desire to cooperate with you and urging them to look for all sorts of “witty” loopholes. As a result, passwords are less secure.
- They are often erroneous, in the sense that the proposed set of rules is insufficient or simply ridiculous. Just look at any example from the board of shame that I referred to above.
- No, really, for the sake of all that is holy, this nonsense with arbitrary password requirements is enough. If you don't believe me, read the NSIT password requirements . That’s what it says: “Avoid setting rules for creating passwords.” Although, in my opinion, there is one inaccuracy, it was necessary to write: "Avoid setting stupid rules."
2. Set the minimum password length in Unicode.
One rule, at least, is easy to remember, understand, and implement. This is the same notorious rule to rule everyone, it is more important than all, it will put everyone together and put it in darkness.

- It's simple. Users can count. Well, most can.
- It works. Statistics confirm that it works: just download any list of popular passwords of your choice and sort them by length.
- Mathematics will not lie. All other things being equal, a long password will be more random than a short one, and therefore more secure.
- Accept the fact that even this one rule will have exceptions. The minimum length of 6 characters on the Chinese site is quite reasonable. On the other hand, a password of 20 characters can be ridiculously easy to break.
- If you cannot enter (practically) any character from Unicode in your password field, you are most likely doing something wrong.
- This is more relevant to the implementation details, but do not forget to also set the sane maximum password length.
3. Check the list of the most common passwords.
As I said, which ones are considered “common” depends on your audience and language, but in any case, by allowing users to set passwords from a list of 10,000, 100,000, or a million of the most popular passwords from data leaks, you do them a disservice . There is not the slightest doubt that the hacker will try these passwords when trying to break, and even if you put tight restrictions on the number of attempts to enter, it is enough to drive away the first thousand to achieve shockingly good results.
- 1.6% of users have a password of the 10 most popular;
- 4.4% of users have a password among the 100 most popular;
- 9.7% of users have the password among the 500 most popular;
- for 13.2% of users, the password is among the 1000 most popular;
- 30% of users have a password of the 10,000 most popular.
But you are lucky: you can find millions of lists of "published" passwords on the web. Making an investigation based on this data is even fun - after all, these are not some abstract, artificial rules for you that some programmer made out of boredom. No, these are the real passwords that the real users used.
Do research. Collect data. Save users from themselves.
4. Control the amount of entropy
There is nothing particularly abstruse, just choose the value that instinctively seems to be suitable for you deep down. But do not forget: you will have to explain your logic to users who do not pass the test.

With some sadness, I realized that we were completely satisfied with the user setting a password of 10 completely identical characters ("aaaaaaaaa"). In my opinion, the easiest way to avoid such a situation is to set a minimum of x unique characters to the total number y. So we do in the latest beta version of Discourse. But if you have any other ideas, we will be glad to hear them in the comments. The simpler and clearer the better!
5. Catch specific types of passwords.
I am ashamed to admit, but, realizing the authorization window for Discourse, we completely forgot about two common cases that need to be monitored and suppressed ( I mentioned this in another article ):
- a password that matches the username;
- password that matches e-mail.
If you have Discourse version 1.3 and below - I'm sorry, please update it as soon as possible.
You may also want to block some more varieties:
- a password that matches the site URL or domain name;
- password that matches the name of the application.
In short, try to think, going beyond the input field - just like your users.
Explanation
Some readers took my words as "all the rules, except for these four, which I am now writing out, are complete nonsense." I meant something else.
The idea is this: focus on one clear, simple and practical rule that really works in any situation - length. Users can enter anything (within reason) on Unicode with one condition - that there are enough characters. The password must be long - this is the only collective rule that we must teach users.
Points three through five are just reservations for special occasions (such as a genie you cannot make a wish to get an unlimited number of desires ). It does not need any preliminary discussions, because such things should be rare exceptions. Users need to be stopped if they try to enter a password that matches the name, or 0123456789, or simply “aaaaaaaaaaaa”, but this should occur as part of data verification after entry, and not in accordance with a previously clarified rule.
So, if in two words: one rule - length. Enter what your soul desires, if only the number of characters is drawn to a normal password.
Source: https://habr.com/ru/post/323864/
All Articles