Pink spacesuit, cryptocurrency and genetically modified iOS: tasks of the online-stage NeoQUEST-2017 and some statistics
 March 1-10, the online cybersecurity competition NeoQUEST-2017 was held . It's time to take stock, share interesting statistics of the passage, and also briefly tell about the tasks themselves.
March 1-10, the online cybersecurity competition NeoQUEST-2017 was held . It's time to take stock, share interesting statistics of the passage, and also briefly tell about the tasks themselves.This year we decided to send the participants of the competition to the endless space and invented for them a galaxy of 9 task planets , each of which was unique.
All 9 "planets" could not be passed to anyone, but, nevertheless, we did not have a single uncompleted task! The winner of AV1ct0r submitted 7 tasks, and his 1025 points were the best result in the online stage of the competition! The silver medalist, Ilja , fully completed 4 tasks and received one more key in two, his result - 817 points. "Bronze" received VampiRUS , on his account 4 completed tasks and one - half solved, the number of points was 731.
Three prizewinners are waiting for great gifts, and everyone who received at least one key will receive souvenirs! We now turn to the subject and "highlights" of tasks NeoQUEST-2017!
')
Task number 1 of the planet Greenoid: “Repair the Leader!”
Green planet, green robots with horns, big mouths and stick-legs-sticks? Well this is Android! The name of the planet, by the way, also hinted precisely at this mobile operating system.
And when the participants downloaded the apk-file, all their doubts about the subject of the assignment should have been dispelled! To “fix” the leader of the green robots, the participants needed to expose the reverse engineering apk-file, decrypt the encrypted byte-code stored there, disassemble the native library and find a collision to the CRC32 hash function. The write-up for this task has already been published on his blog by the winner of the online stage AV1ct0r and described GH0st3rs in habrastatie (read here !)
Task number 2 of the planet Photonis: "Photomania"
In this task, the participants received an archive with images, but the images were unusual: some of them contained just color noise, and in the rest, the R, G and B components of each pixel turned out to be equal to each other (grayscale). Also, each image included additional meta-information, in particular, geo-tags.
Participants were required to filter out the noise and mark the geographical coordinates of the remaining images on the world map. As a result, the resulting points created an image of characters that are the key to the task (and, as mentioned in the legend, places on Earth that aliens managed to visit). Such a funny steganography! Write-up for this task has also been published, read !
Task number 3 of the planet Etheris: "Citizens, keep money in cryptocurrency!"
In this task, participants are confronted with the blockchain technology . They had to deal with the principles of work of smart contracts Ethereum and conduct two attacks on one of them. The first one resembled a well-known recursive attack on The DAO, during which the attacker almost stole $ 60 million worth of cryptocurrency! For the second attack, it was necessary to use a memory error and replace the contract owner with oneself.
Task number 4 of the planet iFetus: "Forbidden Fruit"
In the legend for this assignment, were the carriers of information sized? The hint is clear! Here it is - the announced task on iOS! Participants received an archive in which there were 780 files with obscure names.
At first glance, it was absolutely incomprehensible what to do with them. The best option was sorting them by type: 4 files were immediately detected with extensions that let you understand that these files are nothing more than a backup of an iOS device. Then the participants either wandered through the files and followed the prompts that the developer left for them, or searched for IP from our subnet (this was how the most cunning ones did!). The result of the search was a zip-archive, whose name is the first key of the task.
But the task was also the second part! The contents of the archive - iOS application in an unusual way (folder with the .app format). Apple lovers could try to run it on the iOS simulator, but we decided to make equal conditions for everyone and force the participants to reverse! The application pulled out a login and an encrypted password from NSUserDefaults, decrypted it and sent it to the server, and if the password was correct, it received the key.
Having recovered the password, the participants encountered another problem: the server constantly responded with “Incorrect App”. And the trick was that it was necessary to replace the User-Agent with the one used in the application! Few managed to get the second key, and even our winner tried about 200 different options and only then found the right one (read write-up here !).
