Security Week 10: DNS remote control, how Google deceived its captcha, a hole in the Wordpress plugin
 The virtuosos on the dark side have not translated yet. Some clever guys have found another harmful use of the long-suffering DNS protocol. Remember, ten years ago, DNS Amplification DDoS attacks came into fashion? So they are still in trend.
The virtuosos on the dark side have not translated yet. Some clever guys have found another harmful use of the long-suffering DNS protocol. Remember, ten years ago, DNS Amplification DDoS attacks came into fashion? So they are still in trend.Even then, the ddosers had thought of using remarkable TXT fields in the DNS record. After all, you can put arbitrary data, because the organizers of the attacks registered a domain with a random name, and TXT was filled with garbage (out of place, up to 4 Kb in the field - 16 lines of 256 bytes each). The request is 64 bytes, the answer is 3.8 Kb (to fit in UDP), the victim receives traffic at a rate of 1:60, and her channel, or even the channel of her provider, says “kva” from several dozen bots already.
In short, the story is not new. But ever since, the TXT fields have been asking for more efficient use. And they received it ( news ) - Talos Intelligence described an interesting attack by DNSMessenger, in which a bidirectional channel for taxiing was organized using the DNS protocol.
The authors of DNSMessenger really, really wanted their activities to remain out of the researchers' view. And for some time it even turned out: the attack does not write files to the hard disk, in addition to the document with the script of the first stage of the attack, and all communications go through DNS, which is usually not controlled.
')
 It all starts with a VBA script loaded into a Microsoft Word document that the victim of the attack receives by mail, and, when opened, sees a soothing message that the content is safe, as protected by the infinite power of McAfee. Well, once safe, click on the enable content in order to run a script that will do you well.
It all starts with a VBA script loaded into a Microsoft Word document that the victim of the attack receives by mail, and, when opened, sees a soothing message that the content is safe, as protected by the infinite power of McAfee. Well, once safe, click on the enable content in order to run a script that will do you well.And he is glad to try. Determines the version of PowerShell installed in the system: and if it is 3.0, which is well able to work with ADS (alternative NTFS streams where hidden information about files is stored), then it stores the script code of the next attack stage in ADS. If PowerShell is older, the script writes code to the registry. Well, in the end sets the task scheduler to run this code after half an hour of inactivity of the system.
 Next, the next stage script organizes the transfer of messages between the attacker and the shell of the victim system. He knocks on one of the C & C servers with an innocent-looking DNS request, and he sends him a DNS response, where the TXT field contains the input for the command line.
Next, the next stage script organizes the transfer of messages between the attacker and the shell of the victim system. He knocks on one of the C & C servers with an innocent-looking DNS request, and he sends him a DNS response, where the TXT field contains the input for the command line.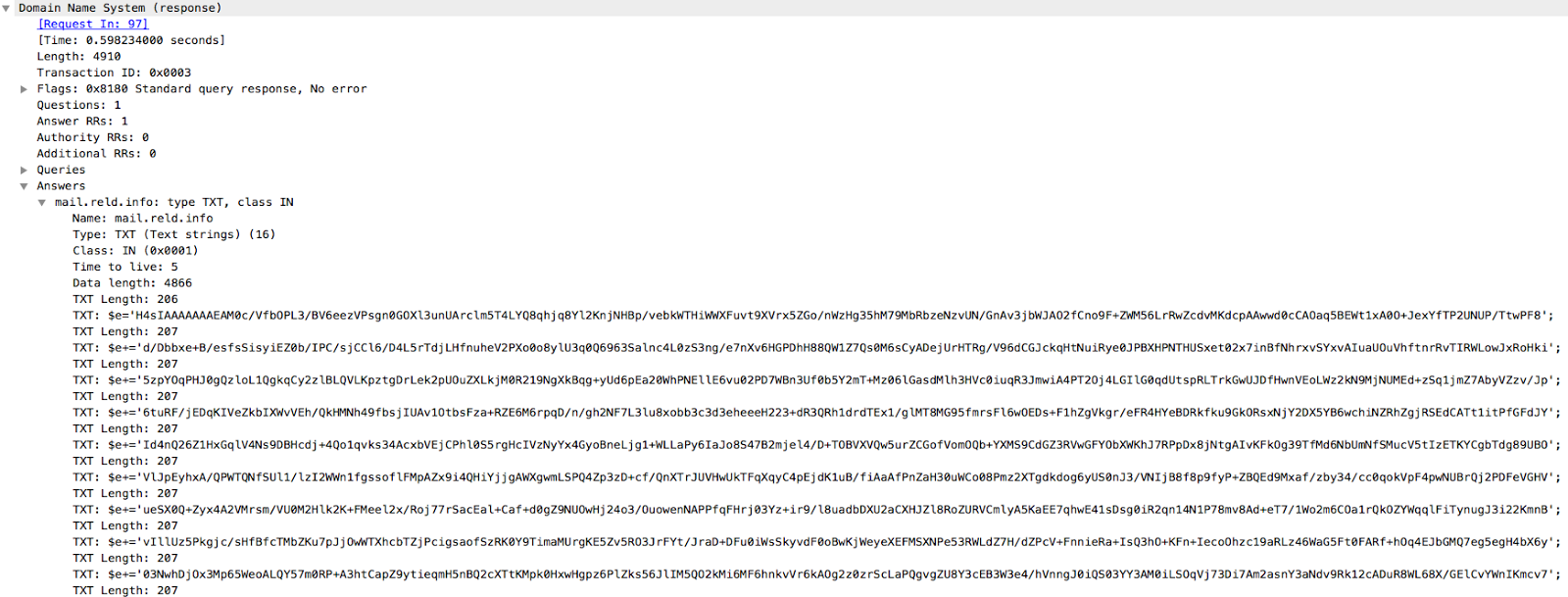
A malicious script sends the console output to the same server, disguised as a URL. In the example given in the study, the domain is
708001701462b7fae70d0a28432920436f70797269676874.
