OpenVAS 9 release took place

OpenVAS (Open Vulnerability Assessment System, Open Vulnerability Assessment System, the original name is GNessUs) is a framework consisting of several services and utilities that allows scanning network nodes for vulnerabilities and managing vulnerabilities.
The OpenVAS project, under the name GNessUs, began as a fork of the open source vulnerability scanner Nessus, developed by Tenable Network Security, after the company decided in October 2005 to close the source code of the application and make it proprietary. All OpenVAS products are open source and are licensed under the GPL. About 2 years passed between the previous (8) and current (9) releases.
')
OpenVAS is an open source scanner and vulnerability management tool. It is designed to actively monitor network nodes to identify problems related to security, assess the criticality of these problems and monitor their removal. Active monitoring means that OpenVAS performs some actions on the host: scans open ports, sends specially formed packets to simulate an attack, or even logs in on the host, gains access to the management console, and executes commands on it. In simple terms - OpenVAS allows you to identify problem nodes with non-updated software or unsafely configured.
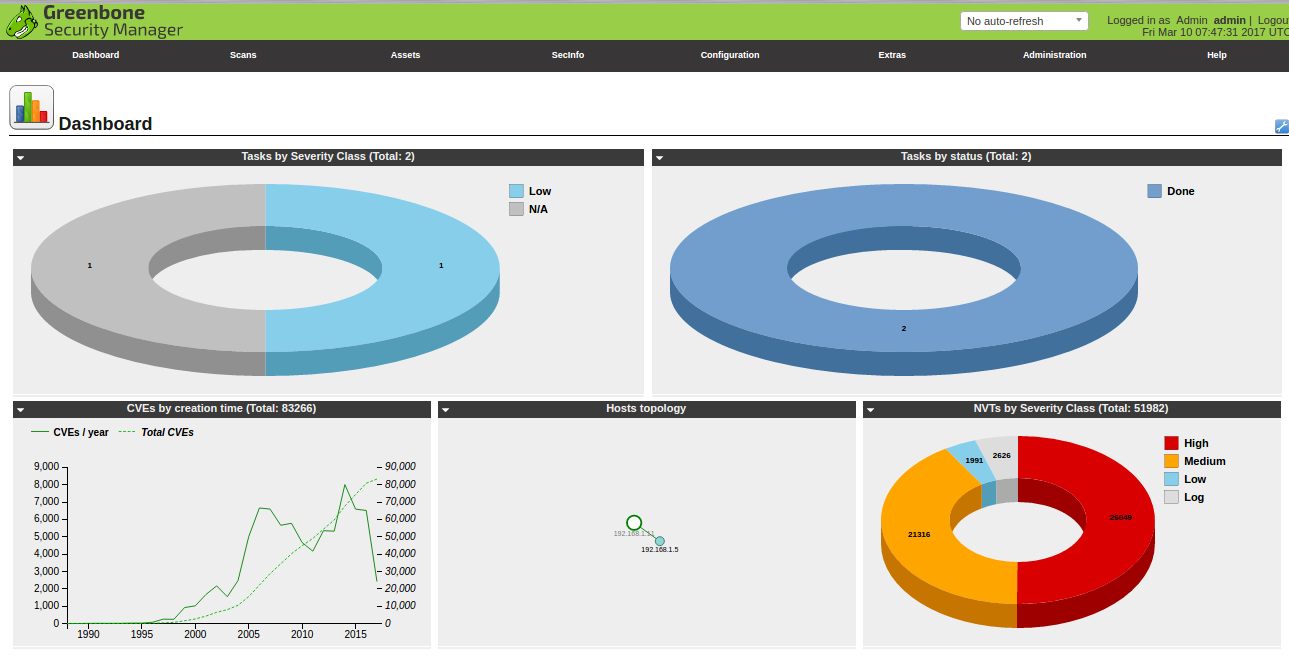
The basis of the OpenVAS operation is the NVT (Network Vulnerability Tests) collection of security tests (in the new version - about 50,000, as opposed to the old version - about 30,000), which make it possible to identify the vulnerability. The description of known problems is then checked against the CVE and OpenSCAP vulnerability management databases (Security Content Automation Protocol). OpenSCAP itself (open-scap.org) supports several specifications: XCCDF, OVAL, ARF, CCE, CVSS and CVE.
