Check Point. What is it, what is it eaten with or briefly about the main thing
Hello, dear readers of Habr! This is TS Solution's corporate blog. We are a system integrator and for the most part we specialize in IT infrastructure security solutions ( Check Point , Fortinet ) and machine data analysis systems ( Splunk ). We begin our blog with a small introduction to Check Point technology.
We have long thought about whether to write this article, because there is nothing new in it that could not be found on the Internet. However, despite this abundance of information when working with clients and partners, we often hear the same questions. Therefore, it was decided to write a kind of introduction to the world of Check Point technologies and reveal the essence of the architecture of their solutions. And all this within the framework of one “small” post, so to speak, a quick excursion. And we will try not to go into the marketing war, because we are not a vendor, but simply a system integrator (even though we love Check Point very much) and just consider the main points without comparing them with other manufacturers (such as Palo Alto, Cisco, Fortinet, etc.). The article turned out to be quite voluminous, but it cuts off most of the questions at the stage of familiarization with Check Point. If you are interested, welcome under the cat…
UTM / NGFW
Starting a conversation about Check Point, the first thing to start is to explain what UTM, NGFW are and how they differ. We will do this very succinctly so that the post does not turn out to be too large (perhaps in the future we will consider this question in a bit more detail)
')
UTM - Unified Threat Management
In short, the essence of UTM is the consolidation of several protection tools in one solution. Those. all in one box or some all inclusive. What is meant by “multiple remedies”? The most common option is: Firewall, IPS, Proxy (URL filtering), Streaming Antivirus, Anti-Spam, VPN, and so on. All this is combined in a single UTM solution, which is simpler in terms of integration, configuration, administration and monitoring, and this in turn has a positive effect on the overall security of the network. When UTM solutions only appeared, they were considered exclusively for small companies, since UTM could not cope with large volumes of traffic. This was for two reasons:
- Packet handling method. The first versions of UTM solutions processed packets sequentially, with each “module”. Example: first, the packet is processed by the firewall, then the IPS, then the Anti-Virus checks it, and so on. Naturally, such a mechanism introduced serious delays in traffic and heavily consumed system resources (processor, memory).
- Weak "iron". As mentioned above, the sequential processing of packets strongly eats off resources and the hardware of those times (1995-2005) simply could not cope with the large traffic.
But progress does not stand still. Since then, the hardware capacities have significantly increased, and packet processing has changed (it must be admitted that not all vendors have done so) and has begun to allow almost simultaneous analysis in several modules (ME, IPS, AntiVirus, etc.). Modern UTM solutions can “digest” tens and even hundreds of gigabits in the deep analysis mode, which makes it possible to use them in the segment of large business or even datacenters.
Below is the famous Gartner magic quadrant for UTM solutions for August 2016:

I will not strongly comment on this picture, I’ll just say that there are leaders in the upper right corner.
NGFW - Next Generation Firewall
The name speaks for itself - the next generation firewall. This concept appeared much later than UTM. The main idea of NGFW is in-depth packet analysis (DPI) using the built-in IPS and access control at the application level (Application Control). In this case, IPS is just needed in order to detect an application in the packet stream, which allows you to allow or deny it. Example: We can allow Skype to work, but prohibit file transfer. We can prohibit the use of Torrent or RDP. Web applications are also supported: You can allow access to VK.com, but prohibit games, messages or watching videos. In fact, the quality of NGFW depends on the number of applications it can determine. Many believe that the emergence of the concept of NGFW was the usual marketing ploy against which Palo Alto began its rapid growth.
Gartner's Magic Quadrant for NGFW for May 2016:
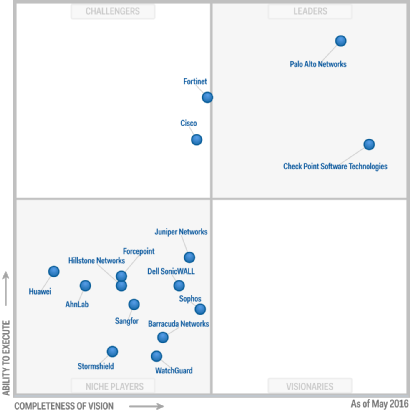
UTM vs NGFW
Very frequent question, what is better? There is no definite answer and there can not be. Especially if you take into account the fact that almost all modern UTM solutions contain NGFW functionality and most NGFW contain features inherent to UTM (Antivirus, VPN, Anti-Bot, etc.). As always, “the devil is in the details”, so first of all you need to decide what you need specifically, to decide on the budget. Based on these solutions, you can choose several options. And everything needs to be unequivocally tested, not believing in marketing materials.
In our turn, within the framework of several articles we will try to tell you about Check Point, how you can try it and what you can try in principle (almost all the functionality).
Three Check Point Entities
When working with Check Point, you will definitely come across three components of this product:
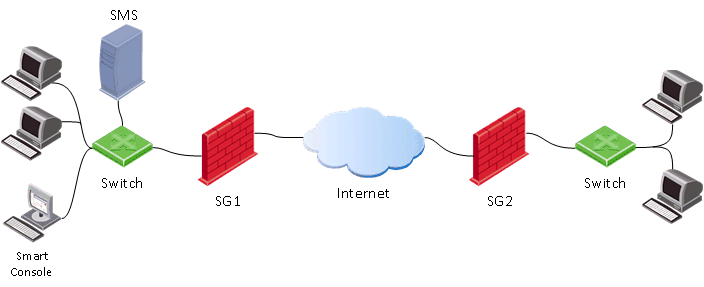
- Security Gateway (SG) is the security gateway itself, which is usually placed on the perimeter of the network and acts as a firewall, streaming antivirus, anti-bot, IPS, etc.
- Security Management Server (SMS) - gateway management server. Almost all settings on the gateway (SG) are performed using this server. SMS can also act as a log server and process them with an integrated system for analyzing and correlating events - a Smart Event (similar to SIEM for Check Point), but more on that later. SMS is used for centralized management of several gateways (the number of gateways depends on the SMS model, or on the license), but you must use it even if you have only one gateway. It should be noted here that Check Point is one of the first to use such a centralized management system, which for many years has been recognized as the “gold standard” according to Gartner reports. There is even a joke: “If Cisco had a normal control system, then Check Point would never appear.”
- Smart Console - client console to connect to the management server (SMS). As a rule, it is installed on the administrator’s computer. Through this console, all changes are made on the management server, and after that you can apply the settings to the Security Gateways (Install Policy).