Task number 5 of the planet Espion: "Multi passport!"
In this assignment, we decided to force participants to take a walk on various social networks and implement OSINT or, in some way, “spying” (it was from the word espionage that the name of the planet was formed!).
The participants were given an archive with a large number of photos and were asked to fill in the questionnaire of the “participant of the space expedition”. The questionnaire was conditionally divided into three blocks and, as it turned out, it was necessary to visit 5 social networks to fill it out.
The first step was the most difficult: how to move from photos to a user profile in a social network? It turns out that if you look at the photographs, some of them were taken near the space itself: NASA Tourist Space Center. One of the photos closest in number (yes, only one!) Kept geographical coordinates in its EXIF. Using them when searching in the popular blue social network (this is Peter, baby!) You could go to the user profile, and then, seeing that he was selling a chic pink space suit, figure out where to go next! By the way, hackzard wrote a great (and, which is very valuable, fun!) Write-up to this task.
Task number 6 of the planet Prioritus: "Too many things ..."
The participants were provided with IP-address and hints on the use of "priorities" as initial data. At the specified address was a web server that operates using the HTTP / 2 protocol.
Having studied the HTTP / 2 protocol and its features, participants could discover the technology of prioritizing HTTP / 2 streams. By generating its requests with different priorities, the server sent various responses. After going through the 256 values of priorities, participants received the first key and found a “pass” to the second key - an entry form with fields for login and password. Here, participants were given the opportunity to develop their own way of conducting boolean-based blind SQL-injection over HTTP / 2 to obtain a second key.
Task number 7 of the planet E-mu: "Lost in the dodecahedron"
And here, the participants were provided with a QEMU compiled for Linux as source data, while a new virtual PCI device was added at compile time, which made the task of finding a key much more difficult.
Participants were also required to break their heads over a sudoku puzzle: the key to the task was a message, recorded using ASCI graphics, which was stored in an array of 16x256. Initially, this array was encrypted, and the 16x16 sudoku puzzle solution was the encryption key.
Task number 8 of the Endian Planet: "Rescue Crew"
Intel technology and its features are a frequent topic in NeoQUEST reports (for example, this and this !)!
We have no doubt that many of our participants practically “from the cradle” are able to study the disassembler of the machine code for the Intel architecture and even calculate in their mind how much memory is needed in order to zamp out 16GB of address space in long-mode with PML4 of 2Mb. But not only Intel'om beautiful and diverse world! We decided to pause for a bit and remembered the times when the sky was bluer, the trees were bigger, and the MacBooks were on PowerPC .
Participants were given 2 files - a PCI-Expansion ROM image for QEMU and a PowerPC binary file for IDA Pro. Our PCI ROM just asked for a password ... JNE on NOP and VZhUUUH! All is ready! It's time to try using your website to download your patched PCI ROM. However, the most attentive noticed that ROM is checked for integrity, and not by the standard 8-bit cheksumma, but by the neo-Quest integrity monitoring algorithm! There you already had to take on the insidious and incomprehensible PowerPC and try to figure out how to bypass the integrity control and get the coveted key!
Task number 9 of the planet Paradisos: "In Search of Earthlings"
On the “heavenly” planet, the participants were given the address of a Web site where information about four scientists was posted. According to the legend, the participants were required to obtain information about a scientist who is absent from the site by conducting a SQL injection.
The task was complicated by the presence of WAF , which blocked dangerous requests. Participants were forced to form non-trivial SQL queries to bypass the logic of WAF. The imagination of the participants was limited to a little, someone plunged into the BBbSQLi operation, and someone had enough tricks with comments in the request to throw WAF on the shoulder blades. How hackzard coped with this task can be read here .
The task site will be available until April, so there is still time to figure it out!