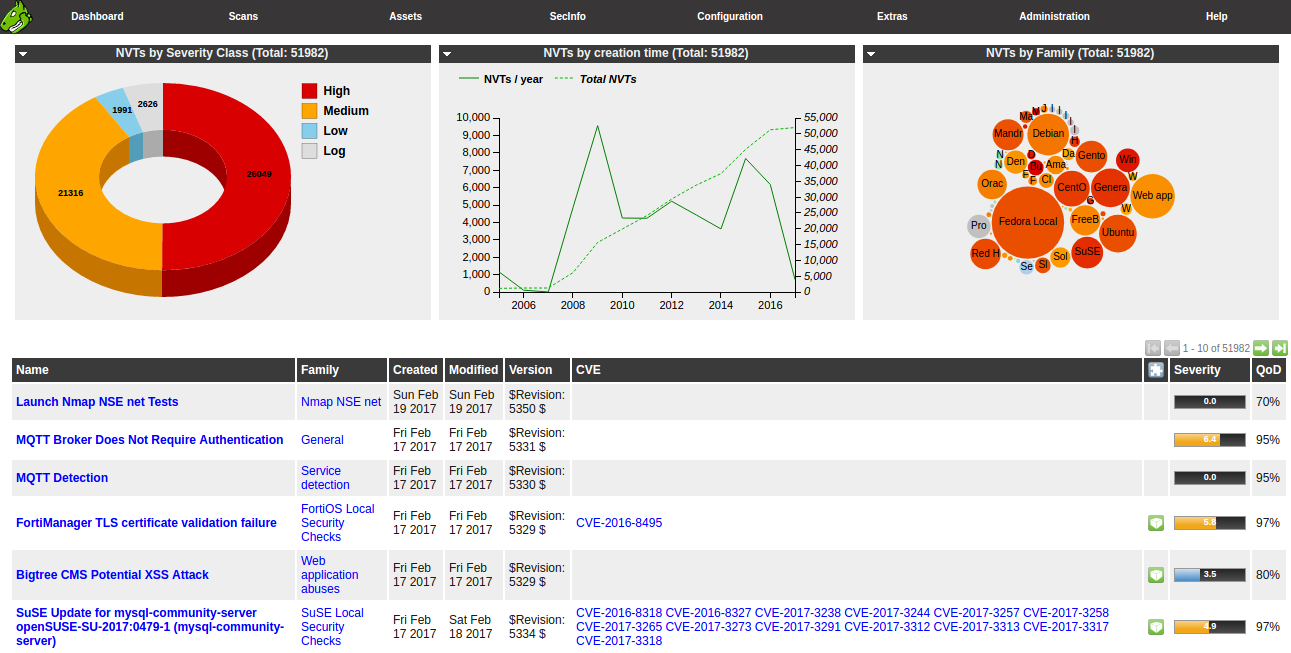
In version 9 of OpenVAS, a new web interface for scanning and managing vulnerabilities is presented in the form of panels with advanced features for ease of use. This helps to improve the analysis of scan results and vulnerability management. The new interface has become more innovative, in contrast to the previous version, which did not differ in elegance.
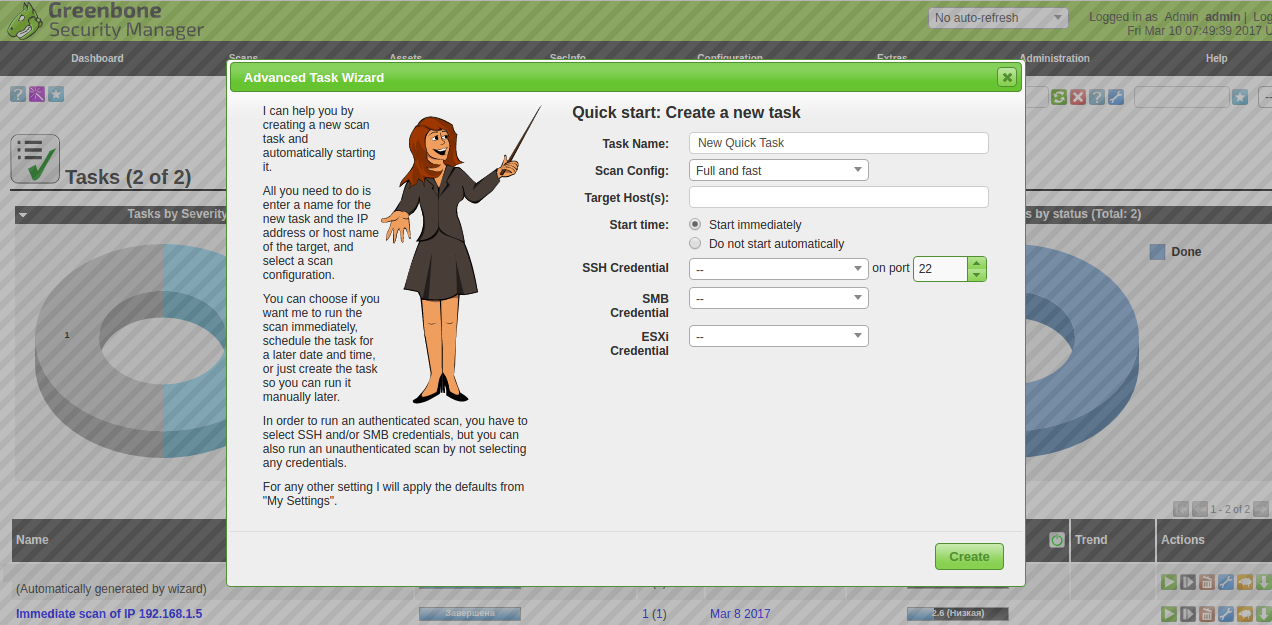
The most notable new functionality is resource management, which adds a new view of scan results for hosts and operating systems. This allows you to more quickly manage workflow management vulnerabilities. The scanning process is transferred to the multiscan architecture.
Greenbone is developing OpenVAS as the basis for the Greenbone Security Manager professional product line. Previously, Greenbone did not promote the OpenVAS commercial version, and many OpenVAS users are not aware of this. With the new release, GSM Community Edition (GCE) appears, for the use of which a key is needed. On the one hand, this is a sensible step for the development of the project, on the other hand, it can greatly separate the versions in the future, as was the case with other security products.
OpenVAS is included in popular penetration testing distributions (such as Kali Linux), deployed in * nix systems. The most convenient mode of use is a virtual upline, which contains everything you need. Note: after installation, it takes some time for OpenVAS to update the NVT database in the background.
Minimum requirements: 2 CPU, 2 GB RAM, 9 GB HDD.
Compatibility: VirtualBox, ESXi, Hyper-V.
Vulnerability scanning is an important phase of penetration testing . A timely updated vulnerability scanner can play an important role and help detect previously missing elements. Using a tool such as OpenVAS allows you to identify incorrectly configured hosts, non-updated software versions, and helps IT / IB technicians to make their infrastructure safer.
Source: https://habr.com/ru/post/323568/
All Articles