Check Point Operating System
Speaking of the Check Point operating system, you can remember three at once: IPSO, SPLAT and GAIA.
- IPSO is the operating system of Ipsilon Networks, which was owned by Nokia. In 2009, Check Point bought this business. No longer develops.
- SPLAT - Check Point's own development, based on the RedHat core. No longer develops.
- Gaia is an up-to-date Check Point operating system, which emerged from the merger of IPSO and SPLAT, incorporating the very best. Appeared in 2012 and continues to grow rapidly.
Speaking of Gaia, it should be said that currently the most common version is R77.30. A relatively recently appeared version of the R80, which is significantly different from the previous one (both in terms of functionality and management). We will dedicate a separate post to the topic of their differences. Another important point is that currently the FSTEC certificate only has version R77.10 and is certified version R77.30.
Execution Options (Check Point Appliance, Virtual machine, OpenSerever)
There is nothing surprising, as many vendors Check Point has several product options:
- Appliance is a hardware / software device, i.e. its own piece of hardware. There are a lot of models that differ in performance, functionality and performance (there are options for industrial networks).

- Virtual Machine - Checkia Virtual Machine with Gaia OS. ESXi, Hyper-V, KVM hypervisors are supported. Licensed by the number of processor cores.
- OpenServer - installing Gaia directly on the server as the main operating system (the so-called “Bare metal”). Only certain “hardware” is supported. There are recommendations for this hardware that must be followed, otherwise there may be problems with the drivers and those. support you may refuse to service.
Deployment options (Distributed or Standalone)
Slightly above, we have already discussed what a gateway (SG) and a management server (SMS) are. Now we will discuss options for their implementation. There are two main ways:
- Standalone (SG + SMS) - an option when both the gateway and the management server are installed within one device (or virtual machine).

This option is suitable when you have only one gateway, which is lightly loaded with user traffic. This option is the most economical, because No need to buy a management server (SMS). However, if the gateway is heavily loaded, you can get a “braking” control system. Therefore, before choosing a Standalone solution, it is best to consult or even test this option. - Distributed - the management server is installed separately from the gateway.
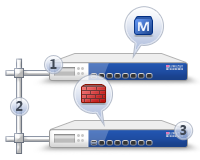
The best option in terms of convenience and performance. It is used when it is necessary to manage several gateways at once, for example, central and branch offices. In this case, a management server (SMS) purchase is required, which can also be in the form of an appliance (piece of iron) or a virtual machine.
As I said a little higher, Check Point has its own SIEM system - the Smart Event. You can use it only in the case of a distributed installation.
Modes of operation (Bridge, Routed)
Security Gateway (SG) can operate in two main modes:
- Routed is the most common option. In this case, the gateway is used as an L3 device and routes the traffic through itself, i.e. Check Point is the default gateway for the protected network.
- Bridge - transparent mode. In this case, the gateway is installed as a normal “bridge” and passes traffic at the second level (OSI) through itself. This option is usually used when there is no possibility (or desire) to change an existing infrastructure. You practically do not have to change the network topology and do not have to think about changing the IP addressing.
I would like to note that in Bridge mode there are some restrictions on functionality, so we, as an integrator, advise all our customers to use the Routed mode, of course, if possible.
Software Blades (Check Point Software Blades)
We got almost to the main theme of Check Point, which causes the most questions from customers. What are these “software blades”? Blades are defined as Check Point features.