Statistics
1352 people took part in the competition, 80 participants got at least one key. Like last year, we collected changes in our standings into a nice gif (which, of course, did not fit all the participants)
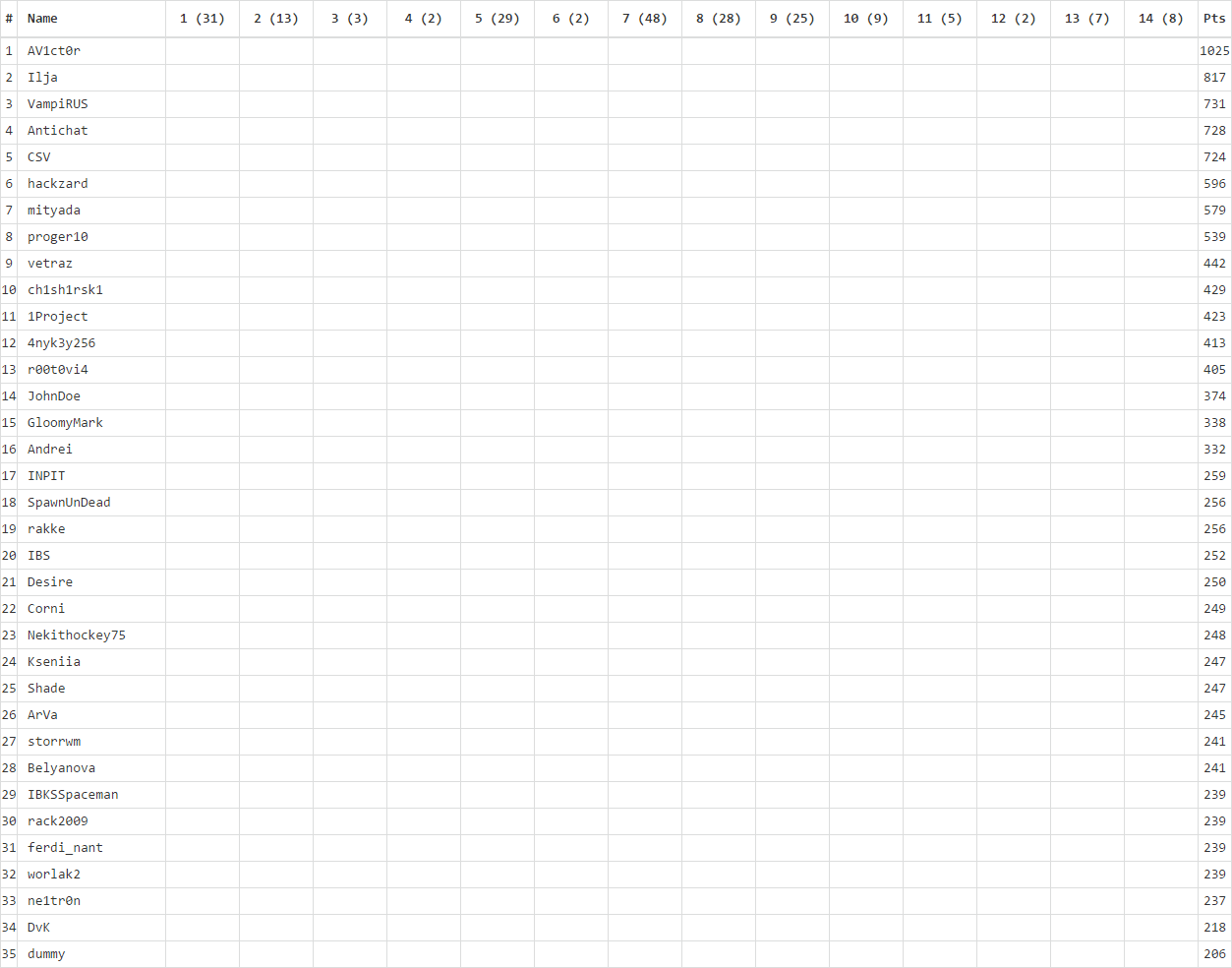