20313938352d32303031204d696372.6f736f667420436f72702e0d0a0d0a.433a5c54454d503e.cspg.pw 708001701462b7fae70d0a28432920436f70797269676874.
20313938352d32303031204d696372.6f736f667420436f72702e0d0a0d0a.433a5c54454d503e.cspg.pw 708001701462b7fae70d0a28432920436f70797269676874.
20313938352d32303031204d696372.6f736f667420436f72702e0d0a0d0a.433a5c54454d503e.cspg.pw decoded to \r\n(C) Copyright 1985-2001 Microsoft Corp.\r\n\r\nC:\\TEMP> .Google can fool its own captcha (no longer)
News Research
If Google is all-powerful, can it create a captcha that it doesn't recognize itself? No one knows, but Google is constantly trying. This time, some anonymous researcher, who identified himself as Eeast-Ee Security, poisoned ReCaptcha 2.0 and Google Speech Recognition. The idea lay on the surface: if, after a click confirming that you are not a robot, the system offers to solve the riddle, you just need to reload the captcha until you get the option of recognizing the numbers spoken aloud. And you do not even need to engage in the capture of sound, you can simply download the audio.
Then we convert it into wav, feed Google Speech Recognition through its own API, and copy-paste the result of recognition back. The simplest attack, perfectly automated, which the author did . It must be said that they tried to implement a similar detour of the captchus five years ago , but at that time the researchers built their own speech recognition system from the hash function, the neural network and the routing machines, and this was specifically a manual method. Now a piece of Python code does it all by itself.
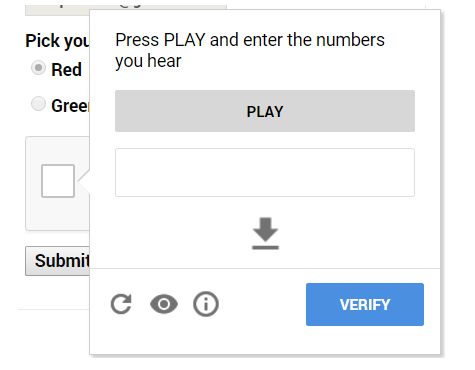 On paper, everything went smoothly, but as soon as the news of clever self-deception Google went through the community, many rushed to test the provided code, and the captcha, having discovered multiple attempts at automatic recognition, naturally began to defend itself. Then he will add more figures, he will add noise, he will ask to recognize the numbers several times in a row.
On paper, everything went smoothly, but as soon as the news of clever self-deception Google went through the community, many rushed to test the provided code, and the captcha, having discovered multiple attempts at automatic recognition, naturally began to defend itself. Then he will add more figures, he will add noise, he will ask to recognize the numbers several times in a row.The author initially responded that the problem in the source's IP address, they say, Google considers him suspicious, but soon he acknowledged that the captcha is rapidly becoming more complicated. Three days after the exploit was published, the method stopped working altogether. Total in the fight against Google against Google once again defeated Google. But it's too early to lose heart - we believe that Google will still strike back.
More than a million Wordpress sites use a leaky plugin.
News Research
Just do not say that the news about the holes in Wordpress and its plug-ins have long been boring to everyone! I write myself, gritting my teeth. But do you know how many sites are online on this CMS? And I do not know, but a year ago there were 16 million! Therefore, every hole in it responds with a sharp pain in the tambourines of a huge crowd of webmasters. An important topic, you can not keep silent.
This time, among the potential victims are users of the NextGen Gallery plugin. Vulnerability is not weak - SQL injection, which allows (attention!) "Unauthenticated user to steal data from the database, including important user data."
The authors of the popular plugin violated the golden rule "never trust the input data, suddenly there is a malicious SQL query." In general, if you have Wordpress websites, you know what to do. Everything is as usual.

Antiquities
"MTLI-830"
Resident very dangerous virus. Standard affects .COM files when they are launched. On Friday, some time after launch, it starts deleting files instead of launching them. It contains the text: “Hello! MLTI! ”,“ Eddie die somewhere in time! This programm was written in the city of Prostokwashino © 1990 RED DIAVOLYATA.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 76.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/323652/
All Articles