These functions can be turned on or off depending on your needs. At the same time, there are blades that are activated exclusively on the Gateway (Network Security) and only on the Management Server (Management). The pictures below are examples for both cases:
1) For Network Security (gateway functionality)
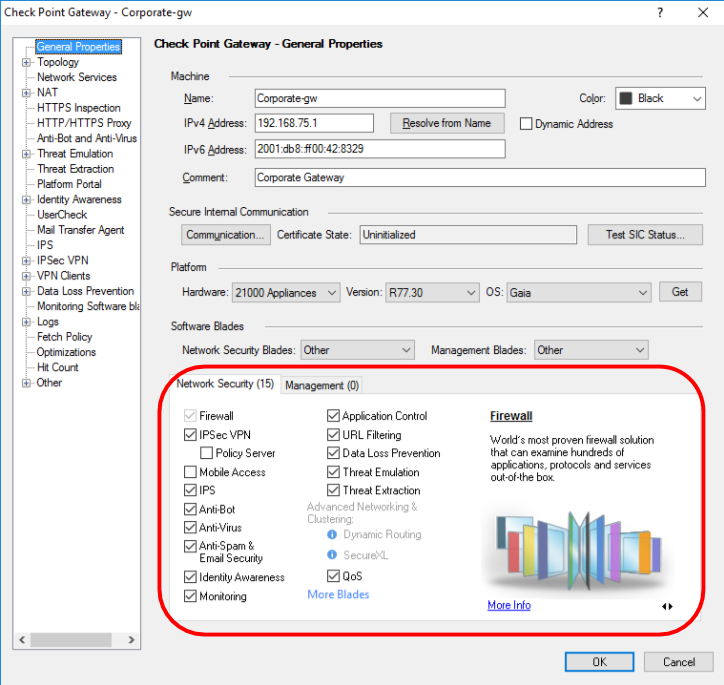
We describe briefly, because each blade deserves a separate article.
- Firewall - firewall functionality;
- IPSec VPN - building private virtual networks;
- Mobile Access - remote access from mobile devices;
- IPS - Intrusion Prevention System;
- Anti-Bot - protection from botnet networks;
- AntiVirus - streaming antivirus;
- AntiSpam & Email Security - protection of corporate mail;
- Identity Awareness - integration with Active Directory;
- Monitoring - monitoring almost all gateway parameters (load, bandwidth, VPN status, etc.)
- Application Control - application-level firewall (NGFW functionality);
- URL Filtering - Web security (+ proxy functionality);
- Data Loss Prevention - Leak Protection (DLP);
- Threat Emulation - sandbox technology (SandBox);
- Threat Extraction - file cleaning technology;
- QoS - traffic prioritization.
Literally through several articles we will look in detail at the Threat Emulation and Threat Extraction blades, I am sure that it will be interesting.
2) For Management (management server functionality)

- Network Policy Management - centralized policy management;
- Endpoint Policy Management - centralized management of Check Point agents (yes, Check Point produces solutions not only for network protection, but also for protecting workstations (PCs) and smartphones);
- Logging & Status - centralized collection and processing of logs;
- Management Portal - security management from the browser;
- Workflow - control over policy changes, audit changes, etc .;
- User Directory - integration with LDAP;
- Provisioning - automation of gateway control;
- Smart Reporter - reporting system;
- Smart Event - event analysis and correlation (SIEM);
- Compliance - automatic verification of settings and issuing recommendations.
We will not now consider in detail the issues of licensing, so as not to inflate the article and not confuse the reader. Most likely we will take it to a separate post.
The blade architecture allows you to use only the functions you really need, which affects the budget of the solution and the overall performance of the device. It makes sense that the more blades you activate, the less traffic you can “drive off”. That is why the following performance table is attached to each Check Point model (for example, they took the characteristics of the 5400 model):
As you can see here are two categories of tests: on synthetic traffic and on real - mixed. Generally speaking, Check Point is simply forced to publish synthetic tests, since Some vendors use similar tests as a reference, without examining the performance of their solutions on real traffic (or they intentionally hide such data due to their unsatisfactory performance).
In each type of dough you can see several options:
- Firewall test only;
- Firewall + IPS test;
- Firewall + IPS + NGFW (Application control) test;
- test Firewall + Application Control + URL Filtering + IPS + Antivirus + Anti-Bot + SandBlast (sandbox)
Carefully look at these parameters when choosing your solution, or ask for advice .
I think this can finish the introductory article on Check Point technologies. Next, we will look at how Check Point can be tested and how to deal with modern information security threats (viruses, phishing, cryptographers, zero-day).
PS An important point. Despite the foreign (Israeli) origin, the decision is certified in the Russian Federation in the supervisory authorities, which automatically legalizes their presence in state institutions (comment by Denyemall ).
Source: https://habr.com/ru/post/323606/
All Articles