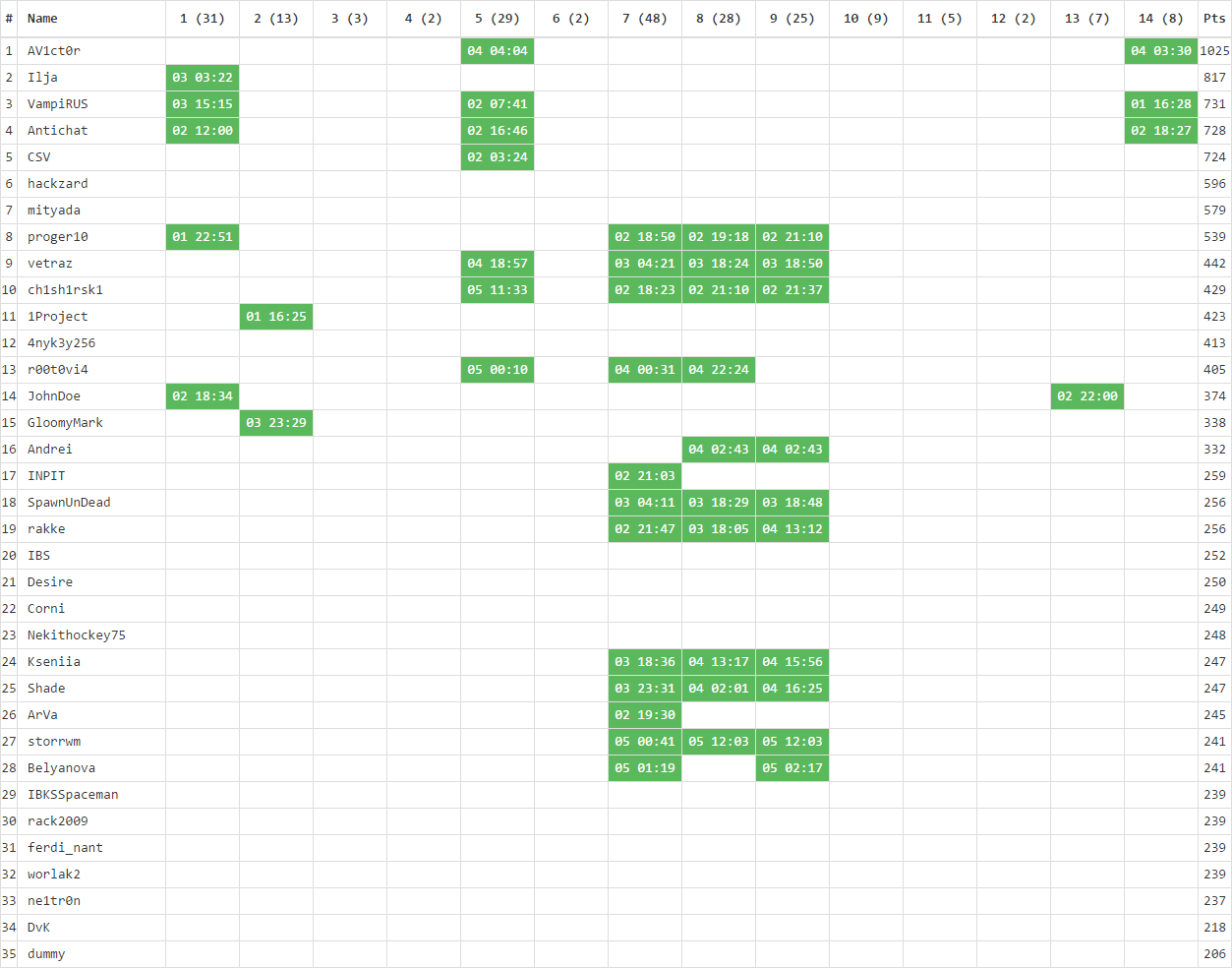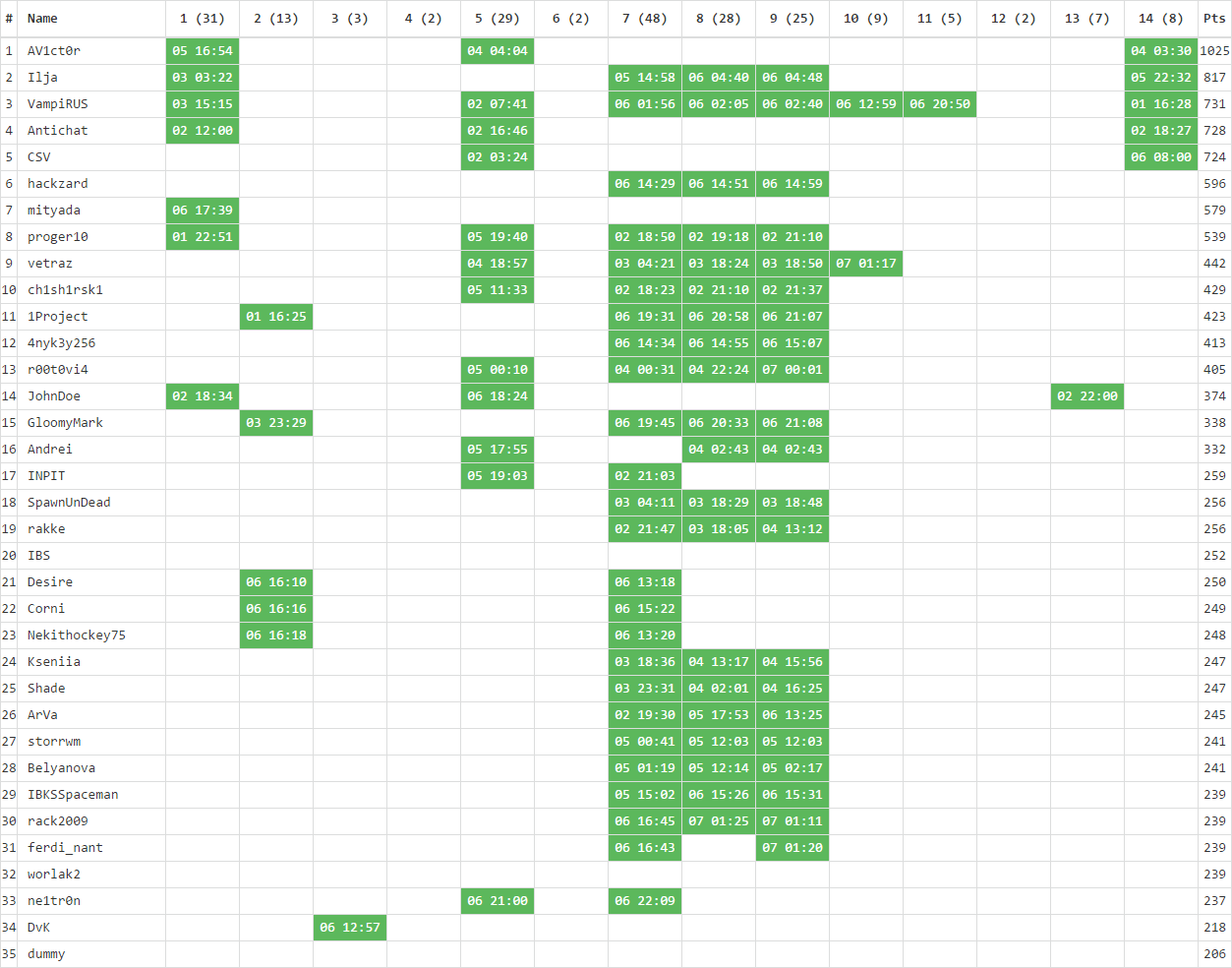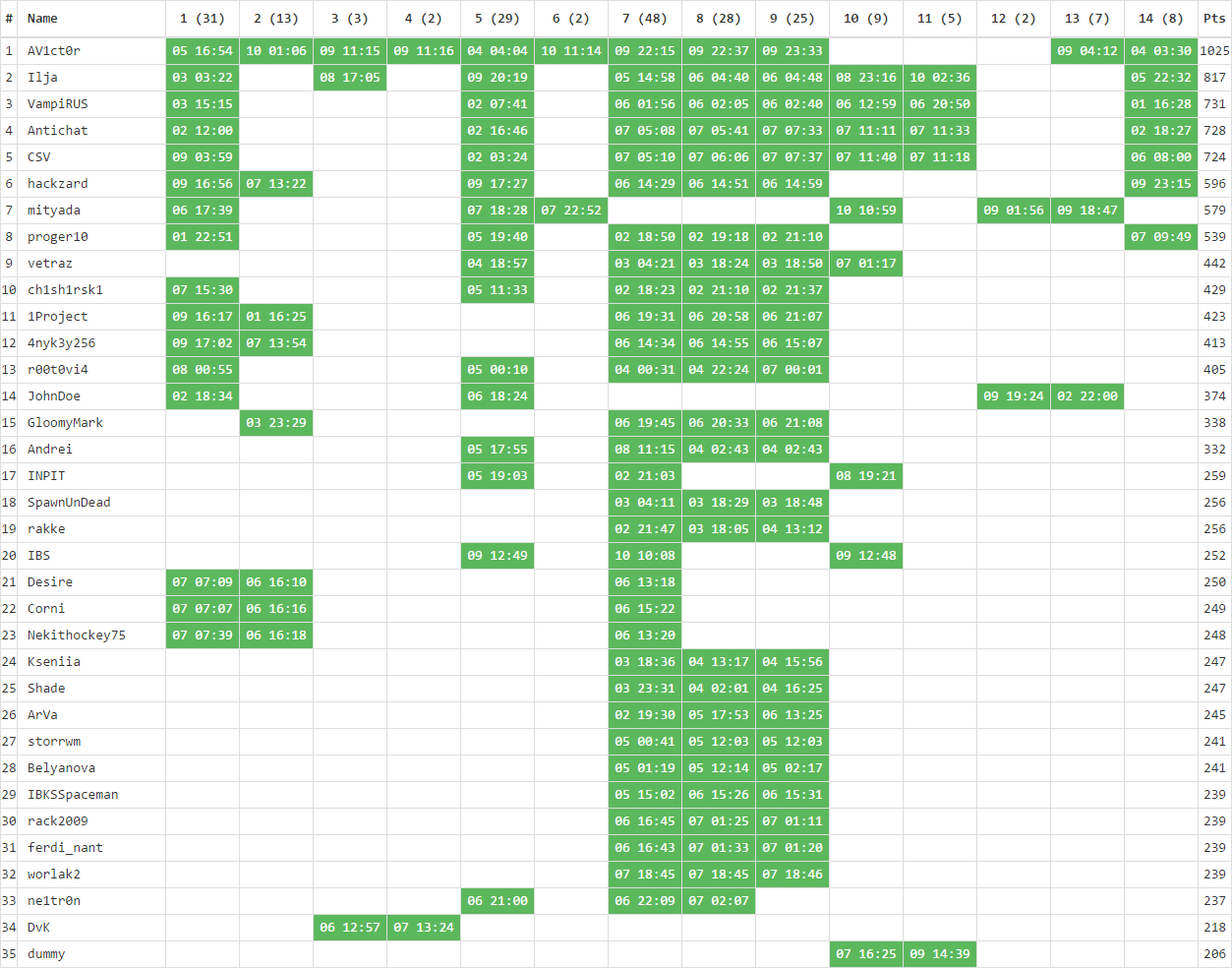
We also collected statistics on the complexity of the tasks and on which days the participants of NeoQUEST-2017 were the most active!
Here is the situation with the complexity of the tasks: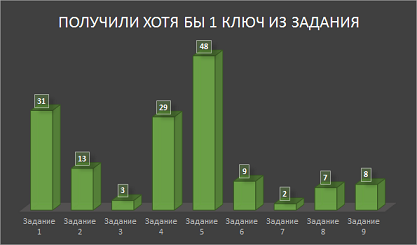
The simplest task was the number 5 of the planet Espion, codenamed “Multi passport!” - 48 participants received at least one of the three keys available in the task.
The most difficult task turned out to be task # 7 of the planet E-mu with the cerebral name “Lost in the dodecahedron”: only 2 participants passed it. As the second most complex task, Planet 3 of Etheris is “Citizens, keep money in cryptocurrency!” - here at least one of the two keys managed to get only three.

The simplest task was the number 5 of the planet Espion, codenamed “Multi passport!” - 48 participants received at least one of the three keys available in the task.
The most difficult task turned out to be task # 7 of the planet E-mu with the cerebral name “Lost in the dodecahedron”: only 2 participants passed it. As the second most complex task, Planet 3 of Etheris is “Citizens, keep money in cryptocurrency!” - here at least one of the two keys managed to get only three.
Now let's see what keys in the "multi-key" tasks turned out to be the hardest.
Tasks with multiple keys
"Multi-key" tasks were 4:
The easiest way for 48 participants was to get the first key to task number 5, but a little less than half (20) of those who received the first key could not get the other keys.
The second keys to tasks # 3 and # 4 turned out to be the most difficult keys, while if the difference in the number of people who received the key for task # 3 turned out to be small, then the difference between those who received the first and second keys in task # 4 is impressive: only two from 29 managed to get both keys!
- task number 3 of the planet Etheris "Citizens, keep money in cryptocurrency!" - 2 keys;
- task number 4 of the planet iFetus "Forbidden Fruit" - 2 keys;
- task number 5 of the planet Espion "Multipasport!" - 3 keys;
- task number 6 of the planet Prioritus "Too many things ..." - 2 keys.

The easiest way for 48 participants was to get the first key to task number 5, but a little less than half (20) of those who received the first key could not get the other keys.
The second keys to tasks # 3 and # 4 turned out to be the most difficult keys, while if the difference in the number of people who received the key for task # 3 turned out to be small, then the difference between those who received the first and second keys in task # 4 is impressive: only two from 29 managed to get both keys!
In just 10 days of competition, 212 keys were received, and then it became interesting to us: on which days were our participants most active?
Activity of participants for all time
Suddenly it turned out that the weekend was not particularly productive, and the largest number of keys was received on Monday and Tuesday (March 6 and 7, respectively).

Suddenly it turned out that the weekend was not particularly productive, and the largest number of keys was received on Monday and Tuesday (March 6 and 7, respectively).
We are waiting for everyone to "confrontation"!
The online stage of the competition is over, and we are starting preparations for the summer "confrontation", which will be held on June 29 in St. Petersburg ! Absolutely ALL will be able to visit it, even those who did not participate in the online stage. Free admission!
We will invite the best participants of the online stage as participants in the final eight-hour battle for a trip to one of the international conferences.
And as guests, we are waiting for all-all who are interested in information security! Take friends, colleagues, and come / come / fly. We guarantee: cool, interesting, informative and fun will be ABSOLUTELY ALL! Reports, contests, real-time demonstrations of attacks, Twitter quiz, cool prizes and chat, summing up the final hackquest results - all this is on June 29 in St. Petersburg!
Source: https://habr.com/ru/post/323838/
All Articles